GSNA Exam
Pinpoint GIAC GSNA Real Exam Online

It is more faster and easier to pass the GIAC GSNA exam by using Accurate GIAC GIAC Systems and Network Auditor questuins and answers. Immediate access to the Refresh GSNA Exam and find the same core area GSNA questions with professionally verified answers, then PASS your exam with a high score now.
Online GSNA free questions and answers of New Version:
NEW QUESTION 1
Sarah works as a Web Developer for XYZ CORP. She develops a Web site for the company. She uses tables in the Web site. Sarah embeds three tables within a table. What is the technique of embedding tables within a table known as?
- A. Nesting tables
- B. Stacking tables
- C. CSS tables
- D. Horned tables
Answer: A
Explanation:
In general, nesting means embedding a construct inside another. Nesting tables is a technique in which one or more tables are embedded within a table. Answer B, C, D are incorrect. There are no techniques such as stacking tables, horned tables, or CSS tables.
NEW QUESTION 2
Mark is an attacker. He wants to discover wireless LANs by listening to beacons or sending probe requests and thereby provide a launch point for further attacks. Which of the following tools can he use to accomplish the task?
- A. DStumbler
- B. Wellenreiter
- C. KisMAC
- D. Airmon-ng
Answer: ACD
Explanation:
War driving is an attack in which the attacker discovers wireless LANs by listening to beacons or sending probe requests, thereby providing a launch point for further attacks. Airmon-ng, DStumbler, KisMAC, MacStumbler, NetStumbler, Wellenreiter, and WiFiFoFum are the tools that can be used to perform a war driving attack. Answer B is incorrect. Wellenreiter is a tool that is used to perform MAC spoofing attacks.
NEW QUESTION 3
Which of the following services are provided by the proxy servers?
- A. Intrusion detection
- B. Logging
- C. Hiding network resources
- D. Caching
Answer: BCD
Explanation:
A proxy server is a very important element for firewall applications. The services that it provides are as follows: Hide network resources: Proxy replaces the network IP address with a single IP address. Multiple systems can use a single IP address. Logging: A proxy server can log incoming and outgoing access, allowing a user to see every possible details of successful and failed connections. Cache: A proxy server can save information obtained from the Internet. It regularly updates these copies and automatically shows these pages, and will thus not need to access the Internet to view them.
NEW QUESTION 4
Which of the following statements about the traceroute utility are true?
- A. It uses ICMP echo packets to display the Fully Qualified Domain Name (FQDN) and the IP address of each gateway along the route to the remote host.
- B. It records the time taken for a round trip for each packet at each router.
- C. It is an online tool that performs polymorphic shell code attacks.
- D. It generates a buffer overflow exploit by transforming an attack shell code so that the new attack shell code cannot be recognized by any Intrusion Detection Systems.
Answer: AB
Explanation:
Traceroute is a route-tracing utility that displays the path an IP packet takes to reach its destination. It uses ICMP echo packets to display the Fully Qualified Domain Name (FQDN) and the IP address of each gateway along the route to the remote host. This tool also records the time taken for a round trip for each packet at each router that can be used to find any faulty router along the path. Answer C, D are incorrect. Traceroute does not perform polymorphic shell code attacks. Attacking tools such as ADMutate areused to perform polymorphic shell code attacks.
NEW QUESTION 5
You have made a program secure.c to display which ports are open and what types of services are running on these ports. You want to write the program's output to standard output and simultaneously copy it into a specified file. Which of the following commands will you use to accomplish the task?
- A. cat
- B. more
- C. less
- D. tee
Answer: D
Explanation:
You will use the tee command to write its content to standard output and simultaneously copy it into the specified file. The tee command is used to split the output of a program so that it can be seen on the display and also be saved in a file. It can also be used to capture intermediate output before the data is altered by another command or program. The tee command reads standard input, then writes its content to standard output, and simultaneously copies it into the specified file(s) or variables. The syntax of the tee command is as follows: tee [-a] [-i] [File] where, the -a option appends the output to the end of File instead of writing over it and the -i option is used to ignore interrupts. Answer A is incorrect. The concatenate (cat) command is used to display or print the contents of a file. Syntax: cat filename For example, the following command will display the contents of the /var/log/dmesg file: cat /var/log/dmesg Note: The more command is used in conjunction with the cat command to prevent scrolling of the screen while displaying the contents of a file. Answer C is incorrect. The less command is used to view (but not change) the contents of a text file, one screen at a time. It is similar to the more command. However, it has the extended capability of allowing both forwarB, Dackward navigation through the file. Unlike most Unix text editors/viewers, less does not need to read the entire file before starting; therefore, it has faster load times with large files. The command syntax of the less command is as follows: less [options] file_name Where,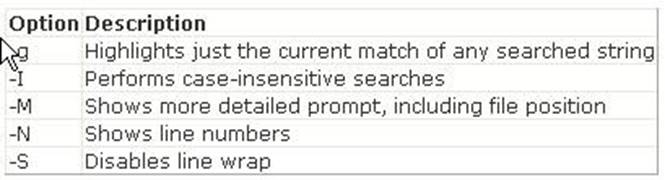
Answer B is incorrect. The more command is used to view (but not modify) the contents of a text file on the terminal screen at a time. The syntax of the more command is as follows: more [options] file_name Where,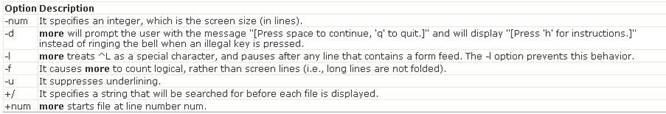
NEW QUESTION 6
Samantha works as a Web Developer for XYZ CORP. She develops a Web application using Visual InterDev. She wants to group a series of HTML elements together so that an action can be performed collectively on them. Which of the following tags will Samantha use to accomplish this?
- A. DIV
- B. GROUP
- C. BODY
- D. SPAN
Answer: A
Explanation:
DIV is an HTML tag that groups a series of elements into a larger group. It can be used when an action needs to be performed collectively on the grouped elements. The DIV tag acts as a container for other elements. Answer D is incorrect. The SPAN tag is used within an element to group a part of it. For example, this tag can be used to group a few sentences from within a paragraph, so that a particular action can be performed only on them. Answer C is incorrect. The BODY tag is used to specify the beginning and end of
the document body. Answer B is incorrect. There is no tag such as GROUP in HTML.
NEW QUESTION 7
Which of the following are attributes of the <TABLE> tag? (Choose three)
- A. BORDER
- B. ALIGN
- C. TD
- D. WIDTH
Answer: ABD
Explanation:
The WIDTH attribute of the <TABLE> tag is used to set the width of a table. Width can be specified in pixels and percentage. For example, if a table of the same width as that of the parent object has to be created, the WIDTH attribute must be set to 100%. The ALIGN attribute aligns the table within the text flow. By default alignment is set to left. The BORDER attribute of the <TABLE> tag is used to set the width of the table border. Answer C is incorrect. <TD> is not an attribute of the <TABLE> tag. It is a tag used to specify cells in a table.
NEW QUESTION 8
John works as a Network Administrator for Perfect Solutions Inc. The company has a
Linux-based network. John is working as a root user on the Linux operating system. He has recently backed up his entire Linux hard drive into the my_backup.tgz file. The size of the my_backup.tgz file is 800MB. Now, he wants to break this file into two files in which the size of the first file named my_backup.tgz.aa should be 600MB and that of the second file named my_backup.tgz.ab should be 200MB. Which of the following commands will John use to accomplish his task?
- A. split --verbose -b 200m my_backup.tgz my_backup.tgz
- B. split --verbose -b 200m my_backup.tgz my_backup.tgz
- C. split --verbose -b 600m my_backup.tgz my_backup.tgz
- D. split --verbose -b 600m my_backup.tgz my_backup.tgz
Answer: D
Explanation:
According to the scenario, John wants to break the my_backup.tgz file into two files in which the size of the first file named my_backup.tgz.aa should be 600MB and that of the second file named my_backup.tgz.ab should be 200MB. Hence, he will use the the split --verbose -b 600 my_backup.tgz my_backup.tgz. command, which will automatically break the first file into 600MB named my_backup.tgz.aa, and the rest of the data (200MB) will be assigned to the second file named my_backup.tgz.ab. The reason behind the names is that the split command provides suffixes as 'aa', 'ab', 'ac', ..., 'az', 'ba', 'bb', etc. in the broken file names by default. Hence, both conditions, the file names as well as the file sizes, match with this command. Note: If the size of the tar file my_backup.tgz is 1300MB, the command split --verbose -b 600 my_backup.tgz my_backup.tgz. breaks the my_backup.tgz file into three files, i.e., my_backup.tgz.aa of size 600MB, my_backup.tgz.ab of size 600MB, and my_backup.tgz.ac of size 100MB.
NEW QUESTION 9
You work as a Database Administrator for BigApple Inc. The Company uses Oracle as its database. You enabled standard database auditing. Later, you noticed that it has a huge impact on performance of the database by generating a large amount of audit data. How will you keep control on this audit data?
- A. By implementing principle of least privilege.
- B. By removing some potentially dangerous privileges.
- C. By setting the REMOTE_LOGIN_PASSWORDFILE instance parameter to NONE.
- D. By limiting the number of audit records generated to only those of interest.
Answer: D
Explanation:
Auditing is the process of monitoring and recording the actions of selected users in a database. Auditing is of the following types: Mandatory auditing Standard auditing Fine-grained auditing By focusing the audits as narrow as possible, you will get audit records for events that are of significance. If it is possible then try doing audit by session, not by access. When auditing a database the SYS.AUD$ table may grow many
gigabytes. You may delete or truncate it periodically to control the load of audit data. minimum set of privileges that are just sufficient to accomplish their requisite roles, so that even if the users try, they cannot perform those actions that may critically endanger the safety of data in the event of any malicious attacks. It is important to mention that some damage to data may still be unavoidable. Therefore, after identifying the scope of their role, users are allocated only those minimal privileges just compatible with that role. This helps in minimizing the damage to data due to malicious attacks. Grant of more privileges than necessary may make data critically vulnerable to malicious exploitation. The principle of least privilege is also known as the principle of minimal privilege and is sometimes also referred to as POLA, an abbreviation for the principle of least authority. The principle of least privilege is implemented to enhance fault tolerance, i.e. to protect data from malicious attacks. While applying the principle of least privilege, one should ensure that the parameter 07_DICTIONARY_ACCESSIBILITY in the data dictionary is set to FALSE, and revoke those packages and roles granted to a special pseudo-user known as Public that are not necessary to perform the legitimate actions, after reviewing them. This is very important since every user of the database, without exception, is automatically allocated the Public pseudo-user role. Some of the packages that are granted to the special pseudo- user known as Public are as follows: UTL_TCP UTL_SMTP UTL_HTTP UTL_FILE REMOTE_LOGIN_PASSWORDFILE is an initialization parameter used to mention whether or not Oracle will check for a password file and by which databases a password file can be used. The various properties of this initialization parameter are as follows: Parameter type: String Syntax: REMOTE_LOGIN_PASSWORDFILE = {NONE | SHARED | EXCLUSIVE}
Default value: NONE Removing some potentially dangerous privileges is a security option. All of the above discussed options are security steps and are not involved in standard database auditing.
NEW QUESTION 10
Which of the following processes are involved under the COBIT framework?
- A. Managing the IT workforce.
- B. Correcting all risk issues.
- C. Conducting IT risk assessments.
- D. Developing a strategic plan.
Answer: ACD
Explanation:
The Control Objectives for Information and related Technology (COBIT) is a set of best practices (framework) for information technology (IT) management, which provides managers, auditors, and IT users with a set of generally accepted measures, indicators, processes and best practices to assist them in maximizing the benefits derived through the use of information technology and developing appropriate IT governance and control in a company. It has the following 11 processes: Developing a strategic plan. Articulating the information architecture. Finding an optimal stage between the IT and the organization's strategy. Designing the IT function to match the organization's needs. Maximizing the return of the IT investment. Communicating IT policies to the user's community. Managing the IT workforce. Obeying external regulations, laws, and contracts. Conducting IT risk assessments. Maintaining a high-quality systems-development process. Incorporating sound project-management techniques. Answer B is incorrect. Correcting all risk issues does not come under auditing processes.
NEW QUESTION 11
Which of the following tools hides information about IIS Webservers so that they can be prevented from various attacks performed by an attacker?
- A. httprint
- B. ServerMask
- C. Whisker
- D. WinSSLMiM
Answer: B
Explanation:
ServerMask is a tool that is used to hide information about IIS Webservers. Since IIS Webservers are vulnerable to various attacks, such as, code red worm, iis unicode exploit, etc., to mitigate such attacks, ServerMask removes all unnecessary HTTP headers & response data, and file extensions like .asp or .aspx, which are clear indicators that a site is running on a Microsoft server. Besides this, ServerMask modifies the ASP session ID cookies values, default messages, pages and scripts of all kinds to misguide an attacker. Answer A is incorrect. httprint is a fingerprinting tool that is based on Web server characteristics to accurately identify Web servers. It works even when Web server may have been obfuscated by changing the server banner strings, or by plug-ins such as mod_security or servermask. Answer C is incorrect. Whisker is an HTTP/Web vulnerability scanner that is written in the PERL language. Whisker runs on both the Windows and UNIX environments. It provides functions for testing HTTP servers for many known security holes, particularly the presence of dangerous CGIs. Answer D is incorrect. WinSSLMiM is an HTTPS Man in the Middle attacking tool. It includes FakeCert, a tool used to make fake certificates. It can be used to exploit the Certificate Chain vulnerability in Internet Explorer. The tool works under Windows 9x/2000.
NEW QUESTION 12
Which of the following statements is true about the Digest Authentication scheme?
- A. A valid response from the client contains a checksum of the username, the password, the given random value, the HTTP method, and the requested URL.
- B. In this authentication scheme, the username and password are passed with everyrequest, not just when the user first types them.
- C. The password is sent over the network in clear text format.
- D. It uses the base64 encoding encryption scheme.
Answer: A
Explanation:
The Digest Authentication scheme is a replacement of the Basic Authentication scheme. This authentication scheme is based on the challenge response model. In Digest authentication, the password is never sent across the network in clear text format but is always transmitted as an MD5 digest of the user's password. In this way, the password cannot be determined with the help of a sniffer.
How does it work? In this authentication scheme, an optional header allows the server to specify the algorithm used to create the checksum or digest (by default, the MD5 algorithm). The Digest Authentication scheme provides the challenge using a randomly chosen value. This randomly chosen value is a server-specified data string which may be uniquely generated each time a 401 response is made. A valid response contains a checksum (by default, the MD5 checksum) of the username, the password, the given random value, the HTTP method, and the requested URL. In this way, the password is never sent in clear text format. Drawback: Although the password is not sent in clear text format, an attacker can gain access with the help of the digested password, since the digested password is really all the information needed to access the web site. Answer B, C, D are incorrect. These statements are true about the Basic Authentication scheme.
NEW QUESTION 13
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to find out when a particular user was last logged in. To accomplish this, you need to analyze the log configuration files. Which of the following Unix log configuration files can you use to accomplish the task?
- A. /var/log/btmp
- B. /var/log/messages
- C. /var/log/lastlog
- D. /var/log/wtmp
Answer: C
Explanation:
In Unix, the /var/log/lastlog file is used by the finger to find when a user was last logged in. Answer D is incorrect. In Unix, the /var/log/wtmp file stores the binary info of users that have been logged on. Answer A is incorrect. In Unix, the /var/log/btmp file is used to store information about failed logins. Answer B is incorrect. In Unix, the /var/log/messages is the main system message log file.
NEW QUESTION 14
You work as the Network Technician for XYZ CORP. The company has a Linux-based network. You are working on the Red Hat operating system. You want to view only the last 4 lines of a file named /var/log/cron. Which of the following commands should you use to accomplish the task?
- A. tail -n 4 /var/log/cron
- B. tail /var/log/cron
- C. cat /var/log/cron
- D. head /var/log/cron
Answer: A
Explanation:
The tail -n 4 /var/log/cron command will show the last four lines of the file /var/log/cron.
NEW QUESTION 15
Ryan wants to create an ad hoc wireless network so that he can share some important files with another employee of his company. Which of the following wireless security protocols should he choose for setting up an ad hoc wireless network?
(Choose two)
- A. WPA2 -EAP
- B. WPA-PSK
- C. WEP
- D. WPA-EAP
Answer: BC
Explanation:
Ryan can either choose WEP or WPA-PSK wireless protocol to set an ad hoc wireless network. Answer A is incorrect. WPA2-EAP cannot be chosen for an ad hoc wireless network, as it requires RADIUS (Remote Authentication Dial- In User Service) server for authentication. Answer D is incorrect. WPA-EAP cannot be chosen for an ad hoc wireless network, as it requires RADIUS (Remote Authentication Dial-In User Service) server for authentication.
NEW QUESTION 16
Which of the following commands can be used to intercept and log the Linux kernel messages?
- A. syslogd
- B. klogd
- C. sysklogd
- D. syslog-ng
Answer: BC
Explanation:
The klogd and sysklogd commands can be used to intercept and log the Linux kernel messages.
NEW QUESTION 17
John works as a Network Auditor for XYZ CORP. The company has a Windows-based network. John wants to conduct risk analysis for the company. Which of the following can be the purpose of this analysis? (Choose three)
- A. To ensure absolute safety during the audit
- B. To analyze exposure to risk in order to support better decision-making and proper management of those risks
- C. To try to quantify the possible impact or loss of a threat
- D. To assist the auditor in identifying the risks and threats
Answer: BCD
Explanation:
There are many purposes of conducting risk analysis, which are as follows: To try to quantify the possible impact or loss of a threat To analyze exposure to risk in order to support better decision-making and proper management of those risks To support risk-based audit decisions To assist the auditor in determining the audit objectives To assist the auditor in identifying the risks and threats Answer A is incorrect. The analysis of risk does not ensure absolute safety. The main purpose of using a risk-based audit strategy is to ensure that the audit adds value with meaningful information.
NEW QUESTION 18
Which of the following firewalls inspects the actual contents of packets?
- A. Circuit-level firewall
- B. Stateful inspection firewall
- C. Packet filtering firewall
- D. Application-level firewall
Answer: D
Explanation:
The application level firewall inspects the contents of packets, rather than the source/destination or connection between the two. An Application level firewall operates at the application layer of the OSI model. Answer A is incorrect. The circuit-level firewall regulates traffic based on whether or not a trusted connection has been established. It operates at the session layer of the OSI model. Answer C is incorrect. The packet filtering firewall filters traffic based on the headers. It operates at the network layer of the OSI model. Answer B is incorrect. The stateful inspection firewall assures the connection between the two parties is valid and inspects packets from this connection to assure the packets are not malicious.
NEW QUESTION 19
You work as a Network Administrator for XYZ CORP. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory- based single forest single domain network. You have installed a Windows Server 2008 computer. You have configured auditing on this server. The client computers of the company use the Windows XP Professional operating system. You want to audit each event that is related to a user managing an account in the user database on the computer
where the auditing is configured. To accomplish the task, you have enabled the Audit account management option on the server. Which of the following events can be audited by enabling this audit option?
- A. Access to an Active Directory object
- B. Change of password for a user account
- C. Addition of a user account to a group
- D. Creation of a user account
Answer: BCD
Explanation:
Audit account management is one of the nine audit settings that can be configured on a Windows computer. This option is enabled to audit each event that is related to a user managing an account in the user database on the computer where the auditing is configured. These events include the following: Creating a user account Adding a user account to a group Renaming a user account Changing password for a user account This option is also used to audit the changes to the domain account of the domain controllers.
NEW QUESTION 20
......
Thanks for reading the newest GSNA exam dumps! We recommend you to try the PREMIUM Thedumpscentre.com GSNA dumps in VCE and PDF here: https://www.thedumpscentre.com/GSNA-dumps/ (368 Q&As Dumps)
