PT0-002 Exam
All About Realistic PT0-002 Samples

we provide Best Quality CompTIA PT0-002 free draindumps which are the best for clearing PT0-002 test, and to get certified by CompTIA CompTIA PenTest+ Certification Exam. The PT0-002 Questions & Answers covers all the knowledge points of the real PT0-002 exam. Crack your CompTIA PT0-002 Exam with latest dumps, guaranteed!
Online PT0-002 free questions and answers of New Version:
NEW QUESTION 1
A penetration tester performs the following command: curl –I –http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?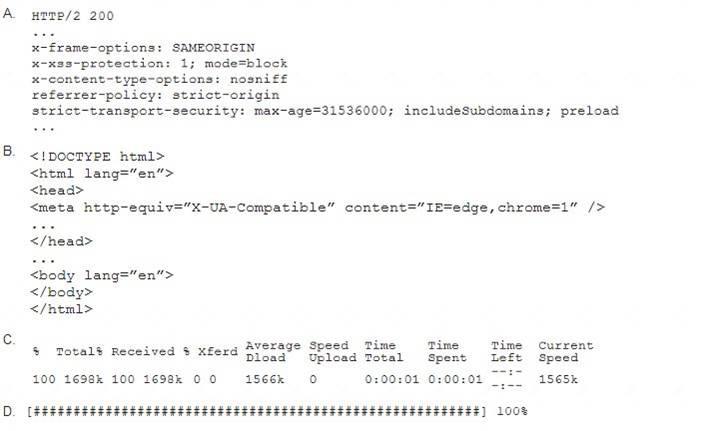
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: A
NEW QUESTION 2
A penetration tester who is conducting a web-application test discovers a clickjacking vulnerability associated with a login page to financial data. Which of the following should the tester do with this information to make this a successful exploit?
- A. Perform XSS.
- B. Conduct a watering-hole attack.
- C. Use BeEF.
- D. Use browser autopwn.
Answer: A
NEW QUESTION 3
A penetration tester gains access to a system and establishes persistence, and then runs the following commands:
cat /dev/null > temp
touch –r .bash_history temp mv temp .bash_history
Which of the following actions is the tester MOST likely performing?
- A. Redirecting Bash history to /dev/null
- B. Making a copy of the user's Bash history for further enumeration
- C. Covering tracks by clearing the Bash history
- D. Making decoy files on the system to confuse incident responders
Answer: C
NEW QUESTION 4
A penetration tester conducted a discovery scan that generated the following: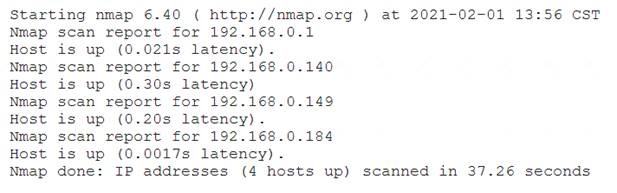
Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?
- A. nmap –oG list.txt 192.168.0.1-254 , sort
- B. nmap –sn 192.168.0.1-254 , grep “Nmap scan” | awk ‘{print S5}’
- C. nmap –-open 192.168.0.1-254, uniq
- D. nmap –o 192.168.0.1-254, cut –f 2
Answer: D
NEW QUESTION 5
A penetration tester is preparing to perform activities for a client that requires minimal disruption to company operations. Which of the following are considered passive reconnaissance tools? (Choose two.)
- A. Wireshark
- B. Nessus
- C. Retina
- D. Burp Suite
- E. Shodan
- F. Nikto
Answer: AE
NEW QUESTION 6
Which of the following should a penetration tester do NEXT after identifying that an application being tested has already been compromised with malware?
- A. Analyze the malware to see what it does.
- B. Collect the proper evidence and then remove the malware.
- C. Do a root-cause analysis to find out how the malware got in.
- D. Remove the malware immediately.
- E. Stop the assessment and inform the emergency contact.
Answer: E
NEW QUESTION 7
Running a vulnerability scanner on a hybrid network segment that includes general IT servers and industrial control systems:
- A. will reveal vulnerabilities in the Modbus protocol.
- B. may cause unintended failures in control systems.
- C. may reduce the true positive rate of findings.
- D. will create a denial-of-service condition on the IP networks.
Answer: B
NEW QUESTION 8
A Chief Information Security Officer wants a penetration tester to evaluate the security awareness level of the company’s employees.
Which of the following tools can help the tester achieve this goal?
- A. Metasploit
- B. Hydra
- C. SET
- D. WPScan
Answer: A
NEW QUESTION 9
A security professional wants to test an IoT device by sending an invalid packet to a proprietary service listening on TCP port 3011. Which of the following would allow the security professional to easily and programmatically manipulate the TCP header length and checksum using arbitrary numbers and to observe how the proprietary service responds?
- A. Nmap
- B. tcpdump
- C. Scapy
- D. hping3
Answer: C
Explanation:
https://0xbharath.github.io/art-of-packet-crafting-with-scapy/scapy/creating_packets/index.html
NEW QUESTION 10
You are a penetration tester running port scans on a server. INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options.
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.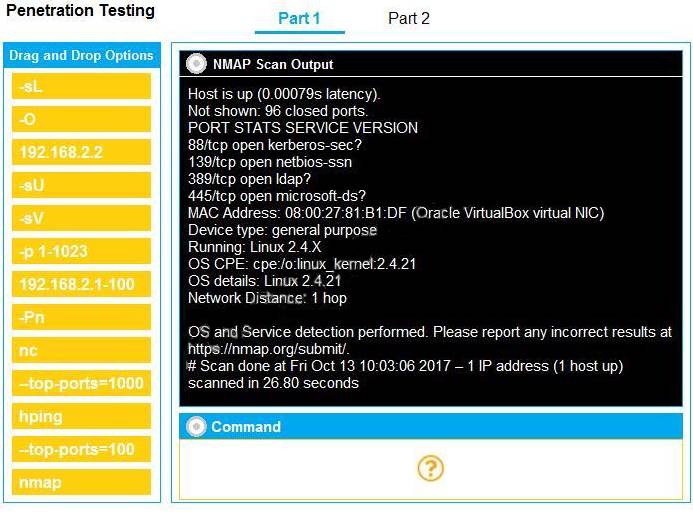
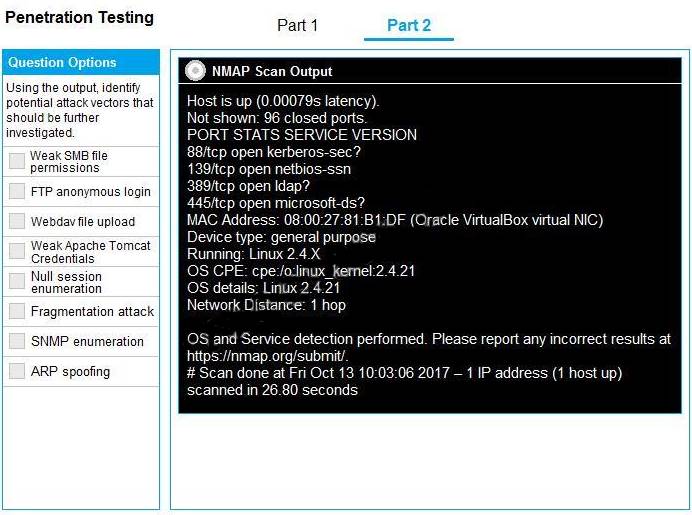
Solution:
Part 1 - nmap 192.168.2.2 -sV -O
Part 2 - Weak SMB file permissions
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 11
The following line-numbered Python code snippet is being used in reconnaissance: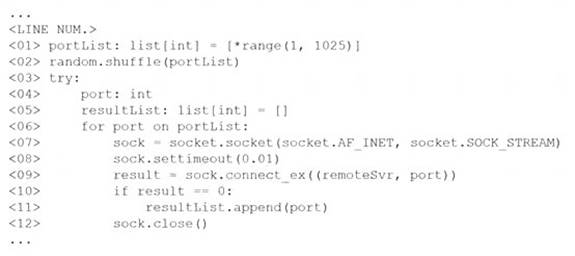
Which of the following line numbers from the script MOST likely contributed to the script triggering a “probable port scan” alert in the organization’s IDS?
- A. Line 01
- B. Line 02
- C. Line 07
- D. Line 08
Answer: A
NEW QUESTION 12
Penetration-testing activities have concluded, and the initial findings have been reviewed with the client. Which of the following best describes the NEXT step in the engagement?
- A. Acceptance by the client and sign-off on the final report
- B. Scheduling of follow-up actions and retesting
- C. Attestation of findings and delivery of the report
- D. Review of the lessons learned during the engagement
Answer: A
NEW QUESTION 13
Which of the following describes the reason why a penetration tester would run the command sdelete mimikatz. * on a Windows server that the tester compromised?
- A. To remove hash-cracking registry entries
- B. To remove the tester-created Mimikatz account
- C. To remove tools from the server
- D. To remove a reverse shell from the system
Answer: B
NEW QUESTION 14
Given the following output: User-agent:*
Disallow: /author/ Disallow: /xmlrpc.php Disallow: /wp-admin Disallow: /page/
During which of the following activities was this output MOST likely obtained?
- A. Website scraping
- B. Website cloning
- C. Domain enumeration
- D. URL enumeration
Answer: A
NEW QUESTION 15
A penetration tester is able to capture the NTLM challenge-response traffic between a client and a server. Which of the following can be done with the pcap to gain access to the server?
- A. Perform vertical privilege escalation.
- B. Replay the captured traffic to the server to recreate the session.
- C. Use John the Ripper to crack the password.
- D. Utilize a pass-the-hash attack.
Answer: D
NEW QUESTION 16
A client has requested that the penetration test scan include the following UDP services: SNMP, NetBIOS, and DNS. Which of the following Nmap commands will perform the scan?
- A. nmap –vv sUV –p 53, 123-159 10.10.1.20/24 –oA udpscan
- B. nmap –vv sUV –p 53,123,161-162 10.10.1.20/24 –oA udpscan
- C. nmap –vv sUV –p 53,137-139,161-162 10.10.1.20/24 –oA udpscan
- D. nmap –vv sUV –p 53, 122-123, 160-161 10.10.1.20/24 –oA udpscan
Answer: B
NEW QUESTION 17
Which of the following provides a matrix of common tactics and techniques used by attackers along with recommended mitigations?
- A. NIST SP 800-53
- B. OWASP Top 10
- C. MITRE ATT&CK framework
- D. PTES technical guidelines
Answer: C
NEW QUESTION 18
......
100% Valid and Newest Version PT0-002 Questions & Answers shared by Dumpscollection.com, Get Full Dumps HERE: https://www.dumpscollection.net/dumps/PT0-002/ (New 110 Q&As)
