220-902 Exam
Virtual 220-902 Exam Dumps 2021

It is more faster and easier to pass the 220 902 practice test by using comptia 220 902. Immediate access to the comptia 220 902 and find the same core area comptia 220 902 with professionally verified answers, then PASS your exam with a high score now.
Online CompTIA 220-902 free dumps demo Below:
NEW QUESTION 1
Which of the following security features is ONLY available in the Windows 7 Enterprise?
- A. Windows Firewall
- B. FTP connectivity
- C. BitLocker
- D. SSL encryption
Answer: C
NEW QUESTION 2
Which of the following security threats happens when another person enters a secured area with an authorized person?
- A. Tailgating
- B. Shoulder surfing
- C. Spoofing
- D. Phishing
Answer: A
NEW QUESTION 3
Which of the following is a security threat that disguises itself as legitimate software?
- A. Trojan
- B. Worm
- C. Virus
- D. Spyware
Answer: A
NEW QUESTION 4
A user needs access to files within a shared folder on a Linux server. The user is mapped to the folder but cannot access the files. Which of the following tools should the technician use to give the user access to these files? (Select two.)
- A. groups
- B. netshare
- C. chown
- D. chmod
- E. apt-get
- F. passwd
Answer: CD
NEW QUESTION 5
A user is experiencing a software application error. The user contacts a technician for support. Which of the following will allow the user to issue an invitation to the technician in this scenario?
- A. Remote desktop
- B. Remote assistance
- C. telnet
- D. FTP
Answer: B
NEW QUESTION 6
A PC technician has been asked to verify certain Group Policies applied on a workstation. Which of the following commands should be run on the workstation?
- A. extract
- B. tasklist
- C. gpupdate
- D. gpresult
- E. chkdsk
Answer: D
NEW QUESTION 7
A user tries to login and receives the error message “The User Profile Service failed to login. User Profile cannot be leaded.” Which of the following should be the FIRST method to troubleshoot the issue?
- A. Use Automated System Recovery
- B. Boot PC into Safe Mode
- C. Use System File Checker
- D. Perform hardware diagnostics
Answer: B
NEW QUESTION 8
A security team is auditing a company’s network logs and notices that a USB drive was previously inserted into several of the servers. Many login attempts were than successfully performed using common login information. Which of the following actions should be taken to close the vulnerability? (Select two.)
- A. Disable guest account
- B. Remove admin permissions
- C. Modify AutoRun settings
- D. Change default credentials
- E. Run OS security updates
- F. Install a software firewall
Answer: AD
NEW QUESTION 9
A PC technician is configuring IP addresses on a Windows system that has multiple NICs. Which of the following commands would show the IP addresses configured on each network interface?
- A. netconfig
- B. ifconfig
- C. ipconfig
- D. netstat
Answer: C
NEW QUESTION 10
You need to configure your mobile device to send and receive electronic messages from your company. Your mobile device must be able to truly synchronize the message state with your desktop, so that when a message is read on your desktop, it is marked as read on your mobile device. These are the proper parameters:
• Email address: tech@techies.com
• Password: P@$$w0rd
• Pop.techies.com Port: 110 Security: None
• IMAP.techies.com Port: 993 Security: SSL
• smtp.techies.com Port: 465 Security: TLS
• Company SSID: Techies
• Security: WPA2
• Passphrase: P@$$w0rd
• SSID is not broadcasted
Instructions: You are not authorized to use the Company's WLAN. The outgoing server does not require login credentials. When you have completed the simulation, please select the done button to submit your answer.
Answer:
Explanation: Since we are instructed to not use the company’s WLAN we only need to worry about the email settings and ignore the WiFi and Networks tab.
On the MAIL tab enter information as shown below: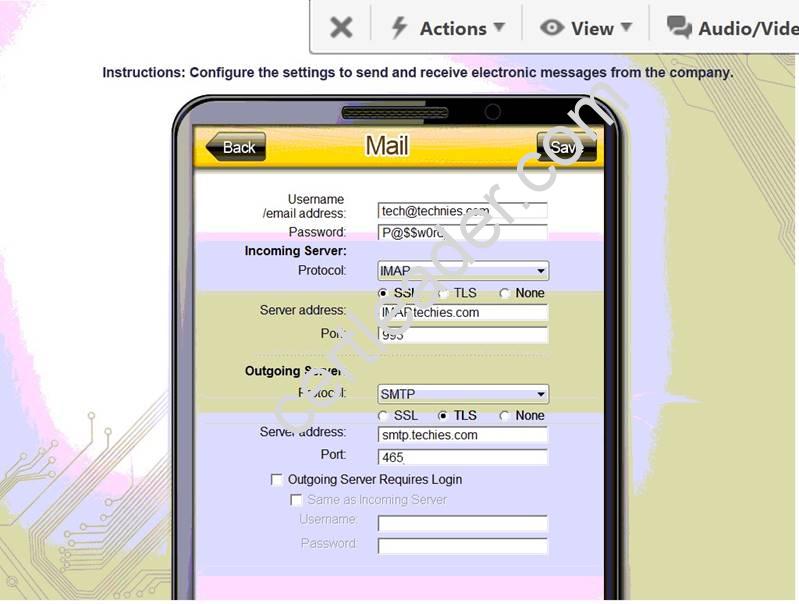
Macintosh HD:Users:danielkeller:Desktop:Screen Shot 2015-07-31 at 7.23.48 AM.png That should be all that is needed.
NEW QUESTION 11
Which of the following is the MAIN reason that corporate policies protect access to PII?
- A. To protect proprietary company data
- B. To reduce the likelihood of identity theft
- C. To maintain the integrity of knowledge management systems
- D. To limit access to those who “need to know”
Answer: B
NEW QUESTION 12
A security administrator is developing workstation hardening standards. As part of the baseline, the administrator recommends implementing controls to mitigate risks associated with dictionary attacks. Which of the following would BEST meet the requirements of the administrator?
- A. Account lockout
- B. Login time restrictions
- C. Mobile tokenization
- D. Full-disk encryption
Answer: A
NEW QUESTION 13
A technician needs to format a new drive on a workstation. The technician will need to configure read attributes to specific local files and write extended attributes to specific folders. Which of the following will allow the technician to configure these settings in a Windows environment?
- A. ext4
- B. HFS+
- C. FAT32
- D. NTFS
Answer: D
NEW QUESTION 14
A user reports browsing the Internet is slow and an icon with a picture of a person with a headset keeps asking them to “click here for help.” The user has clicked on the icon to try to resolve the slowness but all that happens is the computer redirects them to a website to purchase software. Which of the following should be performed FIRST to resolve the issue?
- A. Create a restore point
- B. Run O/S updates
- C. Train the user of malicious software
- D. Identify the type of malware
Answer: D
NEW QUESTION 15
A company wants to streamline the remote deployment of desktop and laptop computers. Which of the following should the technician implement if the primary goal is to ensure the installation can complete automatically once started?
- A. Unattended installation
- B. Remote network installation
- C. Repair installation
- D. Clean installation
Answer: C
NEW QUESTION 16
A technician must remove data from the human resources computers. The technician plans to reuse the drives in the computers. Which of the following data destruction methods should the technician perform to ensure the data is removed completely?
- A. Degaussing
- B. Standard format
- C. Overwrite
- D. Low-level format
Answer: D
NEW QUESTION 17
Users on the corporate network are reporting that accessing folders is very slow on internal network servers. Which of the following should the technician troubleshoot to resolve this problem?
- A. DHCP server
- B. Web server
- C. File server
- D. Proxy server
Answer: C
P.S. Surepassexam now are offering 100% pass ensure 220-902 dumps! All 220-902 exam questions have been updated with correct answers: https://www.surepassexam.com/220-902-exam-dumps.html (420 New Questions)
