PSE-Cortex Exam
Up To The Minute Palo Alto Networks System Engineer - Cortex Professional PSE-Cortex Exams

Want to know Actualtests PSE-Cortex Exam practice test features? Want to lear more about Paloalto-Networks Palo Alto Networks System Engineer - Cortex Professional certification experience? Study Verified Paloalto-Networks PSE-Cortex answers to Far out PSE-Cortex questions at Actualtests. Gat a success with an absolute guarantee to pass Paloalto-Networks PSE-Cortex (Palo Alto Networks System Engineer - Cortex Professional) test on your first attempt.
Paloalto-Networks PSE-Cortex Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
What is the difference between an exception and an exclusion?
- A. An exception is based on rules and exclusions are on alerts
- B. An exclusion is based on rules and exceptions are based on alerts.
- C. An exception does not exist
- D. An exclusion does not exist
Answer: A
NEW QUESTION 2
Which three Demisto incident type features can be customized under Settings > Advanced > Incident Types? (Choose three.)
- A. Define whether a playbook runs automatically when an incident type is encountered
- B. Set reminders for an incident SLA
- C. Add new fields to an incident type
- D. Define the way that incidents of a specific type are displayed in the system
- E. Drop new incidents of the same type that contain similar information
Answer: ABD
NEW QUESTION 3
In an Air-Gapped environment where the Docker package was manually installed after the Cortex XSOAR installation which action allows Cortex XSOAR to access Docker?
- A. create a “docker” group and add the "Cortex XSOAR" or "demisto" user to this group
- B. create a "Cortex XSOAR' or "demisto" group and add the "docker" user to this group
- C. disable the Cortex XSOAR service
- D. enable the docker service
Answer: A
NEW QUESTION 4
During the TMS instance activation, a tenant (Customer) provides the following information for the fields in the Activation - Step 2 of 2 window.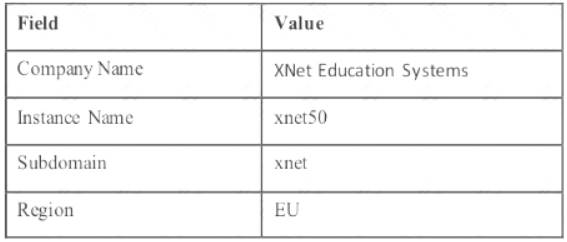
During the service instance provisioning which three DNS host names are created? (Choose three.)
- A. cc-xnet50.traps.paloaltonetworks.com
- B. hc-xnet50.traps.paloaltonetworks.com
- C. cc-xnet.traps.paloaltonetworks.com
- D. cc.xnet50traps.paloaltonetworks.com
- E. xnettraps.paloaltonetworks.com
- F. ch-xnet.traps.paloaltonetworks.com
Answer: ACF
NEW QUESTION 5
What method does the Traps agent use to identify malware during a scheduled scan?
- A. Heuristic analysis
- B. Local analysis
- C. Signature comparison
- D. WildFire hash comparison and dynamic analysis
Answer: D
NEW QUESTION 6
Which two items are stitched to the Cortex XDR causality chain'' (Choose two)
- A. firewall alert
- B. SIEM alert
- C. full URL
- D. registry set value
Answer: AC
NEW QUESTION 7
Which two filter operators are available in Cortex XDR? (Choose two.)
- A. not Contains
- B. !*
- C. =>
- D. < >
Answer: AB
Explanation:
https://docs.paloaltonetworks.com/cortex/cortex-xdr/cortex-xdr-pro-admin/get-started-with-cortex-xdr-pro/use-c
NEW QUESTION 8
What are process exceptions used for?
- A. whitelist programs from WildFire analysis
- B. permit processes to load specific DLLs
- C. change the WildFire verdict for a given executable
- D. disable an EPM for a particular process
Answer: D
NEW QUESTION 9
How many use cases should a POC success criteria document include?
- A. only 1
- B. 3 or more
- C. no more than 5
- D. no more than 2
Answer: A
NEW QUESTION 10
An Administrator is alerted to a Suspicious Process Creation security event from multiple users.
The users believe that these events are false positives Which two steps should the administrator take to confirm the false positives and create an exception? (Choose two )
- A. With the Malware Security profile, disable the "Prevent Malicious Child Process Execution" module
- B. Within the Malware Security profile add the specific parent process, child process, and command line argument to the child process whitelist
- C. In the Cortex XDR security event, review the specific parent process, child process, and command line arguments
- D. Contact support and ask for a security exception.
Answer: BC
NEW QUESTION 11
Which two log types should be configured for firewall forwarding to the Cortex Data Lake for use by Cortex XDR? (Choose two)
- A. Security Event
- B. HIP
- C. Correlation
- D. Analytics
Answer: AB
NEW QUESTION 12
The certificate used for decryption was installed as a trusted toot CA certificate to ensure communication between the Cortex XDR Agent and Cortex XDR Management Console. What action needs to be taken if the administrator determines the Cortex XDR Agents are not communicating with the Cortex XDR Management Console?
- A. add paloaltonetworks.com to the SSL Decryption Exclusion list
- B. enable SSL decryption
- C. disable SSL decryption
- D. reinstall the root CA certificate
Answer: D
NEW QUESTION 13
When a Demisto Engine is part of a Load-Balancing group it?
- A. Must be in a Load-Balancing group with at least another 3 members
- B. It must have port 443 open to allow the Demisto Server to establish a connection
- C. Can be used separately as an engine, only if connected to the Demisto Server directly
- D. Cannot be used separately and does not appear in the in the engines drop-down menu when configuring an integration instance
Answer: D
NEW QUESTION 14
Which option is required to prepare the VDI Golden Image?
- A. Configure the Golden Image as a persistent VDI
- B. Use the Cortex XDR VDI tool to obtain verdicts for all PE files
- C. Install the Cortex XOR Agent on the local machine
- D. Run the Cortex VDI conversion tool
Answer: B
NEW QUESTION 15
An adversary is attempting to communicate with malware running on your network for the purpose of controlling malware activities or for ex filtrating data from your network. Which Cortex XDR Analytics alert is this activity most likely to trigger'?
- A. Uncommon Local Scheduled Task Creation
- B. Malware
- C. New Administrative Behavior
- D. DNS Tunneling
Answer: B
NEW QUESTION 16
What is the result of creating an exception from an exploit security event?
- A. White lists the process from Wild Fire analysis
- B. exempts the user from generating events for 24 hours
- C. exempts administrators from generating alerts for 24 hours
- D. disables the triggered EPM for the host and process involve
Answer: D
NEW QUESTION 17
An administrator of a Cortex XDR protected production environment would like to test its ability to protect users from a known flash player exploit.
What is the safest way to do it?
- A. The administrator should attach a copy of the weapomzed flash file to an email, send the email to a selected group of employees, and monitor the Events tab on the Cortex XDR console
- B. The administrator should use the Cortex XDR tray icon to confirm his corporate laptop is fully protected then open the weaponized flash file on his machine, and monitor the Events tab on the Cortex XDR console.
- C. The administrator should create a non-production Cortex XDR test environment that accurately represents the production environment, introduce the weaponized flash file, and monitor the Events tab on the Cortex XDR console.
- D. The administrator should place a copy of the weaponized flash file on several USB drives, scatter them around the office and monitor the Events tab on the Cortex XDR console
Answer: C
NEW QUESTION 18
......
Recommend!! Get the Full PSE-Cortex dumps in VCE and PDF From Dumpscollection.com, Welcome to Download: https://www.dumpscollection.net/dumps/PSE-Cortex/ (New 60 Q&As Version)
