350-901 Exam
Update Developing Applications Using Cisco Core Platforms & APIs 350-901 Free Demo

we provide 100% Guarantee Cisco 350-901 sample question which are the best for clearing 350-901 test, and to get certified by Cisco Developing Applications using Cisco Core Platforms & APIs. The 350-901 Questions & Answers covers all the knowledge points of the real 350-901 exam. Crack your Cisco 350-901 Exam with latest dumps, guaranteed!
Cisco 350-901 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
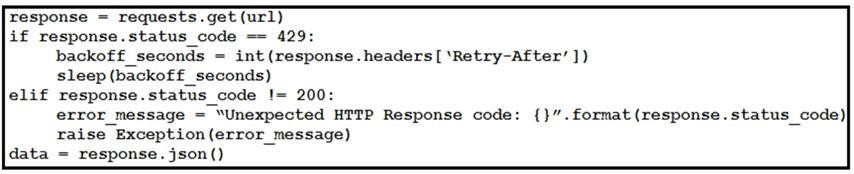
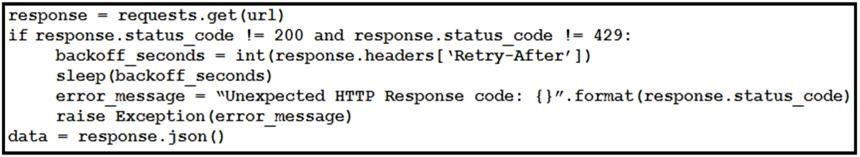
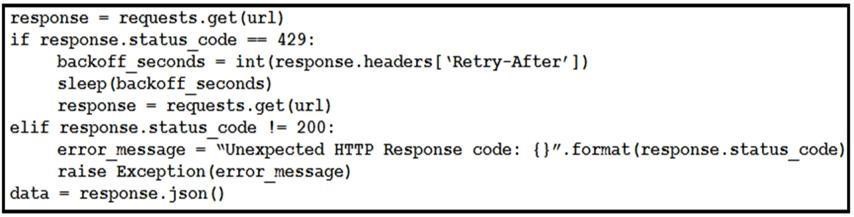
Refer to the exhibit. This snippet of a script has recently started exiting abnormally with an exception stating “Unexpected HTTP Response code: 429”. Which solution handles rate limiting by the remote API?
- A.
- B.

- C.
- D.
Answer: D
NEW QUESTION 2
An application has initiated an OAuth authorization code grant flow to get access to an API resource on behalf of an end user.
Which two parameters are specified in the HTTP request coming back to the application as the end user grants access? (Choose two.)
- A. access token and a refresh token with respective expiration times to access the API resource
- B. access token and expiration time to access the API resource
- C. redirect URI a panel that shows the list of permissions to grant
- D. code that can be exchanged for an access token
- E. state can be used for correlation and security checks
Answer: AB
NEW QUESTION 3
Which two statements are considered best practices according to the 12-factor app methodology for application design? (Choose two.)
- A. Application code writes its event stream to stdout.
- B. Application log streams are archived in multiple replicated databases.
- C. Application log streams are sent to log indexing and analysis systems.
- D. Application code writes its event stream to specific log files.
- E. Log files are aggregated into a single file on individual nodes.
Answer: AD
NEW QUESTION 4
Which transport protocol is used by gNMI?
- A. HTTP/2
- B. HTTP 1.1
- C. SSH
- D. MQTT
Answer: A
NEW QUESTION 5
An automated solution is needed to configure VMs in numerous cloud provider environments to connect the environments to an SDWAN. The SDWAN edge VM is provided as an image in each of the relevant clouds and can be given an identity and all required configuration via cloud-init without needing to log into the VM once online.
Which configuration management and/or automation tooling is needed for this solution?
- A. Ansible
- B. Ansible and Terraform
- C. NSO
- D. Terraform
- E. Ansible and NSO
Answer: E
NEW QUESTION 6
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority. Which approach must be taken to secure API keys and passwords?
- A. Embed them directly in the code.
- B. Store them in a hidden file.
- C. Store them inside the source tree of the application.
- D. Change them periodically.
Answer: D
NEW QUESTION 7
An application uses OAuth to get access to several API resources on behalf of an end user. What are two valid parameters to send to the authorization server as part of the first step of an authorization code grant flow? (Choose two.)
- A. URI to which the authorization server will send the user-agent back when access is granted or denied
- B. list of the API resources that the application is requesting to access
- C. secret that was generated by the authorization server when the application registered as an OAuth integration
- D. list of scopes that correspond to the API resources to which the application is requesting to access
- E. name of the application under which the application registered as an OAuth integration
Answer: AC
NEW QUESTION 8
Which two situations are flagged by software tools designed for dependency checking in continuous integration environments, such as OWASP? (Choose two.)
- A. publicly disclosed vulnerabilities related to the included dependencies
- B. mismatches in coding styles and conventions in the included dependencies
- C. incompatible licenses in the included dependencies
- D. test case failures introduced by bugs in the included dependencies
- E. buffer overflows to occur as the result of a combination of the included dependencies
Answer: AE
NEW QUESTION 9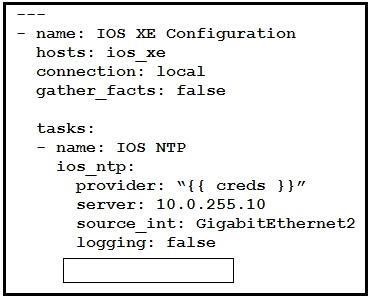
Refer to the exhibit. Which key value pair from the ios_ntp Ansible module creates an NTP server peer?
- A. state: present
- B. state: True
- C. config: present
- D. config: True
Answer: A
NEW QUESTION 10
A cloud native project is being worked on in which all source code and dependencies are written in Python, Ruby, and/or JavaScnpt. A change in code triggers a notification to the CI/CD tool to run the CI/CD pipeline.
Which step should be omitted from the pipeline?
- A. Deploy the code to one or more environments, such as staging and/or production.
- B. Build one of more containers that package up code and all its dependencies.
- C. Compile code.
- D. Run automated tests to validate the correctness.
Answer: A
NEW QUESTION 11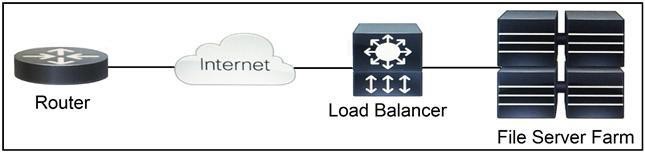
Refer to the exhibit. Which two functions are performed by the load balancer when it handles traffic originating from the Internet destined to an application hosted on the file server farm? (Choose two.)
- A. Terminate the TLS over the UDP connection from the router and originate an HTTPS connection to the selected server.
- B. Terminate the TLS over the UDP connection from the router and originate an HTTP connection to the selected server.
- C. Terminate the TLS over the TCP connection from the router and originate an HTTP connection to the selected server.
- D. Terminate the TLS over the TCP connection from the router and originate an HTTPS connection to the selected server.
- E. Terminate the TLS over the SCTP connection from the router and originate an HTTPS connection to the selected server.
Answer: DE
NEW QUESTION 12
A client is written that uses a REST API to interact with a server. Using HTTPS as the transport, an HTTP request is sent and received an HTTP response. The response contains the HTTP response status code: 503 Service Unavailable.
Which action is the appropriate response?
- A. Add an Authorization header that supplies appropriate credentials and sends the updated request.
- B. Resend the request using HTTP as the transport instead of HTTPS.
- C. Add an Accept header that indicates the content types that the client understands and send the updated request.
- D. Look for a Retry-After header in the response and resend the request after the amount of time indicated.
Answer: A
NEW QUESTION 13
Which two types of storage are supported for app hosting on a Cisco Catalyst 9000 Series Switch? (Choose two.)
- A. external USB storage
- B. internal SSD
- C. CD-ROM
- D. SD-card
- E. bootflash
Answer: AB
NEW QUESTION 14
What is submitted when an SSL certificate is requested?
- A. PEM
- B. CRT
- C. DER
- D. CSR
Answer: D
NEW QUESTION 15
Which two methods are API security best practices? (Choose two.)
- A. Use tokens after the identity of a client has been established.
- B. Use the same operating system throughout the infrastructure.
- C. Use encryption and signatures to secure data.
- D. Use basic auth credentials over all internal API interactions.
- E. Use cloud hosting services to manage security configuration.
Answer: AC
NEW QUESTION 16
A user is receiving a 429 Too Many Requests error. Which scheme is the server employing that causes this error?
- A. rate limiting
- B. time outs
- C. caching
- D. redirection
Answer: A
NEW QUESTION 17
Which type of file is created from issued intermediate, root, and primary certificates for SSL installation on a server?
- A. DER
- B. CSR
- C. PEM
- D. CRT
Answer: C
NEW QUESTION 18
Which two techniques protect against injection attacks? (Choose two.)
- A. input validation
- B. trim whitespace
- C. limit text areas to 255 characters
- D. string escaping of user free text and data entry
- E. only use dropdown, checkbox, and radio button fields
Answer: AE
NEW QUESTION 19
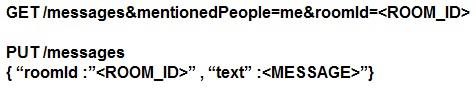
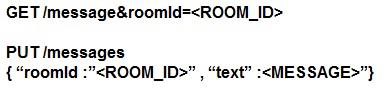
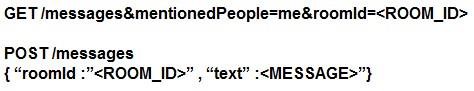
Refer to the exhibit. Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?
- A.

- B.
- C.
- D.
Answer: B
NEW QUESTION 20
Refer to the exhibit. The YAML represented is using the ios_vrf module. As part of the Ansible playbook workflow, what is the result when this task is run?
- A. VRFs not defined in the host_vars file are removed from the device.
- B. VRFs not defined in the host_vars file are added to the device, and any other VRFs on the device remain.
- C. VRFs defined in the host_vars file are removed from the device.
- D. VRFs are added to the device from the host_vars file, and any other VRFs on the device are removed.
Answer: D
NEW QUESTION 21
A developer has created an application based on customer requirements. The customer needs to run the application with the minimum downtime. Which design approach regarding high-availability applications, Recovery Time Objective, and Recovery Point Objective must be taken?
- A. Active/passive results in lower RTO and RP
- B. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
- C. Active/passive results in lower RTO and RP
- D. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
- E. Active/active results in lower RTO and RP
- F. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
- G. Active/active results in lower RTO and RP
- H. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
Answer: A
NEW QUESTION 22
DRAG DROP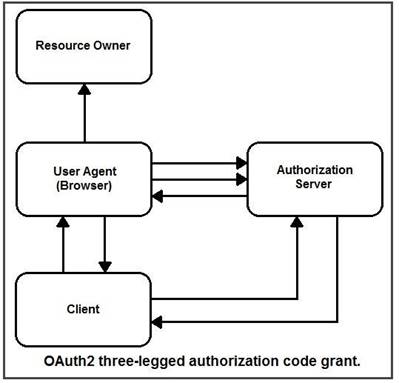
Refer to the exhibit. Drag and drop the steps from the left into the correct order of operation on the right for a successful OAuth2 three-legged authorization code grant flow.
Select and Place: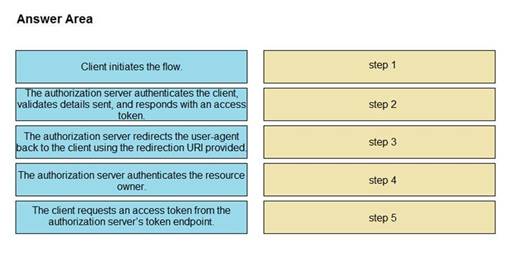
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 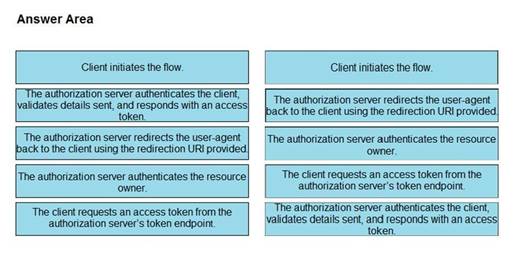
NEW QUESTION 23
......
P.S. 2passeasy now are offering 100% pass ensure 350-901 dumps! All 350-901 exam questions have been updated with correct answers: https://www.2passeasy.com/dumps/350-901/ (0 New Questions)
