156-315.80 Exam
Improve Check Point Certified Security Expert - R80 156-315.80 Exam Dumps

we provide Download Check-Point 156-315.80 dumps which are the best for clearing 156-315.80 test, and to get certified by Check-Point Check Point Certified Security Expert - R80. The 156-315.80 Questions & Answers covers all the knowledge points of the real 156-315.80 exam. Crack your Check-Point 156-315.80 Exam with latest dumps, guaranteed!
Also have 156-315.80 free dumps questions for you:
NEW QUESTION 1
Which of the following process pulls application monitoring status?
- A. fwd
- B. fwm
- C. cpwd
- D. cpd
Answer: D
NEW QUESTION 2
What is true of the API server on R80.10?
- A. By default the API-server is activated and does not have hardware requirements.
- B. By default the API-server is not active and should be activated from the WebUI.
- C. By default the API server is active on management and stand-alone servers with 16GB of RAM (or more).
- D. By default, the API server is active on management servers with 4 GB of RAM (or more) and on stand-alone servers with 8GB of RAM (or more).
Answer: D
NEW QUESTION 3
What API command below creates a new host with the name “New Host” and IP address of “192.168.0.10”?
- A. new host name “New Host” ip-address “192.168.0.10”
- B. set host name “New Host” ip-address “192.168.0.10”
- C. create host name “New Host” ip-address “192.168.0.10”
- D. add host name “New Host” ip-address “192.168.0.10”
Answer: D
NEW QUESTION 4
View the rule below. What does the lock-symbol in the left column mean? (Choose the BEST answer.)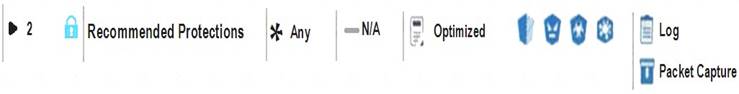
- A. The current administrator has read-only permissions to Threat Prevention Policy.
- B. Another user has locked the rule for editing.
- C. Configuration lock is presen
- D. Click the lock symbol to gain read-write access.
- E. The current administrator is logged in as read-only because someone else is editing the policy.
Answer: B
Explanation:
https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_
NEW QUESTION 5
During inspection of your Threat Prevention logs you find four different computers having one event each with a Critical Severity. Which of those hosts should you try to remediate first?
- A. Host having a Critical event found by Threat Emulation
- B. Host having a Critical event found by IPS
- C. Host having a Critical event found by Antivirus
- D. Host having a Critical event found by Anti-Bot
Answer: D
NEW QUESTION 6
After the initial installation on Check Point appliance, you notice that the Management-interface and default gateway are incorrect.
Which commands could you use to set the IP to 192.168.80.200/24 and default gateway to 192.168.80.1.
- A. set interface Mgmt ipv4-address 192.168.80.200 mask-length 24set static-route default nexthop gateway address 192.168.80.1 onsave config
- B. set interface Mgmt ipv4-address 192.168.80.200 255.255.255.0add static-route 0.0.0.0. 0.0.0.0 gw 192.168.80.1 onsave config
- C. set interface Mgmt ipv4-address 192.168.80.200 255.255.255.0set static-route 0.0.0.0. 0.0.0.0 gw 192.168.80.1 onsave config
- D. set interface Mgmt ipv4-address 192.168.80.200 mask-length 24add static-route default nexthop gateway address 192.168.80.1 onsave config
Answer: A
NEW QUESTION 7
What is the correct command to observe the Sync traffic in a VRRP environment?
- A. fw monitor –e “accept[12:4,b]=224.0.0.18;”
- B. fw monitor –e “accept port(6118;”
- C. fw monitor –e “accept proto=mcVRRP;”
- D. fw monitor –e “accept dst=224.0.0.18;”
Answer: D
NEW QUESTION 8
To enable Dynamic Dispatch on Security Gateway without the Firewall Priority Queues, run the following command in Expert mode and reboot:
- A. fw ctl Dyn_Dispatch on
- B. fw ctl Dyn_Dispatch enable
- C. fw ctl multik set_mode 4
- D. fw ctl multik set_mode 1
Answer: C
NEW QUESTION 9
You are asked to check the status of several user-mode processes on the management server and gateway. Which of the following processes can only be seen on a Management Server?
- A. fwd
- B. fwm
- C. cpd
- D. cpwd
Answer: B
NEW QUESTION 10
When a packet arrives at the gateway, the gateway checks it against the rules in the hop Policy Layer, sequentially from top to bottom, and enforces the first rule that matches a packet. Which of the following statements about the order of rule enforcement is true?
- A. If the Action is Accept, the gateway allows the packet to pass through the gateway.
- B. If the Action is Drop, the gateway continues to check rules in the next Policy Layer down.
- C. If the Action is Accept, the gateway continues to check rules in the next Policy Layer down.
- D. If the Action is Drop, the gateway applies the Implicit Clean-up Rule for that Policy Layer.
Answer: C
NEW QUESTION 11
The fwd process on the Security Gateway sends logs to the fwd process on the Management Server via which 2 processes?
- A. fwd via cpm
- B. fwm via fwd
- C. cpm via cpd
- D. fwd via cpd
Answer: A
NEW QUESTION 12
When installing a dedicated R80 SmartEvent server. What is the recommended size of the root partition?
- A. Any size
- B. Less than 20GB
- C. More than 10GB and less than 20GB
- D. At least 20GB
Answer: D
NEW QUESTION 13
What is the minimum amount of RAM needed for a Threat Prevention Appliance?
- A. 6 GB
- B. 8GB with Gaia in 64-bit mode
- C. 4 GB
- D. It depends on the number of software blades enabled
Answer: C
NEW QUESTION 14
When Dynamic Dispatcher is enabled, connections are assigned dynamically with the exception of:
- A. Threat Emulation
- B. HTTPS
- C. QOS
- D. VoIP
Answer: D
NEW QUESTION 15
What is the main difference between Threat Extraction and Threat Emulation?
- A. Threat Emulation never delivers a file and takes more than 3 minutes to complete.
- B. Threat Extraction always delivers a file and takes less than a second to complete.
- C. Threat Emulation never delivers a file that takes less than a second to complete.
- D. Threat Extraction never delivers a file and takes more than 3 minutes to complete.
Answer: B
NEW QUESTION 16
What command can you use to have cpinfo display all installed hotfixes?
- A. cpinfo -hf
- B. cpinfo –y all
- C. cpinfo –get hf
- D. cpinfo installed_jumbo
Answer: B
NEW QUESTION 17
What is the protocol and port used for Health Check and State Synchronization in ClusterXL?
- A. CCP and 18190
- B. CCP and 257
- C. CCP and 8116
- D. CPC and 8116
Answer: C
NEW QUESTION 18
On R80.10 the IPS Blade is managed by:
- A. Threat Protection policy
- B. Anti-Bot Blade
- C. Threat Prevention policy
- D. Layers on Firewall policy
Answer: C
NEW QUESTION 19
......
Thanks for reading the newest 156-315.80 exam dumps! We recommend you to try the PREMIUM 2passeasy 156-315.80 dumps in VCE and PDF here: https://www.2passeasy.com/dumps/156-315.80/ (428 Q&As Dumps)
