156-215.80 Exam
What Pinpoint 156-215.80 Free Exam Questions Is

Cause all that matters here is passing the Check-Point 156-215.80 exam. Cause all that you need is a high score of 156-215.80 Check Point Certified Security Administrator exam. The only one thing you need to do is downloading Exambible 156-215.80 exam study guides now. We will not let you down with our money-back guarantee.
Online Check-Point 156-215.80 free dumps demo Below:
NEW QUESTION 1
To optimize Rule Base efficiency, the most hit rules should be where?
- A. Removed from the Rule Base.
- B. Towards the middle of the Rule Base.
- C. Towards the top of the Rule Base.
- D. Towards the bottom of the Rule Base.
Answer: C
Explanation:
It is logical that if lesser rules are checked for the matched rule to be found the lesser CPU cycles the device is using. Checkpoint match a session from the first rule on top till the last on the bottom.
NEW QUESTION 2
You have enabled “Full Log” as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
- A. Logging has disk space issue
- B. Change logging storage options on the logging server or Security Management Server properties and install database.
- C. Data Awareness is not enabled.
- D. Identity Awareness is not enabled.
- E. Logs are arriving from Pre-R80 gateways.
Answer: A
Explanation:
The most likely reason for the logs data to stop is the low disk space on the logging device, which can be the Management Server or the Gateway Server.
NEW QUESTION 3
If there are two administrators logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available to other administrators? Choose the BEST answer.
- A. Publish or discard the session.
- B. Revert the session.
- C. Save and install the Policy.
- D. Delete older versions of database.
Answer: A
Explanation:
To make changes available to all administrators, and to unlock the objects and rules that are being edited, the administrator must publish the session.
To make your changes available to other administrators, and to save the database before installing a policy, you must publish the session. When you publish a session, a new database version is created.
When you select Install Policy, you are prompted to publish all unpublished changes. You cannot install a policy if the included changes are not published.
NEW QUESTION 4
What is NOT an advantage of Packet Filtering?
- A. Low Security and No Screening above Network Layer
- B. Application Independence
- C. High Performance
- D. Scalability
Answer: A
Explanation:
Packet Filter Advantages and Disadvantages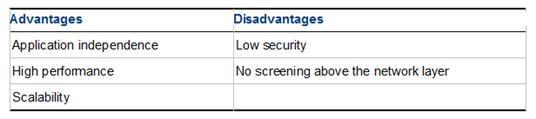
NEW QUESTION 5
SmartEvent does NOT use which of the following procedures to identity events:
- A. Matching a log against each event definition
- B. Create an event candidate
- C. Matching a log against local exclusions
- D. Matching a log against global exclusions
Answer: C
NEW QUESTION 6
Katie has been asked to do a backup on the Blue Security Gateway. Which command would accomplish this in the Gaia CLI?
- A. Blue > add local backup
- B. Expert&Blue#add local backing
- C. Blue > set backup local
- D. Blue > add backup local
Answer: D
NEW QUESTION 7
Which utility allows you to configure the DHCP service on GAIA from the command line?
- A. ifconfig
- B. dhcp_cfg
- C. sysconfig
- D. cpconfig
Answer: C
Explanation:
Sysconfig Configuration Options
NEW QUESTION 8
When launching SmartDashboard, what information is required to log into R77?
- A. User Name, Management Server IP, certificate fingerprint file
- B. User Name, Password, Management Server IP
- C. Password, Management Server IP
- D. Password, Management Server IP, LDAP Server IP
Answer: B
NEW QUESTION 9
Which of the following is NOT a SecureXL traffic flow?
- A. Medium Path
- B. Accelerated Path
- C. Fast Path
- D. Slow Path
Answer: C
Explanation:
SecureXL is an acceleration solution that maximizes performance of the Firewall and does not compromise security. When SecureXL is enabled on a Security Gateway, some CPU intensive operations are processed by virtualized software instead of the Firewall kernel. The Firewall can inspect and process connections more efficiently and accelerate throughput and connection rates. These are the SecureXL traffic flows:
Slow path - Packets and connections that are inspected by the Firewall and are not processed by SecureXL. Accelerated path - Packets and connections that are offloaded to SecureXL and are not processed by the
Firewall.
Medium path - Packets that require deeper inspection cannot use the accelerated path. It is not necessary for the Firewall to inspect these packets, they can be offloaded and do not use the slow path. For example, packets that are inspected by IPS cannot use the accelerated path and can be offloaded to the IPS PSL (Passive Streaming Library). SecureXL processes these packets more quickly than packets on the slow path.
NEW QUESTION 10
The IT Management team is interested in the new features of the Check Point R80 Management and wants to upgrade but they are concerned that the existing R77.30 Gaia Gateways cannot be managed by R80 because it is so different. As the administrator responsible for the Firewalls, how can you answer or confirm these concerns?
- A. R80 Management contains compatibility packages for managing earlier versions of Check Point Gateways prior to R80. Consult the R80 Release Notes for more information.
- B. R80 Management requires the separate installation of compatibility hotfix packages for managing the earlier versions of Check Point Gateways prior to R80. Consult the R80 Release Notes for more information.
- C. R80 Management was designed as a completely different Management system and so can only monitor Check Point Gateways prior to R80.
- D. R80 Management cannot manage earlier versions of Check Point Gateways prior to R80. Only R80 and above Gateways can be manage
- E. Consult the R80 Release Notes for more information.
Answer: A
NEW QUESTION 11
Fill in the blank: The tool ____ generates a R80 Security Gateway configuration report.
- A. infoCP
- B. infoview
- C. cpinfo
- D. fw cpinfo
Answer: C
Explanation:
CPInfo is an auto-updatable utility that collects diagnostics data on a customer's machine at the time of execution and uploads it to Check Point servers (it replaces the standalone cp_uploader utility for uploading files to Check Point servers).
The CPinfo output file allows analyzing customer setups from a remote location. Check Point support engineers can open the CPinfo file in a demo mode, while viewing actual customer Security Policies and Objects. This allows the in-depth analysis of customer's configuration and environment settings.
When contacting Check Point Support, collect the cpinfo files from the Security Management server and Security Gateways involved in your case.
NEW QUESTION 12
Which of the following are available SmartConsole clients which can be installed from the R77 Windows CD? Read all answers and select the most complete and valid list.
- A. SmartView Tracker, SmartDashboard, CPINFO, SmartUpdate, SmartView Status
- B. SmartView Tracker, SmartDashboard, SmartLSM, SmartView Monitor
- C. SmartView Tracker, CPINFO, SmartUpdate
- D. Security Policy Editor, Log Viewer, Real Time Monitor GUI
Answer: C
NEW QUESTION 13
Which NAT rules are prioritized first?
- A. Post-Automatic/Manual NAT rules
- B. Manual/Pre-Automatic NAT
- C. Automatic Hide NAT
- D. Automatic Static NAT
Answer: B
NEW QUESTION 14
Fill in the blanks: A _____ license requires an administrator to designate a gateway for attachment whereas a _____ license is automatically attached to a Security Gateway.
- A. Format; corporate
- B. Local; formal
- C. Local; central
- D. Central; local
Answer: D
NEW QUESTION 15
When logging in for the first time to a Security management Server through SmartConsole, a fingerprint is saved to the:
- A. Security Management Server’s /home/.fgpt file and is available for future SmartConsole authentications.
- B. Windows registry is available for future Security Management Server authentications.
- C. there is no memory used for saving a fingerprint anyway.
- D. SmartConsole cache is available for future Security Management Server authentications.
Answer: D
NEW QUESTION 16
Which command can you use to enable or disable multi-queue per interface?
- A. cpmq set
- B. Cpmqueue set
- C. Cpmq config
- D. Set cpmq enable
Answer: A
NEW QUESTION 17
When an encrypted packet is decrypted, where does this happen?
- A. Security policy
- B. Inbound chain
- C. Outbound chain
- D. Decryption is not supported
Answer: A
NEW QUESTION 18
What component of R80 Management is used for indexing?
- A. DBSync
- B. API Server
- C. fwm
- D. SOLR
Answer: D
NEW QUESTION 19
Choose what BEST describes the Policy Layer Traffic Inspection.
- A. If a packet does not match any of the inline layers, the matching continues to the next Layer.
- B. If a packet matches an inline layer, it will continue matching the next layer.
- C. If a packet does not match any of the inline layers, the packet will be matched against the Implicit Clean-up Rule.
- D. If a packet does not match a Network Policy Layer, the matching continues to its inline layer.
Answer: B
NEW QUESTION 20
Which of the following firewall modes DOES NOT allow for Identity Awareness to be deployed?
- A. Bridge
- B. Load Sharing
- C. High Availability
- D. Fail Open
Answer: A
NEW QUESTION 21
......
P.S. DumpSolutions.com now are offering 100% pass ensure 156-215.80 dumps! All 156-215.80 exam questions have been updated with correct answers: https://www.dumpsolutions.com/156-215.80-dumps/ (485 New Questions)
