300-206 Exam
Printable 300-206 Braindumps 2021

Want to know ccnp security senss 300 206 official cert guide pdf features? Want to lear more about ccnp security senss 300 206 official cert guide pdf experience? Study cisco 300 206. Gat a success with an absolute guarantee to pass Cisco 300-206 (Implementing Cisco Edge Network Security Solutions) test on your first attempt.
Free demo questions for Cisco 300-206 Exam Dumps Below:
NEW QUESTION 1
A network engineer has installed Cisco Security Manager 4.7 on a windows 2008 R2 SP1 server with 8 GB of RAM. When using the reporting feature, Cisco Security Manager frequently fails. Which option is the reason for this fault?
- A. Cisco Security Manager must be running Windows 2008 R2 Service Pack 2.
- B. Cisco Security Manager running all services must have minimum of 16 GB of RAM
- C. Cisco Security Manager is running on a domain controller
- D. Cisco Security Manager was not installed by a user with administrative rights.
Answer: B
NEW QUESTION 2
Where on a firewall does an administrator assign interfaces to contexts?
- A. in the system execution space
- B. in the admin context
- C. in a user-defined context
- D. in the console
Answer: A
NEW QUESTION 3
What can an administrator do to simultaneously capture and trace packets in a Cisco ASA?
- A. Install a Cisco ASA virtual appliance.
- B. Use the trace option of the capture command.
- C. Use the trace option of the packet-tracer command.
- D. Install a switch with a code that supports capturing, and configure a trunk to the Cisco ASA.
Answer: B
NEW QUESTION 4
A firewall administrator must write a short script for network operations that will login to all cisco ASA firewalls and check that the current running version is compliant with company policy. The administrator must first configure a restricted local username on each of the Cisco ASA firewalls so that the current running version can be validated. Which configuration command provides the least access in order to perform this function?
- A. username version user password cisco
- B. username version user password cisco privilege 0
- C. username version user password cisco privilege 2
- D. username version user password cisco privilege 15
Answer: B
Explanation:
When typing the following command, we get the following result.
ciscoasa# show run all privilege | in version
privilege show level 0 mode exec command version
Based on that we can use the show version command with privilege 0
http://www.cisco.com/c/en/us/td/docs/security/asa/asa82/command/reference/cmd_ref/p.html#wp1921158
NEW QUESTION 5
Cisco Security Manager can manage which three products? (Choose three.)
- A. Cisco IOS
- B. Cisco ASA
- C. Cisco IPS
- D. Cisco WLC
- E. Cisco Web Security Appliance
- F. Cisco Email Security Appliance
- G. Cisco ASA CX
- H. Cisco CRS
Answer: ABC
NEW QUESTION 6
To which interface on a Cisco ASA 1000V firewall should a security profile be applied when a VM sits
behind it?
- A. outside
- B. inside
- C. management
- D. DMZ
Answer: B
NEW QUESTION 7
An engineer is applying best practices to stop vlan hopping attacks? (Choose Two)
- A. disable DTP on user facing ports
- B. configure DHCP snooping on all switches
- C. use the vlan dot 1Q tag native command
- D. disable cisco discovary protocol on all switches
- E. configure IP on source Guard on all switches
Answer: AC
NEW QUESTION 8
Which three options are default settings for NTP parameters on a Cisco ASA? (Choose three.)
- A. NTP authentication is enabled.
- B. NTP authentication is disabled.
- C. NTP logging is enabled.
- D. NTP logging is disabled.
- E. NTP traffic is not restricted.
- F. NTP traffic is restricted.
Answer: BDE
NEW QUESTION 9
When creating a cluster of Cisco ASA firewalls, which feature is configured on the cluster, instead of being applied to each Cisco ASA unit?
- A. OSPF routing
- B. URL filtering
- C. HTTPS inspection
- D. resource management
Answer: B
NEW QUESTION 10
An engineer is configuring MACsec encryption. Which two components?
- A. switch-to-switch connection
- B. user- facing downlink support
- C. switch-to-host connection
- D. switch port connected to other switches
- E. host-facing links
Answer: BC
NEW QUESTION 11
Which two types of addresses can be blocked by configuring botnet traffic filtering on an ASA? (Choose two.)
- A. spyware
- B. instant messaging
- C. P2P
- D. games
- E. ads
Answer: AE
Explanation:
Reference:
https://www.cisco.com/c/en/us/td/docs/security/asa/special/botnet/guide/asa-botnet.html
NEW QUESTION 12
Which three options correctly identify the Cisco ASA1000V Cloud Firewall? (Choose three.)
- A. operates at Layer 2
- B. operates at Layer 3
- C. secures tenant edge traffic
- D. secures intraswitch traffic
- E. secures data center edge traffic
- F. replaces Cisco VSG
- G. complements Cisco VSG
- H. requires Cisco VSG
Answer: BCG
NEW QUESTION 13
What is the maximum number of servers configurable in a Cisco Prime Infrastructure high availability
implementation?
- A. 2 servers
- B. 4 servers
- C. 8 servers
- D. 16 servers
Answer: A
NEW QUESTION 14
Which addresses are considered "ambiguous addresses" and are put on the greylist by the Cisco ASA botnet traffic filter feature?
- A. addresses that are unknown
- B. addresses that are on the greylist identified by the dynamic database
- C. addresses that are blacklisted by the dynamic database but also are identified by the static whitelist
- D. addresses that are associated with multiple domain names, but not all of these domain names are on the blacklist
Answer: D
NEW QUESTION 15
Control plane thresholding limit for which protocols?
- A. ICMP
- B. BGP
- C. ARP
Answer: B
Explanation: The queue-thresholding feature policy supports the following TCP/UDP-based protocols:
Bgp,dns,ftp,http,igmp,snmp,ssh,syslog,telnet,Tftp,host-protocols
NEW QUESTION 16
Which action is considered a best practice for the Cisco ASA firewall?
- A. Use threat detection to determine attacks
- B. Disable the enable password
- C. Disable console logging
- D. Enable ICMP permit to monitor the Cisco ASA interfaces
- E. Enable logging debug-trace to send debugs to the syslog server
Answer: C
NEW QUESTION 17
Which statement describes what the arp outside 1.1.1.1 0192.7gid.0020 command accomplishes?
- A. enable ARP inspection for host 1.1.1.1
- B. configures proxy ARP for host 1.1.1.1
- C. assigns virtual MAC address for host 1.1.1.1
- D. creates static ARP entry for host 1.1.1.1 .
Answer: D
Explanation: That command adds a static ARP entry to allow ARP responses from the host at 1.1.1.1 with the MAC address 0009.7cbe.2100 on the outside interface http://www.cisco.com/c/en/us/td/docs/security/asa/asa82/configuration/guide/config/fwmode.html#wp1224694
NEW QUESTION 18
DRAG DROP
An engineer must create an SSHv2 configuration for a remote user with a key size of 2048 on the inside network of 192.168.0.0/19 with a fully qualified domain name. Drag and drop the Cisco ASA commands on the left onto the matching function on the right.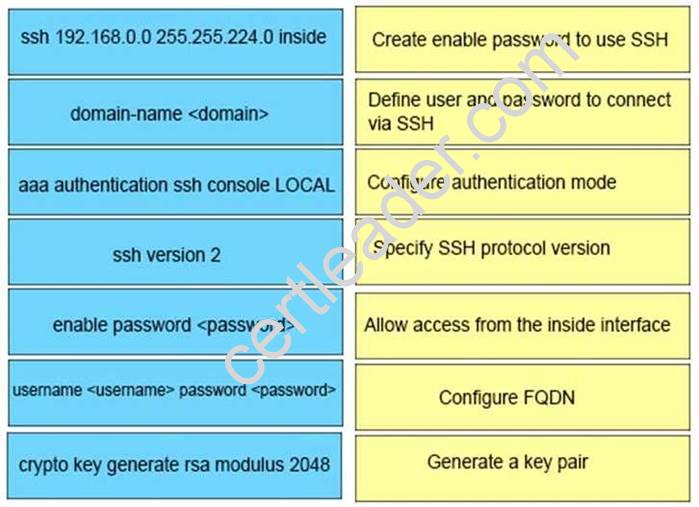
Answer:
Explanation: 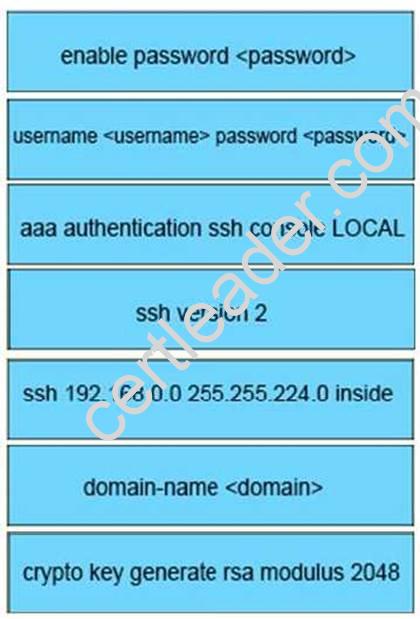
NEW QUESTION 19
What is the lowest combination of ASA model and license providing 1 Gigabit Ethernet interfaces?
- A. ASA 5505 with failover license option
- B. ASA 5510 Security+ license option
- C. ASA 5520 with any license option
- D. ASA 5540 with AnyConnect Essentials License option
Answer: B
Recommend!! Get the Full 300-206 dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.2passeasy.com/dumps/300-206/ (New 343 Q&As Version)
