101 Exam
Top Tips Of Renew 101 Preparation

Want to know Ucertify 101 Exam practice test features? Want to lear more about F5-Networks Application Delivery Fundamentals certification experience? Study Virtual F5-Networks 101 answers to Far out 101 questions at Ucertify. Gat a success with an absolute guarantee to pass F5-Networks 101 (Application Delivery Fundamentals) test on your first attempt.
Online F5-Networks 101 free dumps demo Below:
NEW QUESTION 1
What is used to establish trust relationships between BIG-IP devices?
- A. trust ID
- B. device group identification
- C. certificate-based authentication
- D. unit IDs
Answer: C
NEW QUESTION 2
A VoIP application requires that data payloads will NOT be fragmented. Which protocol controls network behavior in this situation?
- A. RTSP
- B. UDP
- C. TCP
- D. IP
Answer: A
NEW QUESTION 3
Web application http://www example.com at 10.10.1.1.10 is unresponsive.
A recent change installed new firewalls in the network. Which command should be used to locate where data loss has occurred within the network?
A)
B)
C)
D)
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: C
Explanation:
Traceroute attempts to send ICMP-packets that expire further down the network and determine if a network device is responding or allowing traffic through.
NEW QUESTION 4
An administrator suspects that a BIG IP appliance is experiencing performing issue due to spikes in CPU usage checks the performance issues does to spikes in CPU usage checks the performance report in the BIG-IP UI on CPU spikes are evident in the graphs. Which section in the BIG IP UI can the administrator check to troubleshoot the issue further?
- A. Statistics > Utilization
- B. System . Utilization
- C. Statics > Dashboard
- D. System > Services
Answer: C
NEW QUESTION 5
BIG-IP ASM is requesting automatic signature updates from the F5 update service
Who is considered the server in this communication?
- A. BIG-IP
- B. User A
- C. F5 update Service
- D. web application
Answer: C
NEW QUESTION 6
An administrator security policy defines allowed URLs, file types and parameter values Which security model is the administrator using?
- A. negative security model
- B. Closed security model
- C. positive Security model
- D. ACL Security model
Answer: C
Explanation:
https //www owasp.org/index.php/Positive_security_model
NEW QUESTION 7
A new web server VLAN has been created and the IP address 10.1.1.1/24 has been assigned to the BIG IP device. The BIG IP Administrator needs to create the new Self IP and prevent administrator access to the BIG-IP device from the newly created network.
Which TMSH command should be used?
- A. create /net self internal address 10 1.1. 1/24 vlan VLAN 10 allow service none.
- B. add 'net self internal address 10.1.1. 1/24 vlan VLAN 10 allow-service none
- C. create /net self internal address 10. 1. 1. 1/24 vlan VLAN 10 allow service default
- D. add /net self internal address 10 111 mask 265. 255. 2550 vlan VLAN 10 allow
Answer: A
Explanation:
White the default differs from version to version, H typically allows HTTP SSH and iQuety for BIG-IP to BIG-IP communication
NEW QUESTION 8
in which scenario is a full proxy TCP connection required?
- A. when SSL offloading is used
- B. when Traffic is routed
- C. when administrators manage the servers directly
- D. when 3 server responds directly to the client
Answer: A
NEW QUESTION 9
A company deploys F5 load balancers to manage number of secure applications. The company needs to centrally manage certificates.
Which F5 product provides this functionality?
- A. BIG IQ
- B. GTW
- C. iHeath
- D. LTM
Answer: A
NEW QUESTION 10
A device needs to decrypt traffic and send unencrypted traffic to the web server. Which method should the BIG-IP Administrator use?
- A. SSL Optimization
- B. SSL Caching
- C. SSL Termination
- D. SSL Bridging
Answer: C
NEW QUESTION 11
The HTTP 1.1 standard is being used as part of communication to a server. The client fails to maintain the session within the maximum timeout defined by the server. Which device is responsible for ending the HTTP session?
- A. the load balancer
- B. the server
- C. the default gateway of the load balancer
- D. the client
Answer: C
NEW QUESTION 12
A user is trying to access a website using the URL https://1.1.1.1/ The website fails to load. The user can access other websites. Given the packet capture above, what is the most likely issue?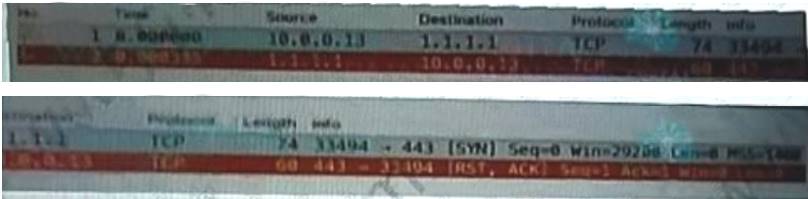
- A. The remote server is not responding because it is down
- B. The client machine is not 'connected to the internet
- C. The client machine's DNS is configured incorrectly
- D. The remote server is actively rejecting the connection
Answer: D
NEW QUESTION 13
An administrator deploys a site in which the load balancer only sees the ingress traffic from the client All
egress traffic from the server bypasses the load balancer. Which type of solution is this?
- A. packet forwarding architecture
- B. delayed binding
- C. switching
- D. Full proxy architecture
Answer: A
NEW QUESTION 14
A load balancer receives a TCP SYN packet from a client and immediately sends the packet on to a server. This is an example of which type of solution?
- A. packet forwarding architecture
- B. Full proxy architecture
- C. TCP compression
- D. TCP optimization
Answer: A
NEW QUESTION 15
A BIG IP virtual Server with an IP address of 10.100.43.108 must be available to public internet users. Which technology should be used to achieve this task?
- A. NDP
- B. DNS
- C. NAT
- D. ARP
Answer: C
Explanation:
10 x.x.x/8 is an RFC 1918 reserved private IP address. It must be NATted from a publicly accessible IP for access from the internet
NEW QUESTION 16
In IPv4 the loopback IP is 127 0.0.1. or IPv6, what is the loopback address?
- A. FEBO::1
- B. FF8Q 0.0 : :1
- C. 2001 :: 127 : : 1
- D. : : 1
Answer: D
NEW QUESTION 17
What is an advantage of a packet forwarding architecture?
- A. allows for manipulation of HTTP headers
- B. allows for SSL offload
- C. reduces latency
- D. handles larger packet sizes
Answer: C
NEW QUESTION 18
Layer 2 mapping information is announced by an interface without receiving a request for the mapping first. Which term describes this event?
- A. ICMP
- B. STP
- C. gratuitous ARP
- D. ARP
Answer: C
NEW QUESTION 19
A BIG IP Administrator wants to add a new VLAN (VLAN 40) to an LACP trunk (named LACP01) connected to the BIG-IP device Mufti VLANS exist on LACPO1.Which TMSH command should the BIGIP Administrator issue to add the new VLAN to the existing LACP trunk?
- A. create net vlan VLAN40 (interfaces add (LACP01 {lagged)) tag 40}
- B. create net vlan VLAN40 {interfaces replace-all-with {LACP01{tagged}} tag 40}
- C. create net vlan VLAN40 interfaces replace all with {LACP01 {untagged)} tag 40}
- D. create net vlan VLAN40 {interfaces add {LACP01 {untagged}} tag 40}
Answer: B
NEW QUESTION 20
Which two protocol are used for the retrieval of email? (Choose two)
- A. ICAP
- B. SMTP
- C. IMAP
- D. POP3
- E. SNMP
Answer: CD
NEW QUESTION 21
......
P.S. Easily pass 101 Exam with 240 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader 101 Dumps: https://www.certleader.com/101-dumps.html (240 New Questions)
