ECSAv10 Exam
What High Quality ECSAv10 Dumps Questions Is

We provide real ECSAv10 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass EC-Council ECSAv10 Exam quickly & easily. The ECSAv10 PDF type is available for reading and printing. You can print more and practice many times. With the help of our EC-Council ECSAv10 dumps pdf and vce product and material, you can easily pass the ECSAv10 exam.
Check ECSAv10 free dumps before getting the full version:
NEW QUESTION 1
In the context of penetration testing, what does blue teaming mean?
- A. A penetration test performed with the knowledge and consent of the organization's IT staff
- B. It is the most expensive and most widely used
- C. It may be conducted with or without warning
- D. A penetration test performed without the knowledge of the organization's IT staff but with permission from upper management
Answer: A
NEW QUESTION 2
Harold is a security analyst who has just run the rdisk /s command to grab the backup SAM file on a computer. Where should Harold navigate on the computer to find the file?
- A. %systemroot%LSA
- B. %systemroot%repair
- C. %systemroot%system32driversetc
- D. %systemroot%system32LSA
Answer: B
NEW QUESTION 3
Which one of the following tools of trade is an automated, comprehensive penetration testing product for assessing the specific information security threats to an organization?
- A. Sunbelt Network Security Inspector (SNSI)
- B. CORE Impact
- C. Canvas
- D. Microsoft Baseline Security Analyzer (MBSA)
Answer: C
NEW QUESTION 4
You just passed your ECSA exam and are about to start your first consulting job running security audits for a financial institution in Los Angeles. The IT manager of the company you will be working for tries to see if you remember your ECSA class. He asks about the methodology you will be using to test the company's network.
How would you answer?
- A. IBM Methodology
- B. LPT Methodology
- C. Google Methodology
- D. Microsoft Methodology
Answer: B
NEW QUESTION 5
War Driving is the act of moving around a specific area, mapping the population of wireless access points for statistical purposes. These statistics are then used to raise awareness of the security problems associated with these types of networks.
Which one of the following is a Linux based program that exploits the weak IV (Initialization Vector) problem documented with static WEP?
- A. Airsnort
- B. Aircrack
- C. WEPCrack
- D. Airpwn
Answer: A
NEW QUESTION 6
Timing is an element of port-scanning that can catch one unaware. If scans are taking too long to complete or obvious ports are missing from the scan, various time parameters may need to be adjusted.
Which one of the following scanned timing options in NMAP’s scan is useful across slow WAN links or to hide the scan?
- A. Paranoid
- B. Sneaky
- C. Polite
- D. Normal
Answer: C
NEW QUESTION 7
Besides the policy implications of chat rooms, Internet Relay Chat (IRC) is frequented by attackers and used as a command and control mechanism. IRC normally uses which one of the following TCP ports?
- A. 6566 TCP port
- B. 6771 TCP port
- C. 6667 TCP port
- D. 6257 TCP port
Answer: C
NEW QUESTION 8
Choose the correct option to define the Prefix Length.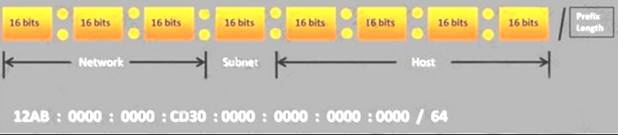
- A. Prefix Length = Subnet + Host portions
- B. Prefix Length = Network + Host portions
- C. Prefix Length = Network + Subnet portions
- D. Prefix Length = Network + Subnet + Host portions
Answer: C
NEW QUESTION 9
Identify the framework that comprises of five levels to guide agency assessment of their security programs and assist in prioritizing efforts for improvement:
- A. Information System Security Assessment Framework (ISSAF)
- B. Microsoft Internet Security Framework
- C. Nortells Unified Security Framework
- D. Federal Information Technology Security Assessment Framework
Answer: D
NEW QUESTION 10
What is the difference between penetration testing and vulnerability testing?
- A. Penetration testing goes one step further than vulnerability testing; while vulnerability tests check for known vulnerabilities, penetration testing adopts the concept of ‘in-depth ethical hacking’
- B. Penetration testing is based on purely online vulnerability analysis while vulnerability testing engages ethical hackers to find vulnerabilities
- C. Vulnerability testing is more expensive than penetration testing
- D. Penetration testing is conducted purely for meeting compliance standards while vulnerability testing is focused on online scans
Answer: A
NEW QUESTION 11
What is the following command trying to accomplish?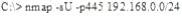
- A. Verify that NETBIOS is running for the 192.168.0.0 network
- B. Verify that TCP port 445 is open for the 192.168.0.0 network
- C. Verify that UDP port 445 is open for the 192.168.0.0 network
- D. Verify that UDP port 445 is closed for the 192.168.0.0 networks
Answer: C
NEW QUESTION 12
Michael works for Kimball Construction Company as senior security analyst. As part of yearly security audit, Michael scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and most of the ports scanned do not give a response. In what state are these ports?
- A. Filtered
- B. Stealth
- C. Closed
- D. Open
Answer: D
NEW QUESTION 13
Identify the policy that defines the standards for the organizational network connectivity and security standards for computers that are connected in the organizational network.
- A. Information-Protection Policy
- B. Special-Access Policy
- C. Remote-Access Policy
- D. Acceptable-Use Policy
Answer: C
NEW QUESTION 14
Vulnerability assessment is an examination of the ability of a system or application, including current security procedures and controls, to withstand assault. It recognizes, measures, and classifies security vulnerabilities in a computer system, network, and communication channels.
A vulnerability assessment is used to identify weaknesses that could be exploited and predict the effectiveness of additional security measures in protecting information resources from attack.
Which of the following vulnerability assessment technique is used to test the web server infrastructure for any misconfiguration and outdated content?
- A. Passive Assessment
- B. Host-based Assessment
- C. External Assessment
- D. Application Assessment
Answer: D
NEW QUESTION 15
The Internet is a giant database where people store some of their most private information on the cloud, trusting that the service provider can keep it all safe. Trojans, Viruses, DoS attacks, website defacement, lost computers, accidental publishing, and more have all been sources of major leaks over the last 15 years.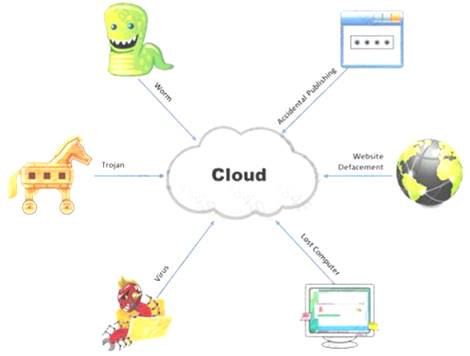
What is the biggest source of data leaks in organizations today?
- A. Weak passwords and lack of identity management
- B. Insufficient IT security budget
- C. Rogue employees and insider attacks
- D. Vulnerabilities, risks, and threats facing Web sites
Answer: C
NEW QUESTION 16
You are assisting a Department of Defense contract company to become compliant with the stringent
security policies set by the DoD. One such strict rule is that firewalls must only allow incoming connections that were first initiated by internal computers.
What type of firewall must you implement to abide by this policy?
- A. Circuit-level proxy firewall
- B. Packet filtering firewall
- C. Application-level proxy firewall
- D. Statefull firewall
Answer: D
NEW QUESTION 17
Which one of the following log analysis tools is used for analyzing the server’s log files?
- A. Performance Analysis of Logs tool
- B. Network Sniffer Interface Test tool
- C. Ka Log Analyzer tool
- D. Event Log Tracker tool
Answer: C
NEW QUESTION 18
What are the 6 core concepts in IT security?
- A. Server management, website domains, firewalls, IDS, IPS, and auditing
- B. Authentication, authorization, confidentiality, integrity, availability, and non-repudiation
- C. Passwords, logins, access controls, restricted domains, configurations, and tunnels
- D. Biometrics, cloud security, social engineering, DoS attack, viruses, and Trojans
Answer: B
NEW QUESTION 19
During the process of fingerprinting a web application environment, what do you need to do in order to analyze HTTP and HTTPS request headers and the HTML source code?
- A. Examine Source of the Available Pages
- B. Perform Web Spidering
- C. Perform Banner Grabbing
- D. Check the HTTP and HTML Processing by the Browser
Answer: D
NEW QUESTION 20
Which one of the following acts related to the information security in the US fix the responsibility of management for establishing and maintaining an adequate internal control structure and procedures for financial reporting?
- A. California SB 1386
- B. Sarbanes-Oxley 2002
- C. Gramm-Leach-Bliley Act (GLBA)
- D. USA Patriot Act 2001
Answer: B
NEW QUESTION 21
Firewall is an IP packet filter that enforces the filtering and security policies to the flowing network traffic. Using firewalls in IPv6 is still the best way of protection from low level attacks at the network and transport layers.
Which one of the following cannot handle routing protocols properly?
- A. “Internet-router-firewall-net architecture”
- B. “Internet-firewall-router-net architecture”
- C. “Internet-firewall/router(edge device)-net architecture”
- D. “Internet-firewall -net architecture”
Answer: B
NEW QUESTION 22
What is a good security method to prevent unauthorized users from "tailgating"?
- A. Electronic key systems
- B. Man trap
- C. Pick-resistant locks
- D. Electronic combination locks
Answer: B
NEW QUESTION 23
Which of the following is NOT related to the Internal Security Assessment penetration testing strategy?
- A. Testing to provide a more complete view of site security
- B. Testing focused on the servers, infrastructure, and the underlying software, including the target
- C. Testing including tiers and DMZs within the environment, the corporate network, or partner company connections
- D. Testing performed from a number of network access points representing each logical and physical segment
Answer: B
NEW QUESTION 24
Information gathering is performed to:
i) Collect basic information about the target company and its network
ii) Determine the operating system used, platforms running, web server versions, etc.
iii) Find vulnerabilities and exploits
Which of the following pen testing tests yields information about a company’s technology infrastructure?
- A. Searching for web page posting patterns
- B. Analyzing the link popularity of the company’s website
- C. Searching for trade association directories
- D. Searching for a company’s job postings
Answer: D
NEW QUESTION 25
The first and foremost step for a penetration test is information gathering. The main objective of this test is to gather information about the target system which can be used in a malicious manner to gain access to the target systems.
Which of the following information gathering terminologies refers to gathering information through social engineering on-site visits, face-to-face interviews, and direct questionnaires?
- A. Active Information Gathering
- B. Pseudonymous Information Gathering
- C. Anonymous Information Gathering
- D. Open Source or Passive Information Gathering
Answer: A
NEW QUESTION 26
Which one of the following is a command line tool used for capturing data from the live network and copying those packets to a file?
- A. Wireshark: Capinfos
- B. Wireshark: Tcpdump
- C. Wireshark: Text2pcap
- D. Wireshark: Dumpcap
Answer: D
NEW QUESTION 27
Identify the injection attack represented in the diagram below: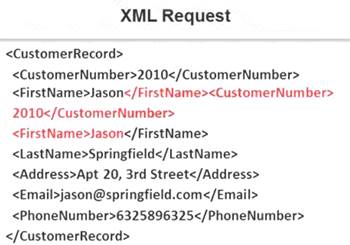
- A. XPath Injection Attack
- B. XML Request Attack
- C. XML Injection Attack
- D. Frame Injection Attack
Answer: C
NEW QUESTION 28
Which vulnerability assessment phase describes the scope of the assessment, identifies and ranks the critical assets, and creates proper information protection procedures such as effective planning, scheduling, coordination, and logistics?
- A. Threat-Assessment Phase
- B. Pre-Assessment Phase
- C. Assessment Phase
- D. Post-Assessment Phase
Answer: B
NEW QUESTION 29
In which of the following IDS evasion techniques does IDS reject the packets that an end system accepts?
- A. IPS evasion technique
- B. IDS evasion technique
- C. UDP evasion technique
- D. TTL evasion technique
Answer: D
NEW QUESTION 30
......
P.S. Easily pass ECSAv10 Exam with 201 Q&As Downloadfreepdf.net Dumps & pdf Version, Welcome to Download the Newest Downloadfreepdf.net ECSAv10 Dumps: https://www.downloadfreepdf.net/ECSAv10-pdf-download.html (201 New Questions)
