CS0-002 Exam
The Down To Date Guide To CS0-002 Vce

Our pass rate is high to 98.9% and the similarity percentage between our CS0-002 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the CompTIA CS0-002 exam in just one try? I am currently studying for the CompTIA CS0-002 exam. Latest CompTIA CS0-002 Test exam practice questions and answers, Try CompTIA CS0-002 Brain Dumps First.
Also have CS0-002 free dumps questions for you:
NEW QUESTION 1
As part of a review of modern response plans, which of the following is MOST important for an organization lo understand when establishing the breach notification period?
- A. Organizational policies
- B. Vendor requirements and contracts
- C. Service-level agreements
- D. Legal requirements
Answer: D
NEW QUESTION 2
A team of security analysis has been alerted to potential malware activity. The initial examination indicates one of the affected workstations on beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445. Which of the following should be the team's NEXT step during the detection phase of this response process?
- A. Escalate the incident to management ,who will then engage the network infrastructure team to keep them informed
- B. Depending on system critically remove each affected device from the network by disabling wired and wireless connections
- C. Engage the engineering team to block SMB traffic internally and outbound HTTP traffic to the five IP addresses Identify potentially affected systems by creating a correlation
- D. Identify potentially affected system by creating a correlation search in the SIEM based on the network traffic.
Answer: D
NEW QUESTION 3
A security analyst is investigating a malware infection that occurred on a Windows system. The system was not connected to a network and had no wireless capability Company policy prohibits using portable media or mobile storage The security analyst is trying to determine which user caused the malware to get onto the system Which of the following registry keys would MOST likely have this information?
A)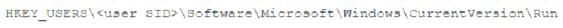
B)
C)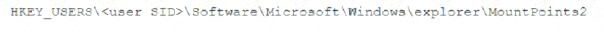
D)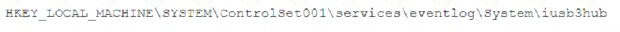
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: C
NEW QUESTION 4
During a cyber incident, which of the following is the BEST course of action?
- A. Switch to using a pre-approved, secure, third-party communication system.
- B. Keep the entire company informed to ensure transparency and integrity during the incident.
- C. Restrict customer communication until the severity of the breach is confirmed.
- D. Limit communications to pre-authorized parties to ensure response efforts remain confidential.
Answer: D
NEW QUESTION 5
Which of the following MOST accurately describes an HSM?
- A. An HSM is a low-cost solution for encryption.
- B. An HSM can be networked based or a removable USB
- C. An HSM is slower at encrypting than software
- D. An HSM is explicitly used for MFA
Answer: A
NEW QUESTION 6
A system’s authority to operate (ATO) is set to expire in four days. Because of other activities and limited staffing, the organization has neglected to start reauthentication activities until now. The cybersecurity group just performed a vulnerability scan with the partial set of results shown below: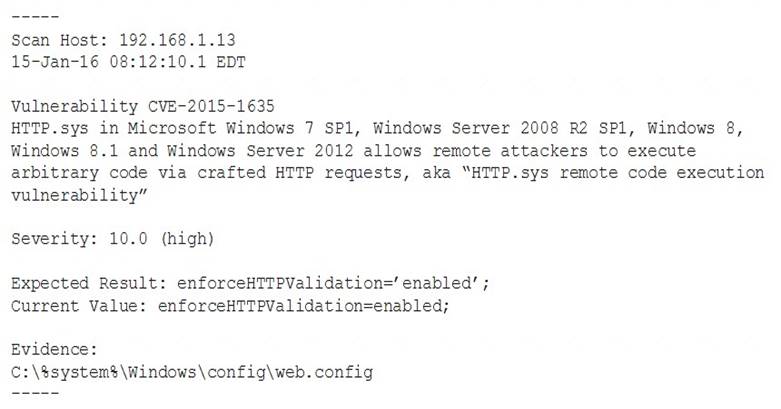
Based on the scenario and the output from the vulnerability scan, which of the following should the security team do with this finding?
- A. Remediate by going to the web config file, searching for the enforce HTTP validation setting, and manually updating to the correct setting.
- B. Accept this risk for now because this is a “high” severity, but testing will require more than the four days available, and the system ATO needs to be competed.
- C. Ignore i
- D. This is false positive, and the organization needs to focus its efforts on other findings.
- E. Ensure HTTP validation is enabled by rebooting the server.
Answer: A
NEW QUESTION 7
Which of the following BEST articulates the benefit of leveraging SCAP in an organization’s cybersecurity analysis toolset?
- A. It automatically performs remedial configuration changes to enterprise security services
- B. It enables standard checklist and vulnerability analysis expressions for automation
- C. It establishes a continuous integration environment for software development operations
- D. It provides validation of suspected system vulnerabilities through workflow orchestration
Answer: B
NEW QUESTION 8
An analyst is investigating an anomalous event reported by the SOC After reviewing the system logs the analyst identifies an unexpected addition of a user with root-level privileges on the endpoint. Which of the following data sources will BEST help the analyst to determine whether this event constitutes an incident?
- A. Patching logs
- B. Threat feed
- C. Backup logs
- D. Change requests
- E. Data classification matrix
Answer: D
NEW QUESTION 9
Which of the following would a security engineer recommend to BEST protect sensitive system data from being accessed on mobile devices?
- A. Use a UEFl boot password.
- B. Implement a self-encrypted disk.
- C. Configure filesystem encryption
- D. Enable Secure Boot using TPM
Answer: A
NEW QUESTION 10
An analyst is performing penetration testing and vulnerability assessment activities against a new vehicle automation platform.
Which of the following is MOST likely an attack vector that is being utilized as part of the testing and assessment?
- A. FaaS
- B. RTOS
- C. SoC
- D. GPS
- E. CAN bus
Answer: E
NEW QUESTION 11
An analyst is participating in the solution analysis process for a cloud-hosted SIEM platform to centralize log monitoring and alerting capabilities in the SOC.
Which of the following is the BEST approach for supply chain assessment when selecting a vendor?
- A. Gather information from providers, including datacenter specifications and copies of audit reports.
- B. Identify SLA requirements for monitoring and logging.
- C. Consult with senior management for recommendations.
- D. Perform a proof of concept to identify possible solutions.
Answer: B
NEW QUESTION 12
Which of the following technologies can be used to house the entropy keys for disk encryption on desktops and laptops?
- A. Self-encrypting drive
- B. Bus encryption
- C. TPM
- D. HSM
Answer: A
NEW QUESTION 13
Which of the following technologies can be used to store digital certificates and is typically used in high-security implementations where integrity is paramount?
- A. HSM
- B. eFuse
- C. UEFI
- D. Self-encrypting drive
Answer: A
NEW QUESTION 14
During an investigation, a security analyst determines suspicious activity occurred during the night shift over the weekend. Further investigation reveals the activity was initiated from an internal IP going to an external website.
Which of the following would be the MOST appropriate recommendation to prevent the activity from happening in the future?
- A. An IPS signature modification for the specific IP addresses
- B. An IDS signature modification for the specific IP addresses
- C. A firewall rule that will block port 80 traffic
- D. A firewall rule that will block traffic from the specific IP addresses
Answer: D
NEW QUESTION 15
A security analyst reviews the following aggregated output from an Nmap scan and the border firewall ACL: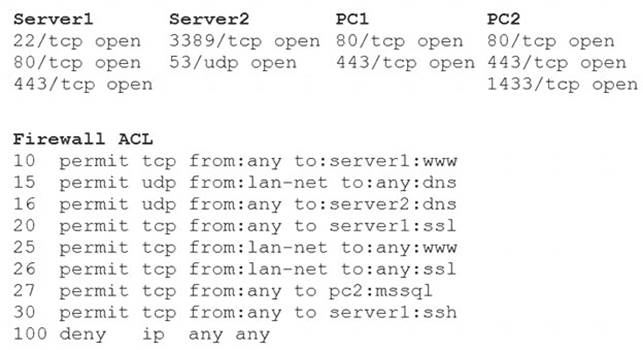
Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?
- A. PC1
- B. PC2
- C. Server1
- D. Server2
- E. Firewall
Answer: B
NEW QUESTION 16
A company wants to establish a threat-hunting team. Which of the following BEST describes the rationale for integration intelligence into hunt operations?
- A. It enables the team to prioritize the focus area and tactics within the company’s environment.
- B. It provide critically analyses for key enterprise servers and services.
- C. It allow analysis to receive updates on newly discovered software vulnerabilities.
- D. It supports rapid response and recovery during and followed an incident.
Answer: A
NEW QUESTION 17
A system administrator is doing network reconnaissance of a company’s external network to determine the vulnerability of various services that are running. Sending some sample traffic to the external host, the administrator obtains the following packet capture: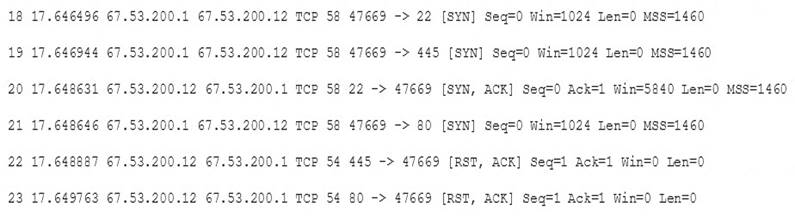
Based on the output, which of the following services should be further tested for vulnerabilities?
- A. SSH
- B. HTTP
- C. SMB
- D. HTTPS
Answer: C
NEW QUESTION 18
A security team wants to make SaaS solutions accessible from only the corporate campus.
Which of the following would BEST accomplish this goal?
- A. Geofencing
- B. IP restrictions
- C. Reverse proxy
- D. Single sign-on
Answer: A
NEW QUESTION 19
For machine learning to be applied effectively toward security analysis automation, it requires.
- A. relevant training data.
- B. a threat feed API.
- C. a multicore, multiprocessor system.
- D. anomalous traffic signatures.
Answer: A
NEW QUESTION 20
......
100% Valid and Newest Version CS0-002 Questions & Answers shared by Dumpscollection.com, Get Full Dumps HERE: https://www.dumpscollection.net/dumps/CS0-002/ (New 186 Q&As)
