200-201 Exam
Most Up-to-date 200-201 Training Tools For Understanding Cisco Cybersecurity Operations Fundamentals Certification

It is impossible to pass Cisco 200-201 exam without any help in the short term. Come to Examcollection soon and find the most advanced, correct and guaranteed Cisco 200-201 practice questions. You will get a surprising result by our Up to the immediate present Understanding Cisco Cybersecurity Operations Fundamentals practice guides.
Online 200-201 free questions and answers of New Version:
NEW QUESTION 1
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise.
Which kind of evidence is this IP address?
- A. best evidence
- B. corroborative evidence
- C. indirect evidence
- D. forensic evidence
Answer: B
NEW QUESTION 2
Which IETF standard technology is useful to detect and analyze a potential security incident by recording session flows that occurs between hosts?
- A. SFlow
- B. NetFlow
- C. NFlow
- D. IPFIX
Answer: D
NEW QUESTION 3
Which regular expression matches "color" and "colour"?
- A. colo?ur
- B. col[08]+our
- C. colou?r
- D. col[09]+our
Answer: C
NEW QUESTION 4
Which evasion technique is a function of ransomware?
- A. extended sleep calls
- B. encryption
- C. resource exhaustion
- D. encoding
Answer: B
NEW QUESTION 5
Which signature impacts network traffic by causing legitimate traffic to be blocked?
- A. false negative
- B. true positive
- C. true negative
- D. false positive
Answer: D
NEW QUESTION 6
When communicating via TLS, the client initiates the handshake to the server and the server responds back with its certificate for identification.
Which information is available on the server certificate?
- A. server name, trusted subordinate CA, and private key
- B. trusted subordinate CA, public key, and cipher suites
- C. trusted CA name, cipher suites, and private key
- D. server name, trusted CA, and public key
Answer: D
NEW QUESTION 7
Why is encryption challenging to security monitoring?
- A. Encryption analysis is used by attackers to monitor VPN tunnels.
- B. Encryption is used by threat actors as a method of evasion and obfuscation.
- C. Encryption introduces additional processing requirements by the CPU.
- D. Encryption introduces larger packet sizes to analyze and store.
Answer: B
NEW QUESTION 8
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
- A. fragmentation
- B. pivoting
- C. encryption
- D. stenography
Answer: D
NEW QUESTION 9
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
- A. file extension associations
- B. hardware, software, and security settings for the system
- C. currently logged in users, including folders and control panel settings
- D. all users on the system, including visual settings
Answer: B
NEW QUESTION 10
Refer to the exhibit.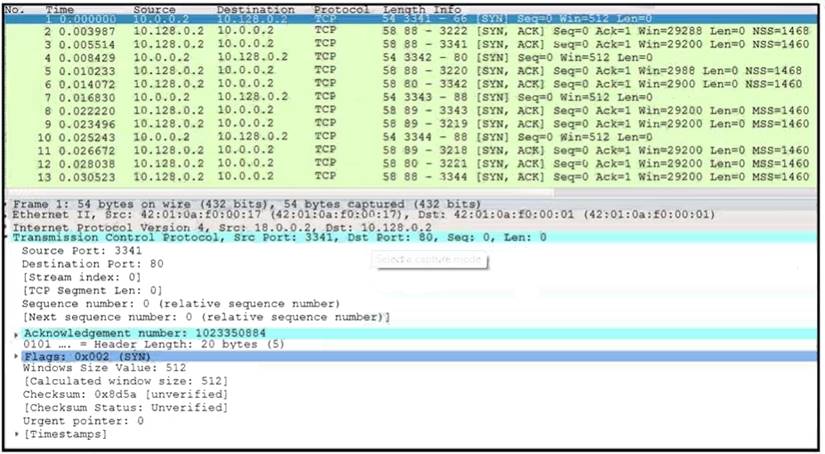
What is occurring in this network traffic?
- A. high rate of SYN packets being sent from a multiple source towards a single destination IP
- B. high rate of SYN packets being sent from a single source IP towards multiple destination IPs
- C. flood of ACK packets coming from a single source IP to multiple destination IPs
- D. flood of SYN packets coming from a single source IP to a single destination IP
Answer: D
NEW QUESTION 11
Which attack method intercepts traffic on a switched network?
- A. denial of service
- B. ARP cache poisoning
- C. DHCP snooping
- D. command and control
Answer: C
NEW QUESTION 12
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
- A. examination
- B. investigation
- C. collection
- D. reporting
Answer: C
NEW QUESTION 13
Which type of data collection requires the largest amount of storage space?
- A. alert data
- B. transaction data
- C. session data
- D. full packet capture
Answer: D
NEW QUESTION 14
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
- A. Untampered images are used in the security investigation process
- B. Tampered images are used in the security investigation process
- C. The image is tampered if the stored hash and the computed hash match
- D. Tampered images are used in the incident recovery process
- E. The image is untampered if the stored hash and the computed hash match
Answer: BE
NEW QUESTION 15
What does cyber attribution identity in an investigation?
- A. cause of an attack
- B. exploit of an attack
- C. vulnerabilities exploited
- D. threat actors of an attack
Answer: D
NEW QUESTION 16
What does an attacker use to determine which network ports are listening on a potential target device?
- A. man-in-the-middle
- B. port scanning
- C. SQL injection
- D. ping sweep
Answer: B
NEW QUESTION 17
......
Recommend!! Get the Full 200-201 dumps in VCE and PDF From Surepassexam, Welcome to Download: https://www.surepassexam.com/200-201-exam-dumps.html (New 98 Q&As Version)
