SY0-501 Exam
CompTIA SY0-501 Exam Questions 2021

It is more faster and easier to pass the by using . Immediate access to the and find the same core area with professionally verified answers, then PASS your exam with a high score now.
Online CompTIA SY0-501 free dumps demo Below:
NEW QUESTION 1
You have just received some room and WiFi access control recommendations from a security consulting company. Click on each building to bring up available security controls. Please implement the following requirements:
The Chief Executive Officer's (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three-factor authentication, while retaining the expensive iris render.
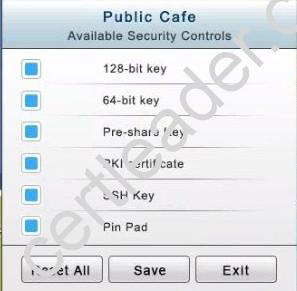
The Public Cafe has wireless available to customers. You need to secure the WAP with WPA and place a passphrase on the customer receipts.
In the Data Center you need to include authentication from the "something you know" category and take advantage of the existing smartcard reader on the door.
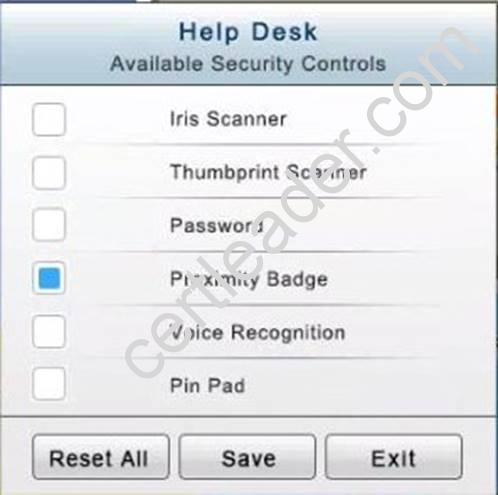
In the Help Desk Office, you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.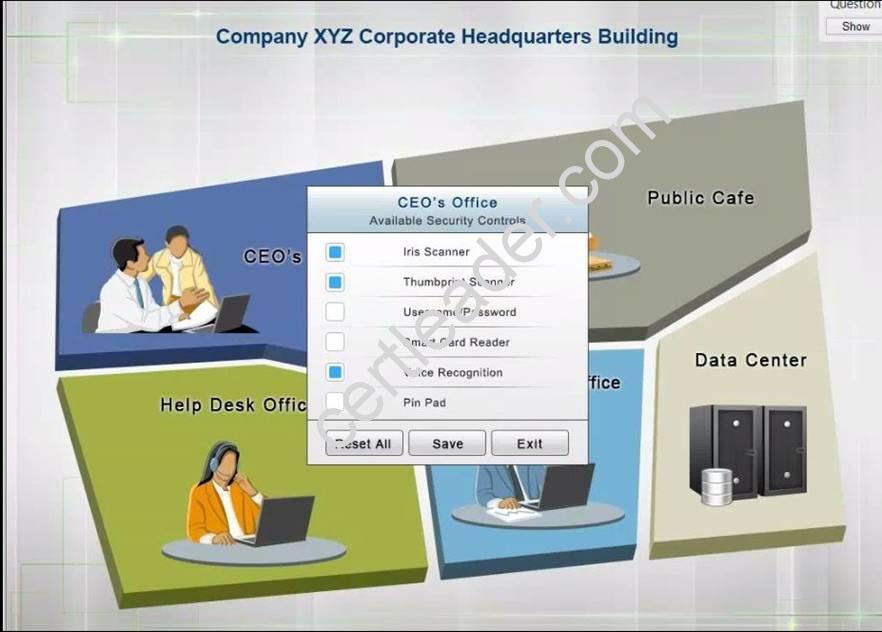
Instructions: The original security controls for each office can be reset at any time by selecting the Reset button. Once you have met the above requirements for each office, select the Save button. When you have completed the entire simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.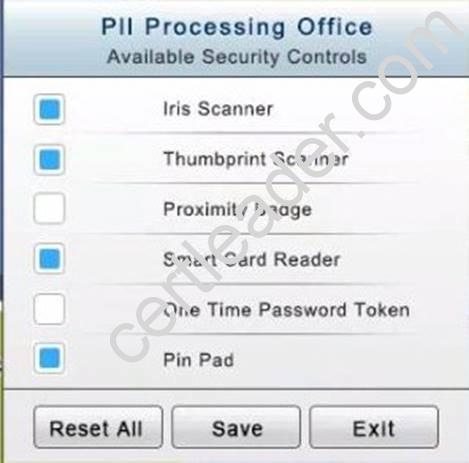
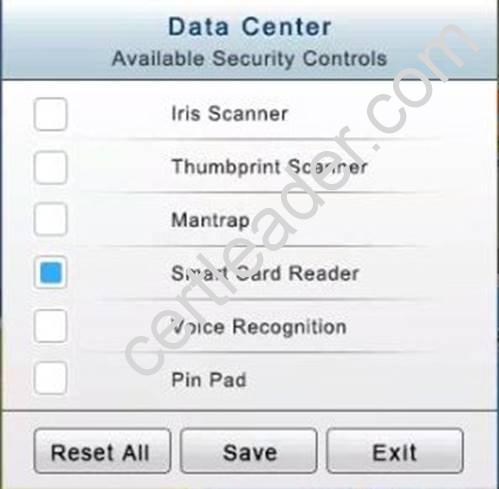
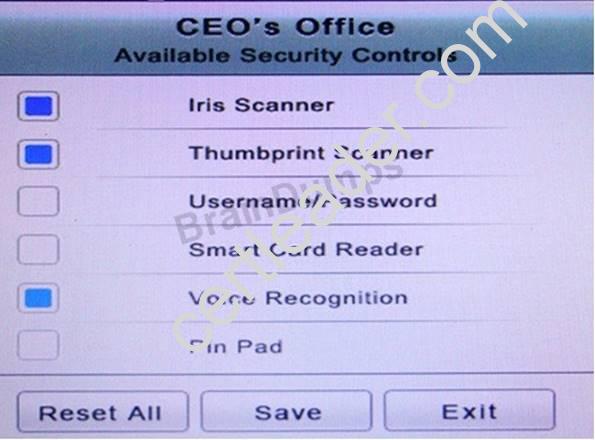
Answer:
Explanation:
Solution as
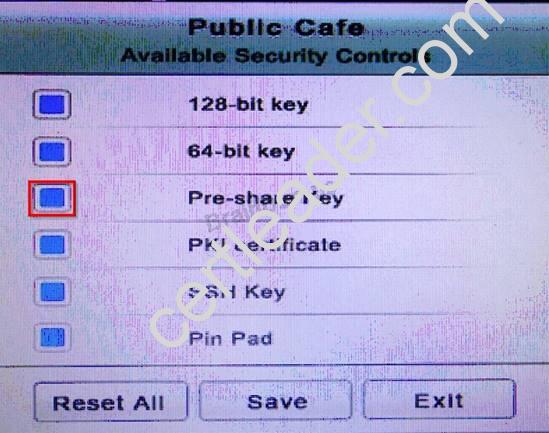
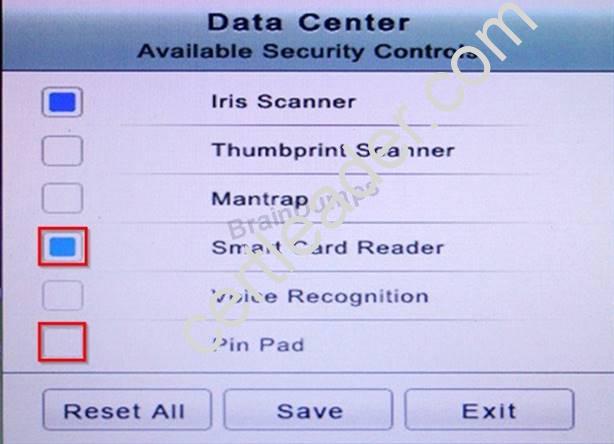
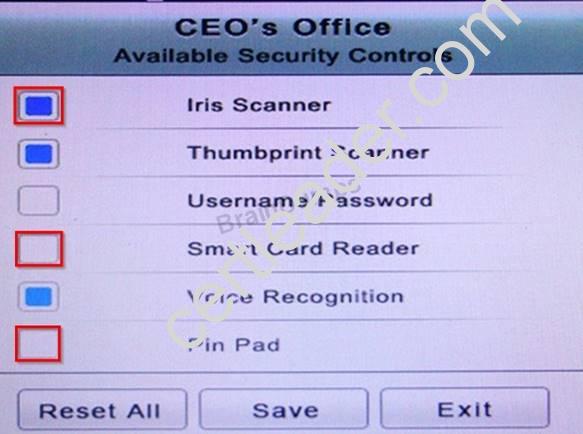
NEW QUESTION 2
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan.
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.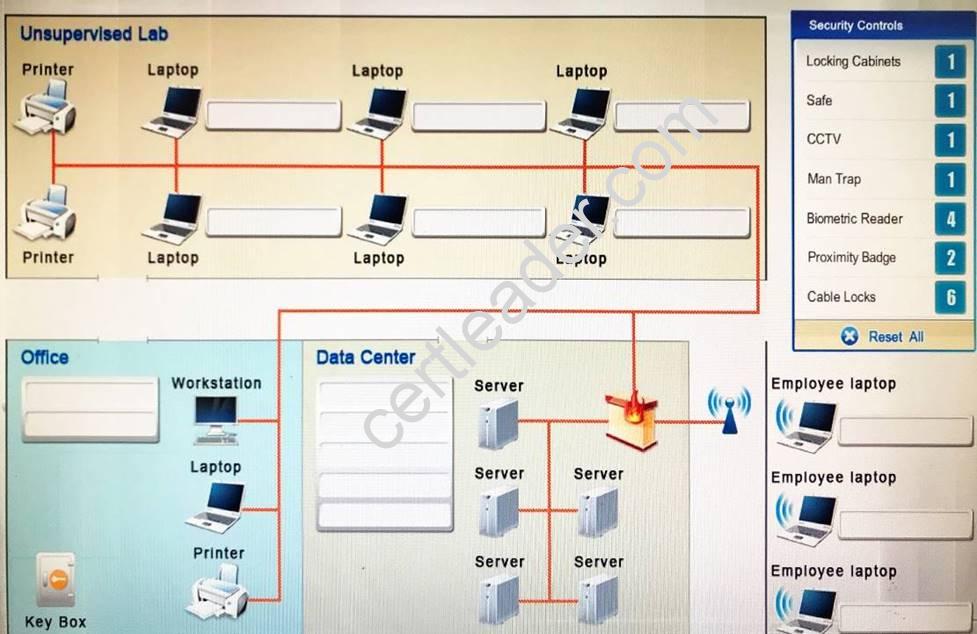
Answer:
Explanation: Cable locks - Adding a cable lock between a laptop and a desk prevents someone from picking it up and
walking away
Proximity badge + reader
Safe is a hardware/physical security measure
Mantrap can be used to control access to sensitive areas. CCTV can be used as video surveillance. Biometric reader can be used to control and prevent unauthorized access. Locking cabinets can be used to
protect backup media, documentation and other physical artefacts.
NEW QUESTION 3
A security technician would like to obscure sensitive data within a file so that it can be transferred without causing suspicion. Which of the following technologies would BEST be suited to accomplish this?
- A. Transport Encryption
- B. Stream Encryption
- C. Digital Signature
- D. Steganography
Answer: D
Explanation: Steganography is the process of hiding a message in another message so as to obfuscate its importance. It is also the process of hiding a message in a medium such as a digital image, audio file, or other file. In theory, doing this prevents analysts from detecting the real message. You could encode your message in another file or message and use that file to hide your message.
NEW QUESTION 4
A security administrator suspects that data on a server has been exhilarated as a result of un- authorized remote access. Which of the following would assist the administrator in con-firming the suspicions? (Select TWO)
- A. Networking access control
- B. DLP alerts
- C. Log analysis
- D. File integrity monitoring
- E. Host firewall rules
Answer: BC
NEW QUESTION 5
The Chief Technology Officer (CTO) of a company, Ann, is putting together a hardware budget for the next 10 years. She is asking for the average lifespan of each hardware device so that she is able to calculate when she will have to replace each device.
Which of the following categories BEST describes what she is looking for?
- A. ALE
- B. MTTR
- C. MTBF
- D. MTTF
Answer: D
NEW QUESTION 6
Ann, a security administrator, has been instructed to perform fuzz-based testing on the company's applications. Which of the following best describes what she will do?
- A. Enter random or invalid data into the application in an attempt to cause it to fault
- B. Work with the developers to eliminate horizontal privilege escalation opportunities
- C. Test the applications for the existence of built-in- back doors left by the developers
- D. Hash the application to verify it won't cause a false positive on the HIPS
Answer: A
NEW QUESTION 7
A security administrator receives notice that a third-party certificate authority has been compromised, and new certificates will need to be issued. Which of the following should the administrator submit to receive a new certificate?
- A. CRL
- B. OSCP
- C. PFX
- D. CSR
- E. CA
Answer: D
NEW QUESTION 8
AChief Information Officer (CIO) has decided it is not cost effective to implement safeguards against a known vulnerability. Which of the following risk responses does this BEST describe?
- A. Transference
- B. Avoidance
- C. Mitigation
- D. Acceptance
Answer: D
NEW QUESTION 9
An organization wants to upgrade its enterprise-wide desktop computer solution. The organization currently has 500 PCs active on the network. the Chief Information Security Officer (CISO) suggests that the organization employ desktop imaging technology for such a large scale upgrade. Which of the following is a security benefit of implementing an imaging solution?
- A. it allows for faster deployment
- B. it provides a consistent baseline
- C. It reduces the number of vulnerabilities
- D. It decreases the boot time
Answer: B
NEW QUESTION 10
A member of a digital forensics team, Joe arrives at a crime scene and is preparing to collect system data. Before powering the system off, Joe knows that he must collect the most volatile date first. Which of the following is the correct order in which Joe should collect the data?
- A. CPU cache, paging/swap files, RAM, remote logging data
- B. RAM, CPU cach
- C. Remote logging data, paging/swap files
- D. Paging/swap files, CPU cache, RAM, remote logging data
- E. CPU cache, RAM, paging/swap files, remote logging data
Answer: D
NEW QUESTION 11
An attack that is using interference as its main attack to impede network traffic is which of the following?
- A. Introducing too much data to a targets memory allocation
- B. Utilizing a previously unknown security flaw against the target
- C. Using a similar wireless configuration of a nearby network
- D. Inundating a target system with SYN requests
Answer: C
NEW QUESTION 12
The availability of a system has been labeled as the highest priority. Which of the following should be focused on the MOST to ensure the objective?
- A. Authentication
- B. HVAC
- C. Full-disk encryption
- D. File integrity checking
Answer: B
NEW QUESTION 13
A security administrator is creating a subnet on one of the corporate firewall interfaces to use as a DMZ which is expected to accommodate at most 14 physical hosts.
Which of the following subnets would BEST meet the requirements?
- A. 192.168.0.16 255.25.255.248
- B. 192.168.0.16/28
- C. 192.168.1.50 255.255.25.240
- D. 192.168.2.32/27
Answer: B
NEW QUESTION 14
Following the successful response to a data-leakage incident, the incident team lead facilitates an exercise that focuses on continuous improvement of the organization's incident response capabilities. Which of the following activities has the incident team lead executed?
- A. Lessons learned review
- B. Root cause analysis
- C. Incident audit
- D. Corrective action exercise
Answer: A
NEW QUESTION 15
An external auditor visits the human resources department and performs a physical security assessment. The auditor observed documents on printers that are unclaimed. A closer look at these documents reveals employee names, addresses, ages, and types of medical and dental coverage options each employee has selected. Which of the following is the MOST appropriate actions to take?
- A. Flip the documents face down so no one knows these documents are PII sensitive
- B. Shred the documents and let the owner print the new set
- C. Retrieve the documents, label them with a PII cover sheet, and return them to the printer
- D. Report to the human resources manager that their personnel are violating a privacy policy
Answer: D
NEW QUESTION 16
Which of the following techniques can be bypass a user or computer's web browser privacy settings? (Select Two)
- A. SQL injection
- B. Session hijacking
- C. Cross-site scripting
- D. Locally shared objects
- E. LDAP injection
Answer: BC
NEW QUESTION 17
A help desk technician receives a phone call from an individual claiming to be an employee of the organization and requesting assistance to access a locked account. The help desk technician asks the individual to provide proof of identity before access can be granted. Which of the following types of attack is the caller performing?
- A. Phishing
- B. Shoulder surfing
- C. Impersonation
- D. Dumpster diving
Answer: C
NEW QUESTION 18
A company is using a mobile device deployment model in which employees use their personal devices for work at their own discretion. Some of the problems the company is encountering include the following: There is no standardization.
There is no standardization. Employees ask for reimbursement for their devices.
Employees ask for reimbursement for their devices. Employees do not replace their devices often enough to keep them running efficiently.
Employees do not replace their devices often enough to keep them running efficiently.  The company does not have enough control over the devices.
The company does not have enough control over the devices.
Which of the following is a deployment model that would help the company overcome these problems?
- A. BYOD
- B. VDI
- C. COPE
- D. CYOD
Answer: D
100% Valid and Newest Version SY0-501 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/SY0-501-dumps.html (New 540 Q&As)
