156-215.81 Exam
Update 156-215.81 Latest Exam For Check Point Certified Security Administrator R81 Certification

we provide Accurate CheckPoint 156-215.81 testing engine which are the best for clearing 156-215.81 test, and to get certified by CheckPoint Check Point Certified Security Administrator R81. The 156-215.81 Questions & Answers covers all the knowledge points of the real 156-215.81 exam. Crack your CheckPoint 156-215.81 Exam with latest dumps, guaranteed!
Online 156-215.81 free questions and answers of New Version:
NEW QUESTION 1
Which of the following situations would not require a new license to be generated and installed?
- A. The Security Gateway is upgraded.
- B. The existing license expires.
- C. The license is upgraded.
- D. The IP address of the Security Management or Security Gateway has changed.
Answer: A
NEW QUESTION 2
In Unified SmartConsole Gateways and Servers tab you can perform the following functions EXCEPT _________.
- A. Upgrade the software version
- B. Open WebUI
- C. Open SSH
- D. Open service request with Check Point Technical Support
Answer: C
NEW QUESTION 3
Which GUI tool can be used to view and apply Check Point licenses?
- A. cpconfig
- B. Management Command Line
- C. SmartConsole
- D. SmartUpdate
Answer: D
Explanation:
SmartUpdate GUI is the recommended way of managing licenses.
NEW QUESTION 4
A Check Point Software license consists of two components, the Software Blade and the Software Container. There are _____ types of Software Containers: _________ .
- A. Two; Security Management and Endpoint Security
- B. Two; Endpoint Security and Security Gateway
- C. Three; Security Management, Security Gateway, and Endpoint Security
- D. Three; Security Gateway, Endpoint Security, and Gateway Management
Answer: C
Explanation:
There are three types of Software Containers: Security Management, Security Gateway, and Endpoint Security. Ref: https://downloads.checkpoint.com/dc/download.htm?ID=11608
NEW QUESTION 5
Your internal networks 10.1.1.0/24, 10.2.2.0/24 and 192.168.0.0/16 are behind the Internet Security Gateway. Considering that Layer 2 and Layer 3 setup is correct, what are the steps you will need to do in SmartConsole in order to get the connection working?
- A. 1. Define an accept rule in Security Policy.2. Define Security Gateway to hide all internal networks behind the gateway’s external IP.3. Publish and install the policy.
- B. 1. Define an accept rule in Security Policy.2. Define automatic NAT for each network to NAT the networks behind a public IP.3. Publish the policy.
- C. 1. Define an accept rule in Security Policy.2. Define automatic NAT for each network to NAT the networks behind a public IP.3. Publish and install the policy.
- D. 1. Define an accept rule in Security Policy.2. Define Security Gateway to hide all internal networks behind the gateway’s external IP.3. Publish the policy.
Answer: C
NEW QUESTION 6
Both major kinds of NAT support Hide and Static NAT. However, one offers more flexibility. Which statement is true?
- A. Manual NAT can offer more flexibility than Automatic NAT.
- B. Dynamic Network Address Translation (NAT) Overloading can offer more flexibility than Port Address Translation.
- C. Dynamic NAT with Port Address Translation can offer more flexibility than Network Address Translation (NAT) Overloading.
- D. Automatic NAT can offer more flexibility than Manual NAT.
Answer: A
Explanation:
"An Auto-NAT rule only uses the source address and port when matching and translating. Manual NAT can match and translate source and destination addresses and ports." https://networkdirection.net/articles/firewalls/firepowermanagementcentre/fmcnatpolicies/
NEW QUESTION 7
When an encrypted packet is decrypted, where does this happen?
- A. Security policy
- B. Inbound chain
- C. Outbound chain
- D. Decryption is not supported
Answer: A
NEW QUESTION 8
Fill in the blank: An Endpoint identity agent uses a _______ for user authentication.
- A. Shared secret
- B. Token
- C. Username/password or Kerberos Ticket
- D. Certificate
Answer: C
Explanation:
Two ways of auth: Username/Password in Captive Portal or Transparent Kerberos Auth through Kerberos Ticket. https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_IdentityAwareness_AdminGuide/T
NEW QUESTION 9
Which Identity Source(s) should be selected in Identity Awareness for when there is a requirement for a higher level of security for sensitive servers?
- A. AD Query
- B. Terminal Servers Endpoint Identity Agent
- C. Endpoint Identity Agent and Browser-Based Authentication
- D. RADIUS and Account Logon
Answer: C
Explanation:
Endpoint Identity Agents and Browser-Based Authentication - When a high level of security is necessary.
Captive Portal is used for distributing the Endpoint Identity Agent. IP Spoofing protection can be set to prevent packets from being IP spoofed.
NEW QUESTION 10
Security Gateway software blades must be attached to what?
- A. Security Gateway
- B. Security Gateway container
- C. Management server
- D. Management container
Answer: B
Explanation:
Security Management and Security Gateway Software Blades must be attached to a Software Container to be licensed. https://downloads.checkpoint.com/dc/download.htm?ID=11608
NEW QUESTION 11
URL Filtering employs a technology, which educates users on web usage policy in real time. What is the name of that technology?
- A. WebCheck
- B. UserCheck
- C. Harmony Endpoint
- D. URL categorization
Answer: B
Explanation:
UserCheck alerts users while attemping to browse a suspicious/blocked or otherwise policy-limited website through a message in their web browsers shown before the actual page loads.
NEW QUESTION 12
Log query results can be exported to what file format?
- A. Word Document (docx)
- B. Comma Separated Value (csv)
- C. Portable Document Format (pdf)
- D. Text (txt)
Answer: B
NEW QUESTION 13
You have created a rule at the top of your Rule Base to permit Guest Wireless access to the Internet. However, when guest users attempt to reach the Internet, they are not seeing the splash page to accept your Terms of Service, and cannot access the Internet. How can you fix this?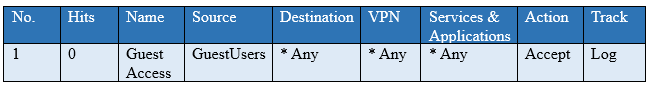
- A. Right click Accept in the rule, select “More”, and then check “Enable Identity Captive Portal”
- B. On the firewall object, Legacy Authentication screen, check “Enable Identity Captive Portal”
- C. In the Captive Portal screen of Global Properties, check “Enable Identity Captive Portal”
- D. On the Security Management Server object, check the box “Identity Logging”
Answer: A
NEW QUESTION 14
The Network Operations Center administrator needs access to Check Point Security devices mostly for troubleshooting purposes. You do not want to give her access to the expert mode, but she still should be able to run tcpdump. How can you achieve this requirement?
- A. Add tcpdump to CLISH using add command.Create a new access role.Add tcpdump to the role.Create new user with any UID and assign role to the user.
- B. Add tcpdump to CLISH using add command.Create a new access role.Add tcpdump to the role.Createnew user with UID 0 and assign role to the user.
- C. Create a new access role.Add expert-mode access to the role.Create new user with UID 0 and assign role to the user.
- D. Create a new access role.Add expert-mode access to the role.Create new user with any UID and assign role to the user.
Answer: A
NEW QUESTION 15
What is the purpose of the Clean-up Rule?
- A. To log all traffic that is not explicitly allowed or denied in the Rule Base
- B. To clean up policies found inconsistent with the compliance blade reports
- C. To remove all rules that could have a conflict with other rules in the database
- D. To eliminate duplicate log entries in the Security Gateway
Answer: A
Explanation:
These are basic access control rules we recommend for all Rule Bases:
There is also an implied rule that drops all traffic, but you can use the Cleanup rule to log the traffic.
NEW QUESTION 16
The purpose of the Communication Initialization process is to establish a trust between the Security Management Server and the Check Point gateways. Which statement best describes this Secure Internal
Communication (SIC)?
- A. After successful initialization, the gateway can communicate with any Check Point node that possesses a SIC certificate signed by the same ICA.
- B. Secure Internal Communications authenticates the security gateway to the SMS before http communications are allowed.
- C. A SIC certificate is automatically generated on the gateway because the gateway hosts a subordinate CA to the SMS ICA.
- D. New firewalls can easily establish the trust by using the expert password defined on the SMS and the SMS IP address.
Answer: A
Explanation:
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_SecurityManagement_AdminGuide
NEW QUESTION 17
Using R80 Smart Console, what does a “pencil icon” in a rule mean?
- A. I have changed this rule
- B. Someone else has changed this rule
- C. This rule is managed by check point’s SOC
- D. This rule can’t be changed as it’s an implied rule
Answer: A
NEW QUESTION 18
A SAM rule Is implemented to provide what function or benefit?
- A. Allow security audits.
- B. Handle traffic as defined in the policy.
- C. Monitor sequence activity.
- D. Block suspicious activity.
Answer: D
Explanation:
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_LoggingAndMonitoring_AdminGu
NEW QUESTION 19
......
P.S. Downloadfreepdf.net now are offering 100% pass ensure 156-215.81 dumps! All 156-215.81 exam questions have been updated with correct answers: https://www.downloadfreepdf.net/156-215.81-pdf-download.html (340 New Questions)
