350-701 Exam
A Review Of Breathing 350-701 Actual Test

Want to know Pass4sure 350-701 Exam practice test features? Want to lear more about Cisco Implementing and Operating Cisco Security Core Technologies certification experience? Study Highest Quality Cisco 350-701 answers to Improved 350-701 questions at Pass4sure. Gat a success with an absolute guarantee to pass Cisco 350-701 (Implementing and Operating Cisco Security Core Technologies) test on your first attempt.
Online 350-701 free questions and answers of New Version:
NEW QUESTION 1
When wired 802.1X authentication is implemented, which two components are required? (Choose two.)
- A. authentication server: Cisco Identity Service Engine
- B. supplicant: Cisco AnyConnect ISE Posture module
- C. authenticator: Cisco Catalyst switch
- D. authenticator: Cisco Identity Services Engine
- E. authentication server: Cisco Prime Infrastructure
Answer: AC
Explanation:
Reference: https://www.lookingpoint.com/blog/ise-series-802.1x
NEW QUESTION 2
What provides visibility and awareness into what is currently occurring on the network?
- A. CMX
- B. WMI
- C. Prime Infrastructure
- D. Telemetry
Answer: C
NEW QUESTION 3
What is the difference between deceptive phishing and spear phishing?
- A. Deceptive phishing is an attacked aimed at a specific user in the organization who holds a C-level role.
- B. A spear phishing campaign is aimed at a specific person versus a group of people.
- C. Spear phishing is when the attack is aimed at the C-level executives of an organization.
- D. Deceptive phishing hijacks and manipulates the DNS server of the victim and redirects the user to a false webpage.
Answer: B
NEW QUESTION 4
Refer to the exhibit.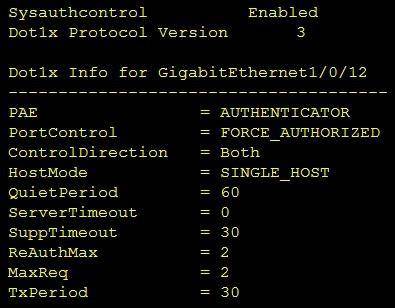
Which command was used to display this output?
- A. show dot1x all
- B. show dot1x
- C. show dot1x all summary
- D. show dot1x interface gi1/0/12
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_8021x/configuration/xe-3se/3850/sec-user-8021x-xe-3se-3850-book/config-ieee-802x-pba.html
NEW QUESTION 5
DRAG DROP
Drag and drop the descriptions from the left onto the correct protocol versions on the right.
[MISSING]
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
[MISSING]
NEW QUESTION 6
Which feature within Cisco Umbrella allows for the ability to inspect secure HTTP traffic?
- A. File Analysis
- B. SafeSearch
- C. SSL Decryption
- D. Destination Lists
Answer: C
NEW QUESTION 7
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
- A. transparent
- B. redirection
- C. forward
- D. proxy gateway
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/117940-qa-wsa-00.html
NEW QUESTION 8
How does Cisco Stealthwatch Cloud provide security for cloud environments?
- A. It delivers visibility and threat detection.
- B. It prevents exfiltration of sensitive data.
- C. It assigns Internet-based DNS protection for clients and servers.
- D. It facilitates secure connectivity between public and private networks.
Answer: A
Explanation:
https://www.content.shi.com/SHIcom/ContentAttachmentImages/SharedResources/FBLP/Cisco/Cisco-091919-Simple-IT-Whitepaper.pdf
NEW QUESTION 9
Which technology reduces data loss by identifying sensitive information stored in public computing environments?
- A. Cisco SDA
- B. Cisco Firepower
- C. Cisco HyperFlex
- D. Cisco Cloudlock
Answer: D
Explanation:
Reference: https://www.cisco.com/c/dam/en/us/products/collateral/security/cloudlock/cisco-cloudlock-cloud-data-security-datasheet.pdf
NEW QUESTION 10
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
- A. Enable IP Layer enforcement.
- B. Activate the Advanced Malware Protection license
- C. Activate SSL decryption.
- D. Enable Intelligent Proxy.
Answer: D
NEW QUESTION 11
What is a language format designed to exchange threat intelligence that can be transported over the TAXII protocol?
- A. STIX
- B. XMPP
- C. pxGrid
- D. SMTP
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/web_security/scancenter/administrator/guide/b_ScanCenter_Administrator_Guide/b_ScanCenter_Administrator_Guide_chapter_0100011.pdf
NEW QUESTION 12
Refer to the exhibit.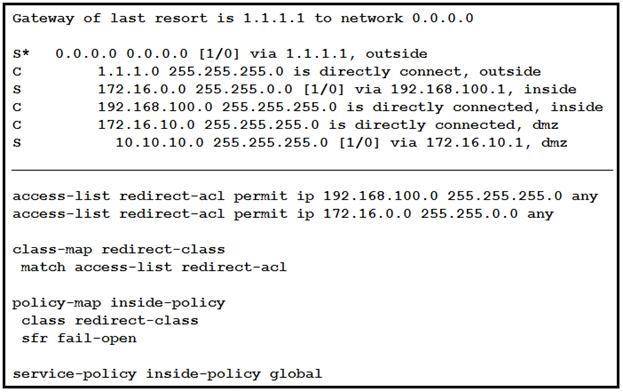
What is a result of the configuration?
- A. Traffic from the DMZ network is redirected.
- B. Traffic from the inside network is redirected.
- C. All TCP traffic is redirected.
- D. Traffic from the inside and DMZ networks is redirected.
Answer: D
NEW QUESTION 13
Which ID store requires that a shadow user be created on Cisco ISE for the admin login to work?
- A. RSA SecureID
- B. Internal Database
- C. Active Directory
- D. LDAP
Answer: C
NEW QUESTION 14
Which two deployment model configurations are supported for Cisco FTDv in AWS? (Choose two.)
- A. Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS
- B. Cisco FTDv with one management interface and two traffic interfaces configured
- C. Cisco FTDv configured in routed mode and managed by a physical FMC appliance on premises
- D. Cisco FTDv with two management interfaces and one traffic interface configured
- E. Cisco FTDv configured in routed mode and IPv6 configured
Answer: AC
Explanation:
Reference: https://www.cisco.com/c/en/us/products/collateral/security/adaptive-security-virtual-appliance-asav/white-paper-c11-740505.html
NEW QUESTION 15
DRAG DROP
Drag and drop the steps from the left into the correct order on the right to enable AppDynamics to monitor an EC2 instance in Amazon Web Services.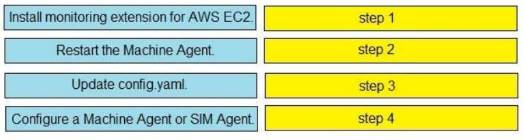
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 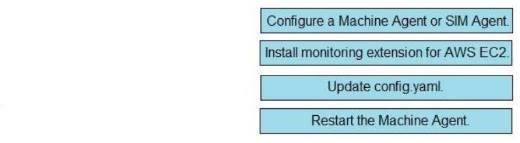
NEW QUESTION 16
Which feature requires a network discovery policy on the Cisco Firepower Next Generation Intrusion Prevention System?
- A. security intelligence
- B. impact flags
- C. health monitoring
- D. URL filtering
Answer: A
NEW QUESTION 17
Which algorithm provides encryption and authentication for data plane communication?
- A. AES-GCM
- B. SHA-96
- C. AES-256
- D. SHA-384
Answer: A
NEW QUESTION 18
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two.)
- A. DDoS
- B. antispam
- C. antivirus
- D. encryption
- E. DLP
Answer: DE
Explanation:
Reference: https://www.cisco.com/c/dam/en/us/td/docs/security/ces/overview_guide/Cisco_Cloud_Hybrid_Email_Security_Overview_Guide.pdf
NEW QUESTION 19
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
- A. smurf
- B. distributed denial of service
- C. cross-site scripting
- D. rootkit exploit
Answer: C
NEW QUESTION 20
An MDM provides which two advantages to an organization with regards to device management? (Choose two.)
- A. asset inventory management
- B. allowed application management
- C. Active Directory group policy management
- D. network device management
- E. critical device management
Answer: AB
NEW QUESTION 21
An engineer needs a solution for TACACS+ authentication and authorization for device administration. The engineer also wants to enhance wired and wireless network security by requiring users and endpoints to use 802.1X, MAB, or WebAuth. Which product meets all of these requirements?
- A. Cisco Prime Infrastructure
- B. Cisco Identity Services Engine
- C. Cisco Stealthwatch
- D. Cisco AMP for Endpoints
Answer: B
NEW QUESTION 22
......
Thanks for reading the newest 350-701 exam dumps! We recommend you to try the PREMIUM Surepassexam 350-701 dumps in VCE and PDF here: https://www.surepassexam.com/350-701-exam-dumps.html (102 Q&As Dumps)
