200-201 Exam
Top Tips Of Up To The Immediate Present 200-201 Free Draindumps

Our pass rate is high to 98.9% and the similarity percentage between our 200-201 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the Cisco 200-201 exam in just one try? I am currently studying for the Cisco 200-201 exam. Latest Cisco 200-201 Test exam practice questions and answers, Try Cisco 200-201 Brain Dumps First.
Free demo questions for Cisco 200-201 Exam Dumps Below:
NEW QUESTION 1
One of the objectives of information security is to protect the CIA of information and systems. What does CIA mean in this context?
- A. confidentiality, identity, and authorization
- B. confidentiality, integrity, and authorization
- C. confidentiality, identity, and availability
- D. confidentiality, integrity, and availability
Answer: D
NEW QUESTION 2
Refer to the exhibit.
Which type of log is displayed?
- A. IDS
- B. proxy
- C. NetFlow
- D. sys
Answer: D
NEW QUESTION 3
What is the difference between statistical detection and rule-based detection models?
- A. Rule-based detection involves the collection of data in relation to the behavior of legitimate users over a period of time
- B. Statistical detection defines legitimate data of users over a period of time and rule-based detection defines it on an IF/THEN basis
- C. Statistical detection involves the evaluation of an object on its intended actions before it executes that behavior
- D. Rule-based detection defines legitimate data of users over a period of time and statistical detection defines it on an IF/THEN basis
Answer: B
NEW QUESTION 4
Refer to the exhibit.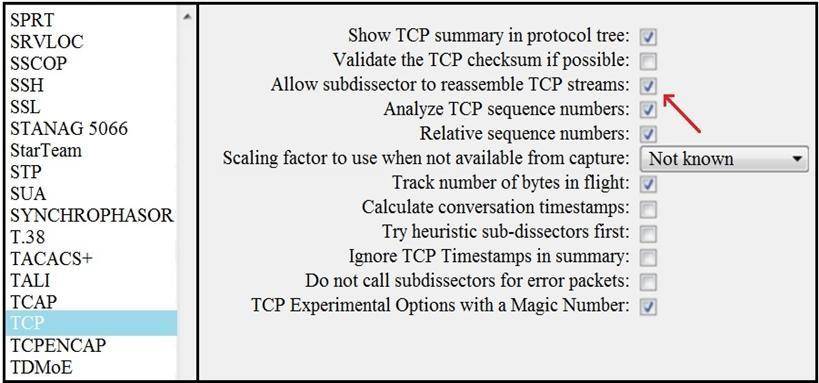
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
- A. insert TCP subdissectors
- B. extract a file from a packet capture
- C. disable TCP streams
- D. unfragment TCP
Answer: D
NEW QUESTION 5
What are two social engineering techniques? (Choose two.)
- A. privilege escalation
- B. DDoS attack
- C. phishing
- D. man-in-the-middle
- E. pharming
Answer: CE
NEW QUESTION 6
Which artifact is used to uniquely identify a detected file?
- A. file timestamp
- B. file extension
- C. file size
- D. file hash
Answer: D
NEW QUESTION 7
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
- A. application identification number
- B. active process identification number
- C. runtime identification number
- D. process identification number
Answer: D
NEW QUESTION 8
What is a difference between inline traffic interrogation and traffic mirroring?
- A. Inline inspection acts on the original traffic data flow
- B. Traffic mirroring passes live traffic to a tool for blocking
- C. Traffic mirroring inspects live traffic for analysis and mitigation
- D. Inline traffic copies packets for analysis and security
Answer: B
NEW QUESTION 9
Refer to the exhibit.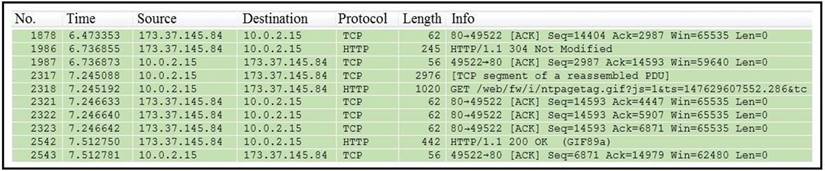
Which packet contains a file that is extractable within Wireshark?
- A. 2317
- B. 1986
- C. 2318
- D. 2542
Answer: D
NEW QUESTION 10
Which incidence response step includes identifying all hosts affected by an attack'?
- A. post-incident activity
- B. detection and analysis
- C. containment eradication and recovery
- D. preparation
Answer: A
NEW QUESTION 11
What specific type of analysis is assigning values to the scenario to see expected outcomes?
- A. deterministic
- B. exploratory
- C. probabilistic
- D. descriptive
Answer: A
NEW QUESTION 12
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
- A. syslog messages
- B. full packet capture
- C. NetFlow
- D. firewall event logs
Answer: C
NEW QUESTION 13
What is the difference between an attack vector and attack surface?
- A. An attack surface identifies vulnerabilities that require user input or validation; and an attack vectoridentifies vulnerabilities that are independent of user actions.
- B. An attack vector identifies components that can be exploited; and an attack surface identifies the potential path an attack can take to penetrate the network.
- C. An attack surface recognizes which network parts are vulnerable to an attack; and an attack vector identifies which attacks are possible with these vulnerabilities.
- D. An attack vector identifies the potential outcomes of an attack; and an attack surface launches an attack using several methods against the identified vulnerabilities.
Answer: C
NEW QUESTION 14
You have identified a malicious file in a sandbox analysis tool. Which piece of file information from the analysis is needed to search for additional downloads of this file by other hosts?
- A. file name
- B. file hash value
- C. file type
- D. file size
Answer: B
NEW QUESTION 15
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication.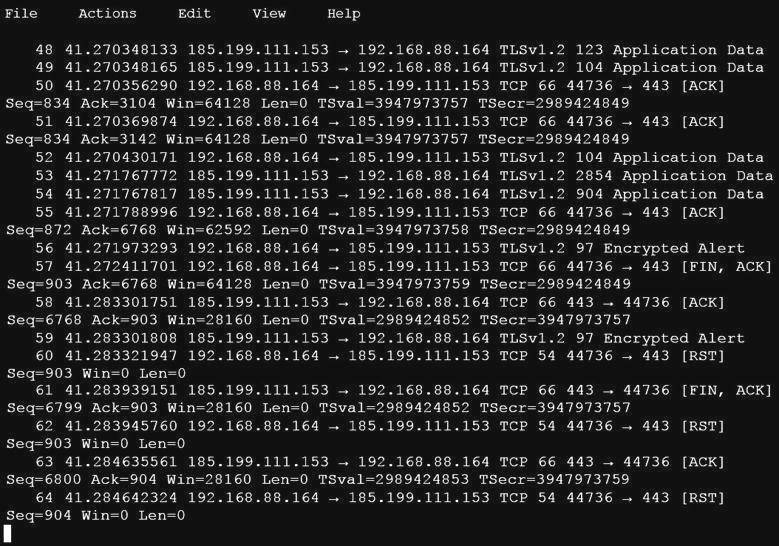
Which obfuscation technique is the attacker using?
- A. Base64 encoding
- B. transport layer security encryption
- C. SHA-256 hashing
- D. ROT13 encryption
Answer: B
NEW QUESTION 16
Refer to the exhibit.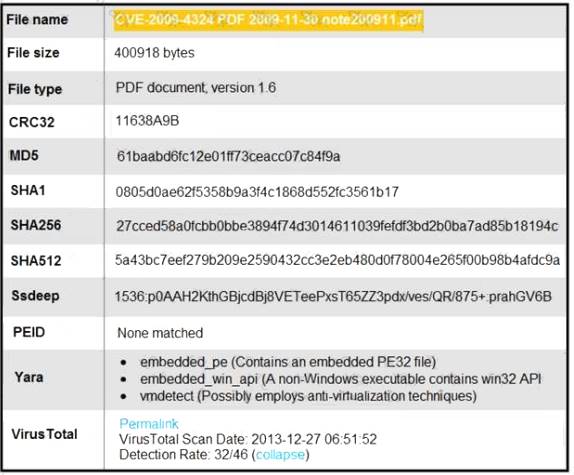
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
- A. The file has an embedded executable and was matched by PEiD threat signatures for further analysis.
- B. The file has an embedded non-Windows executable but no suspicious features are identified.
- C. The file has an embedded Windows 32 executable and the Yara field lists suspicious features for further analysis.
- D. The file was matched by PEiD threat signatures but no suspicious features are identified since the signature list is up to date.
Answer: C
NEW QUESTION 17
......
Thanks for reading the newest 200-201 exam dumps! We recommend you to try the PREMIUM DumpSolutions.com 200-201 dumps in VCE and PDF here: https://www.dumpsolutions.com/200-201-dumps/ (98 Q&As Dumps)
