GSNA Exam
The Secret Of GIAC GSNA Practice

Act now and download your GIAC GSNA test today! Do not waste time for the worthless GIAC GSNA tutorials. Download Up to the minute GIAC GIAC Systems and Network Auditor exam with real questions and answers and begin to learn GIAC GSNA with a classic professional.
GIAC GSNA Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which of the following tools monitors the radio spectrum for the presence of unauthorized, rogue access points and the use of wireless attack tools?
- A. Snort
- B. IDS
- C. Firewall
- D. WIPS
Answer: D
Explanation:
Wireless intrusion prevention system (WIPS) monitors the radio spectrum for the presence of unauthorized, rogue access points and the use of wireless attack tools. The system monitors the radio spectrum used by wireless LANs, and immediately alerts a systems administrator whenever a rogue access point is detected. Conventionally it is achieved by comparing the MAC address of the participating wireless devices. Rogue
devices can spoof MAC address of an authorized network device as their own. WIPS uses fingerprinting approach to weed out devices with spoofed MAC addresses. The idea is to compare the unique signatures exhibited by the signals emitted by each wireless device against the known signatures of pre-authorized, known wireless devices.
Answer B is incorrect. An Intrusion detection system (IDS) is used to detect unauthorized attempts to access and manipulate computer systems locally or through the Internet or an intranet. It can detect several types of attacks and malicious behaviors that can compromise the security of a network and computers. This includes network attacks against vulnerable services, unauthorized logins and access to sensitive data, and malware (e.g. viruses, worms, etc.). An IDS also detects attacks that originate from within a system. In most cases, an IDS has three main components: Sensors, Console, and Engine. Sensors generate security events. A console is used to alert and control sensors and to monitor events. An engine is used to record events and to generate security alerts based on received security events. In many IDS implementations, these three components are combined into a single device. Basically, following two types of IDS are used : Network- based IDS Host-based IDS Answer A is incorrect. Snort is an open source network intrusion prevention and detection system that operates as a network sniffer. It logs activities of the network that is matched with the predefined signatures. Signatures can be designed for a wide range of traffic, including Internet Protocol (IP), Transmission Control Protocol (TCP), User Datagram Protocol (UDP), and Internet Control Message Protocol (ICMP). The three main modes in which Snort can be configured are as follows: Sniffer mode: It reads the packets of the network and displays them in a continuous stream on the console. Packet logger mode: It logs the packets to the disk. Network intrusion detection mode: It is the most complex and configurable configuration, allowing Snort to analyze network traffic for matches against a user-defined rule set. Answer C is incorrect. A firewall is a tool to provide security to a network. It is used to protect an internal network or intranet against unauthorized access from the Internet or other outside networks. It restricts inbound and outbound access and can analyze all traffic between an internal network and the Internet. Users can configure a firewall to pass or block packets from specific IP addresses and ports.
NEW QUESTION 2
Which of the following types of firewall functions at the Session layer of OSI model?
- A. Packet filtering firewall
- B. Circuit-level firewall
- C. Switch-level firewall
- D. Application-level firewall
Answer: B
Explanation:
Circuit-level firewall operates at the Session layer of the OSI model. This type of firewall regulates traffic based on whether or not a trusted connection has been established.
NEW QUESTION 3
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP based switched network. A root bridge has been elected in the switched network. You have installed a new switch with a lower bridge ID than the existing root bridge. What will happen?
- A. The new switch starts advertising itself as the root bridge.
- B. The new switch divides the network into two broadcast domains.
- C. The new switch works as DR or BDR.
- D. The new switch blocks all advertisements.
Answer: A
Explanation:
The new switch starts advertising itself as the root bridge. It acts as it is the only bridge on the network. It has a lower Bridge ID than the existing root, so it is elected as the root bridge after the BPDUs converge and when all switches know about the new switch that it is the better choice. Answer B, C, D are incorrect. All these are not valid options, according to the given scenario.
NEW QUESTION 4
You are the Security Consultant and you frequently do vulnerability assessments on client computers. You want to have a standardized approach that would be applicable to all of your clients when doing a vulnerability assessment. What is the best way to do this?
- A. Utilize OVAL.
- B. Create your own standard and use it with all clients.
- C. Utilize each client's security policies when doing a vulnerability assessment for that client.
- D. Utilize the Microsoft security recommendations.
Answer: A
Explanation:
Open Vulnerability Assessment Language (OVAL) is a common language for security professionals to use when checking for the presence of vulnerabilities on computer systems. OVAL provides a baseline method for performing vulnerability assessments on local computer systems. Answer D is incorrect. While Microsoft security standards will be appropriate for many of your clients, they won't help clients using Linux, Macintosh, or Unix. They also won't give you insight into checking your firewalls or routers. Answer C is incorrect. This would not fulfill the requirement of having a standardized approach applicable to all clients. B is incorrect. This would not be the best way. You should use common industry standards, like OVAL.
NEW QUESTION 5
Which of the following can be the countermeasures to prevent NetBIOS NULL session enumeration in Windows 2000 operating systems?
- A. Denying all unauthorized inbound connections to TCP port 53
- B. Disabling SMB services entirely on individual hosts by unbinding WINS Client TCP/IP from the interface
- C. Editing the registry key HKLM\SYSTEM\CurrentControlSet\LSA and adding the value RestrictAnonymous
- D. Disabling TCP port 139/445
Answer: BCD
Explanation:
NetBIOS NULL session vulnerabilities are hard to prevent, especially if NetBIOS is needed as part of the infrastructure. One or more of the following steps can be taken to limit NetBIOS NULL session vulnerabilities: 1.Null sessions require access to the TCP 139 or TCP 445 port, which can be disabled by a Network Administrator. 2. A Network Administrator can also disable SMB services entirely on individual hosts by unbinding WINS Client TCP/IP from the interface. 3. A Network Administrator can also restrict the anonymous user by editing the registry values: a.Open regedit32, and go to HKLM\SYSTEM\CurrentControlSet\LSA. b.Choose edit > add value. Value name: RestrictAnonymous Data Type: REG_WORD Value: 2 Answer A is incorrect. TCP port 53 is the default port for DNS zone transfer. Although disabling it can help restrict DNS zone transfer enumeration, it is not useful as a countermeasure against the NetBIOS NULL session enumeration.
NEW QUESTION 6
You work as a Desktop Support Technician for XYZ CORP. The company uses a Windows-based network comprising 50 Windows XP Professional computers. You want to
include the Safe Mode with Command Prompt feature into the boot.ini file of a Windows XP Professional computer. Which of the following switches will you use?
- A. /safeboot:network /sos /bootlog /noguiboot
- B. /safeboot:minimal /sos /bootlog /noguiboot
- C. /safeboot:minimal(alternateshell) /sos /bootlog /noguiboot
- D. /safeboot:dsrepair /sos
Answer: C
Explanation:
Safe-mode boot switches are used in the Windows operating systems to use the afe-mode boot feature. To use this feature the user should press F8 during boot. These modes are available in the Boot.ini file. Users can also automate the boot process using this feature. Various switches used for various modes are given below:
NEW QUESTION 7
You work as a Network Administrator for XYZ CORP. The company has a TCP/IP-based network environment. The network contains Cisco switches and a Cisco router. You run the following command for a router interface: show interface serial0 You get the following output: Serial0 is administratively down, line protocol is down What will be your conclusion after viewing this output?
- A. There is a physical problem either with the interface or the cable attached to it.
- B. The router has no power.
- C. There is a problem related to encapsulation.
- D. The interface is shut down.
Answer: D
Explanation:
According to the question, the output displays that the interface is administratively down. Administratively down means that the interface is shut down. In order to up the interface, you will have to open the interface with the no shutdown command. Answer A is incorrect. Had there been a physical problem with the interface, the output would not have displayed "administratively down". Instead, the output would be as follows: serial0 is down, line protocol is down Answer B is incorrect. You cannot run this command on a router that is powered off. Answer C is incorrect. Encapsulation has nothing to do with the output displayed in the question.
NEW QUESTION 8
You are the security manager of Microliss Inc. Your enterprise uses a wireless network infrastructure with access points ranging 150-350 feet. The employees using the network complain that their passwords and important official information have been traced. You discover the following clues: The information has proved beneficial to an other company. The other company is located about 340 feet away from your office. The other company is also using wireless network. The bandwidth of your network has degraded to a great extent. Which of the following methods of attack has been used?
- A. A piggybacking attack has been performed.
- B. A DOS attack has been performed.
- C. The information is traced using Bluebugging.
- D. A worm has exported the information.
Answer: A
Explanation:
Piggybacking refers to access of a wireless Internet connection by bringing one's own computer within the range of another's wireless connection, and using that service without the subscriber's explicit permission or knowledge. It is a legally and ethically controversial practice, with laws that vary in jurisdictions around the world. While completely outlawed in some jurisdictions, it is permitted in others. The process of sending data along with the acknowledgment is called piggybacking. Answer C is incorrect. Bluebugging is an attack used only in a Bluetooth network. Bluebugging is a form of bluetooth attack often caused by a lack of awareness. Bluebugging tools allow attacker to "take control" of the victim's phone via the usage of the victim's Bluetooth phone headset. It does this by pretending to be the users bluetooth headset and therefore "tricking" the phone to obey its call commands. Answer D is incorrect. A worm is a software program that uses computer networks and security holes to replicate itself from one computer to another. It usually performs malicious actions, such as using the resources of computers as well as shutting down computers. Answer B is incorrect. A Denial-of-Service (DoS) attack is mounted with the objective of causing a negative impact on the performance of a computer or network. It is also known as a network saturation attack or bandwidth consumption attack. Attackers perform DoS attacks by sending a large number of protocol packets to the network. The effects of a DoS attack are as follows: Saturates network resources Disrupts connections between two computers, thereby preventing communications between services Disrupts services to a specific computer Causes failure to access a Web site Results in an increase in the amount of spam A Denial-of-Service attack is very common on the Internet because it is much easier to accomplish. Most of the DoS attacks rely on the weaknesses in the TCP/IP protocol.
NEW QUESTION 9
Which of the following statements about a screened host is true?
- A. It facilitates a more efficient use of the Internet connection bandwidth and hides the real IP addresses of computers located behind the proxy.
- B. It is a small network that lies in between the Internet and a private network.
- C. It provides added security by using Internet access to deny or permit certain traffic from the Bastion Host.
- D. It provides a physical connection between computers within a network.
Answer: C
Explanation:
A screened host provides added security by using Internet access to deny or permit certain traffic from the Bastion Host. Answer D is incorrect. A network interface card provides a physical connection between computers within a network.
Answer B is incorrect. Demilitarized zone (DMZ) or perimeter network is a small network that lies in between the Internet and a private network. It is the boundary between the Internet and an internal network, usually a combination of firewalls and bastion hosts that are gateways between inside networks and outside networks. DMZ provides a large enterprise network or corporate network the ability to use the Internet while still maintaining its security. Answer A is incorrect. A proxy server facilitates a more efficient use of the Internet connection bandwidth and hides the real IP addresses of computers located behind the proxy.
NEW QUESTION 10
With reference to the given case study, one of the security goals requires to configure a secure connection between the Boston distribution center and the headquarters. You want to implement IP filter to fulfill the security requirements. How should you implement IP filters at the headquarters? (Click the Exhibit button on the toolbar to see the case study.)
- A. Add source filters for the headquarters for UDP port 1701 and IP protocol 50.Add destination filters for the Boston distribution center for UDP port 1701 and IP protocol 50.
- B. Add source filters for the Boston distribution center for UDP port 80 and IP protocol 50. Add destination filters for headquarters for UDP port 80 and IP protocol 50.
- C. Add source filters for the headquarters for UDP port 80 and IP protocol 50.Add destination filters for the Boston distribution center for UDP port 80 and IP protocol 50.
- D. Add source filters for the Boston distribution center for UDP port 1701 and IP protocol 50.Add destination filters for the headquarters for UDP port 1701 and IP protocol 50.
Answer: D
Explanation:
To implement IP filters at the headquarters, add source filters for the Boston distribution center for UDP port 1701 and IP protocol 50. Also, add destination filters for the headquarters for UDP port 1701 and IP protocol 50. The Windows 2000 Router service provides routing services in the LAN and WAN environments, and over the Internet, using secure virtual private network (VPN) connections. The VPN connections are based on the Point-to-Point Tunneling Protocol (PPTP) and the Layer 2 Tunneling Protocol (L2TP) L2TP is very similar to PPTP but uses UDP, and therefore can be used over asynchronous transfer mode (ATM), Frame Relay, and X.25 networks as well. When L2TP is used over IP networks, it uses a UDP port 1701 packet format for both a control channel and a data channel. L2TP can also be used with IPSec to provide a fully secured network link. Further, IP packet filtering provides an ability to restrict the traffic into and out of each interface. Packet filtering is based on filters defined by the values of source and destination IP addresses, TCP, and UDP port numbers, and IP protocol numbers. Inbound filters that are
applied to the receiving traffic allow the receiving computer to match the traffic with the IP Filter List for the source IP address. Similarly, the outbound filters that are applied to the traffic leaving a computer towards a destination trigger a security negotiation for the destination IP address. That is why, to implement the IP filtering at the headquarters, you have to add a source address for the filters at the Boston center and a destination address for the filters at the headquarters.
NEW QUESTION 11
Zorp is a proxy firewall suite developed by Balabit IT Security. Which of the following statements are true about Zorp?
- A. It allows the administrators to fine-tune proxy decisions.
- B. Zorp aims for compliance with the Common Criteria/Application Level Firewall Protection Profile for Medium Robustness.
- C. It allows full analysis of embedded protocols.
- D. The GPL version of Zorp lacks much of the usability and functions from the other versions.
Answer: ABC
Explanation:
Zorp is a proxy firewall suite developed by Balabit IT Security. Its core framework allows the administrator to fine-tune proxy decisions (with its built-in script language), and fully analyze embedded protocols (such as SSL with an embedded POP3 or HTTP protocol). The FTP, HTTP, FINGER, WHOIS, TELNET, and SSL protocols are fully supported with an application-level gateway. Zorp aims for compliance with the Common Criteria/Application Level Firewall Protection Profile for Medium Robustness. Zorp is released under GNU/GPL and commercial license too. The GPL version is completely usable and functional; however, it lacks some of the more advanced functions available in the commercially available version only. Some of the Zorp supported protocols are Finger, Ftp, Http, Pop3, NNTP, IMAP4, RDP, RPC, SIP, SSL, SSH, Telnet, Whois, LDAP, RADIUS, TFtp, SQLNet NET8, Rsh, etc. Answer D is incorrect. The GPL version of Zorp is completely usable and functional; however, it lacks some of the more advanced functions available in the commercially available version only.
NEW QUESTION 12
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He wants to forward all the kernel messages to the remote host having IP address 192.168.0.1. Which of the following changes will he perform in the syslog.conf file to accomplish the task?
- A. kern.* @192.168.0.1
- B. !*.* @192.168.0.1
- C. !kern.* @192.168.0.1
- D. *.* @192.168.0.1
Answer: A
Explanation:
According to the scenario, John will make the following entry in the syslog.conf file to forward all the kernel messages to the remote host having IP address 192.168.0.1: kern.* @192.168.0.1 Answer D is incorrect. This entry will forward all the messages to the remote host having IP address 192.168.0.1. Answer B is incorrect. This entry will not forward any message to the remote host having IP address 192.168.0.1. Answer C is incorrect. This entry will not forward any kernel message to the remote host having IP address 192.168.0.1.
NEW QUESTION 13
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to run a command that forces all the unwritten blocks in the buffer cache to be written to the disk. Which of the following Unix commands can you use to accomplish the task?
- A. swapon
- B. tune2fs
- C. swapoff
- D. sync
Answer: D
Explanation:
The sync command is used to flush filesystem buffers. It ensures that all disk writes have been completed before the processor is halted or rebooted. Generally, it is preferable to use reboot or halt to shut down a system, as they may perform additional actions such as resynchronizing the hardware clock and flushing internal caches before performing a final sync. Answer B is incorrect. In Unix, the tune2fs command is used to adjust tunable filesystem parameters on the second extended filesystems. Answer A is incorrect. In Unix, the swapon command is used to activate a swap partition. Answer C is incorrect. In Unix, the swapoff command is used to de-activate a swap partition.
NEW QUESTION 14
You work as a Network Administrator for NTY Inc. The company has a secure wireless network. While auditing the network for maintaining security, you find an unknown node. You want to locate that node. Which tool will you use to pinpoint the actual physical location of the node?
- A. Kismet
- B. Ekahau
- C. WEPCrack
- D. AirSnort
Answer: B
Explanation:
Ekahau is an easy-to-use powerful and comprehensive tool for network site surveys and optimization. It is an auditing tool that can be used to pinpoint the actual physical location of wireless devices in the network. This tool can be used to make a map of the office and then perform the survey of the office. In the process, if one finds an unknown node, ekahau can be used to locate that node. Answer D is incorrect. AirSnort is a Linux-based WLAN WEP cracking tool that recovers encryption keys. AirSnort operates by passively monitoring transmissions. It uses Ciphertext Only Attack and captures approximately 5 to 10 million packets to decrypt the WEP keys.
Answer A is incorrect. Kismet is a Linux-based 802.11 wireless network sniffer and intrusion detection system. It can work with any wireless card that supports raw monitoring (rfmon) mode. Kismet can sniff 802.11b, 802.11a, 802.11g, and 802.11n traffic. Kismet can be used for the following tasks: To identify networks by passively collecting packets To detect standard named networks To detect masked networks To collect the presence of non-beaconing networks via data traffic Answer C is incorrect. WEPcrack is a wireless network cracking tool that exploits the vulnerabilities in the RC4 Algorithm, which comprises the WEP security parameters. It mainly consists of three tools, which are as follows: WeakIVGen: It allows a user to emulate the encryption output of 802.11 networks to weaken the secret key used to encrypt the network traffic. Prism-getIV: It analyzes packets of information until ultimately matching patterns to the one known to decrypt the secret key. WEPcrack: It pulls the all beneficial data of WeakIVGen and Prism-getIV to decipher the network encryption.
NEW QUESTION 15
You work as a Network Administrator for XYZ CORP. The company has a TCP/IP-based network environment. The network contains Cisco switches and a Cisco router. A user is unable to access the Internet from Host B. You also verify that Host B is not able to connect to other resources on the network. The IP configuration of Host B is shown below: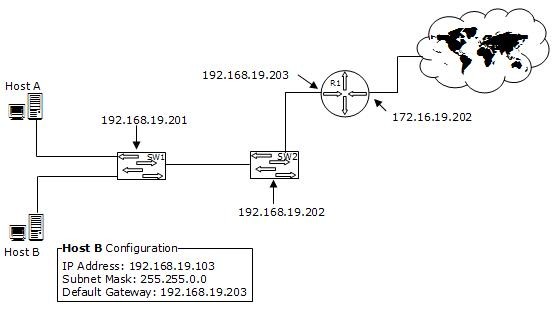
Which of the following is the most likely cause of the issue?
- A. An incorrect subnet mask is configured on Host B.
- B. The IP address of Host B is not from the correct IP address range of the network.
- C. There is an IP address conflict on the network.
- D. An incorrect default gateway is configured on Host B.
Answer: A
Explanation:
According to the network diagram, the IP address range used on the network is from the class C private address range. The class C IP address uses the following default subnet mask: 255.255.255.0 The question specifies that the subnet mask used in Host B is 255.255.0.0, which is an incorrect subnet mask.
NEW QUESTION 16
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP- based network. Rick, your assistant, is configuring some laptops for wireless access. For security, WEP needs to be configured for wireless communication. By mistake, Rick configures different WEP keys in a laptop than that is configured on the Wireless Access Point (WAP). Which of the following statements is true in such situation?
- A. The laptop will be able to access the wireless network but the security will be compromised.
- B. The WAP will allow the connection with the guest account's privileges.
- C. The laptop will be able to access the wireless network but other wireless devices will be unable to communicate with it.
- D. The laptop will not be able to access the wireless network.
Answer: D
Explanation:
In order to communicate with WAP, a wireless device needs to be configured
with the same WEP key. If there is any difference in the key, the device will not be able to access and communicate with the wireless network.
NEW QUESTION 17
You work as the Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. You are a root user on the Red Hat operating system. You want to keep an eye on the system log file /var/adm/messages. Which of the following commands should you use to read the file in real time?
- A. tail -n 3 /var/adm/messages
- B. tail -f /var/adm/messages
- C. cat /var/adm/messages
- D. tail /var/adm/messages
Answer: B
Explanation:
Using the -f option causes tail to continue to display the file in real time, showing added lines to the end of the file as they occur.
NEW QUESTION 18
Which of the following are the limitations for the cross site request forgery (CSRF) attack?
- A. The attacker must determine the right values for all the form inputs.
- B. The attacker must target a site that doesn't check the referrer header.
- C. The target site should have limited lifetime authentication cookies.
- D. The target site should authenticate in GET and POST parameters, not only cookies.
Answer: AB
Explanation:
Following are the limitations of cross site request forgeries to be successful:
* 1. The attacker must target either a site that doesn't check the Referer header (which is common) or a victim with a browser or plugin bug that allows Referer spoofing (which is rare).
* 2. The attacker must find a form submission at the target site that does something useful to the attacker (e.g., transfers money, or changes the victim's e-mail address or password).
* 3. The attacker must determine the right values for all the form inputs: if any of them are required to be secret authentication values or IDs that the attacker can't guess, the attack will fail.
* 4. The attacker must lure the victim to a Web page with malicious code while the victim is logged in to the target site. Since, the attacker can't see what the target Web site sends back to the victim in response to the forged requests, unless he exploits a cross- site scripting or other bug at the target Web site.
Similarly, the attacker can only "click" any links or submit any forms that come up after the initial forged request, if the subsequent links or forms are similarly predictable. (Multiple "clicks" can be simulated by including multiple images on a page, or by using JavaScript to introduce a delay between clicks). from cross site request forgeries (CSRF) by applying the following countermeasures available: Requiring authentication in GET and POST parameters, not only cookies. Checking the HTTP Referer header. Ensuring there's no crossdomain.xml file granting unintended access to Flash movies. Limiting the lifetime of authentication cookies. Requiring a secret, user-specific token in all form submissions prevents CSRF; the attacker's site can't put the right token in its submissions. Individual Web users can do relatively little to prevent cross-site request forgery. Logging out of sites and avoiding their "remember me" features can mitigate CSRF risk; not displaying external images or not clicking links in "spam" or unreliable e-mails may also help.
NEW QUESTION 19
Which of the following commands is most useful for viewing large files?
- A. cat
- B. less
- C. touch
- D. cp
Answer: B
Explanation:
The less command is most useful for viewing large files. The less command displays the output of a file one page at a time. Viewing large files through cat may take more time to scroll pages, so it is better to use the less command to see the content of large files. Answer A is incorrect. The cat command is also used to view the content of a file, but it is most useful for viewing short files. Answer D is incorrect. The cp command is used to copy files and directories from one location to another. Answer C is incorrect. The touch command is not used to view the content of a file. It is used to create empty files or to update file timestamps.
NEW QUESTION 20
......
Thanks for reading the newest GSNA exam dumps! We recommend you to try the PREMIUM Allfreedumps.com GSNA dumps in VCE and PDF here: https://www.allfreedumps.com/GSNA-dumps.html (368 Q&As Dumps)
