300-210 Exam
Cisco 300-210 Exam Questions 2021

Want to know features? Want to lear more about experience? Study . Gat a success with an absolute guarantee to pass Cisco 300-210 (Implementing Cisco Threat Control Solutions (SITCS)) test on your first attempt.
Free 300-210 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
Which option is a benefit of Cisco Email Security virtual appliance over the Cisco ESA appliance?
- A. reduced space and power requirements
- B. outbound message protection
- C. automated administration
- D. global threat intelligence updates from Talos
Answer: A
NEW QUESTION 2
Which three functions can Cisco Application Visibility and Control perform within Cisco Cloud Web Security? (Choose three.)
- A. validation of malicious traffic
- B. traffic control
- C. extending Web Security to all computing devices
- D. application-level classification
- E. monitoring
- F. signature tuning
Answer: BDE
NEW QUESTION 3
Which Cisco technology secures the network through malware filtering, category-based control, and reputation-based control?
- A. Cisco ASA 5500 Series appliances
- B. Cisco remote-access VPNs
- C. Cisco IronPort WSA
- D. Cisco IPS
Answer: C
NEW QUESTION 4
When you configure the Cisco ESA to perform blacklisting, what are two items you can disable to enhance performance? (Choose two.)
- A. spam scanning
- B. antivirus scanning
- C. APT detection
- D. rootkit detection
Answer: AB
NEW QUESTION 5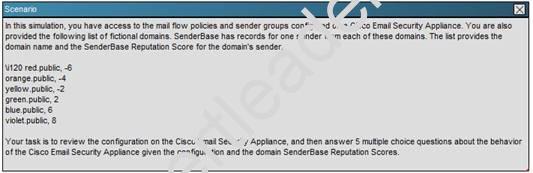
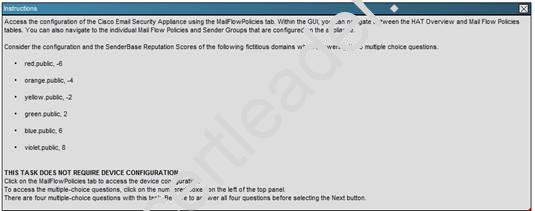
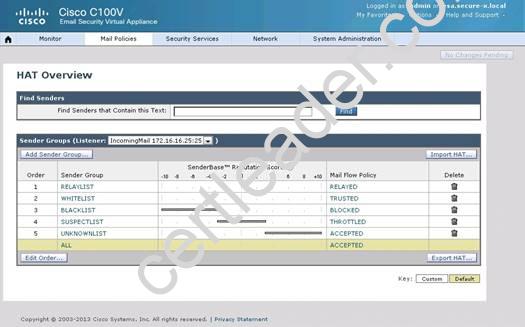
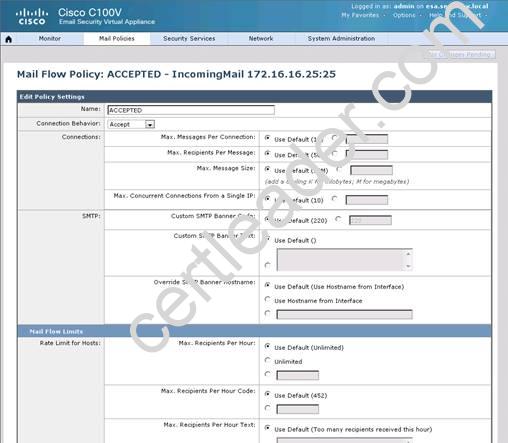
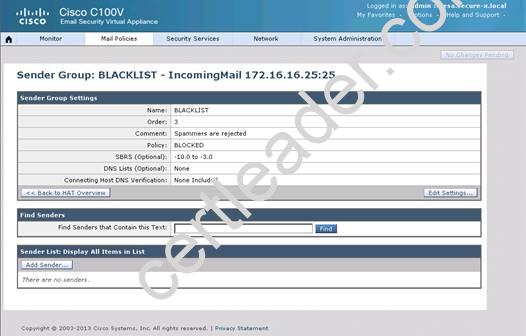
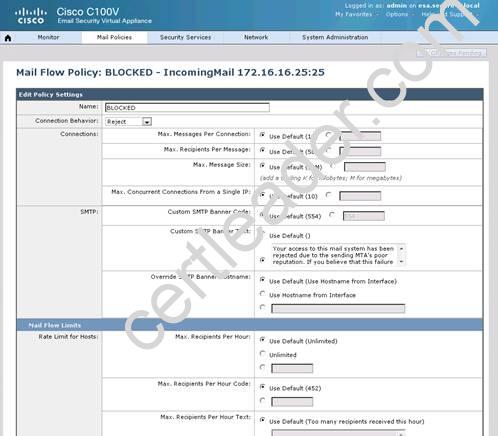
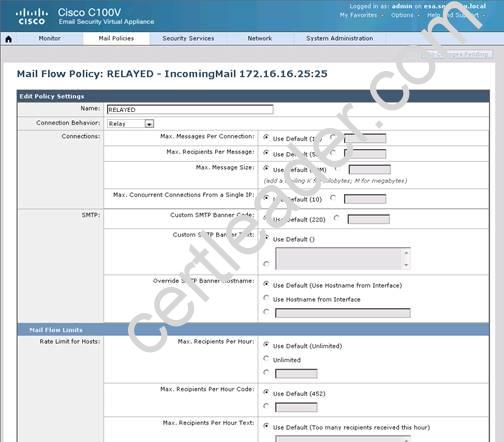
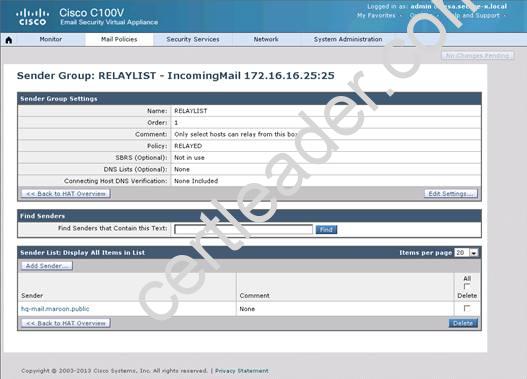
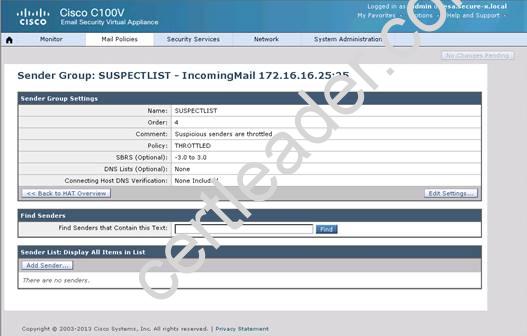
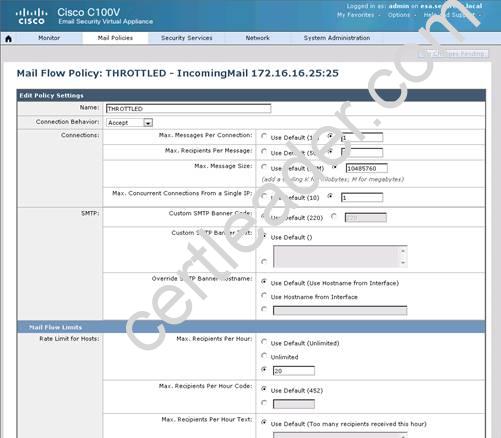
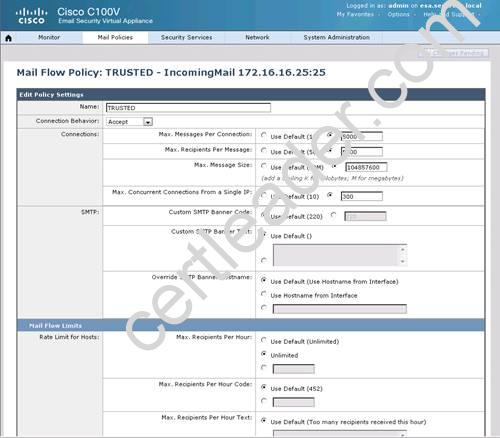
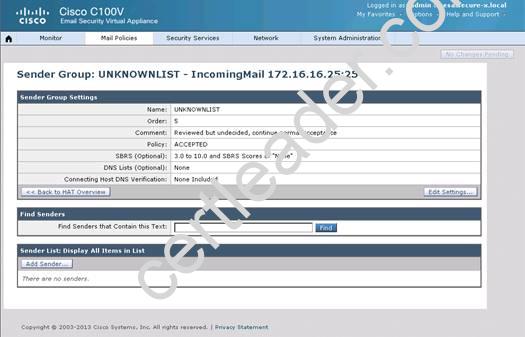
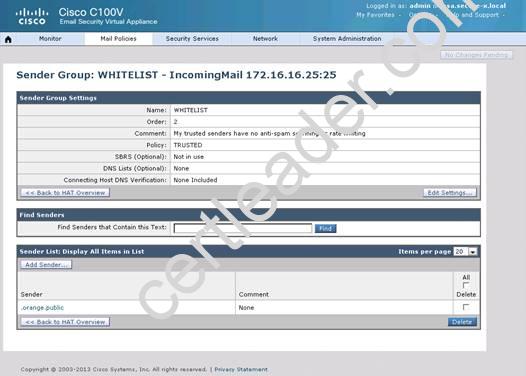
What is the maximum number of recipients per hour that the Cisco Email Security Appliance will accept from the green.public domain?
- A. 1
- B. 20
- C. 25
- D. 50
- E. 5000
- F. Unlimited
Answer: C
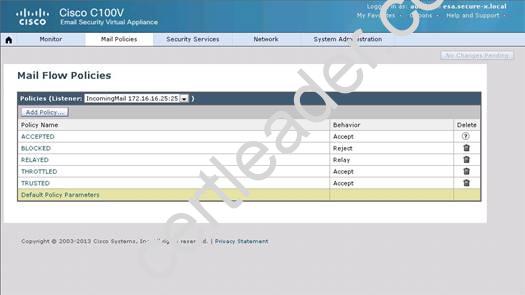
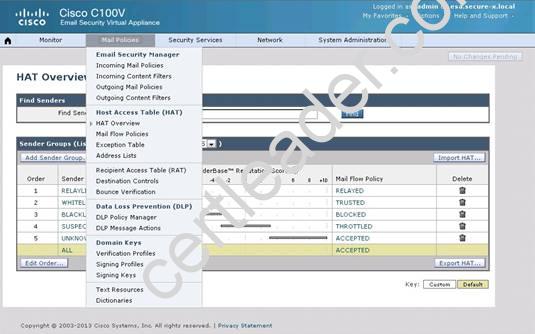
Explanation: From the instructions we know that the green.public domain has been assigned a reputation score of 2. From below we know that a reputation score of 2 belongs to the SUSPECTLIST, which has a policy of “THROTTLED”:
Capture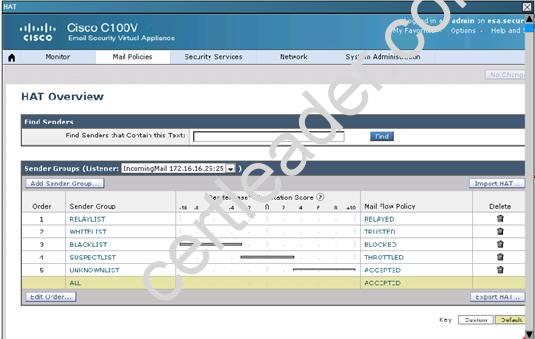
By clicking on the THROTTLED policy we see that the max recipients per hour has been set to 20: Capture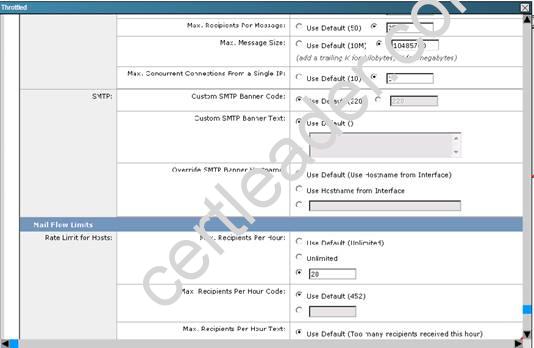
NEW QUESTION 6
Refer to the exhibit.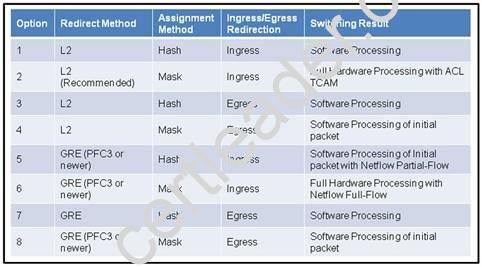
When designing the network to redirect web traffic utilizing the Catalyst 6500 to the Cisco Web Security Appliance, impact on the switch platform needs consideration. Which four rows identify the switch behavior in correlation to the redirect method? (Choose four.)
- A. Row 1
- B. Row 2
- C. Row 3
- D. Row 4
- E. Row 5
- F. Row 6
- G. Row 7
- H. Row 8
Answer: BCFG
NEW QUESTION 7
Exhibit:
Which configuration below would result in this output of the show server?
- A. Option A
- B. Option B
- C. Option C
Answer: C
NEW QUESTION 8
Which statement about the Cisco ASA botnet traffic filter is true?
- A. The four threat levels are low, moderate, high, and very high.
- B. By default, the dynamic-filter drop blacklist interface outside command drops traffic with a threat level of high or very high.
- C. Static blacklist entries always have a very high threat level.
- D. A static or dynamic blacklist entry always takes precedence over the static whitelist entry.
Answer: C
NEW QUESTION 9
Which command sets the number of packets to log on a Cisco IPS sensor?
- A. ip-log-count number
- B. ip-log-packets number
- C. ip-log-bytes number
- D. ip-log number
Answer: B
NEW QUESTION 10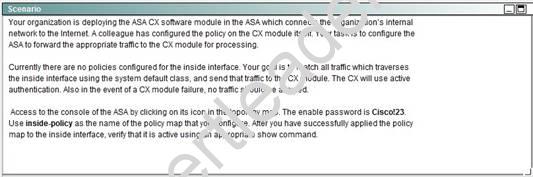
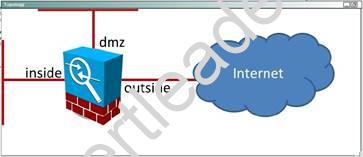
Answer:
Explanation: We need to create a policy map named inside-policy and send the traffic to the CXSC blade:
ASA-FW# config t
ASA-FW(config)# policy-map inside-policy
ASA-FW(config-pmap)# policy-map inside-policy ASA-FW(config-pmap)# class class-default
ASA-FW(config-pmap-c)# cxsc fail-close auth-proxy ASA-FW(config-pmap-c)# exit
ASA-FW(config-pmap)# exit
The fail-close is needed as per instructions that if the CX module fails, no traffic should be allowed. The auth-proxy keyword is needed for active authentication.
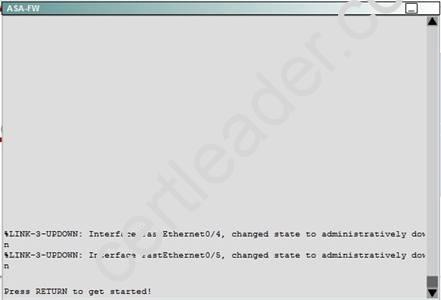
Next, we need to apply this policy map to the inside interface: ASA-FW(config)#service-policy inside-policy interface inside. Finally, verify that the policy is active:
ASA-FW# show service-policy interface inside Interface inside:
Service-policy: inside-policy Class-map: class-default
Default QueueingCXSC: card status Up, mode fail-close, auth-proxy enabled Packet input 181, packet output 183, drop 0, reset-drop 0, proxied 0 Configuration guidelines can be found at this reference link:
Reference:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa84/configuration/guide/asa_84_cli_config/modules_cx.pdf
NEW QUESTION 11
Which three statements about Cisco ASACX are true? (Choose three.)
- A. It groups multiple ASAs as a single logical device.
- B. It can perform context-aware inspection.
- C. It provides high-density security services with high availability.
- D. It uses policy-based interface controls to inspect and forward TCP- and UDP-based packets.
- E. It can make context-aware decisions.
- F. It uses four cooperative architectural constructs to build the firewall.
Answer: BEF
NEW QUESTION 12
What is the function of the Cisco Context Adaptive Scanning Engine in Cisco Hybrid Email Security services?
- A. It uses real-time traffic threat assessment to identify suspicious email senders and messages.
- B. It provides a preventive defense against viruses by scanning messages before they enter the network.
- C. It analyzes message content and attachments to protect an organization's intellectual property.
- D. It protects against blended threats by using human-like logic to review and evaluate traffic.
Answer: D
NEW QUESTION 13
Which statement describes a traffic profile on a Cisco Next Generation Intrusion Prevention System?
- A. It allows traffic if it does not meet the profile.
- B. It defines a traffic baseline for traffic anomaly deduction.
- C. It inspects hosts that meet the profile with more intrusion rules.
- D. It blocks traffic if it does not meet the profile.
Answer: B
NEW QUESTION 14
In a Cisco FirePOWER instrusion policy, which two event actions can be configured on a rule? (Choose two.)
- A. drop packet
- B. drop and generate
- C. drop connection
- D. capture trigger packet
- E. generate events
Answer: B
Explanation: Topic 2, Exam Set 2
NEW QUESTION 15
Which two Snort actions are available by default creating Snort rules, regardless of deployment mode? (Choose two)
- A. activate
- B. sdrop
- C. drop
- D. pass
- E. reject
Answer: AD
NEW QUESTION 16
Which piece of information is required to perform a policy trace for the Cisco WSA?
- A. the destination IP address of the trace
- B. the source IP address of the trace
- C. the URL to trace
- D. authentication credentials to make the request
Answer: C
NEW QUESTION 17
What are three features of the Cisco Security Intellishield Alert Manager Service? (Choose three.)
- A. validation of alerts by security analysts
- B. custom notifications
- C. complete threat and vulnerability remediation
- D. vendor-specific threat analysis
- E. workflow-management tools
- F. real-time threat and vulnerability mitigation
Answer: ABE
NEW QUESTION 18
Which type of interface do you configure to receive traffic from a switch or tap, promiscuously, on a cisco firePOWER device?
- A. inline set
- B. transparent
- C. Routed
- D. Passive
Answer: D
Thanks for reading the newest 300-210 exam dumps! We recommend you to try the PREMIUM 2passeasy 300-210 dumps in VCE and PDF here: https://www.2passeasy.com/dumps/300-210/ (431 Q&As Dumps)
