GCIA Exam
Latest GIAC Certified Intrusion Analyst GCIA Free Samples

Exam Code: GCIA (Practice Exam Latest Test Questions VCE PDF)
Exam Name: GIAC Certified Intrusion Analyst
Certification Provider: GIAC
Free Today! Guaranteed Training- Pass GCIA Exam.
Free demo questions for GIAC GCIA Exam Dumps Below:
NEW QUESTION 1
You work as a Network Administrator for McRobert Inc. Your company has a TCP/IP-based network.
You want to know the statistics of each protocol installed on your computer. Which of the following commands will you use?
- A. NBTSTAT -r
- B. NETSTAT -s
- C. NETSTAT -r
- D. NBTSTAT -s
Answer: B
NEW QUESTION 2
In a complex network, Router transfers data packets by observing some form of parameters or metrics provided in the routing table. Which of the following metrics is NOT included in the routing table?
- A. Frequency
- B. Delay
- C. Load
- D. Bandwidth
Answer: A
NEW QUESTION 3
John works as a professional Ethical Hacker. He has been assigned a project for testing the security of www.we-are-secure.com. He scans the We-are-secure server and gets the following result:
sysDescr.0 = STRING. "SunOS we-are-secure.com 4.1.3_U1 1 sun4m"
sysObjectID.0 = OID. enterprises.hp.nm.hpsystem.10.1.1
sysUpTime.0 = Timeticks: (156474552) 18 days, 12:00:09
sysContact.0 = STRING. ""
sysName.0 = STRING. "we-are-secure.com"
sysLocation.0 = STRING. ""
sysServices.0 = INTEGER: 6
Which of the following tools is John using to perform the scan?
- A. snmpwalk
- B. Kismet
- C. AirMagnet
- D. AiroPeek
Answer: A
NEW QUESTION 4
You work as a Network Administrator of a TCP/IP network. You are having DNS resolution problem. Which of the following utilities will you use to diagnose the problem?
- A. IPCONFIG
- B. PING
- C. TRACERT
- D. NSLOOKUP
Answer: D
NEW QUESTION 5
Which of the following tools are used to determine the hop counts of an IP packet?
Each correct answer represents a complete solution. Choose two.
- A. TRACERT
- B. Ping
- C. IPCONFIG
- D. Netstat
Answer: AB
NEW QUESTION 6
Which of the following utilities produces the output shown in the image below?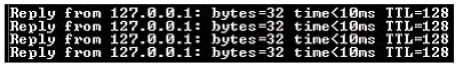
- A. IPCONFIG
- B. PING
- C. PATHPING
- D. TRACERT
Answer: B
NEW QUESTION 7
Which of the following are not functions of the SNORT application?
Each correct answer represents a complete solution. Choose two.
- A. Packet logging
- B. Virus detection
- C. Hard disk drive scanning
- D. Packet sniffing
- E. Intrusion detection
Answer: BC
NEW QUESTION 8
What is the function of PING LOCALHOST command?
- A. It verifies that DNS is correctly set up to allow communication with a host, named LOCALHO S
- B. It verifies that TCP/IP is bound correctly to the network adapter by communicating with the domain controlle
- C. It verifies that TCP/IP is bound correctly to the network adapter by communicating with the successfully initialized IP addres
- D. It verifies that TCP/IP is bound correctly to the network adapter by communicating with the loopback address 127.0.0.1.
Answer: D
NEW QUESTION 9
Peter works as a professional Computer Hacking Forensic Investigator for eLaw-Suit law firm. He is working on a case of a cyber crime. Peter knows that the good investigative report should not only communicate the relevant facts, but also present expert opinion. This report should not include the cases in which the expert acted as a lay witness. Which of the following type of witnesses is a lay witness?
- A. One who can give a firsthand account of something seen, heard, or experience
- B. One with special knowledge of the subject about which he or she is testifyin
- C. One who observes an even
- D. One who is not qualified as an expert witnes
Answer: D
NEW QUESTION 10
Which of the following file systems supports the hot fixing feature?
- A. FAT16
- B. exFAT
- C. NTFS
- D. FAT32
Answer: C
NEW QUESTION 11
Which of the following classes refers to the fire involving electricity?
- A. Class B
- B. Class D
- C. Class A
- D. Class C
Answer: D
NEW QUESTION 12
Which of the following is used as a default port by the TELNET utility?
- A. 21
- B. 80
- C. 23
- D. 20
Answer: C
NEW QUESTION 13
What is the maximum size of an IP datagram for Ethernet?
- A. 4500 bytes
- B. 1024 bytes
- C. 1200 bytes
- D. 1500 bytes
Answer: D
NEW QUESTION 14
Which of the following proxy servers can be used for spamming?
- A. Caching proxy server
- B. Web proxy server
- C. Open proxy server
- D. Anonymizing proxy server
Answer: C
NEW QUESTION 15
Which of the following is a checksum algorithm?
- A. Hash buster
- B. Snort
- C. Adler-32
- D. Dsniff
Answer: C
NEW QUESTION 16
You work as a System Administrator for McNeil Inc. The company has a Linux-based network. You are a root user on the Red Hat operating system. Your network is configured for IPv6 IP addressing. Which of the following commands will you use to test TCP/IP connectivity?
- A. ping6
- B. ifconfig
- C. traceroute
- D. ping
Answer: A
NEW QUESTION 17
Rick works as a Computer Forensic Investigator for BlueWells Inc. He has been informed that some confidential information is being leaked out by an employee of the company. Rick suspects that someone is sending the information through email. He checks the emails sent by some employees to other networks. Rick finds out that Sam, an employee of the Sales department, is continuously sending text files that contain special symbols, graphics, and signs. Rick suspects that Sam is using the Steganography technique to send data in a disguised form. Which of the following techniques is Sam using?
Each correct answer represents a part of the solution. Choose all that apply.
- A. Text Semagrams
- B. Linguistic steganography
- C. Technical steganography
- D. Perceptual masking
Answer: AB
NEW QUESTION 18
Which of the following would allow you to automatically close connections or restart a server or service when a DoS attack is detected?
- A. Active IDS
- B. Signature-based IDS
- C. Passive IDS
- D. Network-based IDS
Answer: A
NEW QUESTION 19
Which of the following tools is used to detect spam email without checking the content?
- A. Kismet
- B. EtherApe
- C. DCC
- D. Sniffer
Answer: C
NEW QUESTION 20
Which of the following techniques is used to log network traffic?
- A. Cracking
- B. IP address spoofing
- C. Tunneling
- D. Sniffing
Answer: D
NEW QUESTION 21
......
P.S. DumpSolutions.com now are offering 100% pass ensure GCIA dumps! All GCIA exam questions have been updated with correct answers: https://www.dumpsolutions.com/GCIA-dumps/ (508 New Questions)
