Identity-and-Access-Management-Designer Exam
Breathing Salesforce Identity-and-Access-Management-Designer Exam Online

Exam Code: Identity-and-Access-Management-Designer (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Salesforce Certified Identity and Access Management Designer (SP19)
Certification Provider: Salesforce
Free Today! Guaranteed Training- Pass Identity-and-Access-Management-Designer Exam.
Check Identity-and-Access-Management-Designer free dumps before getting the full version:
NEW QUESTION 1
Uwversal Containers (UC) is building a custom employee hut) application on Amazon Web Services (AWS) and would like to store their users' credentials there. Users will also need access to Salesforce for internal operations. UC has tasked an identity architect with evaluating Afferent solutions for authentication and authorization between AWS and Salesforce.
How should an identity architect configure AWS to authenticate and authorize Salesforce users?
- A. Configure the custom employee app as a connected app.
- B. Configure AWS as an OpenID Connect Provider.
- C. Create a custom external authentication provider.
- D. Develop a custom Auth server in AWS.
Answer: B
NEW QUESTION 2
An Identity architect works for a multinational, multi-brand organization. As they work with the organization to understand their Customer Identity and Access Management requirements, the identity architect learns that the brand experience is different for each of the customer's sub-brands and each of these branded experiences must be carried through the login experience depending on which sub-brand the user is logging into.
Which solution should the architect recommend to support scalability and reduce maintenance costs, if the organization has more than 150 sub-brands?
- A. Assign each sub-brand a unique Experience ID and use the Experience ID to dynamically brand the login experience.
- B. Use Audiences to customize the login experience for each sub-brand and pass an audience ID to the community during the OAuth and Security Assertion Markup Language (SAML) flows.
- C. Create a community subdomain for each sub-brand and customize the look and feel of the Login page for each community subdomain to match the brand.
- D. Create a separate Salesforce org for each sub-brand so that each sub-brand has complete control over the user experience.
Answer: A
NEW QUESTION 3
IT security at Unversal Containers (UC) us concerned about recent phishing scams targeting its users and wants to add additional layers of login protection. What should an Architect recommend to address the issue?
- A. Use the Salesforce Authenticator mobile app with two-step verification
- B. Lock sessions to the IP address from which they originated.
- C. Increase Password complexity requirements in Salesforce.
- D. Implement Single Sign-on using a corporate Identity store.
Answer: A
NEW QUESTION 4
Universal Containers (UC) uses Salesforce as a CRM and identity provider (IdP) for their Sales Team to seamlessly login to intemaJ portals. The IT team at UC is now evaluating Salesforce to act as an IdP for its remaining employees.
Which Salesforce license is required to fulfill this requirement?
- A. External Identity
- B. Identity Verification
- C. Identity Connect
- D. Identity Only
Answer: D
NEW QUESTION 5
Universal Containers (UC) wants its closed Won opportunities to be synced to a Data warehouse in near real time. UC has implemented Outbound Message to enable near real-time data sync. UC wants to ensure that communication between Salesforce and Target System is secure. What certificate is sent along with the Outbound Message?
- A. The Self-signed Certificates from the Certificate & Key Management menu.
- B. The default client Certificate from the Develop--> API menu.
- C. The default client Certificate or the Certificate and Key Management menu.
- D. The CA-signed Certificate from the Certificate and Key Management Menu.
Answer: B
NEW QUESTION 6
Universal containers (UC) has built a custom based Two-factor Authentication (2fa) system for their existing on-premise applications. Thru are now implementing salesforce and would like to enable a Two-factor login process for it, as well. What is the recommended solution an architect should consider?
- A. Replace the custom 2fa system with salesforce 2fa for on-premise application and salesforce.
- B. Use the custom 2fa system for on-premise applications and native 2fa for salesforce.
- C. Replace the custom 2fa system with an app exchange app that supports on-premise applications and salesforce.
- D. Use custom login flows to connect to the existing custom 2fa system for use in salesforce.
Answer: D
NEW QUESTION 7
Universal containers (UC) is setting up their customer Community self-registration process. They are uncomfortable with the idea of assigning new users to a default account record. What will happen when customers self-register in the community?
- A. The self-registration process will produce an error to the user.
- B. The self-registration page will ask user to select an account.
- C. The self-registration process will create a person Account record.
- D. The self-registration page will create a new account record.
Answer: A
NEW QUESTION 8
Universal Containers (UC) has a classified information system that its call center team uses only when they are working on a case with a record type "Classified". They are only allowed to access the system when they own an open "Classified" case, and their access to the system is removed at all other times. They would like to implement SAML SSO eith Salesforce as the Idp, and automatically allow or deny the staff's access to the classified information system based on whether they currently own an open "Classified" case record when they try to access the system using SSO. What is the recommended solution for automatically allowing or denying the access to the classified information system based on the open "classified" case record criteria?
- A. Use Salesforce reports to identify users that currently owns open "Classified" cases and should be granted access to the Classified information system.
- B. Use Apex trigger on case to dynamically assign permission Sets that Grant access when an user is assigned with an open "Classified" case, and remove it when the case is closed.
- C. Use Custom SAML JIT Provisioning to dynamically query the user's open "Classified" cases when attempting to access the classified information system.
- D. Use a Common Connected App Handler using Apex to dynamically allow access to the system based on whether the staff owns any open "Classified" Cases.
Answer: D
NEW QUESTION 9
A global company's Salesforce Identity Architect is reviewing its Salesforce production org login history and is seeing some intermittent Security Assertion Markup Language (SAML SSO) 'Replay Detected and Assertion Invalid' login errors.
Which two issues would cause these errors? Choose 2 answers
- A. The subject element is missing from the assertion sent to salesforce.
- B. The certificate loaded into SSO configuration does not match the certificate used by the IdP.
- C. The current time setting of the company's identity provider (IdP) and Salesforce platform is out of sync by more than eight minutes.
- D. The assertion sent to 5alesforce contains an assertion ID previously used.
Answer: AD
NEW QUESTION 10
How should an Architect force users to authenticate with Two-factor Authentication (2FA) for Salesforce only when not connected to an internal company network?
- A. Use Custom Login Flows with Apex to detect the user's IP address and prompt for 2FA if needed.
- B. Add the list of company's network IP addresses to the Login Range list under 2FA Setup.
- C. Use an Apex Trigger on the UserLogin object to detect the user's IP address and prompt for 2FA if needed.
- D. Apply the "Two-factor Authentication for User Interface Logins" permission and Login IP Ranges for all Profiles.
Answer: A
NEW QUESTION 11
Universal Containers (UC) uses a home-grown Employee portal for their employees to collaborate. UC decides to use Salesforce Ideas to allow employees to post Ideas from the Employee portal. When users click on some of the links in the Employee portal, the users should be redirected to Salesforce, authenticated, and presented with the relevant pages. What OAuth flow is best suited for this scenario?
- A. Web Application flow
- B. SAML Bearer Assertion flow
- C. User-Agent flow
- D. Web Server flow
Answer: D
NEW QUESTION 12
An Identity and Access Management (IAM) Architect is recommending Identity Connect to integrate Microsoft Active Directory (AD) with Salesforce for user provisioning, deprovisioning and single sign-on (SSO).
Which feature of Identity Connect is applicable for this scenano?
- A. When Identity Connect is in place, if a user is deprovisioned in an on-premise AD, the user's Salesforce session Is revokedImmediately.
- B. If the number of provisioned users exceeds Salesforce licence allowances, identity Connect will start disabling the existingSalesforce users in First-in, First-out (FIFO) fashion.
- C. Identity Connect can be deployed as a managed package on salesforce org, leveraging High Availability of Salesforce Platformout-of-the-box.
- D. When configured, Identity Connect acts as an identity provider to both Active Directory and Salesforce,thus providing SSO as a default feature.
Answer: A
NEW QUESTION 13
Ttie executive sponsor for an organization has asked if Salesforce supports the ability to embed a login widget into its service providers in order to create a more seamless user experience.
What should be used and considered before recommending it as a solution on the Salesforce Platform?
- A. OpenID Connect Web Server Flo
- B. Determine if the service provider is secure enough to store the client secret on.
- C. Embedded Logi
- D. Identify what level of UI customization will be required to make it match the service providers look and feel.
- E. Salesforce REST api
- F. Ensure that Secure Sockets Layer (SSL) connection for the integration is used.
- G. Embedded Logi
- H. Consider whether or not it relies on third party cookies which can cause browser compatibility issues.
Answer: C
NEW QUESTION 14
A company with 15,000 employees is using Salesforce and would like to take the necessary steps to highlight or curb fraudulent activity.
Which tool should be used to track login data, such as the average number of logins, who logged in more than the average number of times and who logged in during non-business hours?
- A. Login Forensics
- B. Login Report
- C. Login Inspector
- D. Login History
Answer: A
NEW QUESTION 15
The security team at Universal Containers (UC) has identified exporting reports as a high-risk action and would like to require users to be logged into Salesforce with their Active Directory (AD) credentials when doing so. For all other users of Salesforce, users should be allowed to use AD Credentials or Salesforce credentials. What solution should be recommended to prevent exporting reports except when logged in using AD credentials while maintaining the ability to view reports when logged in with Salesforce credentials?
- A. Use SAML Federated Authentication and block access to reports when accessed through a Standard Assurance session.
- B. Use SAML Federated Authentication and Custom SAML JIT Provisioning to dynamically and or remove a permission set that grants the Export Reports Permission.
- C. Use SAML federated Authentication, treat SAML Sessions as High Assurance, and raise the session level required for exporting reports.
- D. Use SAML federated Authentication with a Login Flow to dynamically add or remove a Permission Set that grants the Export Reports Permission.
Answer: C
NEW QUESTION 16
Universal Containers (UC) has implemented SAML-based Single Sign-On to provide seamless access to its Salesforce Orgs, financial system, and CPQ system. Below is the SSO implementation landscape.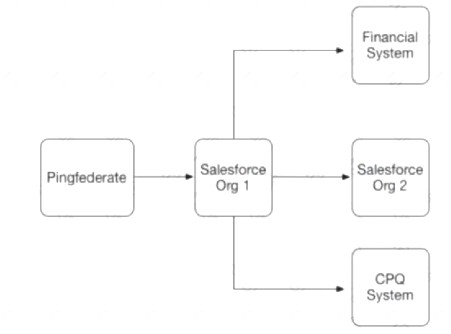
What role combination is represented by the systems in this scenario''
- A. Financial System and CPQ System are the only Service Providers.
- B. Salesforce Org1 and Salesforce Org2 are the only Service Providers.
- C. Salesforce Org1 and Salesforce Org2 are acting as Identity Providers.
- D. Salesforce Org1 and PingFederate are acting as Identity Providers.
Answer: D
NEW QUESTION 17
......
P.S. Easily pass Identity-and-Access-Management-Designer Exam with 196 Q&As Certshared Dumps & pdf Version, Welcome to Download the Newest Certshared Identity-and-Access-Management-Designer Dumps: https://www.certshared.com/exam/Identity-and-Access-Management-Designer/ (196 New Questions)
