GCIA Exam
The Secret Of GIAC GCIA Exam Guide

Master the GCIA GIAC Certified Intrusion Analyst content and be ready for exam day success quickly with this Testking GCIA study guide. We guarantee it!We make it a reality and give you real GCIA questions in our GIAC GCIA braindumps.Latest 100% VALID GIAC GCIA Exam Questions Dumps at below page. You can use our GIAC GCIA braindumps and pass your exam.
Also have GCIA free dumps questions for you:
NEW QUESTION 1
Which of the following tools is an open source network intrusion prevention and detection system that operates as a network sniffer?
- A. Swatch
- B. IPLog
- C. Timbersee
- D. Snort
Answer: D
NEW QUESTION 2
Which of the following hacking tools provides shell access over ICMP?
- A. John the Ripper
- B. Loki
- C. Nessus
- D. Nmap
Answer: B
NEW QUESTION 3
Which of the following tools is used to analyze a system and report any unsigned drivers found?
- A. regedit.exe
- B. sigverify.exe
- C. sigverif.exe
- D. msconfig
Answer: C
NEW QUESTION 4
Which of the following files records all driver installations after the system has booted?
- A. setupapi.com
- B. recdriver.log
- C. drivinst.log
- D. setupapi.log
Answer: D
NEW QUESTION 5
Which of the following two cryptography methods are used by NTFS Encrypting File System (EFS) to encrypt the data stored on a disk on a file-by-file basis?
- A. Public key
- B. Digital certificates
- C. Twofish
- D. RSA
Answer: AB
NEW QUESTION 6
Which of the following statements are true about an IPv6 network?
Each correct answer represents a complete solution. Choose all that apply.
- A. For interoperability, IPv4 addresses use the last 32 bits of IPv6 addresse
- B. It increases the number of available IP addresse
- C. It provides improved authentication and securit
- D. It uses 128-bit addresse
- E. It uses longer subnet masks than those used in IPv4.
Answer: ABCD
NEW QUESTION 7
Which of the following are core TCP/IP protocols that can be implemented with Windows NT to connect computers and internetworks?
Each correct answer represents a complete solution. Choose all that apply.
- A. Address Resolution Protocol (ARP)
- B. Network Link Protocol (NWLink)
- C. Internet Control Message Protocol (ICMP)
- D. User Datagram Protocol (UDP)
Answer: ACD
NEW QUESTION 8
Which of the following are well-known ports?
Each correct answer represents a complete solution. Choose two.
- A. 443
- B. 21
- C. 1024
- D. 8080
Answer: AB
NEW QUESTION 9
Which of the following Windows Registry key contains the password file of the user?
- A. HKEY_USER
- B. HKEY_DYN_DATA
- C. HKEY_LOCAL_MACHINE
- D. HKEY_CURRENT_CONFIG
Answer: C
NEW QUESTION 10
You work as a desktop administrator for BlueSkwer.com. You are logged on to a Windows 7 computer with administrator rights. You have run the 'netsh interface IPv6 show interface' command which displays the following: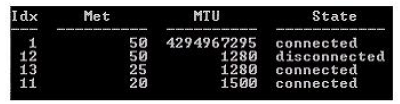
What is the first interface index used for?
- A. 6to4 tunneling
- B. MAC address
- C. Intra-Site Automatic Tunnel Addressing Protocol
- D. Loopback
Answer: D
NEW QUESTION 11
Which of the following is used over the Internet for better security?
- A. SOCKS
- B. S-HTTP
- C. Wingate
- D. IMAP Server
Answer: A
NEW QUESTION 12
Adam works as a Security Administrator for Umbrella. A project has been assigned to him to test the network security of the company. He created a webpage to discuss the progress of the tests with employees who were interested in following the test. Visitors were allowed to click on a company's icon to mark the progress of the test. Adam successfully embeds a keylogger. He also added some statistics on the webpage. The firewall protects the network well and allows strict Internet access.
How was security compromised and how did the firewall respond?
- A. The attack was Cross Site Scripting and the firewall blocked i
- B. Security was not compromised as the webpage was hosted internall
- C. The attack was social engineering and the firewall did not detect i
- D. Security was compromised as keylogger is invisible for firewal
Answer: C
NEW QUESTION 13
Allen works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate a computer, which is used by the suspect to sexually harass the victim using instant messenger program. Suspect's computer runs on Windows operating system. Allen wants to recover password from instant messenger program, which suspect is using, to collect the evidence of the crime. Allen is using Helix Live for this purpose. Which of the following utilities of Helix will he use to accomplish the task?
- A. Asterisk Logger
- B. Access PassView
- C. Mail Pass View
- D. MessenPass
Answer: D
NEW QUESTION 14
Which of the following statements are true about routers?
Each correct answer represents a complete solution. Choose all that apply.
- A. Routers do not limit physical broadcast traffi
- B. Routers organize addresses into classes, which are used to determine how to move packets from one network to anothe
- C. Routers act as protocol translators and bind dissimilar network
- D. Routers are responsible for making decisions about which of several paths network (or Internet) traffic will follo
Answer: BCD
NEW QUESTION 15
Which of the following programs in UNIX is used to identify and fix lost blocks or orphans?
- A. File Check (fck)
- B. Block Check (bsck)
- C. Lost Block (lck)
- D. Filesystem Check (fsck)
Answer: D
NEW QUESTION 16
Which of the following statements is true about ICMP packets?
Each correct answer represents a complete solution. Choose all that apply.
- A. The PING utility uses them to verify connectivity between two host
- B. They guarantee the delivery of datagram
- C. They are encapsulated within IP datagram
- D. They use UDP datagram
- E. They are used to report errors if a problem in IP processing occur
Answer: ACE
NEW QUESTION 17
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate computer of an unfaithful employee of SecureEnet Inc. Suspect's computer runs on Windows operating system. Which of the following sources will Adam investigate on a Windows host to collect the electronic evidences?
Each correct answer represents a complete solution. Choose all that apply.
- A. Allocated cluster
- B. Swap files
- C. Slack spaces
- D. Unused and hidden partition
Answer: BCD
NEW QUESTION 18
Host-based IDS (HIDS) is an Intrusion Detection System that runs on the system to be monitored. HIDS monitors only the data that it is directed to, or originates from the system on which HIDS is installed. Besides monitoring network traffic for detecting attacks, it can also monitor other parameters of the system such as running processes, file system access and integrity, and user logins for identifying malicious activities. Which of the following tools are examples of HIDS?
Each correct answer represents a complete solution. Choose all that apply.
- A. HPing
- B. BlackIce Defender
- C. Tripwire
- D. Legion
Answer: BC
NEW QUESTION 19
Which of the following malicious programs changes its signature continuously to be invisible to IDS?
- A. Boot sector virus
- B. Trojan
- C. Malware
- D. Polymorphic virus
Answer: D
NEW QUESTION 20
Adam works as a Senior Programmer for Umbrella Inc. A project has been assigned to him to write a short program to gather user input for a Web application. He wants to keep his program neat and simple. His chooses to use printf(str) where he should have ideally used printf("%s", str).
What attack will his program expose the Web application to?
- A. Sequence++ attack
- B. Cross Site Scripting attack
- C. Format string attack
- D. SQL injection attack
Answer: C
NEW QUESTION 21
......
Thanks for reading the newest GCIA exam dumps! We recommend you to try the PREMIUM Thedumpscentre.com GCIA dumps in VCE and PDF here: https://www.thedumpscentre.com/GCIA-dumps/ (508 Q&As Dumps)
