SY0-601 Exam
How Many Questions Of SY0-601 Preparation Labs

we provide Printable CompTIA SY0-601 vce which are the best for clearing SY0-601 test, and to get certified by CompTIA CompTIA Security+ Exam. The SY0-601 Questions & Answers covers all the knowledge points of the real SY0-601 exam. Crack your CompTIA SY0-601 Exam with latest dumps, guaranteed!
Online CompTIA SY0-601 free dumps demo Below:
NEW QUESTION 1
The IT department’s on-site developer has been with the team for many years. Each time an application is released, the security team is able to identify multiple vulnerabilities. Which of the following would BEST help the team ensure the application is ready to be released to production?
- A. Limit the use of third-party libraries.
- B. Prevent data exposure queries.
- C. Obfuscate the source code.
- D. Submit the application to QA before releasing it.
Answer: D
NEW QUESTION 2
A security analyst discovers several .jpg photos from a cellular phone during a forensics investigation involving a compromised system. The analyst runs a forensics tool to gather file metadata. Which of the following would be part of the images if all the metadata is still intact?
- A. The GPS location
- B. When the file was deleted
- C. The total number of print jobs
- D. The number of copies made
Answer: A
NEW QUESTION 3
An enterprise has hired an outside security firm to conduct penetration testing on its network and applications. The firm has only been given the documentation available to the customers of the applications. Which of the following BEST represents the type of testing that will occur?
- A. Bug bounty
- B. Black-box
- C. Gray-box
- D. White-box
Answer: A
NEW QUESTION 4
A network engineer has been asked to investigate why several wireless barcode scanners and wireless computers in a warehouse have intermittent connectivity to the shipping server. The barcode scanners and computers are all on forklift trucks and move around the warehouse during their regular use. Which of the following should the engineer do to determine the issue? (Choose two.)
- A. Perform a site survey
- B. Deploy an FTK Imager
- C. Create a heat map
- D. Scan for rogue access points
- E. Upgrade the security protocols
- F. Install a captive portal
Answer: AC
NEW QUESTION 5
A security engineer is setting up passwordless authentication for the first time. INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.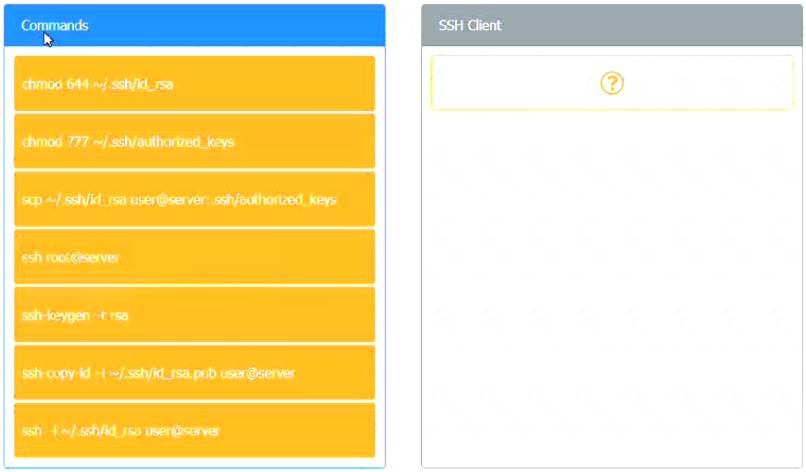
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 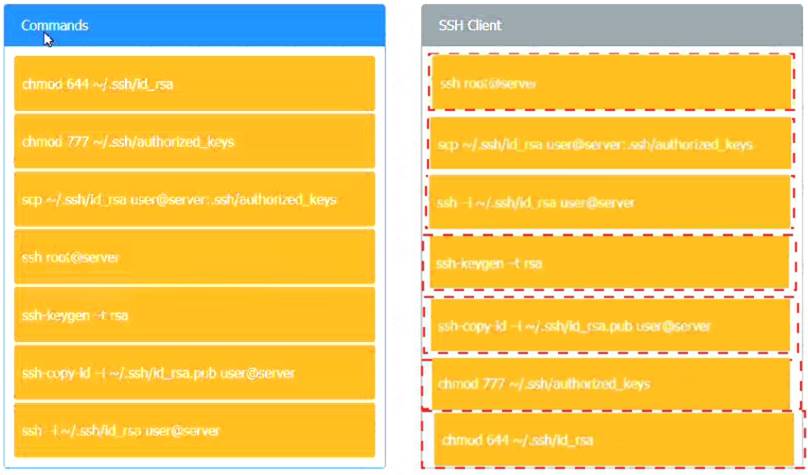
NEW QUESTION 6
A company wants to deploy PKI on its Internet-facing website. The applications that are currently deployed are: www.company.com (main website)
www.company.com (main website) contactus.company.com (for locating a nearby location)
contactus.company.com (for locating a nearby location)  quotes.company.com (for requesting a price quote)
quotes.company.com (for requesting a price quote)
The company wants to purchase one SSL certificate that will work for all the existing applications and any future applications that follow the same naming conventions, such as store.company.com. Which of the following certificate types would BEST meet the requirements?
- A. SAN
- B. Wildcard
- C. Extended validation
- D. Self-signed
Answer: B
NEW QUESTION 7
A root cause analysis reveals that a web application outage was caused by one of the company’s developers uploading a newer version of the third-party libraries that were shared among several applications. Which of the following implementations would be BEST to prevent the issue from reoccurring?
- A. CASB
- B. SWG
- C. Containerization
- D. Automated failover
Answer: C
NEW QUESTION 8
A security administrator checks the table of a network switch, which shows the following output: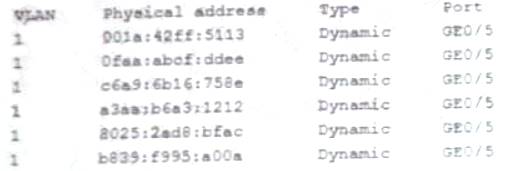
Which of the following is happening to this switch?
- A. MAC Flooding
- B. DNS poisoning
- C. MAC cloning
- D. ARP poisoning
Answer: A
NEW QUESTION 9
A smart switch has the ability to monitor electrical levels and shut off power to a building in the event of power surge or other fault situation. The switch was installed on a wired network in a hospital and is monitored by the facilities department via a cloud application. The security administrator isolated the switch on a separate VLAN and set up a patch routine. Which of the following steps should also be taken to harden the smart switch?
- A. Set up an air gap for the switch.
- B. Change the default password for the switch.
- C. Place the switch In a Faraday cage.
- D. Install a cable lock on the switch
Answer: B
NEW QUESTION 10
Which of the following types of controls is a turnstile?
- A. Physical
- B. Detective
- C. Corrective
- D. Technical
Answer: A
NEW QUESTION 11
A company recently moved sensitive videos between on-premises. Company-owned websites. The company then learned the videos had been uploaded and shared to the internet. Which of the following would MOST likely allow the company to find the cause?
- A. Checksums
- B. Watermarks
- C. Oder of volatility
- D. A log analysis
- E. A right-to-audit clause
Answer: D
NEW QUESTION 12
An organization has been experiencing outages during holiday sales and needs to ensure availability of its point-of-sale systems The IT administrator has been asked to improve both server-data fault tolerance and site availability under high consumer load Which of the following are the BEST options to accomplish this objective'? (Select TWO)
- A. Load balancing
- B. Incremental backups
- C. UPS
- D. RAID
- E. Dual power supply
- F. NIC teaming
Answer: AD
NEW QUESTION 13
A user recently attended an exposition and received some digital promotional materials The user later noticed blue boxes popping up and disappearing on the computer, and reported receiving several spam emails, which the user did not open Which of the following is MOST likely the cause of the reported issue?
- A. There was a drive-by download of malware
- B. The user installed a cryptominer
- C. The OS was corrupted
- D. There was malicious code on the USB drive
Answer: D
NEW QUESTION 14
An organization just experienced a major cyberattack modem. The attack was well coordinated sophisticated and highly skilled. Which of the following targeted the organization?
- A. Shadow IT
- B. An insider threat
- C. A hacktivist
- D. An advanced persistent threat
Answer: D
NEW QUESTION 15
An organization wants to implement a third factor to an existing multifactor authentication. The organization already uses a smart card and password. Which of the following would meet the organization’s needs for a third factor?
- A. Date of birth
- B. Fingerprints
- C. PIN
- D. TPM
Answer: B
NEW QUESTION 16
A company has drafted an insider-threat policy that prohibits the use of external storage devices. Which of the following would BEST protect the company from data exfiltration via removable media?
- A. Monitoring large data transfer transactions in the firewall logs
- B. Developing mandatory training to educate employees about the removable media policy
- C. Implementing a group policy to block user access to system files
- D. Blocking removable-media devices and write capabilities using a host-based security tool
Answer: D
NEW QUESTION 17
An organization's RPO for a critical system is two hours. The system is used Monday through Friday, from 9:00 am to 5:00 pm. Currently, the organization performs a full backup every Saturday that takes four hours to complete. Which of the following additional backup implementations would be the BEST way for the analyst to meet the business requirements?
- A. Incremental backups Monday through Friday at 6:00 p.m and differential backups hourly
- B. Full backups Monday through Friday at 6:00 p.m and incremental backups hourly.
- C. incremental backups Monday through Friday at 6:00 p.m and full backups hourly.
- D. Full backups Monday through Friday at 6:00 p.m and differential backups hourly.
Answer: A
NEW QUESTION 18
Which of the following organizational policies are MOST likely to detect fraud that is being conducted by existing employees? (Select TWO).
- A. Offboarding
- B. Mandatory vacation
- C. Job rotation
- D. Background checks
- E. Separation of duties
- F. Acceptable use
Answer: BC
NEW QUESTION 19
A security analyst is preparing a threat for an upcoming internal penetration test. The analyst needs to identify a method for determining the tactics, techniques, and procedures of a threat against the organization’s network. Which of the following will the analyst MOST likely use to accomplish the objective?
- A. A table exercise
- B. NST CSF
- C. MTRE ATT$CK
- D. OWASP
Answer: A
NEW QUESTION 20
A security administrator suspects there may be unnecessary services running on a server. Which of the following tools will the administrator MOST likely use to confirm the suspicions?
- A. Nmap
- B. Wireshark
- C. Autopsy
- D. DNSEnum
Answer: A
NEW QUESTION 21
A vulnerability assessment report will include the CVSS score of the discovered vulnerabilities because the score allows the organization to better.
- A. validate the vulnerability exists in the organization's network through penetration testing
- B. research the appropriate mitigation techniques in a vulnerability database
- C. find the software patches that are required to mitigate a vulnerability
- D. prioritize remediation of vulnerabilities based on the possible impact.
Answer: D
NEW QUESTION 22
A user is concerned that a web application will not be able to handle unexpected or random input without crashing. Which of the following BEST describes the type of testing the user should perform?
- A. Code signing
- B. Fuzzing
- C. Manual code review
- D. Dynamic code analysis
Answer: D
NEW QUESTION 23
A development team employs a practice of bringing all the code changes from multiple team members into the same development project through automation. A tool is utilized to validate the code and track source code through version control. Which of the following BEST describes this process?
- A. Continuous delivery
- B. Continuous integration
- C. Continuous validation
- D. Continuous monitoring
Answer: B
NEW QUESTION 24
......
100% Valid and Newest Version SY0-601 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/SY0-601-dumps.html (New 218 Q&As)
