156-215.77 Exam
Check Point 156-215.77 Dumps Questions 2021

Your success in checkpoint 156 215.77 is our sole target and we develop all our 156 215.77 pdf in a way that facilitates the attainment of this target. Not only is our checkpoint 156 215.77 material the best you can find, it is also the most detailed and the most updated. exam 156 215.77 for Check Point 156-215.77 are written to the highest standards of technical accuracy.
Check Point 156-215.77 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which feature in R77 permits blocking specific IP addresses for a specified time period?
- A. Suspicious Activity Monitoring
- B. HTTP Methods
- C. Local Interface Spoofing
- D. Block Port Overflow
Answer: A
NEW QUESTION 2
Your company has two headquarters, one in London, one in New York. Each of the headquarters includes several branch offices. The branch offices only need to communicate with the headquarters in their country, not with each other, and the headquarters need to communicate directly. What is the BEST configuration for establishing VPN Communities among the branch offices and their headquarters, and between the two headquarters? VPN Communities comprised of:
- A. Three mesh Communities: one for London headquarters and its branches; one for New York headquarters and its branches; and one for London and New York headquarters.
- B. Two mesh and one star Community: Each mesh Community is set up for each site between headquarters their branche
- C. The star Community has New York as the center and London as its satellite.
- D. Two star communities and one mesh: A star community for each city with headquarters as center, and branches as satellite
- E. Then one mesh community for the two headquarters.
- F. One star Community with the option to mesh the center of the star: New York and London Gateways added to the center of the star with the “mesh center Gateways? option checked; all London branch offices defined in one satellite window; but, all New York branch offices defined in another satellite window.
Answer: C
NEW QUESTION 3
In SmartDashboard, you configure 45 MB as the required free hard-disk space to accommodate logs. What can you do to keep old log files, when free space falls below 45 MB?
- A. Do nothin
- B. Old logs are deleted, until free space is restored.
- C. Use the command fwm logexport to export the old log files to another location.
- D. Configure a script to run fw logswitch and SCP the output file to a separate file server.
- E. Do nothin
- F. The Security Management Server automatically copies old logs to a backup server before purging.
Answer: C
NEW QUESTION 4
The technical-support department has a requirement to access an intranet server. When configuring a User Authentication rule to achieve this, which of the following should you remember?
- A. You can only use the rule for Telnet, FTP, SMTP, and rlogin services.
- B. The Security Gateway first checks if there is any rule that does not require authentication for this type of connection before invoking the Authentication Security Server.
- C. Once a user is first authenticated, the user will not be prompted for authentication again until logging out.
- D. You can limit the authentication attempts in the User Properties’ Authentication tab.
Answer: B
NEW QUESTION 5
You are responsible for the configuration of MegaCorp’s Check Point Firewall. You need to allow two NAT rules to match a connection. Is it possible? Give the BEST answer.
- A. No, it is not possible to have more than one NAT rule matching a connectio
- B. When the firewall receives a packet belonging to a connection, it compares it against the first rule in the Rule Base, then the second rule, and so o
- C. When it finds a rule that matches, it stops checking and applies that rule.
- D. Yes, it is possible to have two NAT rules which match a connection, but only in using Manual NAT (bidirectional NAT).
- E. Yes, there are always as many active NAT rules as there are connections.
- F. Yes, it is possible to have two NAT rules which match a connection, but only when using Automatic NAT (bidirectional NAT).
Answer: D
NEW QUESTION 6
What information is found in the SmartView Tracker Management log?
- A. SIC revoke certificate event
- B. Destination IP address
- C. Most accessed Rule Base rule
- D. Number of concurrent IKE negotiations
Answer: A
NEW QUESTION 7
Your primary Security Gateway runs on GAiA. What is the easiest way to back up your Security Gateway R77 configuration, including routing and network configuration files?
- A. Copying the directories $FWDIR/conf and $FWDIR/lib to another location.
- B. Using the native GAiA backup utility from command line or in the Web based user interface.
- C. Using the command upgrade_export.
- D. Run the pre_upgrade_verifier and save the .tgz file to the directory /temp.
Answer: B
NEW QUESTION 8
Your manager requires you to setup a VPN to a new business partner site. The administrator from the partner site gives you his VPN settings and you notice that he setup AES 128 for IKE phase 1 and AES 256 for IKE phase 2. Why is this a problematic setup?
- A. The two algorithms do not have the same key length and so don’t work togethe
- B. You will get the error …. No proposal chosen….
- C. All is fine as the longest key length has been chosen for encrypting the data and a shorter key length for higher performance for setting up the tunnel.
- D. Only 128 bit keys are used for phase 1 keys which are protecting phase 2, so the longer key length in phase 2 only costs performance and does not add security due to a shorter key in phase 1.
- E. All is fine and can be used as is.
Answer: C
NEW QUESTION 9
Which SmartView Tracker selection would most effectively show who installed a Security Policy blocking all traffic from the corporate network?
- A. Management tab
- B. Custom filter
- C. Network and Endpoint tab
- D. Active tab
Answer: A
NEW QUESTION 10
NAT can NOT be configured on which of the following objects?
- A. HTTP Logical Server
- B. Gateway
- C. Address Range
- D. Host
Answer: A
NEW QUESTION 11
Which command line interface utility allows the administrator to verify the Security Policy name and timestamp currently installed on a firewall module?
- A. cpstat fwd
- B. fw ver
- C. fw stat
- D. fw ctl pstat
Answer: C
NEW QUESTION 12
Why should the upgrade_export configuration file (.tgz) be deleted after you complete the import process?
- A. SmartUpdate will start a new installation process if the machine is rebooted.
- B. It will prevent a future successful upgrade_export since the .tgz file cannot be overwritten.
- C. It contains your security configuration, which could be exploited.
- D. It will conflict with any future upgrades when using SmartUpdate.
Answer: C
NEW QUESTION 13
You manage a global network extending from your base in Chicago to Tokyo, Calcutta and Dallas. Management wants a report detailing the current software level of each Enterprise class Security Gateway. You plan to take the opportunity to create a proposal outline, listing the most cost-effective way to upgrade your Gateways.
Which two SmartConsole applications will you use to create this report and outline?
- A. SmartView Tracker and SmartView Monitor
- B. SmartLSM and SmartUpdate
- C. SmartDashboard and SmartView Tracker
- D. SmartView Monitor and SmartUpdate
Answer: D
NEW QUESTION 14
Which R77 SmartConsole tool would you use to verify the installed Security Policy name on a Security Gateway?
- A. SmartView Monitor
- B. SmartUpdate
- C. SmartView Status
- D. None, SmartConsole applications only communicate with the Security Management Server.
Answer: A
NEW QUESTION 15
You are a Security Administrator using one Security Management Server managing three different firewalls. One firewall does NOT show up in the dialog box when attempting to install a Security Policy. Which of the following is a possible cause?
- A. The firewall has failed to sync with the Security Management Server for 60 minutes.
- B. The firewall object has been created but SIC has not yet been established.
- C. The firewall is not listed in the Policy Installation Targets screen for this policy package.
- D. The license for this specific firewall has expired.
Answer: C
NEW QUESTION 16
Exhibit: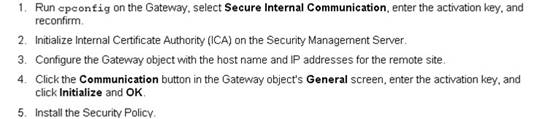
You installed Security Management Server on a computer using GAiA in the MegaCorp home office. You use IP address 10.1.1.1. You also installed the Security Gateway on a second GAiA computer, which you plan to ship to another Administrator at a MegaCorp hub office.
What is the correct order for pushing SIC certificates to the Gateway before shipping it?
- A. 2, 3, 4, 1, 5
- B. 2, 1, 3, 4, 5
- C. 1, 3, 2, 4, 5
- D. 2, 3, 4, 5, 1
Answer: B
NEW QUESTION 17
One of your remote Security Gateway’s suddenly stops sending logs, and you cannot install the Security Policy on the Gateway. All other remote Security Gateways are logging normally to the Security Management Server, and Policy installation is not affected. When you click the Test SIC status button in the problematic Gateway object, you receive an error message. What is the problem?
- A. The remote Gateway's IP address has changed, which invalidates the SIC Certificate.
- B. The time on the Security Management Server’s clock has changed, which invalidates the remote Gateway's Certificate.
- C. The Internal Certificate Authority for the Security Management Server object has been removed from objects_5_0.C.
- D. There is no connection between the Security Management Server and the remote Gatewa
- E. Rules or routing may block the connection.
Answer: D
NEW QUESTION 18
The INSPECT engine inserts itself into the kernel between which two OSI model layers?
- A. Session and Transport
- B. Physical and Data
- C. Presentation and Application
- D. Datalink and Network
Answer: D
NEW QUESTION 19
Which of the following objects is a valid source in an authentication rule?
- A. Host@Any
- B. User@Network
- C. User_group@Network
- D. User@Any
Answer: C
NEW QUESTION 20
You want to configure a mail alert for every time the policy is installed to a specific Gateway.
Where would you configure this alert?
- A. In SmartView Monitor, select Gateway > Configure Thresholds and in SmartDashboard select Global Properties > Log and Alerts > Alert Commands.
- B. In SmartDashboard, select Global Properties > Log and Alerts > Alert Commands.
- C. You cannot create a mail alert for Policy installation.
- D. In SmartView Monitor, select Gateway > Configure Thresholds.
Answer: A
P.S. Certleader now are offering 100% pass ensure 156-215.77 dumps! All 156-215.77 exam questions have been updated with correct answers: https://www.certleader.com/156-215.77-dumps.html (388 New Questions)
