GCIH Exam
Replace GIAC Certified Incident Handler GCIH Exam Question

It is more faster and easier to pass the GIAC GCIH exam by using Top Quality GIAC GIAC Certified Incident Handler questuins and answers. Immediate access to the Down to date GCIH Exam and find the same core area GCIH questions with professionally verified answers, then PASS your exam with a high score now.
Free demo questions for GIAC GCIH Exam Dumps Below:
NEW QUESTION 1
Adam works as a Security Administrator for the Umbrella Inc. A project has been assigned to him to strengthen the security policies of the company, including its password policies. However, due to some old applications, Adam is only able to enforce a password group policy in Active Directory with a minimum of 10 characters. He informed the employees of the company, that the new password policy requires that everyone must have complex passwords with at least 14 characters. Adam wants to ensure that everyone is using complex passwords that meet the new security policy requirements. He logged on to one of the network's domain controllers and runs the following command: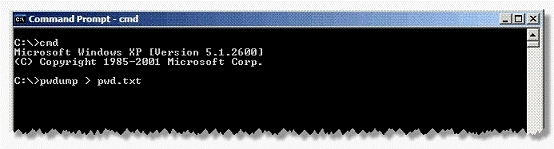
Which of the following actions will this command take?
- A. Dumps the SAM password hashes to pwd.txt
- B. Dumps the SAM password file to pwd.txt
- C. Dumps the Active Directory password hashes to pwd.txt
- D. The password history file is transferred to pwd.txt
Answer: A
NEW QUESTION 2
Mark works as a Network Administrator for Perfect Inc. The company has both wired and wireless networks. An attacker attempts to keep legitimate users from accessing services that they require. Mark uses IDS/IPS sensors on the wired network to mitigate the attack. Which of the following attacks best describes the attacker's intentions?
- A. Internal attack
- B. Reconnaissance attack
- C. Land attack
- D. DoS attack
Answer: D
NEW QUESTION 3
Which of the following is a type of computer security vulnerability typically found in Web applications that allow code injection by malicious Web users into the Web pages viewed by other users?
- A. SID filtering
- B. Cookie poisoning
- C. Cross-site scripting
- D. Privilege Escalation
Answer: C
NEW QUESTION 4
John is a malicious attacker. He illegally accesses the server of We-are-secure Inc. He then places a backdoor in the We-are-secure server and alters its log files. Which of the following steps of malicious hacking includes altering the server log files?
- A. Maintaining access
- B. Covering tracks
- C. Gaining access
- D. Reconnaissance
Answer: B
NEW QUESTION 5
You are monitoring your network's behavior. You find a sudden increase in traffic on the network. It seems to come in bursts and emanate from one specific machine. You have been able to determine that a user of that machine is unaware of the activity and lacks the computer knowledge required to be responsible for a computer attack. What attack might this indicate?
- A. Spyware
- B. Ping Flood
- C. Denial of Service
- D. Session Hijacking
Answer: A
NEW QUESTION 6
In which of the following attacking methods does an attacker distribute incorrect IP address?
- A. IP spoofing
- B. Mac flooding
- C. DNS poisoning
- D. Man-in-the-middle
Answer: C
NEW QUESTION 7
Which of the following types of malware can an antivirus application disable and destroy?
Each correct answer represents a complete solution. Choose all that apply.
- A. Rootkit
- B. Trojan
- C. Crimeware
- D. Worm
- E. Adware
- F. Virus
Answer: ABDF
NEW QUESTION 8
Which of the following tools can be used to perform brute force attack on a remote database?
Each correct answer represents a complete solution. Choose all that apply.
- A. SQLBF
- B. SQLDict
- C. FindSA
- D. nmap
Answer: ABC
NEW QUESTION 9
Which of the following types of malware does not replicate itself but can spread only when the circumstances are beneficial?
- A. Mass mailer
- B. Worm
- C. Blended threat
- D. Trojan horse
Answer: D
NEW QUESTION 10
108 ms 14 0.so-4-1-0.TL1.ATL5.ALTER.NET (152.63.10.129) 37.894 ms 33.244 ms
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 11
TCP/IP stack fingerprinting is the passive collection of configuration attributes from a remote device during standard layer 4 network communications. The combination of parameters may then be used to infer the remote operating system (OS fingerprinting), or incorporated into a device fingerprint.
Which of the following Nmap switches can be used to perform TCP/IP stack fingerprinting?
- A. nmap -sS
- B. nmap -sU -p
- C. nmap -O -p
- D. nmap -sT
Answer: C
NEW QUESTION 12
You run the following bash script in Linux:
for i in 'cat hostlist.txt' ;do
nc -q 2 -v $i 80 < request.txt done
Where, hostlist.txt file contains the list of IP addresses and request.txt is the output file. Which of the following tasks do you want to perform by running this script?
- A. You want to put nmap in the listen mode to the hosts given in the IP address list.
- B. You want to perform banner grabbing to the hosts given in the IP address list.
- C. You want to perform port scanning to the hosts given in the IP address list.
- D. You want to transfer file hostlist.txt to the hosts given in the IP address list.
Answer: B
NEW QUESTION 13
Which of the following functions can be used as a countermeasure to a Shell Injection attack?
Each correct answer represents a complete solution. Choose all that apply.
- A. escapeshellarg()
- B. mysql_real_escape_string()
- C. regenerateid()
- D. escapeshellcmd()
Answer: AD
NEW QUESTION 14
A Denial-of-Service (DoS) attack is mounted with the objective of causing a negative impact on the performance of a computer or network. It is also known as network saturation attack or bandwidth consumption attack. Attackers perform DoS attacks by sending a large number of protocol packets to a network. The problems caused by a DoS attack are as follows:
l Saturation of network resources
l Disruption of connections between two computers, thereby preventing communications between services
l Disruption of services to a specific computer
l Failure to access a Web site
l Increase in the amount of spam
Which of the following can be used as countermeasures against DoS attacks?
Each correct answer represents a complete solution. Choose all that apply.
- A. Blocking undesired IP addresses
- B. Applying router filtering
- C. Disabling unneeded network services
- D. Permitting network access only to desired traffic
Answer: ABCD
NEW QUESTION 15
In which of the following attacks does an attacker use packet sniffing to read network traffic between two parties to steal the session cookie?
- A. Session fixation
- B. Cross-site scripting
- C. Session sidejacking
- D. ARP spoofing
Answer: C
NEW QUESTION 16
......
P.S. 2passeasy now are offering 100% pass ensure GCIH dumps! All GCIH exam questions have been updated with correct answers: https://www.2passeasy.com/dumps/GCIH/ (328 New Questions)
