156-215.80 Exam
Renovate 156-215.80 Testing Bible 2021

Exambible offers free demo for 156-215.80 exam. "Check Point Certified Security Administrator", also known as 156-215.80 exam, is a Check-Point Certification. This set of posts, Passing the Check-Point 156-215.80 exam, will help you answer those questions. The 156-215.80 Questions & Answers covers all the knowledge points of the real exam. 100% real Check-Point 156-215.80 exams and revised by experts!
Check 156-215.80 free dumps before getting the full version:
NEW QUESTION 1
What is true about the IPS-Blade?
- A. in R80, IPS is managed by the Threat Prevention Policy
- B. in R80, in the IPS Layer, the only three possible actions are Basic, Optimized and Strict
- C. in R80, IPS Exceptions cannot be attached to “all rules”
- D. in R80, the GeoPolicy Exceptions and the Threat Prevention Exceptions are the same
Answer: A
NEW QUESTION 2
What needs to be configured if the NAT property ‘Translate destination on client side’ is not enabled in Global properties?
- A. A host route to route to the destination IP
- B. Use the file local.arp to add the ARP entries for NAT to work
- C. Nothing, the Gateway takes care of all details necessary
- D. Enabling ‘Allow bi-directional NAT’ for NAT to work correctly
Answer: C
NEW QUESTION 3
Fill in the blank: Service blades must be attached to a _____ .
- A. Security Gateway
- B. Management container
- C. Management server
- D. Security Gateway container
Answer: A
NEW QUESTION 4
Which of the following licenses are considered temporary?
- A. Perpetual and Trial
- B. Plug-and-play and Evaluation
- C. Subscription and Perpetual
- D. Evaluation and Subscription
Answer: B
Explanation:
Should be Trial or Evaluation, even Plug-and-play (all are synonyms ). Answer B is the best choice.
NEW QUESTION 5
Which utility shows the security gateway general system information statistics like operating system information and resource usage, and individual software blade statistics of VPN, Identity Awareness and DLP?
- A. cpconfig
- B. fw ctl pstat
- C. cpview
- D. fw ctl multik stat
Answer: C
Explanation:
CPView Utility is a text based built-in utility that can be run ('cpview' command) on Security Gateway / Security Management Server / Multi-Domain Security Management Server. CPView Utility shows statistical data that contain both general system information (CPU, Memory, Disk space) and information for different Software Blades (only on Security Gateway). The data is continuously updated in easy to access views.
NEW QUESTION 6
What is the best sync method in the ClusterXL deployment?
- A. Use 1 cluster + 1st sync
- B. Use 1 dedicated sync interface
- C. Use 3 clusters + 1st sync + 2nd sync + 3rd sync
- D. Use 2 clusters + 1st sync + 2nd sync
Answer: B
NEW QUESTION 7
Which set of objects have an Authentication tab?
- A. Templates, Users
- B. Users, Networks
- C. Users, User Group
- D. Networks, Hosts
Answer: A
NEW QUESTION 8
How Capsule Connect and Capsule Workspace differ?
- A. Capsule Connect provides a Layer3 VP
- B. Capsule Workspace provides a Desktop with usable applications
- C. Capsule Workspace can provide access to any application
- D. Capsule Connect provides Business data isolation
- E. Capsule Connect does not require an installed application at client
Answer: A
NEW QUESTION 9
When using GAiA, it might be necessary to temporarily change the MAC address of the interface eth 0 to 00:0C:29:12:34:56. After restarting the network the old MAC address should be active. How do you configure this change?
- A. As expert user, issue these commands:# IP link set eth0 down# IP link set eth0 addr 00:0C:29:12:34:56# IP link set eth0 up
- B. Edit the file /etc/sysconfig/netconf.C and put the new MAC address in the field(conf:(conns:(conn:hwaddr (“00:0C:29:12:34:56”)
- C. As expert user, issue the command:# IP link set eth0 addr 00:0C:29:12:34:56
- D. Open the WebUI, select Network > Connections > eth0. Place the new MAC address in the field Physical Address, and press Apply to save the settings.
Answer: C
NEW QUESTION 10
You want to store the GAiA configuration in a file for later reference. What command should you use?
- A. write mem <filename>
- B. show config -f <filename>
- C. save config -o <filename>
- D. save configuration <filename>
Answer: D
NEW QUESTION 11
What happens if the identity of a user is known?
- A. If the user credentials do not match an Access Role, the system displays the Captive Portal.
- B. If the user credentials do not match an Access Role, the system displays a sandbox.
- C. If the user credentials do not match an Access Role, the traffic is automatically dropped.
- D. If the user credentials match an Access Role, the rule is applied and traffic is accepted or dropped based on the defined action.
Answer: D
NEW QUESTION 12
Examine the following Rule Base.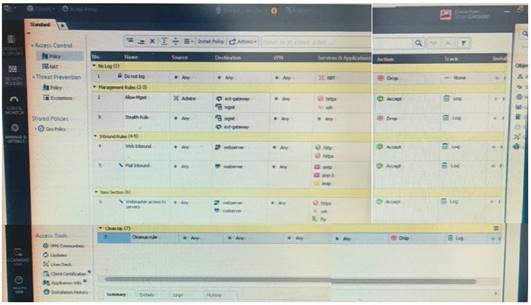
What can we infer about the recent changes made to the Rule Base?
- A. Rule 7 was created by the 'admin' administrator in the current session
- B. 8 changes have been made by administrators since the last policy installation
- C. The rules 1, 5 and 6 cannot be edited by the 'admin' administrator
- D. Rule 1 and object webserver are locked by another administrator
Answer: D
Explanation:
On top of the print screen there is a number "8" which consists for the number of changes made and not saved. Session Management Toolbar (top of SmartConsole)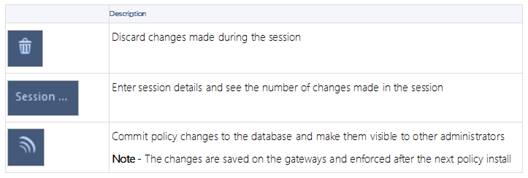
NEW QUESTION 13
Traffic from source 192.168.1.1 is going to www.google.com. The Application Control Blade on the gateway is inspecting the traffic. Assuming acceleration is enable which path is handling the traffic?
- A. Slow Path
- B. Medium Path
- C. Fast Path
- D. Accelerated Path
Answer: A
NEW QUESTION 14
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ____ .
- A. User Directory
- B. Captive Portal and Transparent Kerberos Authentication
- C. Captive Portal
- D. UserCheck
Answer: B
Explanation:
To enable Identity Awareness:
Log in to SmartDashboard.
From the Network Objects tree, expand the Check Point branch.
Double-click the Security Gateway on which to enable Identity Awareness.
In the Software Blades section, select Identity Awareness on the Network Security tab.
The Identity Awareness
Configuration wizard opens.
Select one or more options. These options set the methods for acquiring identities of managed and unmanaged assets.
AD Query - Lets the Security Gateway seamlessly identify Active Directory users and computers
Browser-Based Authentication - Sends users to a Web page to acquire identities from unidentified users. If Transparent Kerberos Authentication is configured, AD users may be identified transparently.
NEW QUESTION 15
What is the purpose of Captive Portal?
- A. It provides remote access to SmartConsole
- B. It manages user permission in SmartConsole
- C. It authenticates users, allowing them access to the Internet and corporate resources
- D. It authenticates users, allowing them access to the Gaia OS
Answer: C
Explanation:
Captive Portal – a simple method that authenticates users through a web interface before granting them access to Intranet resources. When users try to access a protected resource, they get a web page that
must be filled out to continue.
Reference : https://www.checkpoint.com/products/identity-awareness-software-blade/
NEW QUESTION 16
During the Check Point Stateful Inspection Process, for packets that do not pass Firewall Kernel Inspection and are rejected by the rule definition, packets are:
- A. Dropped without sending a negative acknowledgment
- B. Dropped without logs and without sending a negative acknowledgment
- C. Dropped with negative acknowledgment
- D. Dropped with logs and without sending a negative acknowledgment
Answer: D
NEW QUESTION 17
Which one of the following is the preferred licensing model? Select the Best answer.
- A. Local licensing because it ties the package license to the IP-address of the gateway and has no dependency of the Security Management Server.
- B. Central licensing because it ties the package license to the IP-address of the Security Management Server and has no dependency of the gateway.
- C. Local licensing because it ties the package license to the MAC-address of the gateway management interface and has no Security Management Server dependency.
- D. Central licensing because it ties the package license to the MAC-address of the Security Management Server Mgmt-interface and has no dependency of the gateway.
Answer: B
Explanation:
Central License
A Central License is a license attached to the Security Management server IP address, rather than the gatewa IP address. The benefits of a Central License are:
Only one IP address is needed for all licenses.
A license can be taken from one gateway and given to another.
The new license remains valid when changing the gateway IP address. There is no need to create and install a new license.
NEW QUESTION 18
Fill in the blank: The R80 utility fw monitor is used to troubleshoot _______
- A. User data base corruption
- B. LDAP conflicts
- C. Traffic issues
- D. Phase two key negotiation
Answer: C
Explanation:
Check Point's FW Monitor is a powerful built-in tool for capturing network traffic at the packet level. The Monitor utility captures network packets at multiple capture points along the FireWall inspection chains. These captured packets can be inspected later using the WireShark
NEW QUESTION 19
Which of these components does NOT require a Security Gateway R77 license?
- A. Security Management Server
- B. Check Point Gateway
- C. SmartConsole
- D. SmartUpdate upgrading/patching
Answer: C
NEW QUESTION 20
How do you configure the Security Policy to provide uses access to the Captive Portal through an external (Internet) interface?
- A. Change the gateway settings to allow Captive Portal access via an external interface.
- B. No action is necessar
- C. This access is available by default.
- D. Change the Identity Awareness settings under Global Properties to allow Captive Policy access on all interfaces.
- E. Change the Identity Awareness settings under Global Properties to allow Captive Policy access for an external interface.
Answer: A
NEW QUESTION 21
Fill the blank. IT is Best Practice to have a _____ rule at the end of each policy layer.
- A. Explicit Drop
- B. Implied Drop
- C. Explicit Cleanup
- D. Implicit Drop
Answer: A
NEW QUESTION 22
Which of the following is NOT an integral part of VPN communication within a network?
- A. VPN key
- B. VPN community
- C. VPN trust entities
- D. VPN domain
Answer: A
Explanation:
VPN key (to not be confused with pre-shared key that is used for authentication).
VPN trust entities, such as a Check Point Internal Certificate Authority (ICA). The ICA is part of the Check Point suite used for creating SIC trusted connection between Security Gateways, authenticating administrators and third party servers. The ICA provides certificates for internal Security Gateways and remote access clients which negotiate the VPN link.
VPN Domain - A group of computers and networks connected to a VPN tunnel by one VPN gateway that handles encryption and protects the VPN Domain members.
VPN Community - A named collection of VPN domains, each protected by a VPN gateway. References: http://sc1.checkpoint.com/documents/R77/CP_R77_VPN_AdminGuide/13868.htm
NEW QUESTION 23
Fill in the blank: The IPS policy for pre-R80 gateways is installed during the _____.
- A. Firewall policy install
- B. Threat Prevention policy install
- C. Anti-bot policy install
- D. Access Control policy install
Answer: B
Explanation:
https://sc1.checkpoint.com/documents/R80/CP_R80BC_ThreatPrevention/html_frameset.htm?topic=documents
NEW QUESTION 24
While in SmartView Tracker, Brady has noticed some very odd network traffic that he thinks could be an intrusion. He decides to block the traffic for 60 minutes, but cannot remember all the steps. What is the correct order of steps needed to set up the block?
1) Select Active Mode tab in SmartView Tracker.
2) Select Tools > Block Intruder.
3) Select Log Viewing tab in SmartView Tracker.
4) Set Blocking Timeout value to 60 minutes.
5) Highlight connection that should be blocked.
- A. 1, 2, 5, 4
- B. 3, 2, 5, 4
- C. 1, 5, 2, 4
- D. 3, 5, 2, 4
Answer: C
NEW QUESTION 25
Which component functions as the Internal Certificate Authority for R77?
- A. Security Gateway
- B. Management Server
- C. Policy Server
- D. SmartLSM
Answer: B
NEW QUESTION 26
Where can administrator edit a list of trusted SmartConsole clients in R80?
- A. cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server.
- B. Only using SmartConsole: Manage and Settings > Permissions and Administrators > Advanced > Trusted Clients.
- C. In cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server, in SmartConsole: Manage and Settings>Permissions and Administrators>Advanced>Trusted Clients.
- D. WebUI client logged to Security Management Server, SmartDashboard: Manage and Settings>Permissions and Administrators>Advanced>Trusted Clients, via cpconfig on a Security Gateway.
Answer: C
NEW QUESTION 27
What does ExternalZone represent in the presented rule?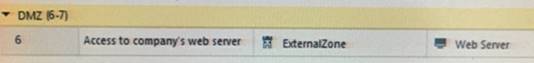
- A. The Internet.
- B. Interfaces that administrator has defined to be part of External Security Zone.
- C. External interfaces on all security gateways.
- D. External interfaces of specific gateways.
Answer: B
Explanation:
Configuring Interfaces
Configure the Security Gateway 80 interfaces in the Interfaces tab in the Security Gateway window. To configure the interfaces:
From the Devices window, double-click the Security Gateway 80.
The Security Gateway
window opens.
Select the Interfaces tab.
Select Use the following settings. The interface settings open.
Select the interface and click Edit.
The Edit window opens.
From the IP Assignment section, configure the IP address of the interface:
Select Static IP.
Enter the IP address and subnet mask for the interface.
In Security Zone, select Wireless, DMS, External, or Internal. Security zone is a type of zone, created by a bridge to easily create segments, while maintaining IP addresses and router configurations. Security zones let you choose if to enable or not the firewall between segments.
References:
NEW QUESTION 28
ABC Corp., and have recently returned from a training course on Check Point's new advanced R80 management platform. You are presenting an in-house R80 Management to the other administrators in ABC Corp.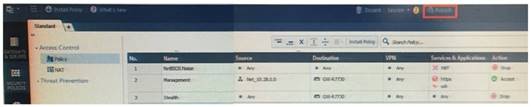
How will you describe the new “Publish” button in R80 Management Console?
- A. The Publish button takes any changes an administrator has made in their management session, publishes a copy to the Check Point of R80, and then saves it to the R80 database.
- B. The Publish button takes any changes an administrator has made in their management session and publishes a copy to the Check Point Cloud of R80 and but does not save it to the R80
- C. The Publish button makes any changes an administrator has made in their management session visible to all other administrator sessions and saves it to the Database.
- D. The Publish button makes any changes an administrator has made in their management session visible to the new Unified Policy session and saves it to the Database.
Answer: C
Explanation:
To make your changes available to other administrators, and to save the database before installing a policy, you must publish the session. When you publish a session, a new database version is created.
NEW QUESTION 29
VPN gateways must authenticate to each other prior to exchanging information. What are the two types of credentials used for authentication?
- A. 3DES and MD5
- B. Certificates and IPsec
- C. Certificates and pre-shared secret
- D. IPsec and VPN Domains
Answer: C
NEW QUESTION 30
You can see the following graphic: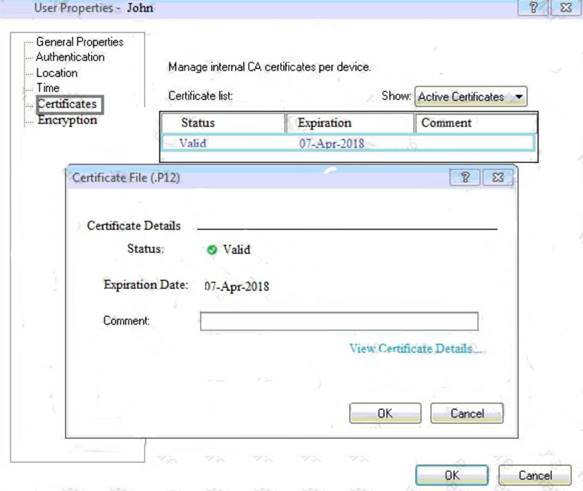
What is presented on it?
- A. Properties of personal .p12 certificate file issued for user John.
- B. Shared secret properties of John’s password.
- C. VPN certificate properties of the John’s gateway.
- D. Expired .p12 certificate properties for user John.
Answer: A
NEW QUESTION 31
......
Thanks for reading the newest 156-215.80 exam dumps! We recommend you to try the PREMIUM Dumpscollection 156-215.80 dumps in VCE and PDF here: http://www.dumpscollection.net/dumps/156-215.80/ (485 Q&As Dumps)
