412-79v9 Exam
Realistic EC-Council 412-79v9 Free Demo Online

It is more faster and easier to pass the EC-Council 412-79v9 exam by using High value EC-Council EC-Council Certified Security Analyst (ECSA) v9 questuins and answers. Immediate access to the Refresh 412-79v9 Exam and find the same core area 412-79v9 questions with professionally verified answers, then PASS your exam with a high score now.
Free 412-79v9 Demo Online For EC-Council Certifitcation:
NEW QUESTION 1
Which one of the following log analysis tools is used for analyzing the server’s log files?
- A. Performance Analysis of Logs tool
- B. Network Sniffer Interface Test tool
- C. Ka Log Analyzer tool
- D. Event Log Tracker tool
Answer: C
NEW QUESTION 2
Which of the following password hashing algorithms is used in the NTLMv2 authentication mechanism?
- A. AES
- B. DES (ECB mode)
- C. MD5
- D. RC5
Answer: C
NEW QUESTION 3
John, the penetration tester in a pen test firm, was asked to find whether NTP services are opened on the target network (10.0.0.7) using Nmap tool.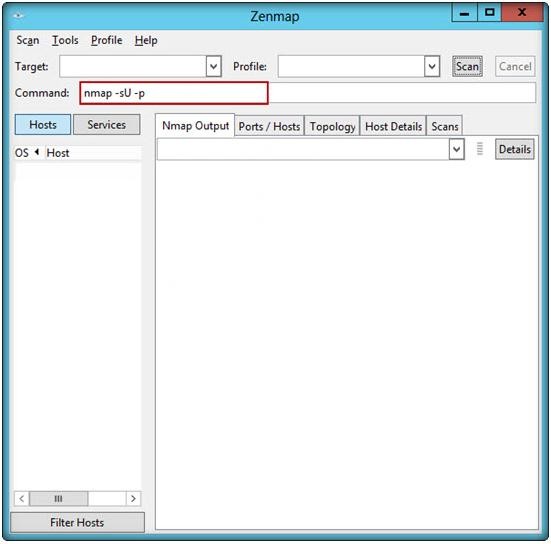
Which one of the following Nmap commands will he use to find it?
- A. nmap -sU –p 389 10.0.0.7
- B. nmap -sU –p 123 10.0.0.7
- C. nmap -sU –p 161 10.0.0.7
- D. nmap -sU –p 135 10.0.0.7
Answer: B
NEW QUESTION 4
Software firewalls work at which layer of the OSI model?
- A. Data Link
- B. Network
- C. Transport
- D. Application
Answer: A
NEW QUESTION 5
What information can be collected by dumpster diving?
- A. Sensitive documents
- B. Email messages
- C. Customer contact information
- D. All the above
Answer: A
Explanation:
Reference: http://www.spamlaws.com/dumpster-diving.html
NEW QUESTION 6
Which of the following has an offset field that specifies the length of the header and data?
- A. IP Header
- B. UDP Header
- C. ICMP Header
- D. TCP Header
Answer: D
NEW QUESTION 7
Transmission control protocol accepts data from a data stream, divides it into chunks, and adds a TCP header creating a TCP segment.
The TCP header is the first 24 bytes of a TCP segment that contains the parameters and state of an end-to-end TCP socket. It is used to track the state of communication between two TCP endpoints.
For a connection to be established or initialized, the two hosts must synchronize. The synchronization requires each side to send its own initial sequence number and to receive a confirmation of exchange in an acknowledgment (ACK) from the other side
The below diagram shows the TCP Header format: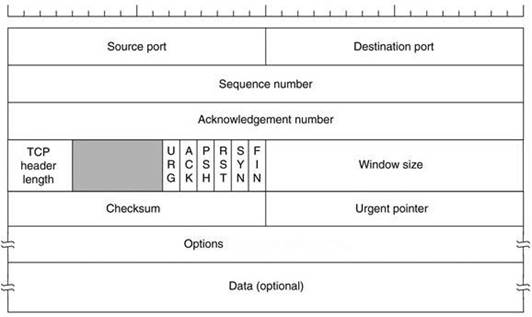
How many bits is a acknowledgement number?
- A. 16 bits
- B. 32 bits
- C. 8 bits
- D. 24 bits
Answer: B
Explanation:
Reference: http://en.wikipedia.org/wiki/Transmission_Control_Protocol (acknowledgement number)
NEW QUESTION 8
Which one of the following Snort logger mode commands is associated to run a binary log file through Snort in sniffer mode to dump the packets to the screen?
- A. ./snort -dvr packet.log icmp
- B. ./snort -dev -l ./log
- C. ./snort -dv -r packet.log
- D. ./snort -l ./log –b
Answer: C
NEW QUESTION 9
Identify the port numbers used by POP3 and POP3S protocols.
- A. 113 and 981
- B. 111 and 982
- C. 110 and 995
- D. 109 and 973
Answer: C
Explanation:
Reference: https://publib.boulder.ibm.com/infocenter/wsmashin/v1r1/index.jsp?topic=/com.ibm.websph ere.sMash.doc/using/zero.mail/MailStoreConfiguration.html
NEW QUESTION 10
You work as an IT security auditor hired by a law firm in Boston. You have been assigned the responsibility to audit the client for security risks. When assessing the risk to the clients network, what step should you take first?
- A. Analyzing, categorizing and prioritizing resources
- B. Evaluating the existing perimeter and internal security
- C. Checking for a written security policy
- D. Analyzing the use of existing management and control architecture
Answer: C
NEW QUESTION 11
ARP spoofing is a technique whereby an attacker sends fake ("spoofed") Address
Resolution Protocol (ARP) messages onto a Local Area Network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host (such as the default gateway), causing any traffic meant for that IP address to be sent to the attacker instead.
ARP spoofing attack is used as an opening for other attacks.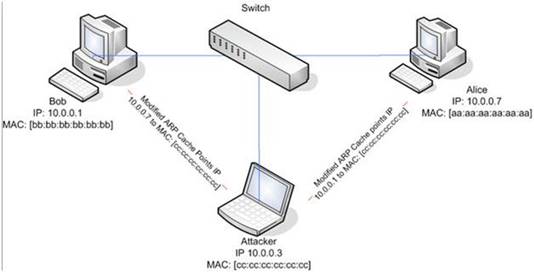
What type of attack would you launch after successfully deploying ARP spoofing?
- A. Parameter Filtering
- B. Social Engineering
- C. Input Validation
- D. Session Hijacking
Answer: D
Explanation:
http://en.wikipedia.org/wiki/ARP_spoofing
NEW QUESTION 12
Identify the policy that defines the standards for the organizational network connectivity and security standards for computers that are connected in the organizational network.
- A. Information-Protection Policy
- B. Special-Access Policy
- C. Remote-Access Policy
- D. Acceptable-Use Policy
Answer: C
NEW QUESTION 13
Due to illegal inputs, various types of TCP stacks respond in a different manner. Some IDSs do not take into account the TCP protocol's urgency feature, which could allow testers to evade the IDS.
Penetration tester needs to try different combinations of TCP flags (e.g. none, SYN/FIN, SYN/RST, SYN/FIN/ACK, SYN/RST/ACK, and All Flags) to test the IDS.
Which of the following TCP flag combinations combines the problem of initiation, midstream, and termination flags with the PSH and URG?
- A. SYN/RST/ACK
- B. SYN/FIN/ACK
- C. SYN/FIN
- D. All Flags
Answer: D
Explanation:
Reference: http://books.google.com.pk/books?id=tUCumJot0ocC&pg=PA63&lpg=PA63&dq=TCP+flag
+combinations+combines+the+problem+of+initiation,+midstream,+and+termination+flags+ with+the+PSH+and+URG&source=bl&ots=mIGSXBIi15&sig=WMnXlEChVSU4RhK65W_V 3tzNjns&hl=en&sa=X&ei=H7AfVJCtLaufygO1v4DQDg&ved=0CBsQ6AEwAA#v=onepage& q=TCP%20flag%20combinations%20combines%20the%20problem%20of%20initiation%2 C%20midstream%2C%20and%20termination%20flags%20with%20the%20PSH%20and% 20URG&f=false (see the highlighted sentence in Table 3-1 at the end of the page)
NEW QUESTION 14
Which of the following contents of a pen testing project plan addresses the strengths, weaknesses, opportunities, and threats involved in the project?
- A. Project Goal
- B. Success Factors
- C. Objectives
- D. Assumptions
Answer: D
NEW QUESTION 15
Identify the type of firewall represented in the diagram below: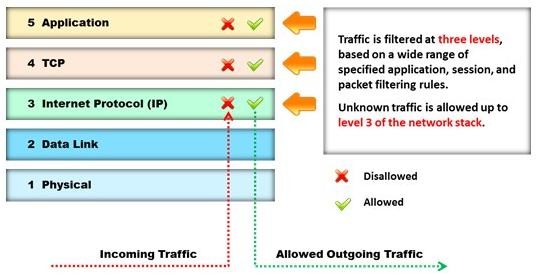
- A. Stateful multilayer inspection firewall
- B. Application level gateway
- C. Packet filter
- D. Circuit level gateway
Answer: A
Explanation:
Reference: http://www.technicolorbroadbandpartner.com/getfile.php?id=4159 (page 13)
NEW QUESTION 16
Wireless communication allows networks to extend to places that might otherwise go untouched by the wired networks. When most people say ‘Wireless’ these days, they are referring to one of the 802.11 standards. There are three main 802.11 standards: B, A, and
- A. Which one of the following 802.11 types uses DSSS Modulation, splitting the 2.4ghz band into channels?
- B. 802.11b
- C. 802.11g
- D. 802.11-Legacy
- E. 802.11n
Answer: A
NEW QUESTION 17
A Blind SQL injection is a type of SQL Injection attack that asks the database true or false questions and determines the answer based on the application response. This attack is often used when the web application is configured to show generic error messages, but has not mitigated the code that is vulnerable to SQL injection.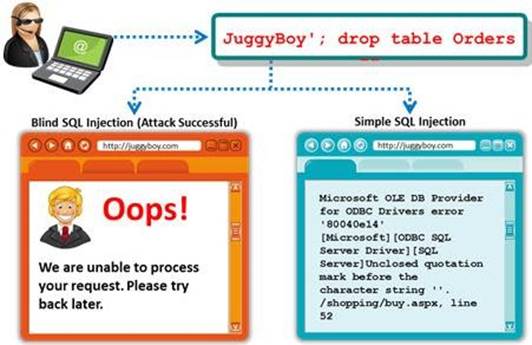
It is performed when an error message is not received from application while trying to exploit SQL vulnerabilities. The developer's specific message is displayed instead of an error message. So it is quite difficult to find SQL vulnerability in such cases.
A pen tester is trying to extract the database name by using a blind SQL injection. He tests the database using the below query and finally finds the database name.
http://juggyboy.com/page.aspx?id=1; IF (LEN(DB_NAME())=4) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),1,1)))=97) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),2,1)))=98) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),3,1)))=99) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),4,1)))=100) WAITFOR DELAY '00:00:10'--
What is the database name?
- A. WXYZ
- B. PQRS
- C. EFGH
- D. ABCD
Answer: D
Explanation:
Reference: http://www.scribd.com/doc/184891028/CEHv8-Module-14-SQL-Injection-pdf (see module 14, page 2049 to 2051)
NEW QUESTION 18
A firewall protects networked computers from intentional hostile intrusion that could compromise confidentiality or result in data corruption or denial of service. It examines all traffic routed between the two networks to see if it meets certain criteria. If it does, it is routed between the networks, otherwise it is stopped.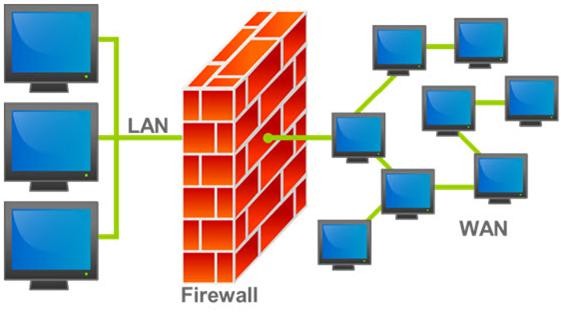
Why is an appliance-based firewall is more secure than those implemented on top of the commercial operating system (Software based)?
- A. Appliance based firewalls cannot be upgraded
- B. Firewalls implemented on a hardware firewall are highly scalable
- C. Hardware appliances does not suffer from security vulnerabilities associated with the underlying operating system
- D. Operating system firewalls are highly configured
Answer: C
NEW QUESTION 19
What sort of vulnerability assessment approach starts by building an inventory of protocols found on the machine?
- A. Inference-based Assessment
- B. Service-based Assessment Solutions
- C. Product-based Assessment Solutions
- D. Tree-based Assessment
Answer: A
Explanation:
Reference: http://www.businessweek.com/adsections/2005/pdf/wp_mva.pdf (page 26, first para on the page)
NEW QUESTION 20
A firewall’s decision to forward or reject traffic in network filtering is dependent upon which of the following?
- A. Destination address
- B. Port numbers
- C. Source address
- D. Protocol used
Answer: D
Explanation:
Reference: http://www.vicomsoft.com/learning-center/firewalls/ (what does a firewall do)
NEW QUESTION 21
A security policy is a document or set of documents that describes, at a high level, the security controls that will be implemented by the company. Which one of the following policies forbids everything and restricts usage of company computers, whether it is system usage or network usage?
- A. Paranoid Policy
- B. Prudent Policy
- C. Promiscuous Policy
- D. Information-Protection Policy
Answer: A
NEW QUESTION 22
Fuzz testing or fuzzing is a software/application testing technique used to discover coding errors and security loopholes in software, operating systems, or networks by inputting massive amounts of random data, called fuzz, to the system in an attempt to make it crash.
Fuzzers work best for problems that can cause a program to crash, such as buffer overflow, cross-site scripting, denial of service attacks, format bugs, and SQL injection.
Fuzzer helps to generate and submit a large number of inputs supplied to the application for testing it against the inputs. This will help us to identify the SQL inputs that generate malicious output.
Suppose a pen tester knows the underlying structure of the database used by the application (i.e., name, number of columns, etc.) that she is testing.
Which of the following fuzz testing she will perform where she can supply specific data to the application to discover vulnerabilities?
- A. Clever Fuzz Testing
- B. Dumb Fuzz Testing
- C. Complete Fuzz Testing
- D. Smart Fuzz Testing
Answer: D
NEW QUESTION 23
You are conducting a penetration test against a company and you would like to know a personal email address of John, a crucial employee. What is the fastest, cheapest way to find out John’s email address.
- A. Call his wife and ask for his personal email account
- B. Call a receptionist and ask for John Stevens’ personal email account
- C. Search in Google for his personal email ID
- D. Send an email to John stating that you cannot send him an important spreadsheet attachment file to his business email account and ask him if he has any other email accounts
Answer: D
NEW QUESTION 24
A framework is a fundamental structure used to support and resolve complex issues. The framework that delivers an efficient set of technologies in order to develop applications which are more secure in using Internet and Intranet is:
- A. Microsoft Internet Security Framework
- B. Information System Security Assessment Framework (ISSAF)
- C. Bell Labs Network Security Framework
- D. The IBM Security Framework
Answer: A
NEW QUESTION 25
Which of the following attacks does a hacker perform in order to obtain UDDI information
such as businessEntity, businesService, bindingTemplate, and tModel?
- A. Web Services Footprinting Attack
- B. Service Level Configuration Attacks
- C. URL Tampering Attacks
- D. Inside Attacks
Answer: A
Explanation:
Reference: http://www.scribd.com/doc/184891017/CEHv8-Module-13-Hacking-Web- Applications-pdf (page 99)
NEW QUESTION 26
Identify the transition mechanism to deploy IPv6 on the IPv4 network from the following diagram.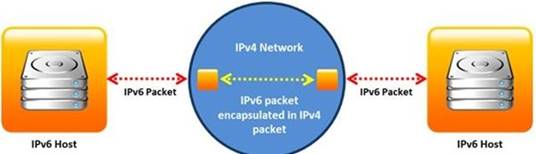
- A. Translation
- B. Tunneling
- C. Dual Stacks
- D. Encapsulation
Answer: B
NEW QUESTION 27
The framework primarily designed to fulfill a methodical and organized way of addressing five threat classes to network and that can be used to access, plan, manage, and maintain secure computers and communication networks is:
- A. Nortells Unified Security Framework
- B. The IBM Security Framework
- C. Bell Labs Network Security Framework
- D. Microsoft Internet Security Framework
Answer: C
NEW QUESTION 28
Transmission Control Protocol (TCP) is a connection-oriented four layer protocol. It is responsible for breaking messages into segments, re-assembling them at the destination
station, and re-sending. Which one of the following protocols does not use the TCP?
- A. Reverse Address Resolution Protocol (RARP)
- B. HTTP (Hypertext Transfer Protocol)
- C. SMTP (Simple Mail Transfer Protocol)
- D. Telnet
Answer: A
NEW QUESTION 29
Which one of the following acts related to the information security in the US fix the responsibility of management for establishing and maintaining an adequate internal control structure and procedures for financial reporting?
- A. California SB 1386
- B. Sarbanes-Oxley 2002
- C. Gramm-Leach-Bliley Act (GLBA)
- D. USA Patriot Act 2001
Answer: B
NEW QUESTION 30
Which of the following policies states that the relevant application owner must authorize requests for additional access to specific business applications in writing to the IT Department/resource?
- A. Special-Access Policy
- B. User Identification and Password Policy
- C. Personal Computer Acceptable Use Policy
- D. User-Account Policy
Answer: B
NEW QUESTION 31
......
Thanks for reading the newest 412-79v9 exam dumps! We recommend you to try the PREMIUM Thedumpscentre.com 412-79v9 dumps in VCE and PDF here: https://www.thedumpscentre.com/412-79v9-dumps/ (203 Q&As Dumps)
