PT0-002 Exam
How Many Questions Of PT0-002 Questions Pool

Tested of PT0-002 test preparation materials and exam topics for CompTIA certification for examinee, Real Success Guaranteed with Updated PT0-002 pdf dumps vce Materials. 100% PASS CompTIA PenTest+ Certification Exam exam Today!
Also have PT0-002 free dumps questions for you:
NEW QUESTION 1
A tester who is performing a penetration test on a website receives the following output:
Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /var/www/search.php on line 62
Which of the following commands can be used to further attack the website?
- A. <script>var adr= ‘../evil.php?test=’ + escape(document.cookie);</script>
- B. ../../../../../../../../../../etc/passwd
- C. /var/www/html/index.php;whoami
- D. 1 UNION SELECT 1, DATABASE(),3-
Answer: C
NEW QUESTION 2
A penetration tester has established an on-path attack position and must now specially craft a DNS query response to be sent back to a target host. Which of the following utilities would BEST support this objective?
- A. Socat
- B. tcpdump
- C. Scapy
- D. dig
Answer: A
NEW QUESTION 3
A penetration tester exploited a unique flaw on a recent penetration test of a bank. After the test was completed, the tester posted information about the exploit online along with the IP addresses of the exploited machines. Which of the following documents could hold the penetration tester accountable for this action?
- A. ROE
- B. SLA
- C. MSA
- D. NDA
Answer: D
NEW QUESTION 4
An Nmap scan shows open ports on web servers and databases. A penetration tester decides to run WPScan and SQLmap to identify vulnerabilities and additional information about those systems.
Which of the following is the penetration tester trying to accomplish?
- A. Uncover potential criminal activity based on the evidence gathered.
- B. Identity all the vulnerabilities in the environment.
- C. Limit invasiveness based on scope.
- D. Maintain confidentiality of the findings.
Answer: C
NEW QUESTION 5
During a penetration-testing engagement, a consultant performs reconnaissance of a client to identify potential targets for a phishing campaign. Which of the following would allow the consultant to retrieve email addresses for technical and billing contacts quickly, without triggering any of the client’s cybersecurity tools? (Choose two.)
- A. Scraping social media sites
- B. Using the WHOIS lookup tool
- C. Crawling the client’s website
- D. Phishing company employees
- E. Utilizing DNS lookup tools
- F. Conducting wardriving near the client facility
Answer: BC
NEW QUESTION 6
A penetration tester is attempting to discover live hosts on a subnet quickly. Which of the following commands will perform a ping scan?
- A. nmap -sn 10.12.1.0/24
- B. nmap -sV -A 10.12.1.0/24
- C. nmap -Pn 10.12.1.0/24
- D. nmap -sT -p- 10.12.1.0/24
Answer: A
NEW QUESTION 7
A penetration tester has gained access to a network device that has a previously unknown IP range on an interface. Further research determines this is an always-on VPN tunnel to a third-party supplier.
Which of the following is the BEST action for the penetration tester to take?
- A. Utilize the tunnel as a means of pivoting to other internal devices.
- B. Disregard the IP range, as it is out of scope.
- C. Stop the assessment and inform the emergency contact.
- D. Scan the IP range for additional systems to exploit.
Answer: D
NEW QUESTION 8
A penetration tester was able to gather MD5 hashes from a server and crack the hashes easily with rainbow tables.
Which of the following should be included as a recommendation in the remediation report?
- A. Stronger algorithmic requirements
- B. Access controls on the server
- C. Encryption on the user passwords
- D. A patch management program
Answer: C
NEW QUESTION 9
A penetration tester has identified several newly released CVEs on a VoIP call manager. The scanning tool the tester used determined the possible presence of the CVEs based off the version number of the service. Which of the following methods would BEST support validation of the possible findings?
- A. Manually check the version number of the VoIP service against the CVE release
- B. Test with proof-of-concept code from an exploit database
- C. Review SIP traffic from an on-path position to look for indicators of compromise
- D. Utilize an nmap –sV scan against the service
Answer: D
NEW QUESTION 10
Which of the following tools provides Python classes for interacting with network protocols?
- A. Responder
- B. Impacket
- C. Empire
- D. PowerSploit
Answer: B
NEW QUESTION 11
A penetration tester has been contracted to review wireless security. The tester has deployed a malicious wireless AP that mimics the configuration of the target enterprise WiFi. The penetration tester now wants to try to force nearby wireless stations to connect to the malicious AP. Which of the following steps should the tester take NEXT?
- A. Send deauthentication frames to the stations.
- B. Perform jamming on all 2.4GHz and 5GHz channels.
- C. Set the malicious AP to broadcast within dynamic frequency selection channels.
- D. Modify the malicious AP configuration to not use a pre-shared key.
Answer: A
NEW QUESTION 12
A penetration tester ran a ping –A command during an unknown environment test, and it returned a 128 TTL packet. Which of the following OSs would MOST likely return a packet of this type?
- A. Windows
- B. Apple
- C. Linux
- D. Android
Answer: A
NEW QUESTION 13
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are: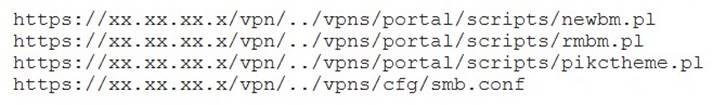
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
- A. Edit the discovered file with one line of code for remote callback
- B. Download .pl files and look for usernames and passwords
- C. Edit the smb.conf file and upload it to the server
- D. Download the smb.conf file and look at configurations
Answer: C
NEW QUESTION 14
You are a penetration tester reviewing a client’s website through a web browser. INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present. Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.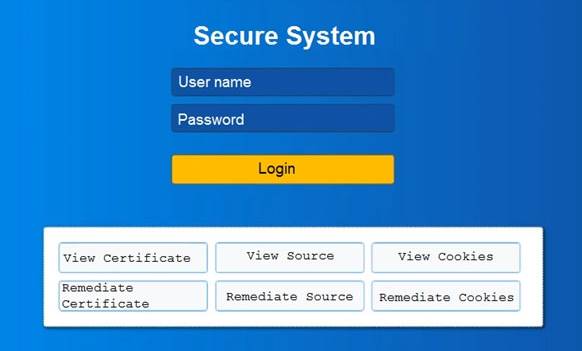
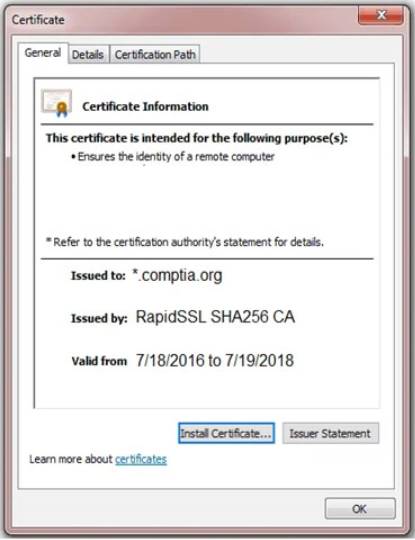
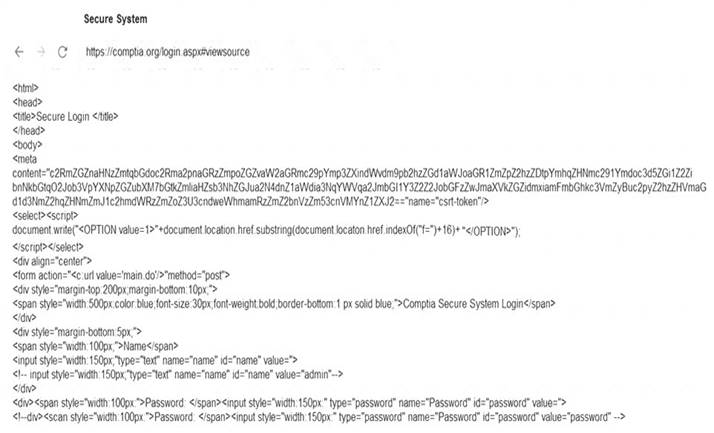
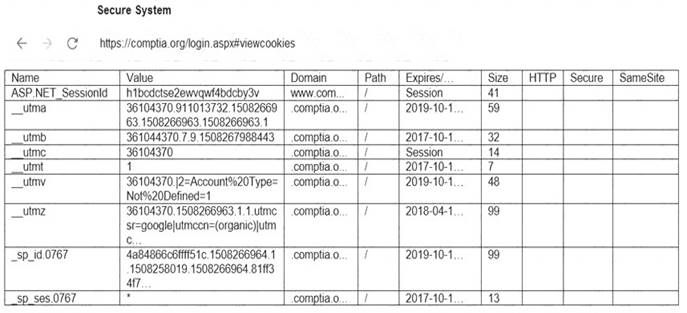
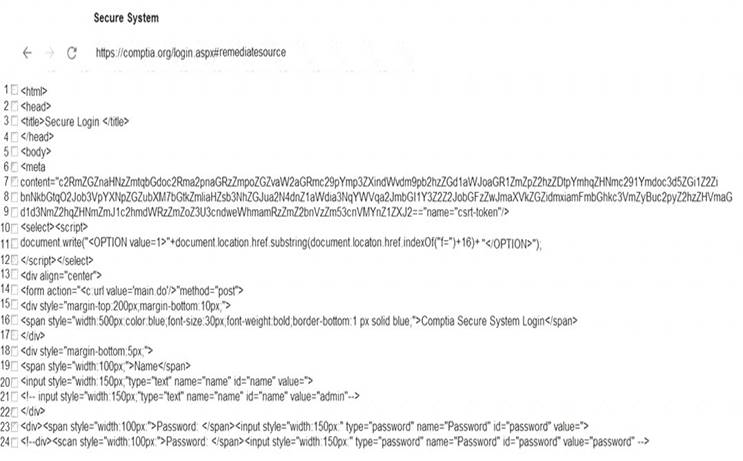
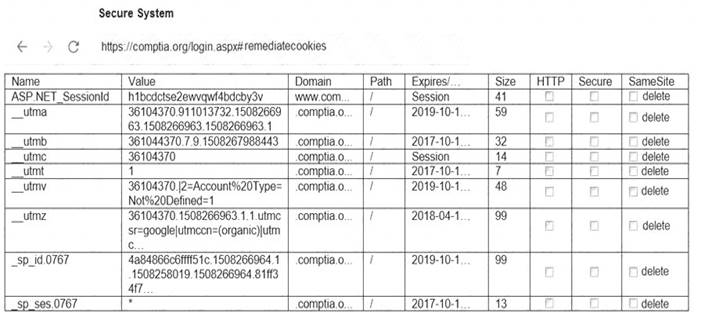
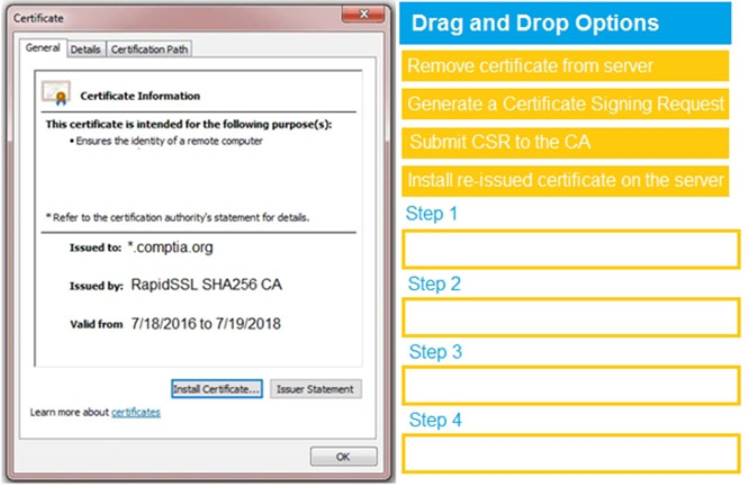
Solution:
Graphical user interface Description automatically generated
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 15
A penetration tester runs the following command on a system:
find / -user root –perm -4000 –print 2>/dev/null
Which of the following is the tester trying to accomplish?
- A. Set the SGID on all files in the / directory
- B. Find the /root directory on the system
- C. Find files with the SUID bit set
- D. Find files that were created during exploitation and move them to /dev/null
Answer: C
NEW QUESTION 16
A penetration tester recently completed a review of the security of a core network device within a corporate environment. The key findings are as follows:
• The following request was intercepted going to the network device: GET /login HTTP/1.1
Host: 10.50.100.16
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Accept-Language: en-US,en;q=0.5
Connection: keep-alive
Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk
• Network management interfaces are available on the production network.
• An Nmap scan returned the following:
Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
- A. Enforce enhanced password complexity requirements.
- B. Disable or upgrade SSH daemon.
- C. Disable HTTP/301 redirect configuration.
- D. Create an out-of-band network for management.
- E. Implement a better method for authentication.
- F. Eliminate network management and control interfaces.
Answer: CE
NEW QUESTION 17
A new security firm is onboarding its first client. The client only allowed testing over the weekend and needed the results Monday morning. However, the assessment team was not able to access the environment as expected until Monday. Which of the following should the security company have acquired BEFORE the start of the assessment?
- A. A signed statement of work
- B. The correct user accounts and associated passwords
- C. The expected time frame of the assessment
- D. The proper emergency contacts for the client
Answer: B
NEW QUESTION 18
......
P.S. 2passeasy now are offering 100% pass ensure PT0-002 dumps! All PT0-002 exam questions have been updated with correct answers: https://www.2passeasy.com/dumps/PT0-002/ (110 New Questions)
