jn0-333 Exam
Juniper Jn0-333 Tutorials 2021

Exam Code: jn0-333 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Security, Specialist (JNCIS-SEC)
Certification Provider: Juniper
Free Today! Guaranteed Training- Pass jn0-333 Exam.
Online Juniper jn0-333 free dumps demo Below:
NEW QUESTION 1
What are the maximum number of supported interfaces on a vSRX hosted in a VMware environment?
- A. 12
- B. 3
- C. 10
- D. 4
Answer: A
NEW QUESTION 2
After an SRX Series device processes the first packet of a session, how are subsequent packets for the same session processed?
- A. They are processed using fast-path processing.
- B. They are forwarded to the control plane for deep packet inspection.
- C. All packets are processed in the same manner.
- D. They are queued on the outbound interface until a matching security policy is found.
Answer: A
NEW QUESTION 3
You have configured source NAT with port address translation. You also need to guarantee that the same IP address is assigned from the source NAT pool to a specific host for multiple concurrent sessions.
Which NAT parameter would meet this requirement?
- A. port block-allocation
- B. port range twin-port
- C. address-persistent
- D. address-pooling paired
Answer: D
NEW QUESTION 4
Click the Exhibit button.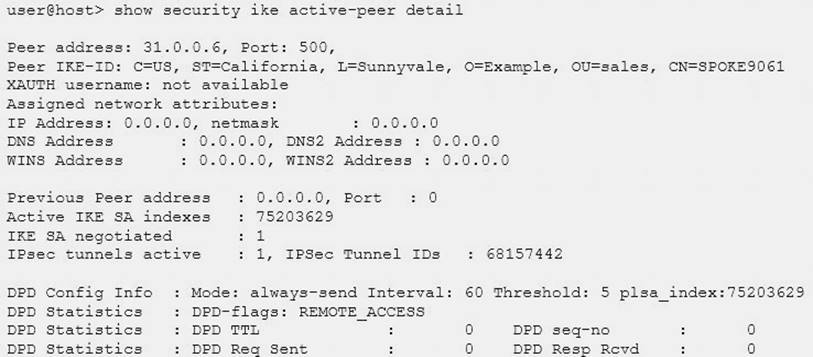
A customer would like to monitor their VPN using dead peer detection.
Referring to the exhibit, for how many minutes was the peer down before the customer was notified?
- A. 5
- B. 3
- C. 4
- D. 2
Answer: A
NEW QUESTION 5
Click the Exhibit button.
Which statement would explain why the IP-monitoring feature is functioning incorrectly?
- A. The global weight value is too large for the configured global threshold.
- B. The secondary IP address should be on a different subnet than the reth IP address.
- C. The secondary IP address is the same as the reth IP address.
- D. The monitored IP address is not on the same subnet as the reth IP address.
Answer: C
NEW QUESTION 6
Which type of VPN provides a secure method of transporting encrypted IP traffic?
- A. IPsec
- B. Layer 3 VPN
- C. VPLS
- D. Layer 2 VPN
Answer: A
NEW QUESTION 7
Which feature is used when you want to permit traffic on an SRX Series device only at specific times?
- A. scheduler
- B. pass-through authentication
- C. ALGs
- D. counters
Answer: A
NEW QUESTION 8
You want to implement IPsec on your SRX Series devices, but you do not want to use a preshared key. Which IPsec implementation should you use?
- A. public key infrastructure
- B. next-hop tunnel binding
- C. tunnel mode
- D. aggressive mode
Answer: A
NEW QUESTION 9
Click the Exhibit button.
Referring to the exhibit, which action will be taken for traffic coming from the untrust zone going to the trust zone?
- A. Source address 2001:db8::8 will be translated to 10.1.1.5.
- B. Source address 2001:db8::8 will be translated to 10.1.1.8.
- C. Source address 10.1.1.8 will be translated to 2001:db8::8.
- D. Source address 10.1.1.5 will be translated to 2001:db8::8.
Answer: B
NEW QUESTION 10
Which statement describes the function of NAT?
- A. NAT encrypts transit traffic in a tunnel.
- B. NAT detects various attacks on traffic entering a security device.
- C. NAT translates a public address to a private address.
- D. NAT restricts or permits users individually or in a group.
Answer: C
NEW QUESTION 11
Click the Exhibit button.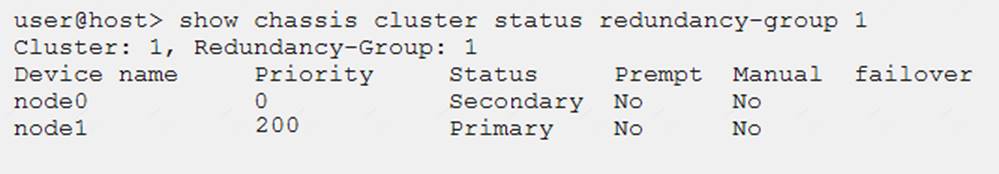
Which two statements describe the output shown in the exhibit? (Choose two.)
- A. Node 0 is controlling traffic for redundancy group 1.
- B. Node 1 is controlling traffic for redundancy group 1.
- C. Redundancy group 1 experienced an operational failure.
- D. Redundancy group 1 was administratively failed over.
Answer: BD
NEW QUESTION 12
Click the Exhibit button. Referring to the exhibit, what will happen if client 172.16.128.50 tries to connect to destination 192.168.150.3 using HTTP?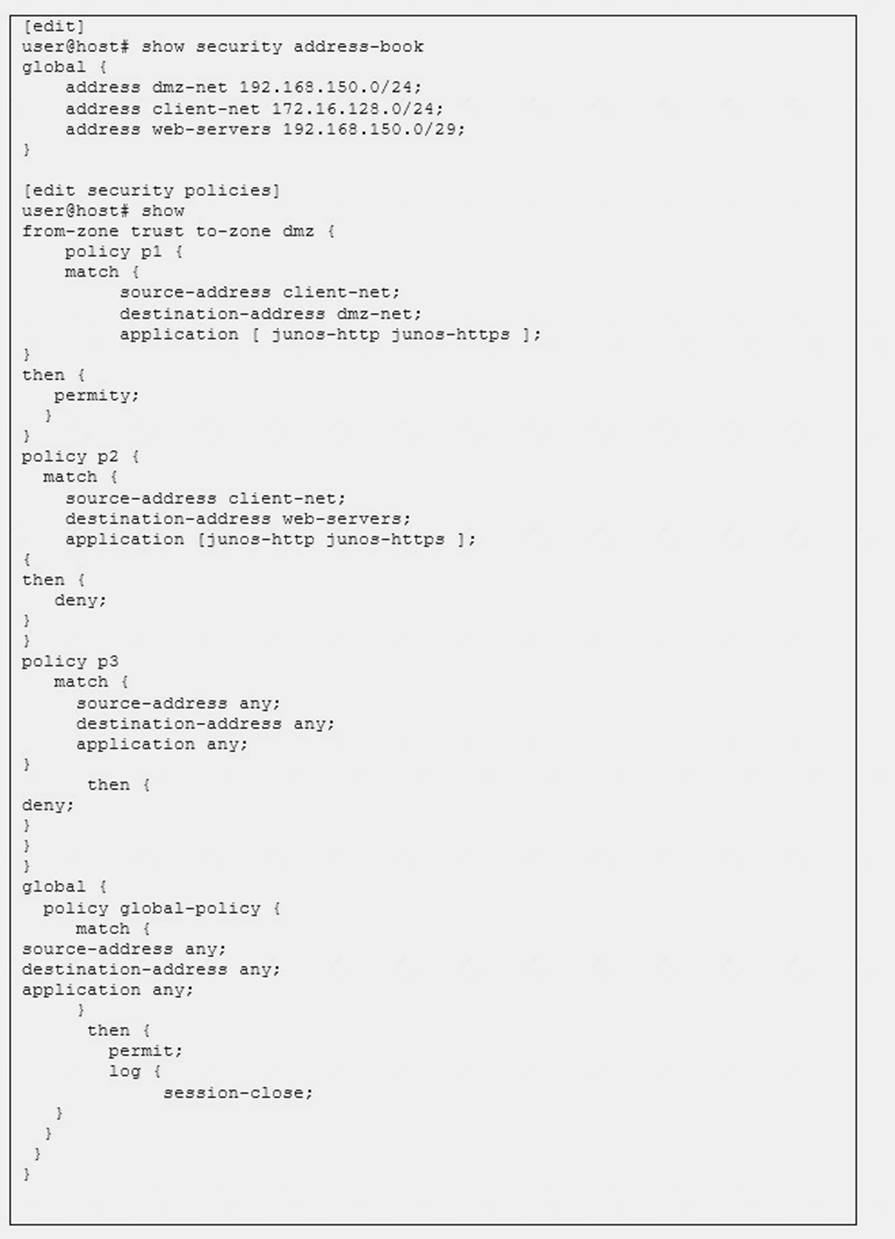
- A. The client will be permitted by policy p1.
- B. The client will be denied by policy p3.
- C. The client will be denied by policy p2.
- D. The client will be permitted by the global policy.
Answer: D
NEW QUESTION 13
You want to protect your SRX Series device from the ping-of-death attack coming from the untrust security zone.
How would you accomplish this task?
- A. Configure the host-inbound-traffic system-services ping except parameter in the untrust security zone.
- B. Configure the application tracking parameter in the untrust security zone.
- C. Configure a from-zone untrust to-zone trust security policy that blocks ICMP traffic.
- D. Configure the appropriate screen and apply it to the [edit security zone security-zone untrust] hierarchy.
Answer: D
NEW QUESTION 14
What are two valid zones available on an SRX Series device? (Choose two.)
- A. security zones
- B. policy zones
- C. transit zones
- D. functional zones
Answer: AD
NEW QUESTION 15
You have recently configured an IPsec tunnel between two SRX Series devices. One of the devices is assigned an IP address using DHCP with an IP address that changes frequently. Initial testing indicates that the IPsec tunnel is not working. Troubleshooting has revealed that Phase 1 negotiations are failing.
Which two actions would solve the problem? (Choose two.)
- A. Verify that the device with the IP address assigned by DHCP is the traffic initiator.
- B. Verify that VPN monitoring is enabled.
- C. Verify that the IKE policy is configured for aggressive mode.
- D. Verify that PKI is properly configured.
Answer: AC
NEW QUESTION 16
Click the Exhibit button.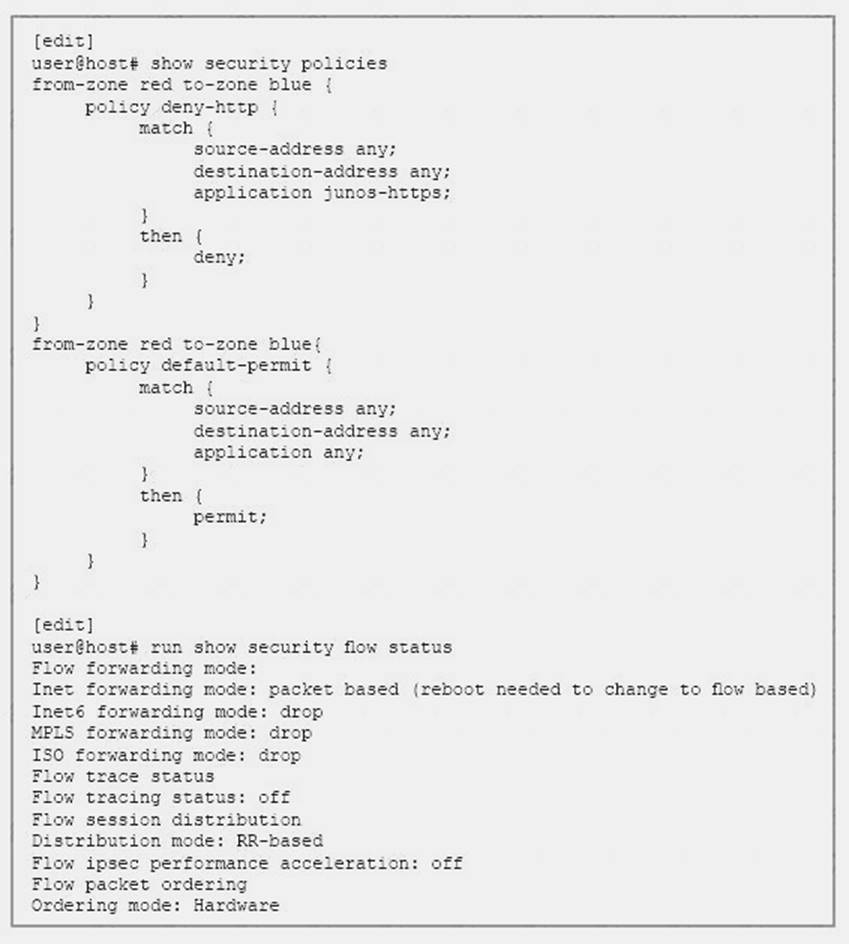
You notice that your SRX Series device is not blocking HTTP traffic as expected. Referring to the exhibit, what should you do to solve the problem?
- A. Commit the configuration.
- B. Reboot the SRX Series device.
- C. Configure the SRX Series device to operate in packet-based mode.
- D. Move the deny-http policy to the bottom of the policy list.
Answer: B
NEW QUESTION 17
Which two statements are true when implementing source NAT on an SRX Series device? (Choose two.)
- A. Source NAT is applied before the security policy search.
- B. Source NAT is applied after the route table lookup.
- C. Source NAT is applied before the route table lookup.
- D. Source NAT is applied after the security policy search.
Answer: BD
NEW QUESTION 18
Which two modes are supported during the Phase 1 IKE negotiations used to establish an IPsec tunnel? (Choose two.)
- A. transport mode
- B. aggressive mode
- C. main mode
- D. tunnel mode
Answer: BC
NEW QUESTION 19
Click the Exhibit button.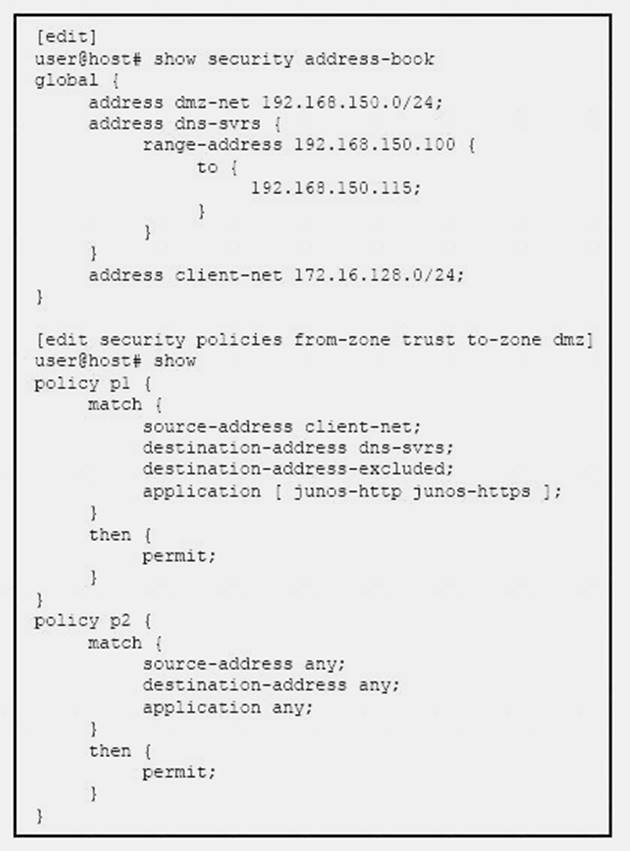
Referring to the exhibit, what will happen if client 172.16.128.50 tries to connect to destination 192.168.150.111 using HTTP?
- A. The client will be denied by policy p2.
- B. The client will be denied by policy p1.
- C. The client will be permitted by policy p2.
- D. The client will be permitted by policy p1.
Answer: D
NEW QUESTION 20
You recently configured an IPsec VPN between two SRX Series devices. You notice that the Phase 1 negotiation succeeds and the Phase 2 negotiation fails.
Which two configuration parameters should you verify are correct? (Choose two.)
- A. Verify that the IKE gateway proposals on the initiator and responder are the same.
- B. Verify that the VPN tunnel configuration references the correct IKE gateway.
- C. Verify that the IPsec policy references the correct IKE proposals.
- D. Verify that the IKE initiator is configured for main mode.
Answer: AC
NEW QUESTION 21
Which interface is used exclusively to forward Ethernet-switching traffic between two chassis cluster nodes?
- A. swfab0
- B. fxp0
- C. fab0
- D. me0
Answer: A
NEW QUESTION 22
Which statement is true about Perfect Forward Secrecy (PFS)?
- A. PFS is used to resolve compatibility issues with third-party IPsec peers.
- B. PFS is implemented during Phase 1 of IKE negotiations and decreases the amount of time required for IKE negotiations to complete.
- C. PFS increases security by forcing the peers to perform a second DH exchange during Phase 2.
- D. PFS increases the IPsec VPN encryption key length and uses RSA or DSA certificates.
Answer: C
NEW QUESTION 23
Click the Exhibit button.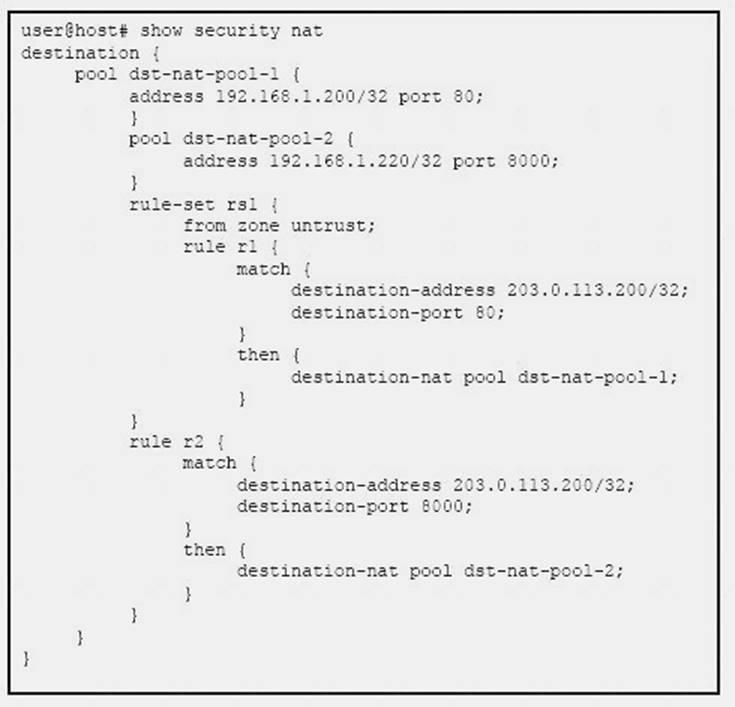
Which feature is enabled with destination NAT as shown in the exhibit?
- A. NAT overload
- B. block allocation
- C. port translation
- D. NAT hairpinning
Answer: D
NEW QUESTION 24
Which statement is true when destination NAT is performed?
- A. The source IP address is translated according to the configured destination NAT rules and then the security policies are applied.
- B. The destination IP address is translated according to the configured source NAT rules and then the security policies are applied.
- C. The destination IP address is translated according to the configured security policies and then the security destination NAT rules are applied.
- D. The destination IP address is translated according to the configured destination NAT rules and then the security policies are applied.
Answer: D
NEW QUESTION 25
......
P.S. Easily pass jn0-333 Exam with 75 Q&As prep-labs.com Dumps & pdf Version, Welcome to Download the Newest prep-labs.com jn0-333 Dumps: https://www.prep-labs.com/dumps/jn0-333/ (75 New Questions)
