156-215.80 Exam
How Many Questions Of 156-215.80 Practice Exam

Exam Code: 156-215.80 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Check Point Certified Security Administrator
Certification Provider: Check-Point
Free Today! Guaranteed Training- Pass 156-215.80 Exam.
Check-Point 156-215.80 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which of the following is NOT a VPN routing option available in a star community?
- A. To satellites through center only
- B. To center, or through the center to other satellites, to Internet and other VPN targets
- C. To center and to other satellites through center
- D. To center only
Answer: A
Explanation:
SmartConsole
For simple hubs and spokes (or if there is only one Hub), the easiest way is to configure a VPN star community in R80 SmartConsole:
On the Star Communitywindow, in the:
Center Gateways section, select the Security Gateway that functions as the "Hub".
Satellite Gateways section, select Security Gateways as the "spokes", or satellites.
On the VPN Routing page, Enable VPN routing for satellites section, select one of these options:
To center and to other Satellites through center - This allows connectivity between the Security Gateways, for example if the spoke Security Gateways are DAIP Security Gateways, and the Hub is a Security Gateway with a static IP address.
To center, or through the center to other satellites, to internet and other VPN targets - This allows connectivity between the Security Gateways as well as the ability to inspect all communication passing through the Hub to the Internet.
Create an appropriate Access Control Policy rule.
NAT the satellite Security Gateways on the Hub if the Hub is used to route connections from Satellites to the Internet.
The two Dynamic Objects (DAIP Security Gateways) can securely route communication through the Security Gateway with the static IP address.
NEW QUESTION 2
Fill in the blanks: In the Network policy layer, the default action for the Implied last rule is ___ all traffic. However, in the Application Control policy layer, the default action is _____ all traffic.
- A. Accept; redirect
- B. Accept; drop
- C. Redirect; drop
- D. Drop; accept
Answer: D
NEW QUESTION 3
In order to modify Security Policies the administrator can use which of the following tools? Select the BEST answer.
- A. Command line of the Security Management Server or mgmt_cli.exe on any Windows computer.
- B. SmartConsole and WebUI on the Security Management Server.
- C. mgmt_cli or WebUI on Security Gateway and SmartConsole on the Security Management Server.
- D. SmartConsole or mgmt_cli on any computer where SmartConsole is installed.
Answer: D
NEW QUESTION 4
Vanessa is expecting a very important Security Report. The Document should be sent as an attachment via
e-m ail. An e-mail with Security_report.pdf file was delivered to her e-mail inbox. When she opened the PDF file, she noticed that the file is basically empty and only few lines of text are in it. The report is missing some graphs, tables and links. Which component of SandBlast protection is her company using on a Gateway?
- A. SandBlast Threat Emulation
- B. SandBlast Agent
- C. Check Point Protect
- D. SandBlast Threat Extraction
Answer: D
NEW QUESTION 5
What port is used for communication to the User Center with SmartUpdate?
- A. CPMI 200
- B. TCP 8080
- C. HTTP 80
- D. HTTPS 443
Answer: D
NEW QUESTION 6
What needs to be configured if the NAT property ‘Translate destination on client side’ is not enabled in Global properties?
- A. A host route to route to the destination IP
- B. Use the file local.arp to add the ARP entries for NAT to work
- C. Nothing, the Gateway takes care of all details necessary
- D. Enabling ‘Allow bi-directional NAT’ for NAT to work correctly
Answer: C
NEW QUESTION 7
Fill in the blank: To create policy for traffic to or from a particular location, use the_____ .
- A. DLP shared policy
- B. Geo policy shared policy
- C. Mobile Access software blade
- D. HTTPS inspection
Answer: B
Explanation:
Shared Policies
The Shared Policies section in the Security Policies shows the policies that are not in a Policy package. T are shared between all Policy packages.
Shared policies are installed with the Access Control Policy. Software Blade
Description Mobile Access
Launch Mobile Access policy in a SmartConsole. Configure how your remote users access internal resources, such as their email accounts, when they are mobile.
DLP Launch Data Loss Prevention policy in a SmartConsole. Configure advanced tools to automatically identify data that must not go outside the network, to block the leak, and to educate users.
Geo Policy
Create a policy for traffic to or from specific geographical or political locations. References:
NEW QUESTION 8
Fill in the blank: An LDAP server holds one or more ______.
- A. Server Units
- B. Administrator Units
- C. Account Units
- D. Account Server
Answer: C
NEW QUESTION 9
Which of the following is the most secure means of authentication?
- A. Password
- B. Certificate
- C. Token
- D. Pre-shared secret
Answer: B
NEW QUESTION 10
Which default user has full read/write access?
- A. Monitor
- B. Altuser
- C. Administrator
- D. Superuser
Answer: C
NEW QUESTION 11
You are about to test some rule and object changes suggested in an R77 news group. Which backup solution should you use to ensure the easiest restoration of your Security Policy to its previous configuration after testing the changes?
- A. Manual copies of the directory $FWDIR/conf
- B. upgrade_export command
- C. Database Revision Control
- D. GAiA backup utilities
Answer: C
NEW QUESTION 12
Ken wants to obtain a configuration lock from other administrator on R80 Security Management Server. He can do this via WebUI or a via CLI. Which command should be use in CLI? Choose the correct answer.
- A. remove database lock
- B. The database feature has one command lock database override.
- C. override database lock
- D. The database feature has two commands: lock database override and unlock databas
- E. Both will work.
Answer: D
Explanation:
Use the database feature to obtain the configuration lock. The database feature has two commands:
lock database [override].
unlock database
The commands do the same thing: obtain the configuration lock from another administrator.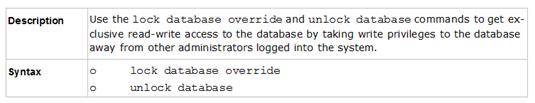
NEW QUESTION 13
What does it mean if Deyra sees the gateway status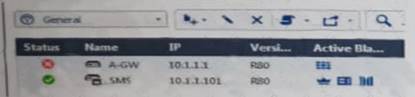
Choose the BEST answer.
- A. SmartCenter Server cannot reach this Security Gateway
- B. There is a blade reporting a problem
- C. VPN software blade is reporting a malfunction
- D. Security Gateway s MGNT NIC card is disconnected
Answer: A
NEW QUESTION 14
What is the SOLR database for?
- A. Used for full text search and enables powerful matching capabilities
- B. Writes data to the database and full text search
- C. Serves GUI responsible to transfer request to the DLE server
- D. Enables powerful matching capabilities and writes data to the database
Answer: A
NEW QUESTION 15
What are the three authentication methods for SIC?
- A. Passwords, Users, and standards-based SSL for the creation of security channels
- B. Certificates, standards-based SSL for the creation of secure channels, and 3DES or AES128 for encryption
- C. Packet Filtering, certificates, and 3DES or AES128 for encryption
- D. Certificates, Passwords, and Tokens
Answer: B
Explanation:
Secure Internal Communication (SIC)
Secure Internal Communication (SIC) lets Check Point platforms and products authenticate with each other. The SIC procedure creates a trusted status between gateways, management servers and other Check Point components. SIC is required to install polices on gateways and to send logs between gateways and management servers.
These security measures make sure of the safety of SIC:
Certificates for authentication
Standards-based SSL for the creation of the secure channel
3DES for encryption
References:
NEW QUESTION 16
What does the “unknown” SIC status shown on SmartConsole mean?
- A. The SMS can contact the Security Gateway but cannot establish Secure Internal Communication.
- B. SIC activation key requires a reset.
- C. The SIC activation key is not known by any administrator.
- D. There is no connection between the Security Gateway and SMS.
Answer: D
Explanation:
The most typical status is Communicating. Any other status indicates that the SIC communication is problematic. For example, if the SIC status is Unknown then there is no connection between the Gateway an the Security Management server. If the SIC status is Not Communicating, the Security Management server is able to contact the gateway, but SIC communication cannot be established.
NEW QUESTION 17
What happens when you run the command: fw sam -J src [Source IP Address]?
- A. Connections from the specified source are blocked without the need to change the Security Policy.
- B. Connections to the specified target are blocked without the need to change the Security Policy.
- C. Connections to and from the specified target are blocked without the need to change the Security Policy.
- D. Connections to and from the specified target are blocked with the need to change the Security Policy.
Answer: A
NEW QUESTION 18
When a Security Gateways sends its logs to an IP address other than its own, which deployment option is installed?
- A. Distributed
- B. Standalone
- C. Bridge
Answer: A
NEW QUESTION 19
Fill in the blank: In order to install a license, it must first be added to the ______ .
- A. User Center
- B. Package repository
- C. Download Center Web site
- D. License and Contract repository
Answer: B
NEW QUESTION 20
Choose what BEST describes the reason why querying logs now is very fast.
- A. New Smart-1 appliances double the physical memory install
- B. Indexing Engine indexes logs for faster search results
- C. SmartConsole now queries results directly from the Security Gateway
- D. The amount of logs been store is less than the usual in older versions
Answer: B
NEW QUESTION 21
......
P.S. Certleader now are offering 100% pass ensure 156-215.80 dumps! All 156-215.80 exam questions have been updated with correct answers: https://www.certleader.com/156-215.80-dumps.html (485 New Questions)
