300-375 Exam
Virtual 300-375 Testing Bible 2021

Cause all that matters here is passing the Cisco 300-375 exam. Cause all that you need is a high score of 300-375 Securing Cisco Wireless Enterprise Networks exam. The only one thing you need to do is downloading Passleader 300-375 exam study guides now. We will not let you down with our money-back guarantee.
NEW QUESTION 1
An engineer with ID 338860948 is implementing Cisco Identity-Based Networking on a Cisco AireOS
controller. The engineer has two ACLs on the controller. The first ACL, named BASE_ACL, is applied to the corporate_clients interface on the WLC, which is used for all corporate clients. The second ACL, named HR_ACL, is referenced by ISE in the Human Resources group policy.
Which option is the resulting ACL when a Human Resources user connects?
- A. HR_ACL only
- B. HR_ACL appended with BASE_ACL
- C. BASE_ACL appended with HR_ACL
- D. BASE_ACL only
Answer: A
NEW QUESTION 2
While deploying PEAP authentication on a customer laptop with the native Windows supplicant, the PEAP security options do not appear. Which option describes what must be done?
- A. Enable automatic connection to the WLAN.
- B. Enable static DNS on the WLAN.
- C. Enable AES on the WLAN settings.
- D. Enable WLAN autoconfig services on the P
Answer: C
NEW QUESTION 3
A customer is concerned about DOS attacks from a neighboring facility. Which feature can be enabled to help alleviate these concerns and mitigate DOS attacks on a WLAN?
- A. PMF
- B. peer-to-peer blocking
- C. Cisco Centralized Key Management
- D. split tunnel
Answer: A
NEW QUESTION 4
An engineer is configuring a wireless network for local FlexConnect authentication. What three configurations are required for the WLC with WLAN 1 and AP Cisco? (Choose three.)
- A. config ap filexconnect vlan enable Cisco
- B. config wlan filexconnect vlan-central-switching 1 enable
- C. config ap filexconnect vlan wlan 1 Cisco
- D. config wlan filexconnect local-switching 1 enable
- E. config wlan filexconnect ap-auth 1 enable
- F. config ap mode filexconnect Cisco
Answer: ACD
NEW QUESTION 5
Clients are failing EAP authentication. A debug shows that an EAPOL start is sent and the clients are then de-authenticated. Which two issues can cause this problem? (Choose two.)
- A. The WLC certificate has changed.
- B. The WLAN is not configured for the correct EAP supplicant type.
- C. The shared secret of the WLC and RADIUS server do not match.
- D. The WLC has not been added to the RADIUS server as a client.
- E. The clients are configured for machine authentication, but the RADIUS server is configured for user authentication.
Answer: CD
NEW QUESTION 6
When you configure BYOD access to the network, you face increased security risks and challenges. Which challenge is resolved by deploying digital client certificates?
- A. managing the increase connected devices
- B. ensuring wireless LAN performance and reliability
- C. providing device choice and support
- D. enforcing company usage policies
Answer: D
NEW QUESTION 7
A wireless engineer wants to view how many wIPS alerts have been detected in Cisco Prime. Which tab does the engineer select in the wireless dashboard?
- A. Security
- B. Cleanair
- C. Context Aware
- D. Mesh
Answer: A
NEW QUESTION 8
Regarding the guidelines for using MFP, under what circumstances will a client without Cisco compatible Extensions v5 be able to associate to a WLAN?
- A. The DHCP Required box is unchecked.
- B. AAA override is configured for the WLAN
- C. Client MFP is disabled or optional.
- D. WPA2 is enabled with TKIP or AE
Answer: D
NEW QUESTION 9
Which three items must be configured on a Cisco WLC v7.0 to allow implementation of isolated bonding network? (Choose three.)
- A. RADIUS server IP address
- B. DHCP IP address
- C. SNMP trap receiver IP address
- D. interface name
- E. SNMP community name
- F. ACL name
Answer: ADF
NEW QUESTION 10
An engineer is configuring EAP-TLS with a client trusting server model and has configured a public root certification authority. Which action does this allow?
- A. specifies a second certification authority to trust
- B. utilizes two subcertification authority servers
- C. creates a PKI infrastructure
- D. validates the AAA server
Answer: D
Explanation:
To support EAP-TLS, the AAA server (for example, Cisco Secure ACS) must have a certificate. Either a public certification authority or a private certification authority can be used to issue the AAA server certificate. The AAA server will trust a client certificate that was issued from the same root
certification authority that issued its certificate.
https://www.cisco.com/en/US/tech/ CK7 22/ CK8 09/technologies_white_paper09186a008009256b.sht ml
NEW QUESTION 11
An engineer is adding APs to an existing VoWLAN to allow for location based services. Which option
will the primary change be to the network?
- A. increased transmit power on all APs
- B. moving to a bridging model
- C. AP footprint
- D. cell overlap would decrease
- E. triangulation of devices
Answer: C
NEW QUESTION 12
An engineer is preparing to implement a BYOD SSID at remote offices using local switching and wants to ensure that Wi-Fi Direct clients can communicate after the SSID is deployed. The engineer is planning on implementing the config wlan wifidirect allow 1 command. Which Wi-Fi Direct Client Policy consideration is applicable?
- A. Policy is applicable only with central switched WLANs on FlexConnect Aps.
- B. Policy is applicable only when P2P is set to disabled.
- C. Policy is applicable only to APs in FlexConnect mode only.
- D. Policy is applicable only on WLANs that have APs in local mode onl
Answer: A
NEW QUESTION 13
An engineer is configuring a new mobility anchor for a WLAN on the CLI with the config wlan mobility anchor add 3 10.10.10.10 command, but the command is failing. Which two conditions must be met to be able to enter this command? (Choose two.)
- A. The anchor controller IP address must be within the management interface subnet.
- B. The anchor controller must be in the same mobility group.
- C. The WLAN must be enabled.
- D. The mobility group keepalive must be configured.
- E. The indicated WLAN ID must be present on the controlle
Answer: AB
NEW QUESTION 14
802.1X AP supplicant credentials have been enabled and configured on a Cisco WLC v7.0 in both the respective Wireless>AP>Global Configuration location and AP>Credentials tab locations. What describes the 802.1X AP authentication process when connected via Ethernet to a switch?
- A. Only WLC AP global credentials are used.
- B. Only AP credentials are used.
- C. WLC global AP credentials are used first; upon failure, the AP credentials are used.
- D. AP credentials are used first; upon failure, the WLC global credentials are use
Answer: B
NEW QUESTION 15
What two actions must be taken by an engineer configuring wireless Identity-Based Networking for a WLAN to enable VLAN tagging? (Choose two.)
- A. enable AAA override on the WLAN
- B. create and apply the appropriate ACL to the WLAN
- C. update the RADIUS server attributes for tunnel type 64, medium type 65, and tunnel private group type 81
- D. configure RADIUS server with WLAN subnet and VLAN ID
- E. enable VLAN Select on the wireless LAN controller and the WLAN
Answer: AC
NEW QUESTION 16
Which two considerations must a network engineer have when planning for voice over wireless roaming? (Choose two.)
- A. Roaming with only 802.1x authentication requires full reauthentication.
- B. Full reauthentication introduces gaps in a voice conversation.
- C. Roaming occurs when e phone has seen at least four APs.
- D. Roaming occurs when the phone has reached -80 dBs or belo
Answer: AB
NEW QUESTION 17
Refer to the exhibit.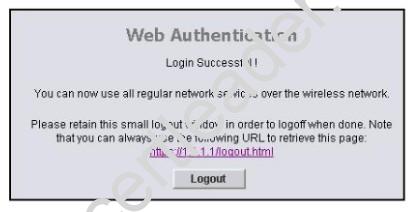
What is the 1.1.1.1 IP address?
- A. the wireless client IP address
- B. the RADIUS server IP address
- C. the controller management IP address
- D. the lightweight IP address
- E. the controller AP-manager IP address
- F. the controller virtual interface IP address
Answer: F
NEW QUESTION 18
Which feature should an engineer select to implement the use of VLAN tagging, QoS, and ACLs to clients based on RADIUS attributes?
- A. per-WLAN RADIUS source support
- B. client profiling
- C. AAA override
- D. captive bypassing
- E. identity-based networking
Answer: C
NEW QUESTION 19
Client Management Frame Protection is supported on which Cisco Compatible Extensions version clients?
- A. v2 and later
- B. v3 and later
- C. v4 and later
- D. v5 only
Answer: D
NEW QUESTION 20
Which command is an SNMPv3-specific command that an engineer can use only in Cisco IOS XE?
- A. snmp-server user remoteuser1 group1 remote 10.12.0.4
- B. snmp-server host 172.16.1.33 public
- C. snmp-server community comaccess ro 4
- D. snmp-server enable traps wireless
Answer: A
NEW QUESTION 21
A customer has deployed PEAP authentication with a Novell eDirectory LDAP Server. Which authentication method must be configured on the client to support this deployment?
- A. PEAP(EAP-MSCHAPv2)
- B. PEAP(EAP-TTLS)
- C. PEAP(EAP-GTC)
- D. PEAP(EAP-WPA)
Answer: C
NEW QUESTION 22
An engineer has configured the wireless controller to authenticate clients on the employee SSID against Microsoft Active Directory using PEAP authentication. Which protocol does the controller use to communicate with the authentication server?
- A. EAP
- B. 802.1x
- C. RADIUS
- D. WPA2
Answer: A
Explanation:
Define the Layer 2 Authentication as WPA2 so that the clients perform EAP-based authentication (PEAP-MS-CHAP v2 in this example) and use the advanced encryption standard (AES) as the encryption mechanism. Leave all other values at their defaults. https://www.cisco.com/c/en/us/support/docs/wireless/5500-series-wireless-controllers/115988-nps-wlc-config-000.html
NEW QUESTION 23
After receiving an alert regarding a rogue AP, a network engineer logs into Cisco Prime and looks at the floor map where the AP that detected the rogue is located. The map is synchronized with a mobility services engine that determines the rogue device is actually inside the campus. The engineer determines the rogue to be a security threat and decides to stop it from broadcasting inside the enterprise wireless network. What is the fastest way to disable the rogue?
- A. Go to the location the rogue device is indicated to be and disable the power.
- B. Create an SSID on WLAN controller resembling the SSID of the rogue to spoof it and disable clients from connecting to it.
- C. Classify the rogue as malicious in Cisco Prime.
- D. Update the status of the rogue in Cisco Prime to containe
Answer: C
NEW QUESTION 24
When a wireless client uses WPA2 AES, which keys are created at the end of the four way handshake process between the client and the access point?
- A. AES key, TKIP key, WEP key
- B. AES key, WPA2 key, PMK
- C. KCK, KEK, TK
- D. KCK, KEK, MIC key
Answer: A
NEW QUESTION 25
Which attribute on the Cisco WLC v7.0 does RADIUS IETF attribute "Tunnel-Private-Group ID" assign?
- A. ACL
- B. DSCP
- C. QoS
- D. VLAN
Answer: D
NEW QUESTION 26
......
P.S. Easily pass 300-375 Exam with 124 Q&As Exambible Dumps & pdf Version, Welcome to Download the Newest Exambible 300-375 Dumps: https://www.exambible.com/300-375-exam/ (124 New Questions)
