400-007 Exam
Up To The Immediate Present Cisco Certified Design Expert (CCDE V3.0) Written Exam 400-007 Vce

Master the 400-007 Cisco Certified Design Expert (CCDE v3.0) Written Exam content and be ready for exam day success quickly with this Examcollection 400-007 exam topics. We guarantee it!We make it a reality and give you real 400-007 questions in our Cisco 400-007 braindumps.Latest 100% VALID Cisco 400-007 Exam Questions Dumps at below page. You can use our Cisco 400-007 braindumps and pass your exam.
Cisco 400-007 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Company XYZ is planning to deploy primary and secondary (disaster recovery) data center sites. Each of these sites will have redundant SAN fabrics and data protection is expected between the data center sites. The sites are 100 miles (160 km) apart and target RPO/RTO are 3 hrs and 24 hrs, respectively. Which two considerations must Company XYZ bear in mind when deploying replication in their scenario? (Choose two.)
- A. Target RPO/RTO requirements cannot be met due to the one-way delay introduced by thedistance between sites.
- B. VSANs must be routed between sites to isolate fault domains and increase overall availability.
- C. Synchronous data replication must be used to meet the business requirements
- D. Asynchronous data replication should be used in this scenario to avoid performance impact in theprimary site.
- E. VSANs must be extended from the primary to the secondary site to improve performance andavailability.
Answer: BD
NEW QUESTION 2
You were tasked to enhance the security of a network with these characteristics:
- A pool of servers is accessed by numerous data centers and remote sites
- The servers are accessed via a cluster of firewalls
- The firewalls are configured properly and are not dropping traffic
- The firewalls occasionally cause asymmetric routing of traffic within the server data center.
Which technology should you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
- A. Poison certain subnets by adding static routes to Null0 on the core switches connected to thepool of servers.
- B. Deploy uRPF strict mode.
- C. Limit sources of traffic that exit the server-facing interface of the firewall cluster with ACLs.
- D. Deploy uRPF loose mode
Answer: C
NEW QUESTION 3
Drag and Drop Question
Drag and drop the design use cases from the left onto the correct uRPF techniques used to prevent spoofing attacks.
Not all options are used.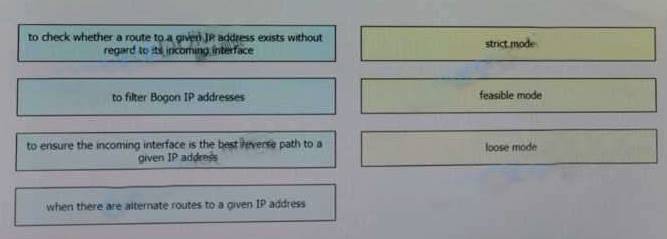
Solution:
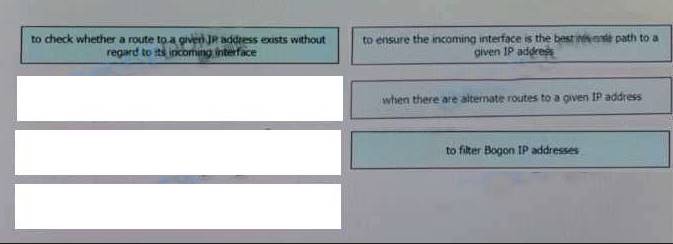
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 4
What are two primary design constraints when a robust infrastructure solution is created? (Choose two.)
- A. monitoring capabilities
- B. project time frame
- C. staff experience
- D. component availability
- E. total cost
Answer: BE
NEW QUESTION 5
You want to split an Ethernet domain in two.
Which parameter must be unique in this design to keep the two domains separated?
- A. VTP domain
- B. VTP password
- C. STP type
- D. VLAN ID
Answer: D
NEW QUESTION 6
A multicast network is sing Bidirectional PIM. Which two combined actions achieve high availability
so that two RPs within the same network can act in a redundant manner? (Choose two)
- A. Use two phantom RP addresses
- B. Manipulate the administration distance of the unicast routes to the two RPs
- C. Manipulate the multicast routing table by creating static mroutes to the two RPs
- D. Advertise the two RP addresses in the routing protocol
- E. Use anycast RP based on MSDP peering between the two RPs
- F. Control routing to the two RPs through a longest match prefix
Answer: AF
NEW QUESTION 7
Which option is a fate-sharing characteristic in regards to network design?
- A. A failure of a single element causes the entire service to fail
- B. It protects the network against failures in the distribution layer
- C. It acts as a stateful forwarding device
- D. It provides data sequencing and acknowledgment mechanisms
Answer: A
NEW QUESTION 8
Company XYZ needs advice in redesigning their legacy Layer 2 infrastructure.
Which technology should be included in the design to minimize or avoid convergence delays due to STP or FHRP and provide a loop-free topology?
- A. Use switch clustering in the access layer.
- B. Use switch clustering in the core/distribution layer.
- C. Use spanning-tree PortFast.
- D. Use BFD.
Answer: B
NEW QUESTION 9
Which MPLS TE design consideration is true?
- A. MPLS TE replaces LDP and the dependency of the IGP to identify the best path.
- B. MPLS TE provides link and node protection
- C. MPLS TE optimizes the routing of IP traffic, given the constraints imposed by backbone capacityand application requirements.
- D. MPLS TE requires Layer 3 VPN full-mesh topology deployment
Answer: C
NEW QUESTION 10
Company XYZ wants to secure the data plane of their network.
Which two technologies can be included in the security design? (Choose two)
- A. DAI
- B. IP Source Guard
- C. BEEP
- D. CPPr
- E. MPP
Answer: AB
NEW QUESTION 11
When designing a WAN that will be carrying real-time traffic, what are two important reasons to consider serialization delay? (Choose two )
- A. Serialization delays are invariable because they depend only on the line rate of the interface
- B. Serialization delays are variable because they depend on the line rate of the interface and on thetype of the packet being serialized.
- C. Serialization delay is the time required to transmit the packet on the physical media.
- D. Serialization delays are variable because they depend only on the size of the packet beingserialized
- E. Serialization delay depends not only on the line rate of the interface but also on the size of thepacket
Answer: BD
NEW QUESTION 12
Company ABC wants to minimize the risk of users plugging unauthorized switches and hubs into the network.
Which two features can be used on the LAN access ports to support this design requirement? (Choose two.)
- A. Loop Guard
- B. PortFast
- C. DTF
- D. Root Guard
- E. BPDU Guard
Answer: BE
NEW QUESTION 13
Retef to the exhibit. This network is running OSPF and EIGRP as the routing protocols. Mutual redistribution of the routing protocols has been contoured on the appropriate ASBRs. The OSPF network must be designed so that flapping routes in EIGRP domains do not affect the SPF runs within OSPF. The design solution must not affect the way EIGRP routes are propagated into the EIGRP domains.
Which technique accomplishes the requirement?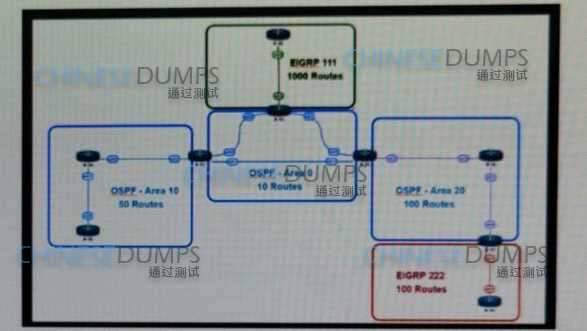
- A. route summarization the ASBR interfaces facing the OSPF domain
- B. route summarization on the appropriate ASBRS.
- C. route summarization on the appropriate ABRS.
- D. route summarization on EIDRP routers connecting toward the ASBR
Answer: B
NEW QUESTION 14
Refer to the exhibit.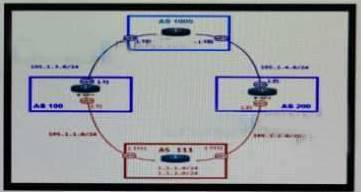
An engineer is designing the network for a multihomed customer running in AS 111 does not have any other Ass connected to it.
Which technology is more comprehensive to use in the design to make sure that the AS is not being used as a transit AS?
- A. Configure the AS-set attribute to allow only routes from AS 111 to be propagated to the neighborASs.
- B. Use the local preference attribute to configure your AS as a non-transit'' AS.
- C. include an AS path access list to send routes to the neighboring ASs that only have AS 111 in theAS path field.
- D. Include a prefix list to only receive routes from neighboring ASs.
Answer: C
NEW QUESTION 15
You are tasked with the design of a high available network. Which two features provide fail closed environments? (Choose two.)
- A. EIGRP
- B. RPVST+
- C. MST
- D. L2MP
Answer: AB
NEW QUESTION 16
......
Recommend!! Get the Full 400-007 dumps in VCE and PDF From Dumps-hub.com, Welcome to Download: https://www.dumps-hub.com/400-007-dumps.html (New 0 Q&As Version)
