202-450 Exam
Downloadable 202-450 Study Guides 2021

Act now and download your LPI 202-450 test today! Do not waste time for the worthless LPI 202-450 tutorials. Download Latest LPI LPIC-2 Exam 202 Part 2 of 2 version 4.5 exam with real questions and answers and begin to learn LPI 202-450 with a classic professional.
Online LPI 202-450 free dumps demo Below:
NEW QUESTION 1
Which of the following OpenVPN configuration options makes OpenVPN forward network packets between VPN clients itself instead of passing the packets on to the Linux host which runs the OpenVPN server for further processing?
- A. inter-client-traffic
- B. client-to-client
- C. client-router
- D. client-pass
- E. grant-client-traffic
Answer: B
NEW QUESTION 2
How must Samba be configured such that it can check CIFS passwords against those found in
/etc/passwd and /etc/shadow?
- A. Set the parameters “encrypt passwords = yes” and “password file = /etc/passwd”
- B. Set the parameters “encrypt passwords = yes”, “password file = /etc/passwd” and “password algorithm = crypt”
- C. Delete the smbpasswd file and create a symbolic link to the passwd and shadow file
- D. It is not possible for Samba to use /etc/passwd and /etc/shadow directly
- E. Run smbpasswd to convert /etc/passwd and /etc/shadow to a Samba password file
Answer: D
NEW QUESTION 3
To allow X connections to be forwarded from or through an SSH server, what configuration keyword must be set to yes in the sshd configuration file?
- A. AllowForwarding
- B. ForwardingAllow
- C. XllForwardingAllow
- D. XllForwarding
Answer: D
NEW QUESTION 4
Which tool creates a Certificate Signing Request (CSR) for serving HTTPS with Apache HTTPD?
- A. apachect1
- B. certgen
- C. cartool
- D. httpsgen
- E. openssl
Answer: E
NEW QUESTION 5
Which of the following Samba services handles the membership of a file server in an Active Directory domain?
- A. winbindd
- B. nmbd
- C. msadd
- D. admemb
- E. samba
Answer: E
NEW QUESTION 6
Which of the following PAM modules allows the system administrator to use an arbitrary file containing a list of user and group names with restrictions on the system resources available to them?
- A. pam_filter
- B. pam_limits
- C. pam_listfile
- D. pam_unix
Answer: B
NEW QUESTION 7
Which of the following statements in the ISC DHCPD configuration is used to specify whether or not an address pool can be used by nodes which have a corresponding host section in the configuration?
- A. identified-nodes
- B. unconfigured-hosts
- C. missing-peers
- D. unmatched-hwaddr
- E. unknown-clients
Answer: E
NEW QUESTION 8
What is the name of the network security scanner project which, at the core, is a server with a set of network vulnerability tests?
- A. NetMap
- B. OpenVAS
- C. Smartscan
- D. Wireshark
Answer: B
NEW QUESTION 9
Which of the following nmap parameters scans a target for open TCP ports? (Choose two.)
- A. -sO
- B. -sZ
- C. -sT
- D. -sU
- E. -sS
Answer: CE
NEW QUESTION 10
In order to protect a directory on an Apache HTTPD web server with a password, this configuration was added to an .htaccess file in the respective directory: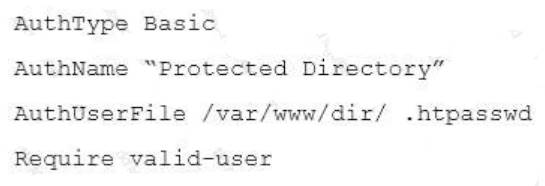
Furthermore, a file /var/www/dir/ .htpasswd was created with the following content: usera:S3cr3t
Given that all these files were correctly processed by the web server processes, which of the following statements is true about requests to the directory?
- A. The user usera can access the site using the password s3cr3t
- B. Accessing the directory as usera raises HTTP error code 442 (User Not Existent)
- C. Requests are answered with HTTP error code 500 (Internal Server Error)
- D. The browser prompts the visitor for a username and password but logins for usera do not seem to work
- E. The web server delivers the content of the directory without requesting authentication
Answer: A
NEW QUESTION 11
Using its standard configuration, how does fail2ban block offending SSH clients?
- A. By rejecting connections due to its role as a proxy in front of SSHD.
- B. By modifying and adjusting the SSHD configuration.
- C. By creating and maintaining netfilter rules.
- D. By creating null routes that drop any answer packets sent to the client.
- E. By modifying and adjusting the TCP Wrapper configuration for SSH
Answer: B
NEW QUESTION 12
In order to prevent all anonymous FTP users from listing uploaded file names, what security precaution can be taken when creating an upload directory?
- A. The directory must not have the execute permission set.
- B. The directory must not have the read permission set.
- C. The directory must not have the read or execute permission set.
- D. The directory must not have the write permission set.
- E. The directory must not contain other directorie
Answer: B
NEW QUESTION 13
Which keyword is used in the Squid configuration to define networks and times used to limit access to the service?
- A. acl
- B. allow
- C. http_allow
- D. permit
Answer: A
NEW QUESTION 14
Select the alternative that shows the correct way to disable a user login for all users except root.
- A. The use of the pam_block module along with the /etc/login configuration file.
- B. The use of the pam_deny module along with the /etc/deny configuration file.
- C. The use of the pam_pwdb module along with the /etc/pwdv.conf configuration file.
- D. The use of the pam_nologin module along with the /etc/nologin configuration fil
Answer: D
NEW QUESTION 15
Which of these sets of entries does the following command return?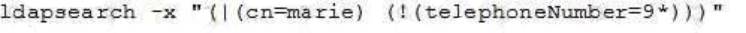
- A. Entries that don’t have a cn of marie or don’t have a telephoneNumber that begins with 9.
- B. Entries that have a cn of marie or don’t have a telephoneNumber beginning with 9.
- C. Entries that have a cn of marie and a telephoneNumber that ending with 9.
- D. Entries that don’t have a cn of marie and don’t have a telephoneNumber beginning with 9.
- E. Entries that have a cn of marie or have a telephoneNumber beginning with 9.
Answer: C
NEW QUESTION 16
Which of the following commands displays an overview of the Postfix queue content to help identify remote sites that are causing excessive mail traffic?
- A. mailtraf
- B. queuequery
- C. qshape
- D. postmap
- E. poststats
Answer: C
NEW QUESTION 17
Which of the following lines is valid in a configuration file in /etc/pam.d/?
- A. authrequired pam_unix.sotry_first_pass nullok
- B. authtry_first_pass nullok, require pam_unix.so
- C. authrequired:pam_unix.so(try_first_pass nullok)
- D. authpam_unix.so(required try_first_pass nullok)
Answer: A
NEW QUESTION 18
Which netfilter table contains built-in chains called INPUT, OUTPUT and FORWARD?
- A. ipconn
- B. filter
- C. nat
- D. default
- E. masq
Answer: B
NEW QUESTION 19
CORRECT TEXT
What command displays NFC kernel statistics? (Specify ONLY the command without any path or parameters.)
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
nfsstat
NEW QUESTION 20
A BIND server should be upgraded to use TSIG. Which configuration parameters should be added if the server should use the algorithm hmac-md5 and the key skrKc4DoTzi/takIlPi7JZA==?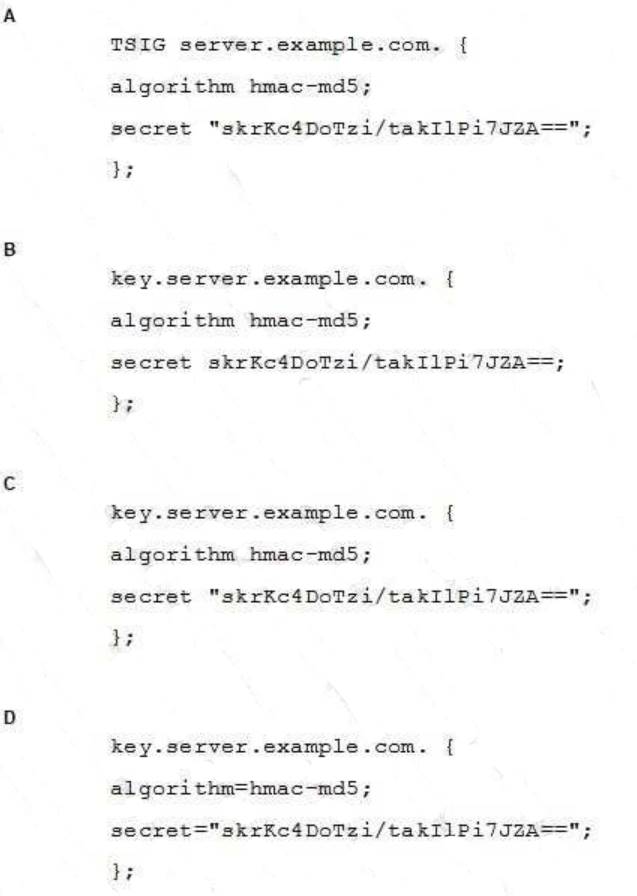
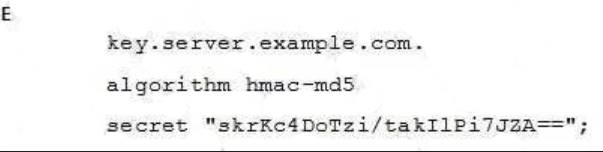
- A. Option A
- B. Option B
- C. Option C
- D. Option D
- E. Option E
Answer: C
NEW QUESTION 21
......
Thanks for reading the newest 202-450 exam dumps! We recommend you to try the PREMIUM prep-labs.com 202-450 dumps in VCE and PDF here: https://www.prep-labs.com/dumps/202-450/ (119 Q&As Dumps)
