300-206 Exam
Real 300-206 Exam Dumps 2021

We provide ccnp security senss 300 206 official cert guide which are the best for clearing 300-206 test, and to get certified by Cisco Implementing Cisco Edge Network Security Solutions. The ccnp security senss 300 206 official cert guide covers all the knowledge points of the real 300-206 exam. Crack your Cisco 300-206 Exam with latest dumps, guaranteed!
Free demo questions for Cisco 300-206 Exam Dumps Below:
NEW QUESTION 1
When you enable IP source Guard on private VLAN ports, which additional action must you take for IP Source Guard to be effective?
- A. Enable DHCP snooping on the isolated VLAN
- B. Enable BPDU guard on the isolated VLAN.
- C. Enable BPDU guard on the primary VLAN.
- D. Enable DHCP snooping on the primary VLAN.
Answer: D
NEW QUESTION 2
Refer to the exhibit.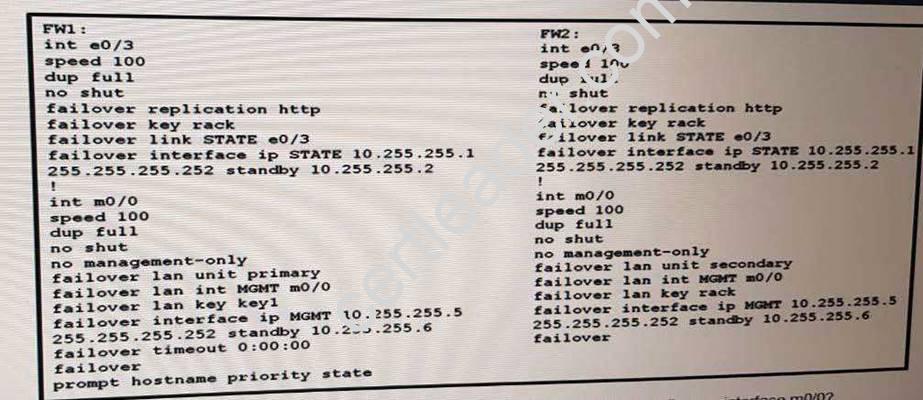
Which Information Is passed between the active and standby Cisco ASA firewalls over interface m0/0?
- A. TCP connection status
- B. network link status
- C. ARP table
- D. SIP signaling session
Answer: A
NEW QUESTION 3
If the Cisco ASA 1000V has too few licenses, what is its behavior?
- A. It drops all traffic.
- B. It drops all outside-to-inside packets.
- C. It drops all inside-to-outside packets.
- D. It passes the first outside-to-inside packet and drops all remaining packets.
Answer: D
NEW QUESTION 4
An enterprise has enforced DHCP snooping on the enterprise switches. In which two cases does the switch drop a DHCP packet? (Choose two.)
- A. A packet is received on an untrusted interface, and the source MAC address and the DHCP client hardware address match.
- B. A DHCP relay agent forwards a DHCP packet that includes a 0.0.0.0 relay-agent IP address.
- C. The switch receives a DHCPRELEASE broadcast message that has a MAC address in the DHCP snooping binding database, and the interface information in the binding database matches the interface on which the message was received.
- D. A packet is received on an untrusted interface, and the source MAC address and the DHCP client hardware address do not match.
- E. A packet from a DHCP server, such as a DHCPOFFER or DHCPLEASEQUERY packet, is received from outside the network or firewall.
Answer: DE
NEW QUESTION 5
Which threat level is the default used in the Botnet Traffic Filter?
- A. high
- B. moderate to very-high
- C. high to very-high
- D. very-high
Answer: B
NEW QUESTION 6
An engineer is configuring control-plane protocol queue thresholding. For which protocol can the
engineer set queue limits?
- A. CDP
- B. ARP
- C. IPX
- D. BGP
Answer: D
NEW QUESTION 7
Which product can manage licenses, updates, and a single signature policy for 15 separate IPS
appliances?
- A. Cisco Security Manager
- B. Cisco IPS Manager Express
- C. Cisco IPS Device Manager
- D. Cisco Adaptive Security Device Manager
Answer: A
NEW QUESTION 8
DRAG DROP
Drag and drop the steps on the left into the correct order of Cisco Security Manager rules when using inheritance on the right.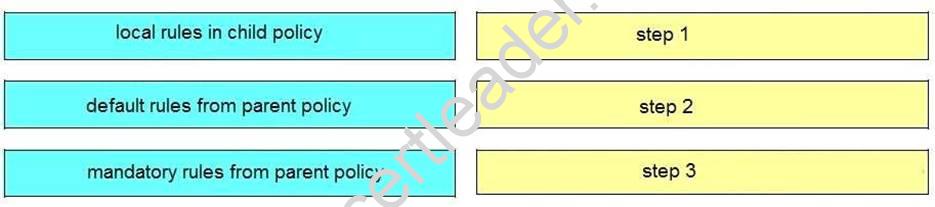
Answer:
Explanation: 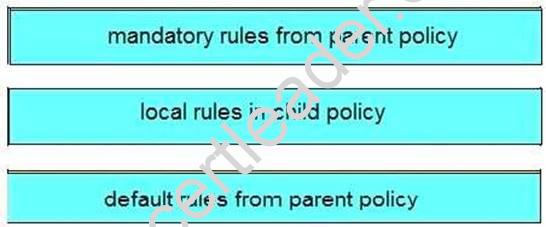
NEW QUESTION 9
A Cisco ASA is configured in multiple context mode and has two user-defined contexts-- Context_A and Context_B. From which context are device logging messages sent?
- A. Admin
- B. Context_A
- C. Context_B
- D. System
Answer: A
NEW QUESTION 10
An engineer is configuring MACsec encryption. Which two components does Cisco TrustSec NDAC
MACsec support? (Choose two.)
- A. user-facing downlink port
- B. switch-to-switch connection
- C. switch-to-host connection
- D. host-facing links
- E. switch ports connected to other switches
Answer: BE
NEW QUESTION 11
How does the DAI works? (Choose two)
- A. DAI relies on DHCP snooping.
- B. It is applied on configured untrusted interfaces
- C. IP address binding stored in trusted database
- D. User-configured ARP ACLs
Answer: AB
NEW QUESTION 12
Which statement about the Cisco Security Manager 4.4 NAT Rediscovery feature is true?
- A. It provides NAT policies to existing clients that connect from a new switch port.
- B. It can update shared policies even when the NAT server is offline.
- C. It enables NAT policy discovery as it updates shared polices.
- D. It enables NAT policy rediscovery while leaving existing shared polices unchanged.
Answer: D
NEW QUESTION 13
When configured in accordance to Cisco best practices, the ip verify source command can mitigate which two types of Layer 2 attacks? (Choose two.)
- A. rogue DHCP servers
- B. ARP attacks
- C. DHCP starvation
- D. MAC spoofing
- E. CAM attacks
- F. IP spoofing
Answer: DF
NEW QUESTION 14
What is the maximum jumbo frame size for IPS standalone appliances with 1G and 10G fixed or add-
on interfaces?
- A. 1024 bytes
- B. 1518 bytes
- C. 2156 bytes
- D. 9216 bytes
Answer: D
NEW QUESTION 15
Which security operations management best practice should be followed to enable appropriate network access for administrators?
- A. Provide full network access from dedicated network administration systems
- B. Configure the same management account on every network device
- C. Dedicate a separate physical or logical plane for management traffic
- D. Configure switches as terminal servers for secure device access
Answer: C
NEW QUESTION 16
Which command is the first that you enter to check whether or not ASDM is installed on the ASA?
- A. Show ip
- B. Show running-config asdm
- C. Show running-config boot
- D. Show version
- E. Show route
Answer: B
NEW QUESTION 17
In the default global policy, which traffic is matched for inspections by default?
- A. match any
- B. match default-inspection-traffic
- C. match access-list
- D. match port
- E. match class-default
Answer: B
NEW QUESTION 18
Which three statements about private VLANs are true? (Choose three.)
- A. Isolated ports can talk to promiscuous and community ports.
- B. Promiscuous ports can talk to isolated and community ports.
- C. Private VLANs run over VLAN Trunking Protocol in client mode.
- D. Private VLANS run over VLAN Trunking Protocol in transparent mode.
- E. Community ports can talk to each other as well as the promiscuous port.
- F. Primary, secondary, and tertiary VLANs are required for private VLAN implementation.
Answer: BDE
NEW QUESTION 19
Which statement about Dynamic ARP Inspection is true ?
- A. In a typical network, you make all ports as trusted expect for the ports connection to switches , which areuntrusted
- B. DAI associates a trust state with each switch
- C. DAI determines the validity of an ARP packet based on valid IP to MAC address binding from the DHCPsnooping database
- D. DAI intercepts all ARP requests and responses on trusted ports only
- E. DAI cannot drop invalid ARP packets
Answer: C
Recommend!! Get the Full 300-206 dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.2passeasy.com/dumps/300-206/ (New 343 Q&As Version)
