156-215.80 Exam
The Secret Of Check-Point 156-215.80 Free Samples

Your success in Check-Point 156-215.80 is our sole target and we develop all our 156-215.80 braindumps in a way that facilitates the attainment of this target. Not only is our 156-215.80 study material the best you can find, it is also the most detailed and the most updated. 156-215.80 Practice Exams for Check-Point 156-215.80 are written to the highest standards of technical accuracy.
Also have 156-215.80 free dumps questions for you:
NEW QUESTION 1
Which of the following commands can be used to remove site-to-site IPSEC Security Associations (SA)?
- A. vpn tu
- B. vpn ipsec remove -l
- C. vpn debug ipsec
- D. fw ipsec tu
Answer: A
Explanation:
vpn tu
Description Launch the TunnelUtil tool which is used to control VPN tunnels.
Usage vpn tu vpn tunnelutil Example vpn tu Output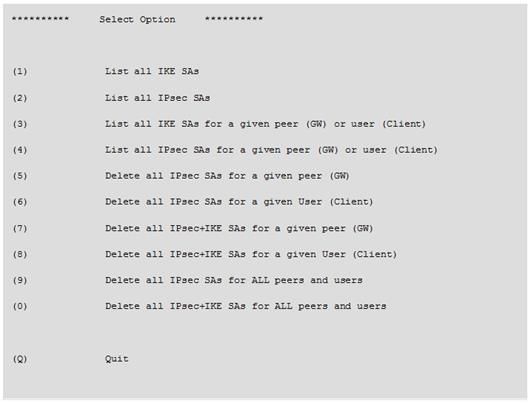
NEW QUESTION 2
Which of the following is NOT a component of a Distinguished Name?
- A. Organization Unit
- B. Country
- C. Common name
- D. User container
Answer: D
Explanation:
Distinguished Name Components
CN=common name, OU=organizational unit, O=organization, L=locality, ST=state or province, C=country name
NEW QUESTION 3
Which set of objects have an Authentication tab?
- A. Templates, Users
- B. Users, Networks
- C. Users, User Group
- D. Networks, Hosts
Answer: A
NEW QUESTION 4
The fw monitor utility is used to troubleshoot which of the following problems?
- A. Phase two key negotiation
- B. Address translation
- C. Log Consolidation Engine
- D. User data base corruption
Answer: B
NEW QUESTION 5
Choose the correct statement regarding Implicit Rules.
- A. To edit the Implicit rules you go to: Launch Button > Policy > Global Properties > Firewall.
- B. Implied rules are fixed rules that you cannot change.
- C. You can directly edit the Implicit rules by double-clicking on a specific Implicit rule.
- D. You can edit the Implicit rules but only if requested by Check Point support personnel.
Answer: A
NEW QUESTION 6
Fill in the blank: The ____ is used to obtain identification and security information about network users.
- A. User Directory
- B. User server
- C. UserCheck
- D. User index
Answer: A
NEW QUESTION 7
According to Check Point Best Practice, when adding a non-managed Check Point Gateway to a Check Point security solution what object SHOULD be added? A(n):
- A. Gateway
- B. Interoperable Device
- C. Externally managed gateway
- D. Network Node
Answer: C
NEW QUESTION 8
Which of the following is NOT an option for internal network definition of Anti-spoofing?
- A. Specific – derived from a selected object
- B. Route-based – derived from gateway routing table
- C. Network defined by the interface IP and Net Mask
- D. Not-defined
Answer: B
NEW QUESTION 9
Which pre-defined Permission Profile should be assigned to an administrator that requires full access to audit all configurations without modifying them?
- A. Auditor
- B. Read Only All
- C. Super User
- D. Full Access
Answer: B
Explanation:
To create a new permission profile:
In SmartConsole, go to Manage & Settings > Permissions and Administrators > Permission Profiles.
Click New Profile.
The New Profile window opens.
Enter a unique name for the profile.
Select a profile type:
Read/Write All - Administrators can make changes
Auditor (Read Only All) - Administrators can see information but cannot make changes
Customized - Configure custom settings
Click OK.
NEW QUESTION 10
Fill in the blank: Authentication rules are defined for ____ .
- A. User groups
- B. Users using UserCheck
- C. Individual users
- D. All users in the database
Answer: A
NEW QUESTION 11
You are conducting a security audit. While reviewing configuration files and logs, you notice logs accepting POP3 traffic, but you do not see a rule allowing POP3 traffic in the Rule Base. Which of the following is the
most likely cause?
- A. The POP3 rule is disabled.
- B. POP3 is accepted in Global Properties.
- C. The POP3 rule is hidden.
- D. POP3 is one of 3 services (POP3, IMAP, and SMTP) accepted by the default mail object in R77.
Answer: C
NEW QUESTION 12
What is the default shell of Gaia CLI?
- A. Monitor
- B. CLI.sh
- C. Read-only
- D. Bash
Answer: B
Explanation:
This chapter gives an introduction to the Gaia command line interface (CLI). The default shell of the CLI is called clish.
NEW QUESTION 13
You work as a security administrator for a large company. CSO of your company has attended a security conference where he has learnt how hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. He wants to make sure that his company has the right protections in place. Check Point has been selected for the security vendor. Which Check Point products protects BEST against malware and zero-day attacks while ensuring quick delivery of safe content to your users?
- A. IPS and Application Control
- B. IPS, anti-virus and anti-bot
- C. IPS, anti-virus and e-mail security
- D. SandBlast
Answer: D
Explanation:
SandBlast Zero-Day Protection
Hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. Zero-day exploit protection from Check Point provides a deeper level of inspection so you can prevent more malware and zero-day attacks, while ensuring quick delivery of safe content to your users.
NEW QUESTION 14
Look at the following screenshot and select the BEST answer.
- A. Clients external to the Security Gateway can download archive files from FTP_Ext server using FTP.
- B. Internal clients can upload and download any-files to FTP_Ext-server using FTP.
- C. Internal clients can upload and download archive-files to FTP_Ext server using FTP.
- D. Clients external to the Security Gateway can upload any files to the FTP_Ext-server using FTP.
Answer: A
NEW QUESTION 15
When defining QoS global properties, which option below is not valid?
- A. Weight
- B. Authenticated timeout
- C. Schedule
- D. Rate
Answer: C
NEW QUESTION 16
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ____ .
- A. User Directory
- B. Captive Portal and Transparent Kerberos Authentication
- C. Captive Portal
- D. UserCheck
Answer: B
Explanation:
To enable Identity Awareness:
Log in to SmartDashboard.
From the Network Objects tree, expand the Check Point branch.
Double-click the Security Gateway on which to enable Identity Awareness.
In the Software Blades section, select Identity Awareness on the Network Security tab.
The Identity Awareness
Configuration wizard opens.
Select one or more options. These options set the methods for acquiring identities of managed and unmanaged assets.
AD Query - Lets the Security Gateway seamlessly identify Active Directory users and computers
Browser-Based Authentication - Sends users to a Web page to acquire identities from unidentified users. If Transparent Kerberos Authentication is configured, AD users may be identified transparently.
NEW QUESTION 17
What are the two high availability modes?
- A. Load Sharing and Legacy
- B. Traditional and New
- C. Active and Standby
- D. New and Legacy
Answer: D
Explanation:
ClusterXL has four working modes. This section briefly describes each mode and its relative advantages and disadvantages.
Load Sharing Multicast Mode
Load Sharing Unicast Mode
New High Availability Mode
High Availability Legacy Mode
NEW QUESTION 18
Fill in the blank: When tunnel test packets no longer invoke a response, SmartView Monitor displays ____ for the given VPN tunnel.
- A. Down
- B. No Response
- C. Inactive
- D. Failed
Answer: A
NEW QUESTION 19
Using mgmt_cli, what is the correct syntax to import a host object called Server_1 from the CLI?
- A. mgmt_cli add-host “Server_1” ip_address “10.15.123.10” --format txt
- B. mgmt_cli add host name “Server_1” ip_address “10.15.123.10” --format json
- C. mgmt_cli add object-host “Server_1” ip_address “10.15.123.10” --format json
- D. mgmt_cli add object “Server_1” ip_address “10.15.123.10” --format json
Answer: A
NEW QUESTION 20
Traffic from source 192.168.1.1 is going to www.google.com. The Application Control Blade on the gateway is inspecting the traffic. Assuming acceleration is enable which path is handling the traffic?
- A. Slow Path
- B. Medium Path
- C. Fast Path
- D. Accelerated Path
Answer: A
NEW QUESTION 21
......
P.S. Easily pass 156-215.80 Exam with 485 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy 156-215.80 Dumps: https://www.2passeasy.com/dumps/156-215.80/ (485 New Questions)
