156-915.77 Exam
100% Correct CheckPoint 156-915.77 Testing Material Online

We provide real 156-915.77 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass CheckPoint 156-915.77 Exam quickly & easily. The 156-915.77 PDF type is available for reading and printing. You can print more and practice many times. With the help of our CheckPoint 156-915.77 dumps pdf and vce product and material, you can easily pass the 156-915.77 exam.
Check 156-915.77 free dumps before getting the full version:
NEW QUESTION 1
Complete this statement from the options provided. Using Captive Portal, unidentified users may be either; blocked, allowed to enter required credentials, or required to download the___.
- A. Identity Awareness Agent
- B. Full Endpoint Client
- C. ICA Certificate
- D. SecureClient
Answer: A
NEW QUESTION 2
Assume you are a Security Administrator for ABCTech. You have allowed authenticated access to users from Mkting_net to Finance_net. But in the user’s properties, connections are only permitted within Mkting_net. What is the BEST way to resolve this conflict?
- A. Select Ignore Database in the Action Properties window.
- B. Permit access to Finance_net.
- C. Select Intersect with user database in the Action Properties window.
- D. Select Intersect with user database or Ignore Database in the Action Properties window.
Answer: D
NEW QUESTION 3
Users with Identity Awareness Agent installed on their machines login with , so that when the user logs into the domain, that information is also used to meet Identity Awareness credential requests.
- A. Key-logging
- B. ICA Certificates
- C. SecureClient
- D. Single Sign-On
Answer: D
NEW QUESTION 4
Which of the following allows administrators to allow or deny traffic to or from a specific network based on the user’s credentials?
- A. Access Policy
- B. Access Role
- C. Access Rule
- D. Access Certificate
Answer: B
NEW QUESTION 5
What is Check Point's CoreXL?
- A. A way to synchronize connections across cluster members
- B. TCP-18190
- C. Multiple core interfaces on the device to accelerate traffic
- D. Multi Core support for Firewall Inspection
Answer: D
NEW QUESTION 6
Match the following commands to their correct function.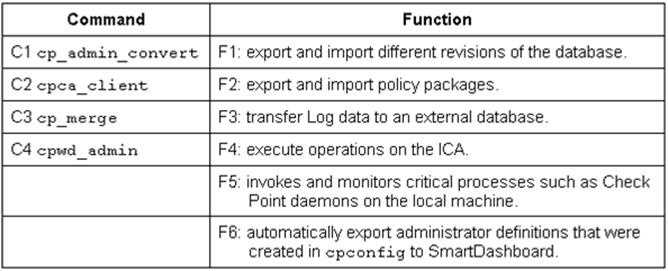
Each command has one function only listed.
- A. C1>F6; C2>F4; C3>F2; C4>F5
- B. C1>F2; C2>F1; C3>F6; C4>F4
- C. C1>F2; C2>F4; C3>F1; C4>F5
- D. C1>F4; C2>F6; C3>F3; C4>F2
Answer: A
NEW QUESTION 7
Update the topology in the cluster object.
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 8
Which Security Gateway R77 configuration setting forces the Client Authentication authorization time-out to refresh, each time a new user is authenticated? The:
- A. Time properties, adjusted on the user objects for each user, in the Client Authentication rule Source.
- B. IPS > Application Intelligence > Client Authentication > Refresh User Timeout option enabled.
- C. Refreshable Timeout setting, in Client Authentication Action Properties > Limits.
- D. Global Properties > Authentication parameters, adjusted to allow for Regular Client Refreshment.
Answer: C
NEW QUESTION 9
CORRECT TEXT
Fill in the blanks. To view the number of concurrent connections going through core 0 on the firewall, you would use the command and syntax _____.
Solution:
fw –i 0 tab –t connections –s
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 10
Which operating systems are supported by a Check Point Security Gateway on an open server? Select MOST complete list.
- A. Sun Solaris, Red Hat Enterprise Linux, Check Point SecurePlatform, IPSO, Microsoft Windows
- B. Check Point GAiA and SecurePlatform, and Microsoft Windows
- C. Check Point GAiA, Microsoft Windows, Red Hat Enterprise Linux, Sun Solaris, IPSO
- D. Check Point GAiA and SecurePlatform, IPSO, Sun Solaris, Microsoft Windows
Answer: B
NEW QUESTION 11
Which of the following authentication methods can be configured in the Identity Awareness setup wizard?
- A. Check Point Password
- B. TACACS
- C. LDAP
- D. Windows password
Answer: C
NEW QUESTION 12
CORRECT TEXT
To provide full connectivity upgrade status, use command
Solution:
cphaprob fcustat
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 13
Which of the following is the preferred method for adding static routes in GAiA?
- A. In the CLI with the command “route add”
- B. In Web Portal, under Network Management > IPv4 Static Routes
- C. In the CLI via sysconfig
- D. In SmartDashboard under Gateway Properties > Topology
Answer: B
NEW QUESTION 14
Configure the new interface via sysconfig from the "non-member" Gateway.
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 15
Your organization maintains several IKE VPN’s. Executives in your organization want to know which mechanism Security Gateway R77 uses to guarantee the authenticity and integrity of messages. Which technology should you explain to the executives?
- A. Certificate Revocation Lists
- B. Application Intelligence
- C. Key-exchange protocols
- D. Digital signatures
Answer: D
NEW QUESTION 16
Select the command set best used to verify proper failover function of a new ClusterXL configuration.
- A. reboot
- B. cphaprob -d failDevice -s problem -t 0 register / cphaprob -d failDevice unregister
- C. clusterXL_admin down / clusterXL_admin up
- D. cpstop/cpstart
Answer: C
NEW QUESTION 17
CORRECT TEXT
Fill in the blank with a numeric value. The default port number for Secure Sockets Layer (SSL) connections with the LDAP Server is
Solution:
636
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 18
Your organization’s disaster recovery plan needs an update to the backup and restore section to reap the new distributed R77 installation benefits. Your plan must meet the following required and desired objectives:
Required Objective: The Security Policy repository must be backed up no less frequently than every 24 hours.
Desired Objective: The R77 components that enforce the Security Policies should be backed up at least once a week.
Desired Objective: Back up R77 logs at least once a week.
Your disaster recovery plan is as follows:
- Use the cron utility to run the command upgrade_export each night on the Security Management Servers.
- Configure the organization's routine back up software to back up the files created by the command upgrade_export.
- Configure the GAiA back up utility to back up the Security Gateways every Saturday night.
- Use the cron utility to run the command upgrade_export each Saturday night on the log servers.
- Configure an automatic, nightly logswitch.
- Configure the organization's routine back up software to back up the switched logs every night.
Upon evaluation, your plan:
- A. Meets the required objective and only one desired objective.
- B. Meets the required objective but does not meet either desired objective.
- C. Does not meet the required objective.
- D. Meets the required objective and both desired objectives.
Answer: D
NEW QUESTION 19
......
Thanks for reading the newest 156-915.77 exam dumps! We recommend you to try the PREMIUM Certshared 156-915.77 dumps in VCE and PDF here: https://www.certshared.com/exam/156-915.77/ (203 Q&As Dumps)
