CS0-002 Exam
The Secret Of CompTIA CS0-002 Exam Dumps

we provide Realistic CompTIA CS0-002 rapidshare which are the best for clearing CS0-002 test, and to get certified by CompTIA CompTIA Cybersecurity Analyst (CySA+) Certification Exam. The CS0-002 Questions & Answers covers all the knowledge points of the real CS0-002 exam. Crack your CompTIA CS0-002 Exam with latest dumps, guaranteed!
CompTIA CS0-002 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
During an investigation, an incident responder intends to recover multiple pieces of digital media. Before removing the media, the responder should initiate:
- A. malware scans.
- B. secure communications.
- C. chain of custody forms.
- D. decryption tools.
Answer: C
NEW QUESTION 2
An organization has several system that require specific logons Over the past few months, the security analyst has noticed numerous failed logon attempts followed by password resets. Which of the following should the analyst do to reduce the occurrence of legitimate failed logons and password resets?
- A. Use SSO across all applications
- B. Perform a manual privilege review
- C. Adjust the current monitoring and logging rules
- D. Implement multifactor authentication
Answer: B
NEW QUESTION 3
After a breach involving the exfiltration of a large amount of sensitive data a security analyst is reviewing the following firewall logs to determine how the breach occurred: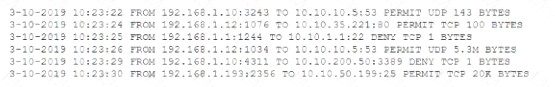
Which of the following IP addresses does the analyst need to investigate further?
- A. 192.168.1.1
- B. 192.168.1.10
- C. 192.168.1.12
- D. 192.168.1.193
Answer: C
NEW QUESTION 4
An information security analyst is reviewing backup data sets as part of a project focused on eliminating archival data sets.
Which of the following should be considered FIRST prior to disposing of the electronic data?
- A. Sanitization policy
- B. Data sovereignty
- C. Encryption policy
- D. Retention standards
Answer: D
NEW QUESTION 5
A development team is testing a new application release. The team needs to import existing client PHI data records from the production environment to the test environment to test accuracy and functionality.
Which of the following would BEST protect the sensitivity of this data while still allowing the team to perform the testing?
- A. Deidentification
- B. Encoding
- C. Encryption
- D. Watermarking
Answer: A
NEW QUESTION 6
A new on-premises application server was recently installed on the network. Remote access to the server was enabled for vendor support on required ports, but recent security reports show large amounts of data are being sent to various unauthorized networks through those ports. Which of the following configuration changes must be implemented to resolve this security issue while still allowing remote vendor access?
- A. Apply a firewall application server rule.
- B. Whitelist the application server.
- C. Sandbox the application server.
- D. Enable port security.
- E. Block the unauthorized networks.
Answer: B
NEW QUESTION 7
Which of the following is the MOST important objective of a post-incident review?
- A. Capture lessons learned and improve incident response processes
- B. Develop a process for containment and continue improvement efforts
- C. Identify new technologies and strategies to remediate
- D. Identify a new management strategy
Answer: A
NEW QUESTION 8
A compliance officer of a large organization has reviewed the firm's vendor management program but has discovered there are no controls defined to evaluate third-party risk or hardware source authenticity. The compliance officer wants to gain some level of assurance on a recurring basis regarding the implementation of controls by third parties.
Which of the following would BEST satisfy the objectives defined by the compliance officer? (Choose two.)
- A. Executing vendor compliance assessments against the organization's security controls
- B. Executing NDAs prior to sharing critical data with third parties
- C. Soliciting third-party audit reports on an annual basis
- D. Maintaining and reviewing the organizational risk assessment on a quarterly basis
- E. Completing a business impact assessment for all critical service providers
- F. Utilizing DLP capabilities at both the endpoint and perimeter levels
Answer: AC
NEW QUESTION 9
A security analyst is reviewing packet captures from a system that was compromised. The system was already isolated from the network, but it did have network access for a few hours after being compromised. When viewing the capture in a packet analyzer, the analyst sees the following:
Which of the following can the analyst conclude?
- A. Malware is attempting to beacon to 128.50.100.3.
- B. The system is running a DoS attack against ajgidwle.com.
- C. The system is scanning ajgidwle.com for PII.
- D. Data is being exfiltrated over DNS.
Answer: D
NEW QUESTION 10
An analyst performs a routine scan of a host using Nmap and receives the following output: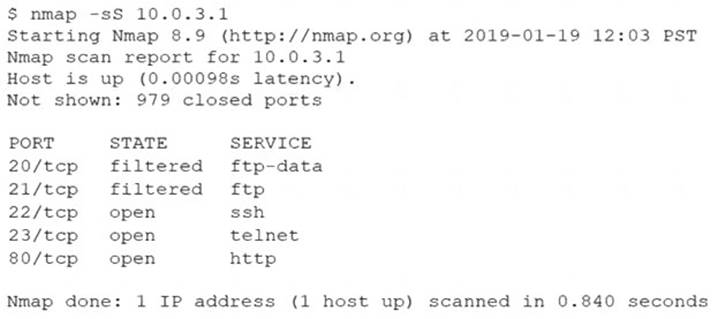
Which of the following should the analyst investigate FIRST?
- A. Port 21
- B. Port 22
- C. Port 23
- D. Port 80
Answer: C
NEW QUESTION 11
Which of the following software security best practices would prevent an attacker from being able to run arbitrary SQL commands within a web application? (Choose two.)
- A. Parameterized queries
- B. Session management
- C. Input validation
- D. Output encoding
- E. Data protection
- F. Authentication
Answer: AC
NEW QUESTION 12
Ransomware is identified on a company's network that affects both Windows and MAC hosts. The command and control channel for encryption for this variant uses TCP ports from 11000 to 65000. The channel goes to good1. Iholdbadkeys.com, which resolves to IP address 72.172.16.2.
Which of the following is the MOST effective way to prevent any newly infected systems from actually encrypting the data on connected network drives while causing the least disruption to normal Internet traffic?
- A. Block all outbound traffic to web host good1 iholdbadkeys.com at the border gateway.
- B. Block all outbound TCP connections to IP host address 172.172.16.2 at the border gateway.
- C. Block all outbound traffic on TCP ports 11000 to 65000 at the border gateway.
- D. Block all outbound traffic on TCP ports 11000 to 65000 to IP host address 172.172.16.2 at the border gateway.
Answer: A
NEW QUESTION 13
A cybersecurity analyst is reading a daily intelligence digest of new vulnerabilities The type of vulnerability that should be disseminated FIRST is one that:
- A. enables remote code execution that is being exploited in the wild.
- B. enables data leakage but is not known to be m the environment
- C. enables lateral movement and was reported as a proof of concept
- D. affected the organization in the past but was probably contained and eradicated
Answer: C
NEW QUESTION 14
A security analyst implemented a solution that would analyze the attacks that the organization’s firewalls failed to prevent. The analyst used the existing systems to enact the solution and executed the following command.
S sudo nc -1 -v -c maildemon . py 25 caplog, txt
Which of the following solutions did the analyst implement?
- A. Log collector
- B. Crontab mail script
- C. Snikhole
- D. Honeypot
Answer: A
NEW QUESTION 15
A security analyst recently discovered two unauthorized hosts on the campus's wireless network segment from a man-m-the-middle attack .The security analyst also verified that privileges were not escalated, and the two devices did not gain access to other network devices Which of the following would BEST mitigate and improve the security posture of the wireless network for this type of attack?
- A. Enable MAC filtering on the wireless router and suggest a stronger encryption for the wireless network,
- B. Change the SSID, strengthen the passcode, and implement MAC filtering on the wireless router.
- C. Enable MAC filtering on the wireless router and create a whitelist that allows devices on the network
- D. Conduct a wireless survey to determine if the wireless strength needs to be reduced.
Answer: A
NEW QUESTION 16
A security analyst has a sample of malicious software and needs to know what the sample does? The analyst runs the sample in a carefully controlled and monitored virtual machine to observe the software behavior. Which of the following malware analysis approaches is this?
- A. White box testing
- B. Fuzzing
- C. Sandboxing
- D. Static code analysis
Answer: C
NEW QUESTION 17
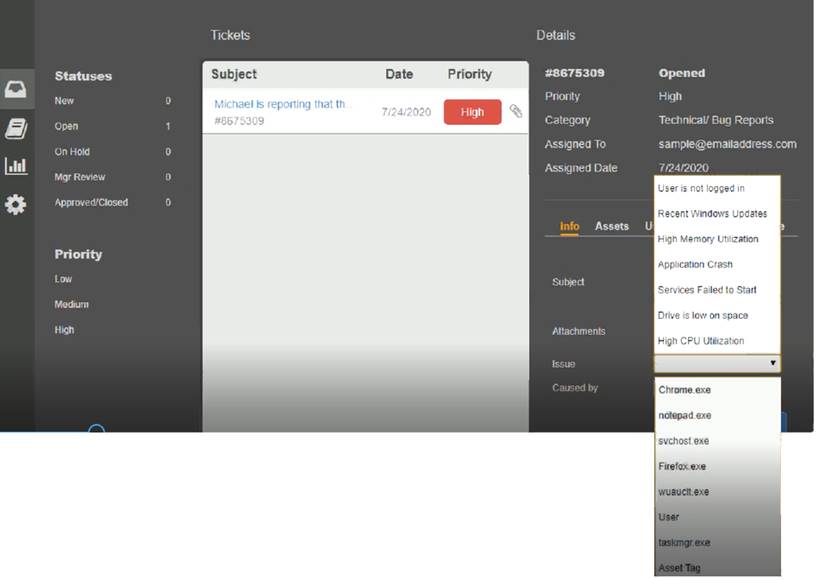
Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the desk ticket queue. INSTRUCTIONS
Click on me ticket to see the ticket details Additional content is available on tabs within the ticket
First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button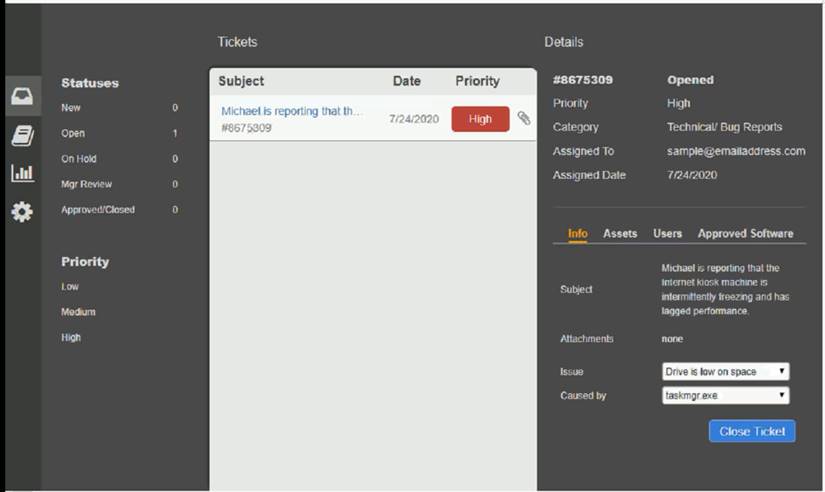
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 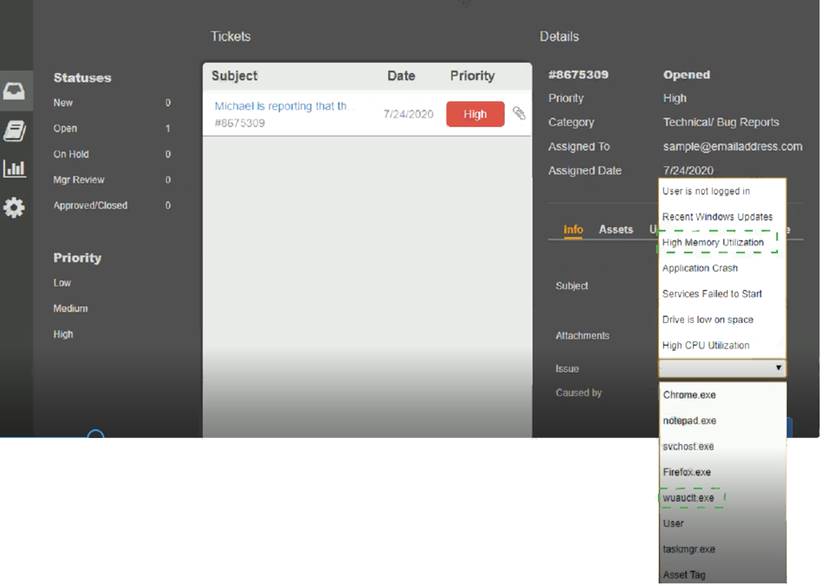
NEW QUESTION 18
A security analyst has discovered trial developers have installed browsers on all development servers in the company's cloud infrastructure and are using them to browse the Internet. Which of the following changes should the security analyst make to BEST protect the environment?
- A. Create a security rule that blocks Internet access in the development VPC
- B. Place a jumpbox m between the developers' workstations and the development VPC
- C. Remove the administrator profile from the developer user group in identity and access management
- D. Create an alert that is triggered when a developer installs an application on a server
Answer: A
NEW QUESTION 19
A company was recently awarded several large government contracts and wants to determine its current risk from one specific APT.
Which of the following threat modeling methodologies would be the MOST appropriate to use during this analysis?
- A. Attack vectors
- B. Adversary capability
- C. Diamond Model of Intrusion Analysis
- D. Kill chain
- E. Total attack surface
Answer: B
NEW QUESTION 20
......
P.S. Surepassexam now are offering 100% pass ensure CS0-002 dumps! All CS0-002 exam questions have been updated with correct answers: https://www.surepassexam.com/CS0-002-exam-dumps.html (186 New Questions)
