300-206 Exam
Cisco 300-206 Exam Questions and Answers 2021

We provide 300 206 senss pdf which are the best for clearing 300-206 test, and to get certified by Cisco Implementing Cisco Edge Network Security Solutions. The 300 206 senss covers all the knowledge points of the real 300-206 exam. Crack your Cisco 300-206 Exam with latest dumps, guaranteed!
Online Cisco 300-206 free dumps demo Below:
NEW QUESTION 1
Which of the following would need to be created to configure an application-layer inspection of
SMTP traffic operating on port 2525?
- A. A class-map that matches port 2525 and applying an inspect ESMTP policy-map for that class in the globalinspection policy
- B. A policy-map that matches port 2525 and applying an inspect ESMTP class-map for that policy
- C. An access-list that matches on TCP port 2525 traffic and applying it on an interface with the inspect option
- D. A class-map that matches port 2525 and applying it on an access-list using the inspect option
Answer: A
NEW QUESTION 2
What is the default behavior of NAT control on Cisco ASA Software Version 8.3?
- A. NAT control has been deprecated on Cisco ASA Software Version 8.3.
- B. It will prevent traffic from traversing from one enclave to the next without proper access configuration.
- C. It will allow traffic to traverse from one enclave to the next without proper access configuration.
- D. It will deny all traffic.
Answer: A
NEW QUESTION 3
At which layer does MACsecprovide encryption?
- A. Layer 1
- B. Layer 2
- C. Layer 3
- D. Layer 4
Answer: B
NEW QUESTION 4
Which three logging methods are supported by Cisco routers? (Choose three.)
- A. console logging
- B. TACACS+ logging
- C. terminal logging
- D. syslog logging
- E. ACL logging
- F. RADIUS logging
Answer: ACD
NEW QUESTION 5
Which command displays syslog messages on the Cisco ASA console as they occur?
- A. Console logging <level>
- B. Logging console <level>
- C. Logging trap <level>
- D. Terminal monitor
- E. Logging monitor <level>
Answer: B
NEW QUESTION 6
The Cisco ASA must support dynamic routing and terminating VPN traffic. Which three Cisco ASA
options will not support these requirements? (Choose three.)
- A. transparent mode
- B. multiple context mode
- C. active/standby failover mode
- D. active/active failover mode
- E. routed mode
- F. no NAT-control
Answer: ABD
NEW QUESTION 7
Refer to the exhibit.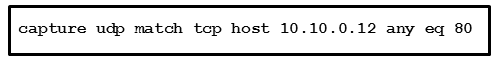
What traffic is being captured by the Cisco ASA adaptive security appliance?
- A. UDP traffic sourced from host 10.10.0.12 on port 80
- B. TCP traffic destined to host 10.10.0.12 on port 80
- C. TCP traffic sourced from host 10.10.0.12 on port 80
- D. UDP traffic destined to host 10.10.0.12 on port 80
Answer: C
NEW QUESTION 8
What are three attributes that can be applied to a user account with RBAC? (Choose three.)
- A. domain
- B. password
- C. ACE tag
- D. user roles
- E. VDC group tag
- F. expiry date
Answer: BDF
NEW QUESTION 9
According to Cisco best practices, which two interface configuration commands help prevent VLAN
hopping attacks? (Choose two.)
- A. switchport mode access
- B. switchport access vlan 2
- C. switchport mode trunk
- D. switchport access vlan 1
- E. switchport trunk native vlan 1
- F. switchport protected
Answer: AB
NEW QUESTION 10
You have installed a web server on a private network. Which type of NAT must you implement to
enable access to the web server for public Internet users?
- A. static NAT
- B. dynamic NAT
- C. network object NAT
- D. twice NAT
Answer: A
NEW QUESTION 11
Enabling what security mechanism can prevent an attacker from gaining network topology information from CDP?
- A. MACsec
- B. Flex VPN
- C. Control Plane Protection
- D. Dynamic Arp Inspection
Answer: A
NEW QUESTION 12
Which two configurations are necessary to enable password-less SSH login to an IOS router? (Choose two.)
- A. Enter a copy of the administrator's public key within the SSH key-chain
- B. Enter a copy of the administrator's private key within the SSH key-chain
- C. Generate a 512-bit RSA key to enable SSH on the router
- D. Generate an RSA key of at least 768 bits to enable SSH on the router
- E. Generate a 512-bit ECDSA key to enable SSH on the router
- F. Generate a ECDSA key of at least 768 bits to enable SSH on the router
Answer: AD
NEW QUESTION 13
You are the administrator of a Cisco ASA 9.0 firewall and have been tasked with ensuring that the
Firewall Admins Active Directory group has full access to the ASA configuration. The Firewall Operators Active Directory group should have a more limited level of access.
Which statement describes how to set these access levels?
- A. Use Cisco Directory Agent to configure the Firewall Admins group to have privilege level 15 acces
- B. Alsoconfigure the Firewall Operators group to have privilege level 6 access.
- C. Use TACACS+ for Authentication and Authorization into the Cisco ASA CLI, with ACS as the AAA server.Configure ACS CLI command authorization sets for the Firewall Operators grou
- D. Configure level 15 access to be assigned to members of the Firewall Admins group.
- E. Use RADIUS for Authentication and Authorization into the Cisco ASA CLI, with ACS as the AAA server.Configure ACS CLI command authorization sets for the Firewall Operators grou
- F. Configure level 15 access to be assigned to members of the Firewall Admins group.
- G. Active Directory Group membership cannot be used as a determining factor for accessing the Cisco ASACLI.
Answer: B
NEW QUESTION 14
A rogue device has connected to the network and has become the STP root bridge, which has caused
a network availability issue.
Which two commands can protect against this problem? (Choose two.)
- A. switch(config)#spanning-tree portfast bpduguard default
- B. switch(config)#spanning-tree portfast bpdufilter default
- C. switch(config-if)#spanning-tree portfast
- D. switch(config-if)#spanning-tree portfast disable
- E. switch(config-if)#switchport port-security violation protect
- F. switch(config-if)#spanning-tree port-priority 0
Answer: AC
NEW QUESTION 15
An engineer is applying best practices to stop STP unauthorized changes from the uses port. Which
two actions help accomplish this task? (Choose two)
- A. Enable STP Guard
- B. Configure RSTP
- C. Disable STP
- D. Enable BPDU Guard
- E. Enable Root Guard
Answer: DE
NEW QUESTION 16
An engineer has successfully captured data on an ASA (ip address 10.10.10.1) and wants to download the file to analyze offline. The filename is capin.
Which option must the engineer enter to accomplish this task?
- A. https://10.10.10.1/admin/capture/capin
- B. http://10.10.10.1/admin/capture/capin/pcap
- C. https://10.10.10.1/admin/capture/capin/pcap
- D. http://10.10.10.1/admin/capture/capin
Answer: C
NEW QUESTION 17
What are two reasons to implement Cisco IOS MPLS Bandwidth-Assured Layer 2 Services? (Choose two.)
- A. guaranteed bandwidth and peak rates as well as low cycle periods, regardless of which systems access the device
- B. increased resiliency through MPLS FRR for AToM circuits and better bandwidth utilization through MPLS TE
- C. enabled services over an IP/MPLS infrastructure, for enhanced MPLS Layer 2 functionality
- D. provided complete proactive protection against frame and device spoofing
Answer: BC
NEW QUESTION 18
Which two options can be used when configuring a packet capture from the command line within
the ASA using the capture command? (Choose two.)
- A. host
- B. snap-length
- C. type
- D. detail
- E. real-time
Answer: CE
NEW QUESTION 19
Which three statements about the software requirements for a firewall failover configuration are
true? (Choose three.)
- A. The firewalls must be in the same operating mode.
- B. The firewalls must have the same major and minor software version.
- C. The firewalls must be in the same context mode.
- D. The firewalls must have the same major software version but can have different minor versions.
- E. The firewalls can be in different context modes.
- F. The firewalls can have different Cisco AnyConnect images.
Answer: ABC
P.S. Easily pass 300-206 Exam with 343 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam 300-206 Dumps: https://www.surepassexam.com/300-206-exam-dumps.html (343 New Questions)
