PCCET Exam
Replace Palo Alto Networks Certified Cybersecurity Entry-level Technician PCCET Testing Engine

Testking offers free demo for PCCET exam. "Palo Alto Networks Certified Cybersecurity Entry-level Technician", also known as PCCET exam, is a Paloalto-Networks Certification. This set of posts, Passing the Paloalto-Networks PCCET exam, will help you answer those questions. The PCCET Questions & Answers covers all the knowledge points of the real exam. 100% real Paloalto-Networks PCCET exams and revised by experts!
Also have PCCET free dumps questions for you:
NEW QUESTION 1
In addition to local analysis, what can send unknown files to WildFire for discovery and deeper analysis to rapidly detect potentially unknown malware?
- A. Cortex XDR
- B. AutoFocus
- C. MineMild
- D. Cortex XSOAR
Answer: A
NEW QUESTION 2
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
- A. Expedition
- B. AutoFocus
- C. MineMeld
- D. Cortex XDR
Answer: D
NEW QUESTION 3
SecOps consists of interfaces, visibility, technology, and which other three elements?
(Choose three.)
- A. People
- B. Accessibility
- C. Processes
- D. Understanding
- E. Business
Answer: ACE
NEW QUESTION 4
What is the key to “taking down” a botnet?
- A. prevent bots from communicating with the C2
- B. install openvas software on endpoints
- C. use LDAP as a directory service
- D. block Docker engine software on endpoints
Answer: A
NEW QUESTION 5
How does DevSecOps improve the Continuous Integration/Continuous Deployment (CI/CD) pipeline?
- A. DevSecOps improves pipeline security by assigning the security team as the lead team for continuous deployment
- B. DevSecOps ensures the pipeline has horizontal intersections for application code deployment
- C. DevSecOps unites the Security team with the Development and Operations teams to integrate security into the CI/CD pipeline
- D. DevSecOps does security checking after the application code has been processed through the CI/CDpipeline
Answer: C
NEW QUESTION 6
Which Palo Alto Networks product provides playbooks with 300+ multivendor integrations that help solve any security use case?
- A. Cortex XSOAR
- B. Prisma Cloud
- C. AutoFocus
- D. Cortex XDR
Answer: A
NEW QUESTION 7
Which Palo Alto Networks subscription service complements App-ID by enabling you to configure the next-generation firewall to identify and control access to websites and to protect your organization from websites hosting malware and phishing pages?
- A. Threat Prevention
- B. DNS Security
- C. WildFire
- D. URL Filtering
Answer: D
NEW QUESTION 8
Which network firewall operates up to Layer 4 (Transport layer) of the OSI model and maintains information about the communication sessions which have been established between hosts on trusted and untrusted networks?
- A. Group policy
- B. Stateless
- C. Stateful
- D. Static packet-filter
Answer: C
NEW QUESTION 9
Which type of Software as a Service (SaaS) application provides business benefits, is fast to deploy, requires minimal cost and is infinitely scalable?
- A. Benign
- B. Tolerated
- C. Sanctioned
- D. Secure
Answer: C
NEW QUESTION 10
Which technique changes protocols at random during a session?
- A. use of non-standard ports
- B. port hopping
- C. hiding within SSL encryption
- D. tunneling within commonly used services
Answer: B
NEW QUESTION 11
Which subnet does the host 192.168.19.36/27 belong?
- A. 192.168.19.0
- B. 192.168.19.16
- C. 192.168.19.64
- D. 192.168.19.32
Answer: D
NEW QUESTION 12
Which type of LAN technology is being displayed in the diagram?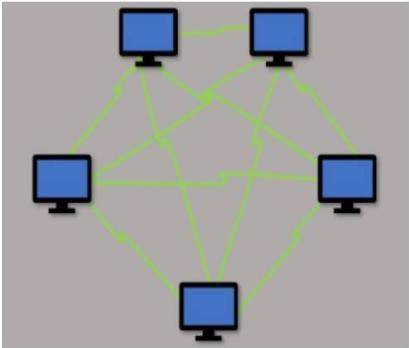
- A. Star Topology
- B. Spine Leaf Topology
- C. Mesh Topology
- D. Bus Topology
Answer: C
NEW QUESTION 13
Which option describes the “selective network security virtualization” phase of incrementally
transforming data centers?
- A. during the selective network security virtualization phase, all intra-host communication paths are strictly controlled
- B. during the selective network security virtualization phase, all intra-host traffic is forwarded to a Web proxy server
- C. during the selective network security virtualization phase, all intra-host traffic is encapsulated and encrypted using the IPSEC protocol
- D. during the selective network security virtualization phase, all intra-host traffic is load balanced
Answer: A
NEW QUESTION 14
An Administrator wants to maximize the use of a network address. The network is 192.168.6.0/24 and there are three subnets that need to be created that can not overlap. Which subnet would you use for the network with 120 hosts?
Requirements for the three subnets:
Subnet 1: 3 host addresses
Subnet 2: 25 host addresses
Subnet 3: 120 host addresses
- A. 192.168.6.168/30
- B. 192.168.6.0/25
- C. 192.168.6.160/29
- D. 192.168.6.128/27
Answer: B
NEW QUESTION 15
Why is it important to protect East-West traffic within a private cloud?
- A. All traffic contains threats, so enterprises must protect against threats across the entire network
- B. East-West traffic contains more session-oriented traffic than other traffic
- C. East-West traffic contains more threats than other traffic
- D. East-West traffic uses IPv6 which is less secure than IPv4
Answer: A
NEW QUESTION 16
Which key component is used to configure a static route?
- A. router ID
- B. enable setting
- C. routing protocol
- D. next hop IP address
Answer: D
NEW QUESTION 17
Which statement describes DevOps?
- A. DevOps is its own separate team
- B. DevOps is a set of tools that assists the Development and Operations teams throughout the software delivery process
- C. DevOps is a combination of the Development and Operations teams
- D. DevOps is a culture that unites the Development and Operations teams throughout the software delivery process
Answer: B
NEW QUESTION 18
Which product from Palo Alto Networks extends the Security Operating Platform with the global threat intelligence and attack context needed to accelerate analysis, forensics, and hunting workflows?
- A. Global Protect
- B. WildFire
- C. AutoFocus
- D. STIX
Answer: C
NEW QUESTION 19
......
P.S. Easily pass PCCET Exam with 75 Q&As DumpSolutions.com Dumps & pdf Version, Welcome to Download the Newest DumpSolutions.com PCCET Dumps: https://www.dumpsolutions.com/PCCET-dumps/ (75 New Questions)
