PT0-003 Exam
The Most Recent Guide To PT0-003 Exam Price

Proper study guides for Latest CompTIA CompTIA PenTest+ Exam certified begins with CompTIA PT0-003 preparation products which designed to deliver the Simulation PT0-003 questions by making you pass the PT0-003 test at your first time. Try the free PT0-003 demo right now.
Free demo questions for CompTIA PT0-003 Exam Dumps Below:
NEW QUESTION 1
Which of the following tasks would ensure the key outputs from a penetration test are not lost as part of the cleanup and restoration activities?
- A. Preserving artifacts
- B. Reverting configuration changes
- C. Keeping chain of custody
- D. Exporting credential data
Answer: A
Explanation:
✑ Preserving Artifacts:
✑ Other Tasks:
Pentest References:
✑ Reporting: Comprehensive documentation and reporting of findings are crucial parts of penetration testing.
✑ Evidence Handling: Properly preserving and handling artifacts ensure that the integrity of the test results is maintained and can be used for future reference.
By preserving artifacts, the penetration tester ensures that all key outputs from the test are retained for analysis, reporting, and future reference.
=================
NEW QUESTION 2
DRAG DROP
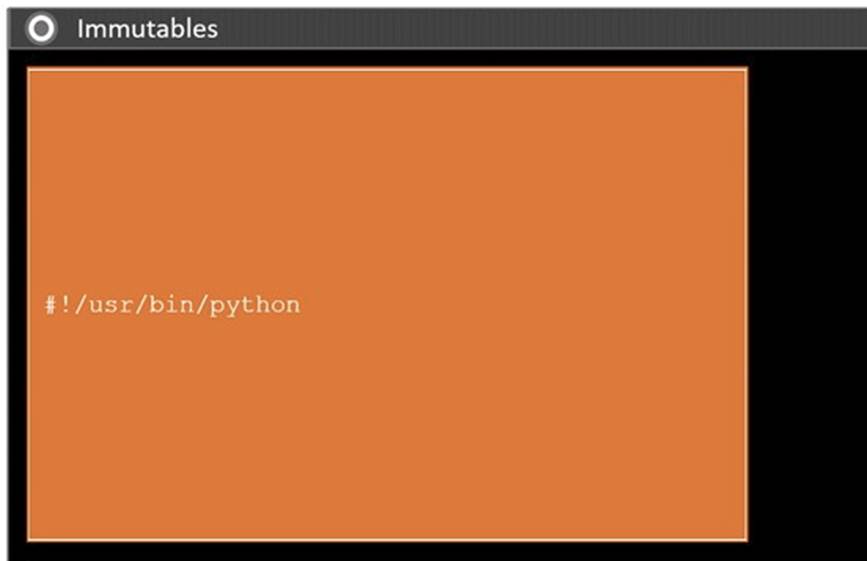
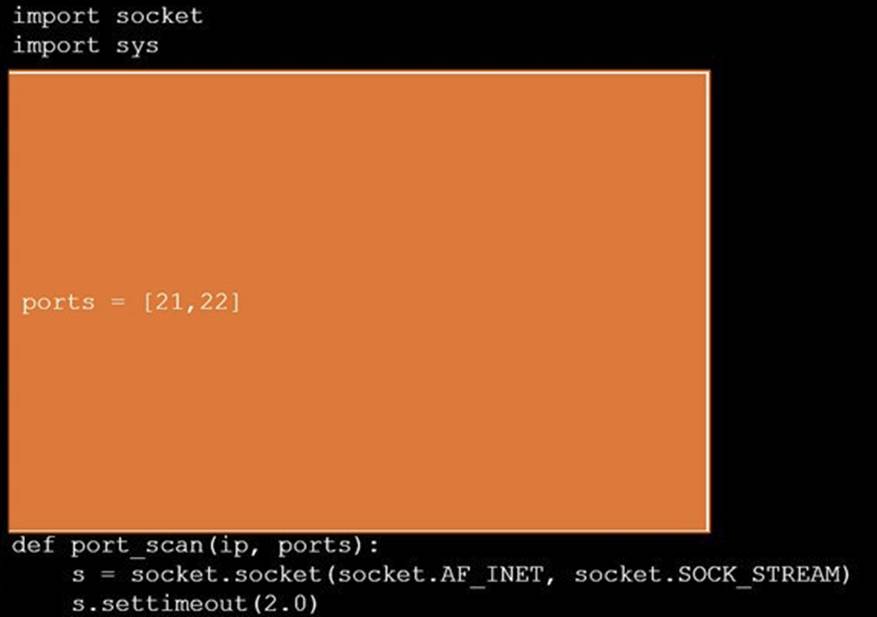
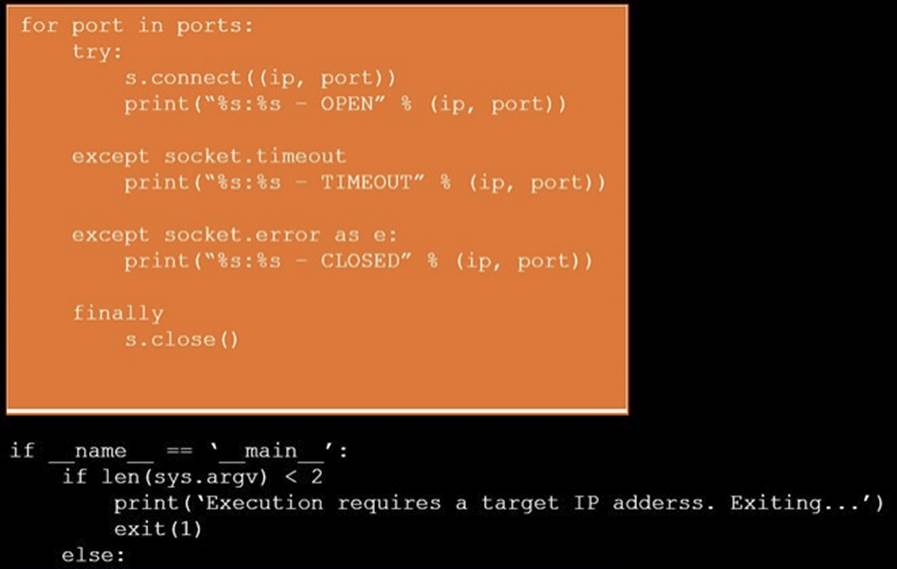
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Solution:
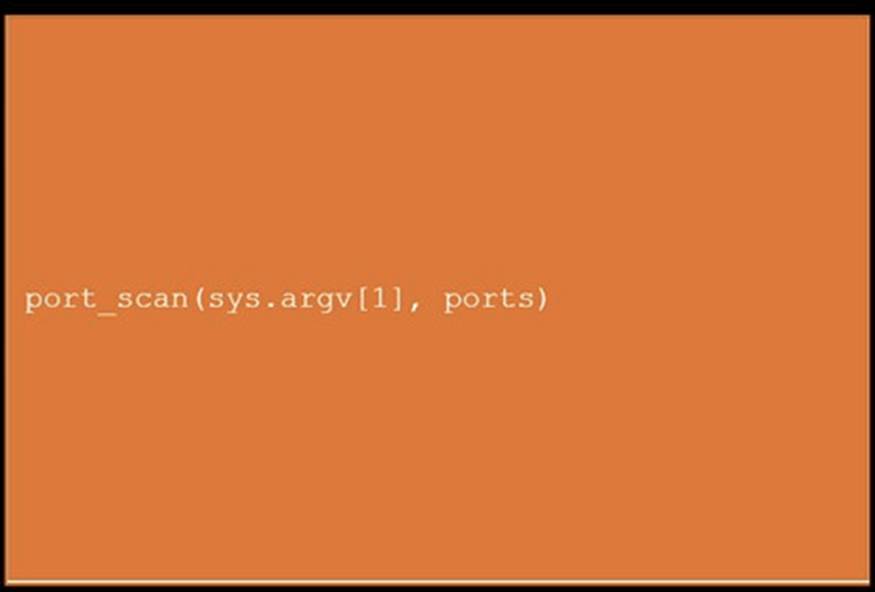
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 3
Which of the following is a term used to describe a situation in which a penetration tester bypasses physical access controls and gains access to a facility by entering at the same time as an employee?
- A. Badge cloning
- B. Shoulder surfing
- C. Tailgating
- D. Site survey
Answer: C
Explanation:
Tailgating is the term used to describe a situation where a penetration tester bypasses physical access controls and gains access to a facility by entering at the same time as an employee.
✑ Tailgating:
✑ Physical Security:
✑ Pentest References:
By understanding and using tailgating, penetration testers can evaluate the effectiveness of an organization??s physical security measures and identify potential vulnerabilities that could be exploited by malicious actors.
=================
NEW QUESTION 4
A penetration tester is evaluating a SCADA system. The tester receives local access to a workstation that is running a single application. While navigating through the application, the tester opens a terminal window and gains access to the underlying operating system. Which of the following attacks is the tester performing?
- A. Kiosk escape
- B. Arbitrary code execution
- C. Process hollowing
- D. Library injection
Answer: A
Explanation:
A kiosk escape involves breaking out of a restricted environment, such as a kiosk or a single application interface, to access the underlying operating system. Here??s why option A is correct:
✑ Kiosk Escape: This attack targets environments where user access is intentionally
limited, such as a kiosk or a dedicated application. The goal is to break out of these restrictions and gain access to the full operating system.
✑ Arbitrary Code Execution: This involves running unauthorized code on the system,
but the scenario described is more about escaping a restricted environment.
✑ Process Hollowing: This technique involves injecting code into a legitimate process, making it appear benign while executing malicious activities.
✑ Library Injection: This involves injecting malicious code into a running process by
loading a malicious library, which is not the focus in this scenario.
References from Pentest:
✑ Forge HTB: Demonstrates techniques to escape restricted environments and gain broader access to the system.
✑ Horizontall HTB: Shows methods to break out of limited access environments, aligning with the concept of kiosk escape.
Conclusion:
Option A, Kiosk escape, accurately describes the type of attack where a tester breaks out of a restricted environment to access the underlying operating system.
=================
NEW QUESTION 5
A penetration tester assesses an application allow list and has limited command-line access on the Windows system. Which of the following would give the penetration tester information that could aid in continuing the test?
- A. mmc.exe
- B. icacls.exe
- C. nltest.exe
- D. rundll.exe
Answer: C
Explanation:
When a penetration tester has limited command-line access on a Windows system, the choice of tool is critical for gathering information to aid in furthering the test. Here??s an explanation for each option:
✑ mmc.exe (Microsoft Management Console):
✑ icacls.exe:
✑ nltest.exe:
✑ rundll.exe:
Conclusion: nltest.exe is the best choice among the given options as it provides valuable information about the network, domain controllers, and trust relationships. This information is crucial for a penetration tester to plan further actions and understand the domain environment.
=================
NEW QUESTION 6
A penetration tester finished a security scan and uncovered numerous vulnerabilities on several hosts. Based on the targets' EPSS and CVSS scores, which of the following targets is the most likely to get attacked?
Host | CVSS | EPSS Target 1 | 4 | 0.6
Target 2 | 2 | 0.3
Target 3 | 1 | 0.6
Target 4 | 4.5 | 0.4
- A. Target 1: CVSS Score = 4 and EPSS Score = 0.6
- B. Target 2: CVSS Score = 2 and EPSS Score = 0.3
- C. Target 3: CVSS Score = 1 and EPSS Score = 0.6
- D. Target 4: CVSS Score = 4.5 and EPSS Score = 0.4
Answer: A
Explanation:
Based on the CVSS (Common Vulnerability Scoring System) and EPSS (Exploit Prediction Scoring System) scores, Target 1 is the most likely to get attacked.
✑ CVSS:
✑ EPSS:
✑ Analysis:
Pentest References:
✑ Vulnerability Prioritization: Using CVSS and EPSS scores to prioritize vulnerabilities based on severity and likelihood of exploitation.
✑ Risk Assessment: Understanding the balance between impact (CVSS) and exploit likelihood (EPSS) to identify the most critical targets for remediation or attack.
By focusing on Target 1, which has a balanced combination of severity and exploitability, the penetration tester can address the most likely target for attacks based on the given scores.
=================
NEW QUESTION 7
A penetration tester identifies an exposed corporate directory containing first and last names and phone numbers for employees. Which of the following attack techniques would be the most effective to pursue if the penetration tester wants to compromise user accounts?
- A. Smishing
- B. Impersonation
- C. Tailgating
- D. Whaling
Answer: A
Explanation:
When a penetration tester identifies an exposed corporate directory containing first and last names and phone numbers, the most effective attack technique to pursue would be smishing. Here's why:
✑ Understanding Smishing:
✑ Why Smishing is Effective:
✑ Alternative Attack Techniques:
=================
NEW QUESTION 8
A penetration tester needs to confirm the version number of a client's web application server. Which of the following techniques should the penetration tester use?
- A. SSL certificate inspection
- B. URL spidering
- C. Banner grabbing
- D. Directory brute forcing
Answer: C
Explanation:
Banner grabbing is a technique used to gather information about a service running on an open port, which often includes the version number of the application or server. Here??s why banner grabbing is the correct Answer
✑ Banner Grabbing: It involves connecting to a service and reading the welcome banner or response, which typically includes version information. This is a direct method to identify the version number of a web application server.
✑ SSL Certificate Inspection: While it can provide information about the server, it is not reliable for identifying specific application versions.
✑ URL Spidering: This is used for discovering URLs and resources within a web application, not for version identification.
✑ Directory Brute Forcing: This is used to discover hidden directories and files, not for identifying version information.
References from Pentest:
✑ Luke HTB: Shows how banner grabbing can be used to identify the versions of services running on a server.
✑ Writeup HTB: Demonstrates the importance of gathering version information through techniques like banner grabbing during enumeration phases.
Conclusion:
Option C, banner grabbing, is the most appropriate technique for confirming the version number of a web application server.
=================
NEW QUESTION 9
A tester completed a report for a new client. Prior to sharing the report with the client, which of the following should the tester request to complete a review?
- A. A generative AI assistant
- B. The customer's designated contact
- C. A cybersecurity industry peer
- D. A team member
Answer: B
Explanation:
Before sharing a report with a client, it is crucial to have it reviewed to ensure accuracy, clarity, and completeness. The best choice for this review is a team member. Here??s why:
✑ Internal Peer Review:
✑ Alternative Review Options:
In summary, an internal team member is the most suitable choice for a thorough and contextually accurate review before sharing the report with the client.
=================
NEW QUESTION 10
A penetration tester is performing an authorized physical assessment. During the test, the tester observes an access control vestibule and on-site security guards near the entry door in the lobby. Which of the following is the best attack plan for the tester to use in order to gain access to the facility?
- A. Clone badge information in public areas of the facility to gain access to restricted areas.
- B. Tailgate into the facility during a very busy time to gain initial access.
- C. Pick the lock on the rear entrance to gain access to the facility and try to gain access.
- D. Drop USB devices with malware outside of the facility in order to gain access to internal machines.
Answer: B
Explanation:
In an authorized physical assessment, the goal is to test physical security controls. Tailgating is a common and effective technique in such scenarios. Here??s why option B is correct:
✑ Tailgating: This involves following an authorized person into a secure area without
proper credentials. During busy times, it??s easier to blend in and gain access without being noticed. It tests the effectiveness of physical access controls and security personnel.
✑ Cloning Badge Information: This can be effective but requires proximity to
employees and specialized equipment, making it more complex and time- consuming.
✑ Picking Locks: This is a more invasive technique that carries higher risk and is less
stealthy compared to tailgating.
✑ Dropping USB Devices: This tests employee awareness and response to malicious devices but does not directly test physical access controls.
References from Pentest:
✑ Writeup HTB: Demonstrates the effectiveness of social engineering and tailgating techniques in bypassing physical security measures.
✑ Forge HTB: Highlights the use of non-invasive methods like tailgating to test physical security without causing damage or raising alarms.
Conclusion:
Option B, tailgating into the facility during a busy time, is the best attack plan to gain access to the facility in an authorized physical assessment.
=================
NEW QUESTION 11
During a penetration test, the tester gains full access to the application's source code. The application repository includes thousands of code files. Given that the assessment timeline is very short, which of the following approaches would allow the tester to identify hard- coded credentials most effectively?
- A. Run TruffleHog against a local clone of the application
- B. Scan the live web application using Nikto
- C. Perform a manual code review of the Git repository
- D. Use SCA software to scan the application source code
Answer: A
Explanation:
Given a short assessment timeline and the need to identify hard-coded credentials in a large codebase, using an automated tool designed for this specific purpose is the most effective approach. Here??s an explanation of each option:
✑ Run TruffleHog against a local clone of the application (Answer: A):
✑ Scan the live web application using Nikto (Option B):
✑ Perform a manual code review of the Git repository (Option C):
✑ Use SCA software to scan the application source code (Option D):
Conclusion: Running TruffleHog against a local clone of the application is the most effective approach for quickly identifying hard-coded credentials in a large codebase within a limited timeframe.
NEW QUESTION 12
During a penetration test, a tester attempts to pivot from one Windows 10 system to another Windows system. The penetration tester thinks a local firewall is blocking connections. Which of the following command-line utilities built into Windows is most likely to disable the firewall?
- A. certutil.exe
- B. bitsadmin.exe
- C. msconfig.exe
- D. netsh.exe
Answer: D
Explanation:
✑ Understanding netsh.exe:
✑ Disabling the Firewall:
netsh advfirewall set allprofiles state off
✑ Usage in Penetration Testing:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 13
A penetration tester executes multiple enumeration commands to find a path to escalate privileges. Given the following command:
find / -user root -perm -4000 -exec ls -ldb {} \; 2>/dev/null
Which of the following is the penetration tester attempting to enumerate?
- A. Attack path mapping
- B. API keys
- C. Passwords
- D. Permission
Answer: D
Explanation:
The command find / -user root -perm -4000 -exec ls -ldb {} \; 2>/dev/null is used to find files with the SUID bit set. SUID (Set User ID) permissions allow a file to be executed with the permissions of the file owner (root), rather than the permissions of the user running the file.
✑ Understanding the Command:
✑ Purpose:
✑ Why Enumerate Permissions:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 14
Which of the following post-exploitation activities allows a penetration tester to maintain persistent access in a compromised system?
- A. Creating registry keys
- B. Installing a bind shell
- C. Executing a process injection
- D. Setting up a reverse SSH connection
Answer: A
Explanation:
Maintaining persistent access in a compromised system is a crucial goal for a penetration
tester after achieving initial access. Here??s an explanation of each option and why creating registry keys is the preferred method:
✑ Creating registry keys (Answer: A):
✑ Installing a bind shell (Option B):
✑ Executing a process injection (Option C):
✑ Setting up a reverse SSH connection (Option D):
Conclusion: Creating registry keys is the most effective method for maintaining persistent access in a compromised system, particularly in Windows environments, due to its stealthiness and reliability.
NEW QUESTION 15
A penetration tester is attempting to discover vulnerabilities in a company's web application. Which of the following tools would most likely assist with testing the security of the web application?
- A. OpenVAS
- B. Nessus
- C. sqlmap
- D. Nikto
Answer: D
Explanation:
When testing the security of a web application, specific tools are designed to uncover vulnerabilities and issues. Here??s an overview of the tools mentioned and why Nikto is the most suitable for this task:
✑ Nikto:
✑ Comparison with Other Tools:
=================
NEW QUESTION 16
Which of the following is most important when communicating the need for vulnerability remediation to a client at the conclusion of a penetration test?
- A. Articulation of cause
- B. Articulation of impact
- C. Articulation of escalation
- D. Articulation of alignment
Answer: B
Explanation:
When concluding a penetration test, effectively communicating the need for vulnerability remediation is crucial. Here??s why the articulation of impact is the most important aspect:
✑ Articulation of Cause (Option A):
✑ Articulation of Impact (Option B):
✑ Articulation of Escalation (Option C):
✑ Articulation of Alignment (Option D):
Conclusion: Articulating the impact of vulnerabilities is the most crucial element when communicating the need for remediation. By clearly explaining the potential risks and consequences, penetration testers can effectively convey the urgency and importance of addressing the discovered issues, thus motivating clients to take prompt and appropriate action.
NEW QUESTION 17
......
100% Valid and Newest Version PT0-003 Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/PT0-003-exam-dumps.html (New 131 Q&As)
