412-79v10 Exam
Up To The Minute EC-Council Certified Security Analyst (ECSA) V10 412-79v10 Training Tools

It is impossible to pass EC-Council 412-79v10 exam without any help in the short term. Come to Exambible soon and find the most advanced, correct and guaranteed EC-Council 412-79v10 practice questions. You will get a surprising result by our Down to date EC-Council Certified Security Analyst (ECSA) V10 practice guides.
Free 412-79v10 Demo Online For EC-Council Certifitcation:
NEW QUESTION 1
When you are running a vulnerability scan on a network and the IDS cuts off your connection, what type of IDS is being used?
- A. Passive IDS
- B. Active IDS
- C. Progressive IDS
- D. NIPS
Answer: B
NEW QUESTION 2
What operating system would respond to the following command?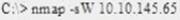
- A. Mac OS X
- B. Windows XP
- C. Windows 95
- D. FreeBSD
Answer: D
NEW QUESTION 3
The framework primarily designed to fulfill a methodical and organized way of addressing five threat classes to network and that can be used to access, plan, manage, and maintain secure computers and communication networks is:
- A. Nortells Unified Security Framework
- B. The IBM Security Framework
- C. Bell Labs Network Security Framework
- D. Microsoft Internet Security Framework
Answer: C
NEW QUESTION 4
Meyer Electronics Systems just recently had a number of laptops stolen out of their office. On these laptops contained sensitive corporate information regarding patents and company strategies.
A month after the laptops were stolen, a competing company was found to have just developed products that almost exactly duplicated products that Meyer produces.
What could have prevented this information from being stolen from the laptops?
- A. SDW Encryption
- B. EFS Encryption
- C. DFS Encryption
- D. IPS Encryption
Answer: B
NEW QUESTION 5
Snort, an open source network-based intrusion detection sensor, is the most widely installed NIDS in the world. It can be configured to run in the four modes. Which one of the following modes reads the packets off the network and displays them in a continuous stream on the console (screen)?
- A. Packet Sniffer Mode
- B. Packet Logger Mode
- C. Network Intrusion Detection System Mode
- D. Inline Mode
Answer: A
NEW QUESTION 6
Jessica works as systems administrator for a large electronics firm. She wants to scan her network quickly to detect live hosts by using ICMP ECHO Requests. What type of scan is Jessica going to perform?
- A. Smurf scan
- B. Tracert
- C. Ping trace
- D. ICMP ping sweep
Answer: D
NEW QUESTION 7
Which one of the following architectures has the drawback of internally considering the hosted services individually?
- A. Weak Screened Subnet Architecture
- B. "Inside Versus Outside" Architecture
- C. "Three-Homed Firewall" DMZ Architecture
- D. Strong Screened-Subnet Architecture
Answer: C
NEW QUESTION 8
Kimberly is studying to be an IT security analyst at a vocational school in her town. The school offers
many different programming as well as networking languages. What networking protocol language should she learn that routers utilize?
- A. OSPF
- B. BPG
- C. ATM
- D. UDP
Answer: A
NEW QUESTION 9
What are placeholders (or markers) in an HTML document that the web server will dynamically replace with data just before sending the requested documents to a browser?
- A. Server Side Includes
- B. Sort Server Includes
- C. Server Sort Includes
- D. Slide Server Includes
Answer: A
NEW QUESTION 10
How many possible sequence number combinations are there in TCP/IP protocol?
- A. 320 billion
- B. 32 million
- C. 4 billion
- D. 1 billion
Answer: C
NEW QUESTION 11
A framework is a fundamental structure used to support and resolve complex issues. The framework that delivers an efficient set of technologies in order to develop applications which are more secure in using Internet and Intranet is:
- A. Microsoft Internet Security Framework
- B. Information System Security Assessment Framework (ISSAF)
- C. Bell Labs Network Security Framework
- D. The IBM Security Framework
Answer: A
NEW QUESTION 12
Which of the following statements is true about Multi-Layer Intrusion Detection Systems (mIDSs)?
- A. Decreases consumed employee time and increases system uptime
- B. Increases detection and reaction time
- C. Increases response time
- D. Both Decreases consumed employee time and increases system uptime and Increases response time
Answer: A
NEW QUESTION 13
Identify the type of testing that is carried out without giving any information to the employees or
administrative head of the organization.
- A. Unannounced Testing
- B. Double Blind Testing
- C. Announced Testing
- D. Blind Testing
Answer: B
NEW QUESTION 14
Terri works for a security consulting firm that is currently performing a penetration test on First National Bank in Tokyo. Terri's duties include bypassing firewalls and switches to gain access to the network. Terri sends an IP packet to one of the company's switches with ACK bit and the source address of her machine set.
What is Terri trying to accomplish by sending this IP packet?
- A. Poison the switch's MAC address table by flooding it with ACK bits
- B. Enable tunneling feature on the switch
- C. Trick the switch into thinking it already has a session with Terri's computer
- D. Crash the switch with a DoS attack since switches cannot send ACK bits
Answer: C
NEW QUESTION 15
Firewall and DMZ architectures are characterized according to its design. Which one of the following architectures is used when routers have better high-bandwidth data stream handling capacity?
- A. Weak Screened Subnet Architecture
- B. "Inside Versus Outside" Architecture
- C. "Three-Homed Firewall" DMZ Architecture
- D. Strong Screened-Subnet Architecture
Answer: A
NEW QUESTION 16
An automated electronic mail message from a mail system which indicates that the user does not exist on that server is called as?
- A. SMTP Queue Bouncing
- B. SMTP Message Bouncing
- C. SMTP Server Bouncing
- D. SMTP Mail Bouncing
Answer: D
NEW QUESTION 17
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?
- A. Vulnerability Report
- B. Executive Report
- C. Client-side test Report
- D. Host Report
Answer: B
NEW QUESTION 18
Vulnerability assessment is an examination of the ability of a system or application, including current security procedures and controls, to withstand assault. It recognizes, measures, and classifies security vulnerabilities in a computer system, network, and communication channels.
A vulnerability assessment is used to identify weaknesses that could be exploited and predict the effectiveness of additional security measures in protecting information resources from attack.
Which of the following vulnerability assessment technique is used to test the web server infrastructure for any misconfiguration and outdated content?
- A. Passive Assessment
- B. Host-based Assessment
- C. External Assessment
- D. Application Assessment
Answer: D
NEW QUESTION 19
Which of the following will not handle routing protocols properly?
- A. “Internet-router-firewall-net architecture”
- B. “Internet-firewall-router-net architecture”
- C. “Internet-firewall -net architecture”
- D. “Internet-firewall/router(edge device)-net architecture”
Answer: B
NEW QUESTION 20
Which of the following are the default ports used by NetBIOS service?
- A. 135, 136, 139, 445
- B. 134, 135, 136, 137
- C. 137, 138, 139, 140
- D. 133, 134, 139, 142
Answer: A
NEW QUESTION 21
......
Thanks for reading the newest 412-79v10 exam dumps! We recommend you to try the PREMIUM Dumps-hub.com 412-79v10 dumps in VCE and PDF here: https://www.dumps-hub.com/412-79v10-dumps.html (201 Q&As Dumps)
