JN0-230 Exam
All About Precise JN0-230 Testing Material

Exam Code: JN0-230 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Security - Associate (JNCIA-SEC)
Certification Provider: Juniper
Free Today! Guaranteed Training- Pass JN0-230 Exam.
Online Juniper JN0-230 free dumps demo Below:
NEW QUESTION 1
You configure and applied several global policies and some of the policies have overlapping match criteria.
- A. In this scenario, how are these global policies applies?
- B. The first matched policy is the only policy applied.
- C. The most restrictive that matches is applied.
- D. The least restrictive policy that matches is applied.
Answer: A
NEW QUESTION 2
Which UTM feature should you use to protect users from visiting certain blacklisted websites?
- A. Content filtering
- B. Web filtering
- C. Antivirus
- D. antispam
Answer: B
NEW QUESTION 3
Which security feature is applied to traffic on an SRX Series device when the device is running n packet mode?
- A. Sky ATP
- B. ALGs
- C. Firewall filters
- D. Unified policies
Answer: C
NEW QUESTION 4
You are designing a new security policy on an SRX Series device. You must block an application and log all occurrence of the application access attempts.
In this scenario, which two actions must be enabled in the security policy? (Choose two.)
- A. Log the session initiations
- B. Enable a reject action
- C. Log the session closures
- D. Enable a deny action
Answer: AD
NEW QUESTION 5
Which two statements are true about UTM on an SRX340? (Choose two.)
- A. A default UTM policy is created.
- B. No default profile is created.
- C. No default UTM policy is created
- D. A default UTM profile is created
Answer: BC
NEW QUESTION 6
Which two statements are true about security policy actions? (Choose two.)
- A. The reject action drops the traffic and sends a message to the source device.
- B. The deny action silently drop the traffic.
- C. The deny action drops the traffic and sends a message to the source device.
- D. The reject action silently drops the traffic.
Answer: AB
NEW QUESTION 7
Exhibit.
Which two statements are true? (Choose two.)
- A. Logs for this security policy are generated.
- B. Logs for this security policy are not generated.
- C. Traffic static for this security policy are not generated.
- D. Traffic statistics for this security policy are generated.
Answer: AD
NEW QUESTION 8
You want to automatically generate the encryption and authentication keys during IPsec VPN establishment. What would be used to accomplish this task?
- A. IPsec
- B. Diffie_Hellman
- C. Main mode
- D. Aggregate mode
Answer: B
NEW QUESTION 9
Which two statements are correct about using global-based policies over zone-based policies? (Choose two.)
- A. With global-based policies, you do not need to specify a destination zone in the match criteria.
- B. With global-based policies, you do not need to specify a source zone in the match criteria.
- C. With global-based policies, you do not need to specify a destination address in the match criteria.
- D. With global-based policies, you do not need to specify a source address in the match criteria.
Answer: AB
NEW QUESTION 10
You have configured antispam to allow e-mail from example.com, however the logs you see thatjcart@example.comis blocked
Referring to the exhibit.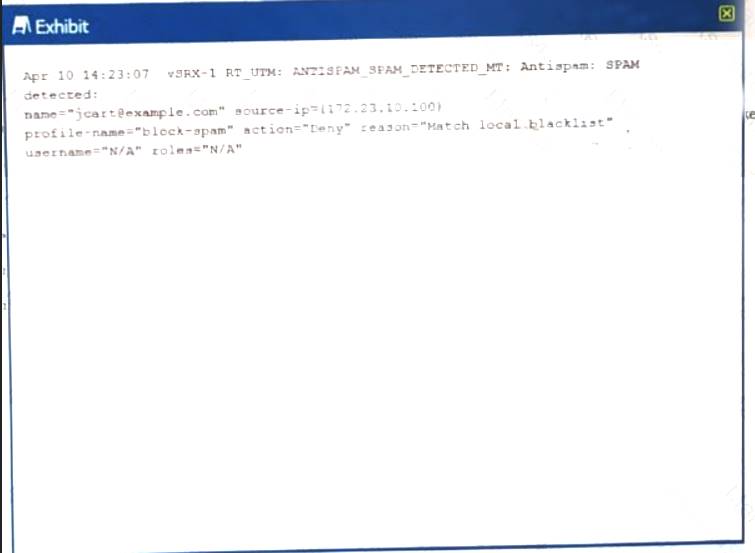
What are two ways to solve this problem?
- A. Verify connectivity with the SBL server.
- B. Addjcart@exmple.comto the profile antispam address whitelist.
- C. Deletejcart@example.comfrom the profile antispam address blacklist
- D. Deletejcart@example.comfrom the profile antispam address whitelist
Answer: BC
NEW QUESTION 11
Which two actions are performed on an incoming packet matching an existing session? (Choose two.)
- A. Zone processing
- B. Security policy evolution
- C. Service ALG processing
- D. Screens processing
Answer: CD
NEW QUESTION 12
You want to generate reports from the l-Web on an SRX Series device. Which logging mode would you use in this scenario?
- A. Syslog
- B. Stream
- C. Event
- D. local
Answer: B
NEW QUESTION 13
What are configuring the antispam UTM feature on an SRX Series device.
Which two actions would be performed by the SRX Series device for e-mail that is identified as spam? (Choose two.)
- A. Tag the e-mail
- B. Queue the e-mail
- C. Block the e-mail
- D. Quarantine e-mail
Answer: AC
NEW QUESTION 14
Which two match conditions would be used in both static NAT and destination NAT rule sets? (Choose two.)
- A. Destination zone
- B. Destination interface
- C. Source interface
- D. Source zone
Answer: BD
NEW QUESTION 15
A new SRX Series device has been delivered to your location. The device has the factory-default configuration loaded. You have powered on the device and connected to the console port.
What would you use to log into the device to begin the initial configuration?
- A. Root with a password of juniper’’
- B. Root with no password
- C. Admin with password
- D. Admin with a password ‘’juniper’’
Answer: B
NEW QUESTION 16
Your company uses SRX Series devices to secure the edge of the network. You are asked protect the company from ransom ware attacks.
Which solution will satisfy this requirement?
- A. Sky ATP
- B. AppSecure
- C. Unified security policies
- D. screens
Answer: A
NEW QUESTION 17
The Sky ATP premium or basic-Threat Feed license is needed fort which two features? (Choose two.)
- A. Outbound protection
- B. C&C feeds
- C. Executable inspection
- D. Custom feeds
Answer: BD
NEW QUESTION 18
You are concerned that unauthorized traffic is using non-standardized ports on your network.
In this scenario, which type of security feature should you implement?
- A. Application firewall
- B. Sky ATP
- C. Firewall filters
- D. Zone-based policies
Answer: A
NEW QUESTION 19
What must you do first to use the Monitor/Alarms/Policy Log workspace in J-Web?
- A. You must enable logging that uses the SD-Syslog format.
- B. You must enable security logging that uses the TLS transport mode.
- C. You must enable stream mode security logging on the SRX Series device.
- D. You must enable event mode security logging on the SRX Series device.
Answer: D
NEW QUESTION 20
Which security object defines a source or destination IP address that is used for an employee Workstation?
- A. Zone
- B. Screen
- C. Address book entry
- D. scheduler
Answer: C
NEW QUESTION 21
Which statements about NAT are correct? (Choose two.)
- A. When multiple NAT rules have overlapping match conditions, the rule listed first is chosen.
- B. Source NAT translates the source port and destination IP address.
- C. Source NAT translates the source IP address of packet.
- D. When multiple NAT rules have overlapping match conditions, the most specific rule is chosen.
Answer: AC
NEW QUESTION 22
......
P.S. Certstest now are offering 100% pass ensure JN0-230 dumps! All JN0-230 exam questions have been updated with correct answers: https://www.certstest.com/dumps/JN0-230/ (65 New Questions)
