312-50v11 Exam
Update 312-50v11 Test For Certified Ethical Hacker Exam (CEH V11) Certification

Master the 312-50v11 Certified Ethical Hacker Exam (CEH v11) content and be ready for exam day success quickly with this Testking 312-50v11 exam engine. We guarantee it!We make it a reality and give you real 312-50v11 questions in our EC-Council 312-50v11 braindumps.Latest 100% VALID EC-Council 312-50v11 Exam Questions Dumps at below page. You can use our EC-Council 312-50v11 braindumps and pass your exam.
Also have 312-50v11 free dumps questions for you:
NEW QUESTION 1
CompanyXYZ has asked you to assess the security of their perimeter email gateway. From your office in New York, you craft a specially formatted email message and send it across the Internet to an employee of CompanyXYZ. The employee of CompanyXYZ is aware of your test. Your email message looks like this:
From: jim_miller@companyxyz.com
To: michelle_saunders@companyxyz.com Subject: Test message Date: 4/3/2017 14:37
The employee of CompanyXYZ receives your email message.
This proves that CompanyXYZ’s email gateway doesn’t prevent what?
- A. Email Masquerading
- B. Email Harvesting
- C. Email Phishing
- D. Email Spoofing
Answer: D
NEW QUESTION 2
A zone file consists of which of the following Resource Records (RRs)?
- A. DNS, NS, AXFR, and MX records
- B. DNS, NS, PTR, and MX records
- C. SOA, NS, AXFR, and MX records
- D. SOA, NS, A, and MX records
Answer: D
NEW QUESTION 3
Although FTP traffic is not encrypted by default, which layer 3 protocol would allow for end-to-end encryption of the connection?
- A. SFTP
- B. Ipsec
- C. SSL
- D. FTPS
Answer: B
NEW QUESTION 4
Joseph was the Web site administrator for the Mason Insurance in New York, who's main Web site was located at www.masonins.com. Joseph uses his laptop computer regularly to administer the Web site. One night, Joseph received an urgent phone call from his friend, Smith. According to Smith, the main Mason Insurance web site had been vandalized! All of its normal content was removed and replaced with an attacker's message ''Hacker Message: You are dead! Freaks!” From his office, which was directly connected to Mason Insurance's internal network, Joseph surfed to the Web site using his laptop. In his browser, the Web site looked completely intact.
No changes were apparent. Joseph called a friend of his at his home to help troubleshoot the problem. The Web site appeared defaced when his friend visited using his DSL connection. So, while Smith and his friend could see the defaced page, Joseph saw the intact Mason Insurance web site. To help make sense of this problem, Joseph decided to access the Web site using hisdial-up ISP. He disconnected his laptop from the corporate internal network and used his modem to dial up the same ISP used by Smith. After his modem connected, he quickly typed www.masonins.com in his browser to reveal the following web page: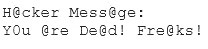
After seeing the defaced Web site, he disconnected his dial-up line, reconnected to the internal network, and used Secure Shell (SSH) to log in directly to the Web server. He ran Tripwire against the entire Web site, and determined that every system file and all the Web content on the server were intact. How did the attacker accomplish this hack?
- A. ARP spoofing
- B. SQL injection
- C. DNS poisoning
- D. Routing table injection
Answer: C
NEW QUESTION 5
Which system consists of a publicly available set of databases that contain domain name registration contact information?
- A. WHOIS
- B. CAPTCHA
- C. IANA
- D. IETF
Answer: A
NEW QUESTION 6
E- mail scams and mail fraud are regulated by which of the following?
- A. 18 U.S.
- B. pa
- C. 1030 Fraud and Related activity in connection with Computers
- D. 18 U.S.
- E. pa
- F. 1029 Fraud and Related activity in connection with Access Devices
- G. 18 U.S.
- H. pa
- I. 1362 Communication Lines, Stations, or Systems
- J. 18 U.S.
- K. pa
- L. 2510 Wire and Electronic Communications Interception and Interception of Oral Communication
Answer: A
NEW QUESTION 7
While using your bank’s online servicing you notice the following string in the URL bar:
“http: // www. MyPersonalBank. com/ account?id=368940911028389&Damount=10980&Camount=21”
You observe that if you modify the Damount & Camount values and submit the request, that data on the web page reflects the changes.
Which type of vulnerability is present on this site?
- A. Cookie Tampering
- B. SQL Injection
- C. Web Parameter Tampering
- D. XSS Reflection
Answer: C
NEW QUESTION 8
Which of the following are well known password-cracking programs?
- A. L0phtcrack
- B. NetCat
- C. Jack the Ripper
- D. Netbus
- E. John the Ripper
Answer: AE
NEW QUESTION 9
This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.
What is this attack?
- A. Cross-site-scripting attack
- B. SQL Injection
- C. URL Traversal attack
- D. Buffer Overflow attack
Answer: A
NEW QUESTION 10
Nedved is an IT Security Manager of a bank in his country. One day. he found out that there is a security breach to his company's email server based on analysis of a suspicious connection from the email server to an unknown IP Address.
What is the first thing that Nedved needs to do before contacting the incident response team?
- A. Leave it as it Is and contact the incident response te3m right away
- B. Block the connection to the suspicious IP Address from the firewall
- C. Disconnect the email server from the network
- D. Migrate the connection to the backup email server
Answer: C
NEW QUESTION 11
A bank stores and processes sensitive privacy information related to home loans. However, auditing has never been enabled on the system. What is the first step that the bank should take before enabling the audit feature?
- A. Perform a vulnerability scan of the system.
- B. Determine the impact of enabling the audit feature.
- C. Perform a cost/benefit analysis of the audit feature.
- D. Allocate funds for staffing of audit log review.
Answer: B
NEW QUESTION 12
You are analysing traffic on the network with Wireshark. You want to routinely run a cron job which will run the capture against a specific set of IPs - 192.168.8.0/24. What command you would use?
- A. wireshark --fetch ''192.168.8*''
- B. wireshark --capture --local masked 192.168.8.0 ---range 24
- C. tshark -net 192.255.255.255 mask 192.168.8.0
- D. sudo tshark -f''net 192 .68.8.0/24''
Answer: D
NEW QUESTION 13
OpenSSL on Linux servers includes a command line tool for testing TLS. What is the name of the tool and the correct syntax to connect to a web server?
- A. openssl s_client -site www.website.com:443
- B. openssl_client -site www.website.com:443
- C. openssl s_client -connect www.website.com:443
- D. openssl_client -connect www.website.com:443
Answer: C
NEW QUESTION 14
John the Ripper is a technical assessment tool used to test the weakness of which of the following?
- A. Passwords
- B. File permissions
- C. Firewall rulesets
- D. Usernames
Answer: A
NEW QUESTION 15
Which of the following steps for risk assessment methodology refers to vulnerability identification?
- A. Determines if any flaws exist in systems, policies, or procedures
- B. Assigns values to risk probabilities; Impact values.
- C. Determines risk probability that vulnerability will be exploited (Hig
- D. Medium, Low)
- E. Identifies sources of harm to an IT syste
- F. (Natural, Huma
- G. Environmental)
Answer: C
NEW QUESTION 16
A large mobile telephony and data network operator has a data center that houses network elements. These are essentially large computers running on Linux. The perimeter of the data center is secured with firewalls and IPS systems.
What is the best security policy concerning this setup?
- A. Network elements must be hardened with user ids and strong password
- B. Regular security tests and audits should be performed.
- C. As long as the physical access to the network elements is restricted, there is no need for additional measures.
- D. There is no need for specific security measures on the network elements as long as firewalls and IPS systems exist.
- E. The operator knows that attacks and down time are inevitable and should have a backup site.
Answer: A
NEW QUESTION 17
As a Certified Ethical Hacker, you were contracted by a private firm to conduct an external security assessment through penetration testing.
What document describes the specifics of the testing, the associated violations, and essentially protects both the organization’s interest and your liabilities as a tester?
- A. Service Level Agreement
- B. Project Scope
- C. Rules of Engagement
- D. Non-Disclosure Agreement
Answer: C
NEW QUESTION 18
The tools which receive event logs from servers, network equipment, and applications, and perform analysis and correlation on those logs, and can generate alarms for security relevant issues, are known as what?
- A. network Sniffer
- B. Vulnerability Scanner
- C. Intrusion prevention Server
- D. Security incident and event Monitoring
Answer: D
NEW QUESTION 19
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?
- A. USER, NICK
- B. LOGIN, NICK
- C. USER, PASS
- D. LOGIN, USER
Answer: A
NEW QUESTION 20
Which of the following programs is usually targeted at Microsoft Office products?
- A. Polymorphic virus
- B. Multipart virus
- C. Macro virus
- D. Stealth virus
Answer: C
NEW QUESTION 21
A company's policy requires employees to perform file transfers using protocols which encrypt traffic. You suspect some employees are still performing file transfers using unencrypted protocols because the employees do not like changes. You have positioned a network sniffer to capture traffic from the laptops used by employees in the data ingest department. Using Wire shark to examine the captured traffic, which command can be used as a display filter to find unencrypted file transfers?
- A. tcp.port != 21
- B. tcp.port = 23
- C. tcp.port ==21
- D. tcp.port ==21 || tcp.port ==22
Answer: D
NEW QUESTION 22
......
Recommend!! Get the Full 312-50v11 dumps in VCE and PDF From Certleader, Welcome to Download: https://www.certleader.com/312-50v11-dumps.html (New 254 Q&As Version)
