GCIH Exam
Highest Quality GIAC GCIH Exam Question Online

we provide 100% Guarantee GIAC GCIH actual exam which are the best for clearing GCIH test, and to get certified by GIAC GIAC Certified Incident Handler. The GCIH Questions & Answers covers all the knowledge points of the real GCIH exam. Crack your GIAC GCIH Exam with latest dumps, guaranteed!
GIAC GCIH Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which of the following is a network worm that exploits the RPC sub-system vulnerability present in the Microsoft Windows operating system?
- A. Win32/Agent
- B. WMA/TrojanDownloader.GetCodec
- C. Win32/Conflicker
- D. Win32/PSW.OnLineGames
Answer: C
NEW QUESTION 2
Which of the following is executed when a predetermined event occurs?
- A. Trojan horse
- B. Logic bomb
- C. MAC
- D. Worm
Answer: B
NEW QUESTION 3
Which of the following is used to gather information about a remote network protected by a firewall?
- A. Warchalking
- B. Wardialing
- C. Firechalking
- D. Firewalking
Answer: D
NEW QUESTION 4
Choose the correct actions performed during the Eradication step of the incident handling process.
Solution:
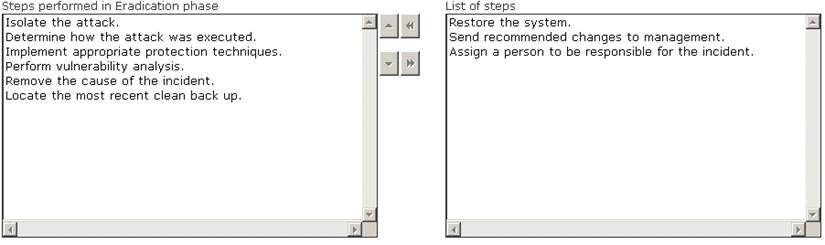
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 5
Which of the following steps of incident response is steady in nature?
- A. Containment
- B. Eradication
- C. Preparation
- D. Recovery
Answer: C
NEW QUESTION 6
Maria works as a professional Ethical Hacker. She recently got a project to test the security of www.we-are-secure.com. Arrange the three pre -test phases of the attack to test the security of weare-secure.
Solution:
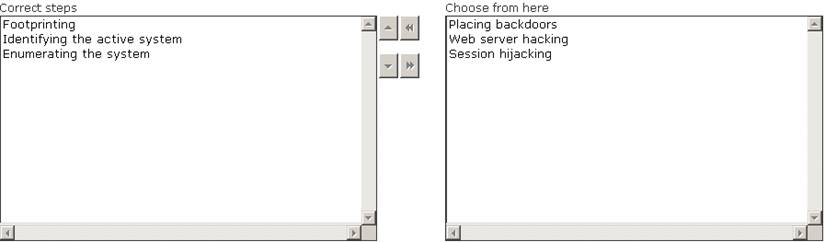
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 7
Which of the following netcat parameters makes netcat a listener that automatically restarts itself when a connection is dropped?
- A. -u
- B. -l
- C. -p
- D. -L
Answer: D
NEW QUESTION 8
Which of the following statements about a Trojan horse are true?
Each correct answer represents a complete solution. Choose two.
- A. It is a macro or script that attaches itself to a file or template.
- B. The writers of a Trojan horse can use it later to gain unauthorized access to a computer.
- C. It is a malicious software program code that resembles another normal program.
- D. It infects the boot record on hard disks and floppy disks.
Answer: BC
NEW QUESTION 9
You want to connect to your friend's computer and run a Trojan on it. Which of the following tools will you use to accomplish the task?
- A. PSExec
- B. Remoxec
- C. Hk.exe
- D. GetAdmin.exe
Answer: A
NEW QUESTION 10
Many organizations create network maps of their network system to visualize the network and understand the relationship between the end devices and the transport layer that provide services.
Which of the following are the techniques used for network mapping by large organizations?
Each correct answer represents a complete solution. Choose three.
- A. Packet crafting
- B. Route analytics
- C. SNMP-based approaches
- D. Active Probing
Answer: BCD
NEW QUESTION 11
Brutus is a password cracking tool that can be used to crack the following authentications:
l HTTP (Basic Authentication)
l HTTP (HTML Form/CGI)
l POP3 (Post Office Protocol v3)
l FTP (File Transfer Protocol)
l SMB (Server Message Block)
l Telnet
Which of the following attacks can be performed by Brutus for password cracking?
Each correct answer represents a complete solution. Choose all that apply.
- A. Hybrid attack
- B. Replay attack
- C. Dictionary attack
- D. Brute force attack
- E. Man-in-the-middle attack
Answer: ACD
NEW QUESTION 12
Which of the following types of attacks slows down or stops a server by overloading it with requests?
- A. DoS attack
- B. Impersonation attack
- C. Network attack
- D. Vulnerability attack
Answer: A
NEW QUESTION 13
Which of the following applications is NOT used for passive OS fingerprinting?
- A. Networkminer
- B. Satori
- C. p0f
- D. Nmap
Answer: D
NEW QUESTION 14
Which of the following Trojans is used by attackers to modify the Web browser settings?
- A. Win32/FlyStudio
- B. Trojan.Lodear
- C. WMA/TrojanDownloader.GetCodec
- D. Win32/Pacex.Gen
Answer: A
NEW QUESTION 15
Which of the following is a reason to implement security logging on a DNS server?
- A. For preventing malware attacks on a DNS server
- B. For measuring a DNS server's performance
- C. For monitoring unauthorized zone transfer
- D. For recording the number of queries resolved
Answer: C
NEW QUESTION 16
......
Thanks for reading the newest GCIH exam dumps! We recommend you to try the PREMIUM Allfreedumps.com GCIH dumps in VCE and PDF here: https://www.allfreedumps.com/GCIH-dumps.html (328 Q&As Dumps)
