350-701 Exam
The Secret Of Cisco 350-701 Practice Question

Proper study guides for Renovate Cisco Implementing and Operating Cisco Security Core Technologies certified begins with Cisco 350-701 preparation products which designed to deliver the Tested 350-701 questions by making you pass the 350-701 test at your first time. Try the free 350-701 demo right now.
Check 350-701 free dumps before getting the full version:
NEW QUESTION 1
What are two list types within AMP for Endpoints Outbreak Control? (Choose two.)
- A. blocked ports
- B. simple custom detections
- C. command and control
- D. allowed applications
- E. URL
Answer: BD
Explanation:
Reference: https://docs.amp.cisco.com/en/A4E/AMP%20for%20Endpoints%20User%20Guide.pdf chapter 2
NEW QUESTION 2
What does the Cloudlock Apps Firewall do to mitigate security concerns from an application perspective?
- A. It allows the administrator to quarantine malicious files so that the application can function, just not maliciously.
- B. It discovers and controls cloud apps that are connected to a company’s corporate environment.
- C. It deletes any application that does not belong in the network.
- D. It sends the application information to an administrator to act on.
Answer: B
Explanation:
Reference: https://www.cisco.com/c/en/us/products/security/cloudlock/index.html#~features
NEW QUESTION 3
Refer to the exhibit.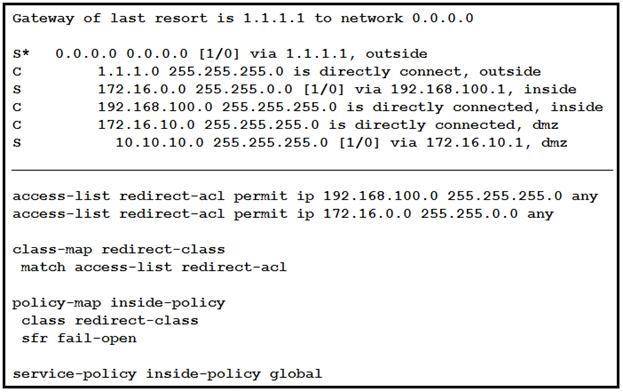
What is a result of the configuration?
- A. Traffic from the DMZ network is redirected.
- B. Traffic from the inside network is redirected.
- C. All TCP traffic is redirected.
- D. Traffic from the inside and DMZ networks is redirected.
Answer: D
NEW QUESTION 4
Which policy represents a shared set of features or parameters that define the aspects of a managed device that are likely to be similar to other managed devices in a deployment?
- A. group policy
- B. access control policy
- C. device management policy
- D. platform service policy
Answer: D
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/622/configuration/guide/fpmc-config-guide-v622/platform_settings_policies_for_managed_devices.pdf
NEW QUESTION 5
Which two behavioral patterns characterize a ping of death attack? (Choose two.)
- A. The attack is fragmented into groups of 16 octets before transmission.
- B. The attack is fragmented into groups of 8 octets before transmission.
- C. Short synchronized bursts of traffic are used to disrupt TCP connections.
- D. Malformed packets are used to crash systems.
- E. Publicly accessible DNS servers are typically used to execute the attack.
Answer: BD
Explanation:
Reference: https://en.wikipedia.org/wiki/Ping_of_death
NEW QUESTION 6
Which functions of an SDN architecture require southbound APIs to enable communication?
- A. SDN controller and the network elements
- B. management console and the SDN controller
- C. management console and the cloud
- D. SDN controller and the cloud
Answer: A
NEW QUESTION 7
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two.)
- A. DDoS
- B. antispam
- C. antivirus
- D. encryption
- E. DLP
Answer: DE
Explanation:
Reference: https://www.cisco.com/c/dam/en/us/td/docs/security/ces/overview_guide/Cisco_Cloud_Hybrid_Email_Security_Overview_Guide.pdf
NEW QUESTION 8
Refer to the exhibit.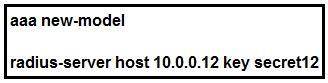
Which statement about the authentication protocol used in the configuration is true?
- A. The authentication request contains only a password
- B. The authentication request contains only a username
- C. The authentication and authorization requests are grouped in a single packet.
- D. There are separate authentication and authorization request packets.
Answer: C
NEW QUESTION 9
How does Cisco Stealthwatch Cloud provide security for cloud environments?
- A. It delivers visibility and threat detection.
- B. It prevents exfiltration of sensitive data.
- C. It assigns Internet-based DNS protection for clients and servers.
- D. It facilitates secure connectivity between public and private networks.
Answer: A
Explanation:
https://www.content.shi.com/SHIcom/ContentAttachmentImages/SharedResources/FBLP/Cisco/Cisco-091919-Simple-IT-Whitepaper.pdf
NEW QUESTION 10
Which two kinds of attacks are prevented by multifactor authentication? (Choose two.)
- A. phishing
- B. brute force
- C. man-in-the-middle
- D. DDOS
- E. tear drop
Answer: BC
NEW QUESTION 11
DRAG DROP
Drag and drop the steps from the left into the correct order on the right to enable AppDynamics to monitor an EC2 instance in Amazon Web Services.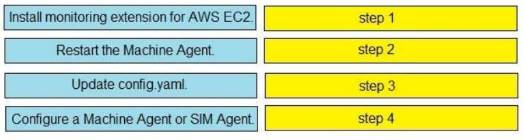
Solution:
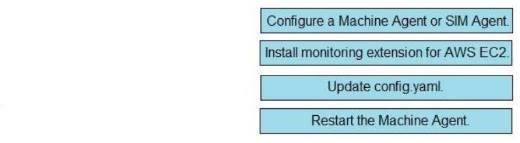
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 12
Which two features are used to configure Cisco ESA with a multilayer approach to fight viruses and malware? (Choose two.)
- A. Sophos engine
- B. white list
- C. RAT
- D. outbreak filters
- E. DLP
Answer: AD
NEW QUESTION 13
Which Cisco solution does Cisco Umbrella integrate with to determine if a URL is malicious?
- A. AMP
- B. AnyConnect
- C. DynDNS
- D. Talos
Answer: D
NEW QUESTION 14
When wired 802.1X authentication is implemented, which two components are required? (Choose two.)
- A. authentication server: Cisco Identity Service Engine
- B. supplicant: Cisco AnyConnect ISE Posture module
- C. authenticator: Cisco Catalyst switch
- D. authenticator: Cisco Identity Services Engine
- E. authentication server: Cisco Prime Infrastructure
Answer: AC
Explanation:
Reference: https://www.lookingpoint.com/blog/ise-series-802.1x
NEW QUESTION 15
Refer to the exhibit.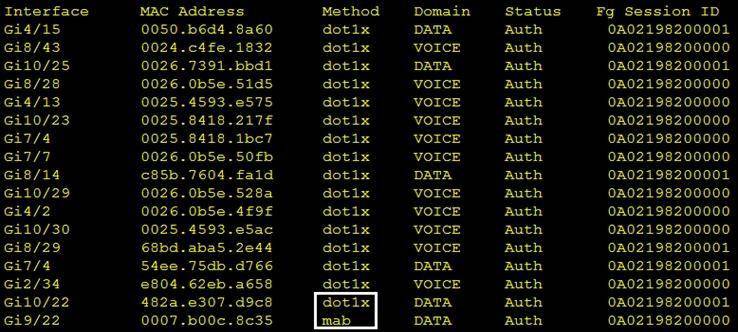
Which command was used to generate this output and to show which ports are authenticating with dot1x or mab?
- A. show authentication registrations
- B. show authentication method
- C. show dot1x all
- D. show authentication sessions
Answer: B
NEW QUESTION 16
Which cloud service model offers an environment for cloud consumers to develop and deploy applications without needing to manage or maintain the underlying cloud infrastructure?
- A. PaaS
- B. XaaS
- C. IaaS
- D. SaaS
Answer: A
NEW QUESTION 17
Which statement about IOS zone-based firewalls is true?
- A. An unassigned interface can communicate with assigned interfaces
- B. Only one interface can be assigned to a zone.
- C. An interface can be assigned to multiple zones.
- D. An interface can be assigned only to one zone.
Answer: D
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/security/ios-firewall/98628-zone-design-guide.html
NEW QUESTION 18
......
100% Valid and Newest Version 350-701 Questions & Answers shared by Thedumpscentre.com, Get Full Dumps HERE: https://www.thedumpscentre.com/350-701-dumps/ (New 337 Q&As)
