SY0-501 Exam
Approved SY0-501 Braindumps 2021

Our pass rate is high to 98.9% and the similarity percentage between our and real exam is 90% based on our seven-year educating experience. Do you want achievements in the CompTIA SY0-501 exam in just one try? I am currently studying for the . Latest , Try CompTIA SY0-501 Brain Dumps First.
Online CompTIA SY0-501 free dumps demo Below:
NEW QUESTION 1
A software development company needs to share information between two remote servers, using encryption to protect it. A programmer suggests developing a new encryption protocol, arguing that using an unknown protocol with secure, existing cryptographic algorithm libraries will provide strong encryption without being
susceptible to attacks on other known protocols. Which of the following summarizes the BEST response to the programmer's proposal?
- A. The newly developed protocol will only be as secure as the underlying cryptographic algorithms used.
- B. New protocols often introduce unexpected vulnerabilities, even when developed with otherwise secure and tested algorithm libraries.
- C. A programmer should have specialized training in protocol development before attempting to design a new encryption protocol.
- D. The obscurity value of unproven protocols against attacks often outweighs the potential for introducing new vulnerabilities.
Answer: B
NEW QUESTION 2
A software development manager is taking over an existing software development project. The team currently suffers from poor communication due to a long delay between requirements documentation and feature delivery. This gap is resulting in an above average number of security-related bugs making it into production. Which of the following development methodologies is the team MOST likely using now?
- A. Agile
- B. Waterfall
- C. Scrum
- D. Spiral
Answer: B
NEW QUESTION 3
A company has noticed multiple instances of proprietary information on public websites. It has also observed an increase in the number of email messages sent to random employees containing malicious links and PDFs. Which of the following changes should the company make to reduce the risks associated with phishing attacks? (Select TWO)
- A. Install an additional firewall
- B. Implement a redundant email server
- C. Block access to personal email on corporate systems
- D. Update the X.509 certificates on the corporate email server
- E. Update corporate policy to prohibit access to social media websites
- F. Review access violation on the file server
Answer: CE
NEW QUESTION 4
A company was recently audited by a third party. The audit revealed the company’s network devices were transferring files in the clear. Which of the following protocols should the company use to transfer files?
- A. HTTPS
- B. LDAPS
- C. SCP
- D. SNMPv3
Answer: C
NEW QUESTION 5
In a corporation where compute utilization spikes several times a year, the Chief Information Officer (CIO) has requested a cost-effective architecture to handle the variable capacity demand. Which of the following characteristics BEST describes what the CIO has requested?
- A. Elasticity
- B. Scalability
- C. High availability
- D. Redundancy
Answer: A
Explanation: Elasticity is defined as “the degree to which a system is able to adapt to workload changes by provisioning and de-provisioning resources in an autonomic manner, such that at each point in time the available resources match the current demand as closely as possible”.
NEW QUESTION 6
Drag and drop the correct protocol to its default port.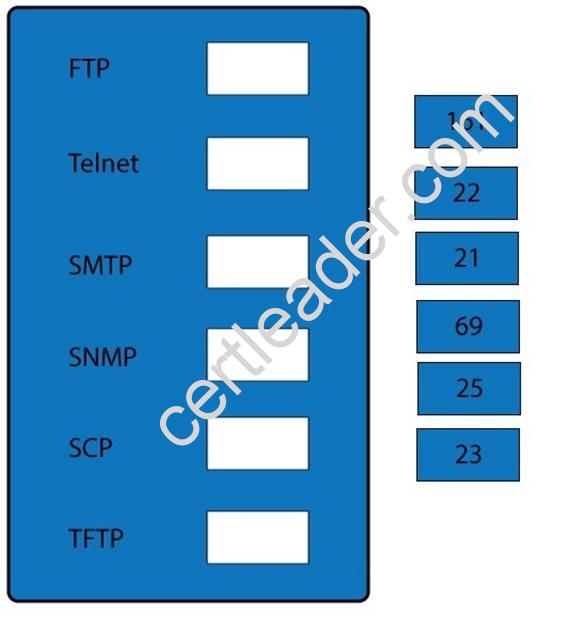
Answer:
Explanation: FTP uses TCP port 21. Telnet uses port 23. SSH uses TCP port 22.
All protocols encrypted by SSH, including SFTP, SHTTP, SCP, SExec, and slogin, also use TCP port 22. Secure Copy Protocol (SCP) is a secure file-transfer facility based on SSH and Remote Copy Protocol (RCP).
Secure FTP (SFTP) is a secured alternative to standard File Transfer Protocol (FTP). SMTP uses TCP port 25. Port 69 is used by TFTP.
SNMP makes use of UDP ports 161 and 162. http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
NEW QUESTION 7
A company determines that it is prohibitively expensive to become compliant with new credit card regulations. Instead, the company decides to purchase insurance to cover the cost of any potential loss. Which of the following is the company doing?
- A. Transferring the risk
- B. Accepting the risk
- C. Avoiding the risk
- D. Migrating the risk
Answer: A
NEW QUESTION 8
An organization wants to conduct secure transactions of large data files. Before encrypting and exchanging the data files, the organization wants to ensure a secure exchange of keys. Which of the following algorithms is appropriate for securing the key exchange?
- A. DES
- B. Blowfish
- C. DSA
- D. Diffie-Hellman
- E. 3DES
Answer: D
NEW QUESTION 9
Joe, a technician, is working remotely with his company provided laptop at the coffee shop near his home. Joe is concerned that another patron of the coffee shop may be trying to access his laptop. Which of the following is an appropriate control to use to prevent the other patron from accessing Joe's laptop directly?
- A. full-disk encryption
- B. Host-based firewall
- C. Current antivirus definitions
- D. Latest OS updates
Answer: B
NEW QUESTION 10
Six months into development, the core team assigned to implement a new internal piece of software must convene to discuss a new requirement with the stake holders. A stakeholder identified a missing feature critical to the organization, which must be implemented. The team needs to validate the feasibility of the newly introduced requirement and ensure it does not introduce new vulnerabilities to the software and other applications that will integrate with it. Which of the following BEST describes what the company?
- A. The system integration phase of the SDLC
- B. The system analysis phase of SSDSLC
- C. The system design phase of the SDLC
- D. The system development phase of the SDLC
Answer: B
NEW QUESTION 11
A wireless network has the following design requirements: Authentication must not be dependent on enterprise directory service
Authentication must not be dependent on enterprise directory service  It must allow background reconnection for mobile users
It must allow background reconnection for mobile users It must not depend on user certificates
It must not depend on user certificates
Which of the following should be used in the design to meet the requirements? (Choose two.)
- A. PEAP
- B. PSK
- C. Open systems authentication
- D. EAP-TLS
- E. Captive portals
Answer: BE
NEW QUESTION 12
A network operations manager has added a second row of server racks in the datacenter. These racks face the opposite direction of the first row of racks.
Which of the following is the reason the manager installed the racks this way?
- A. To lower energy consumption by sharing power outlets
- B. To create environmental hot and cold isles
- C. To eliminate the potential for electromagnetic interference
- D. To maximize fire suppression capabilities
Answer: B
NEW QUESTION 13
An organization's file server has been virtualized to reduce costs. Which of the following types of backups would be MOST appropriate for the particular file server?
- A. Snapshot
- B. Full
- C. Incremental
- D. Differential
Answer: C
NEW QUESTION 14
A new hire wants to use a personally owned phone to access company resources. The new hire expresses concern about what happens to the data on the phone when they leave the company. Which of the following portions of the company's mobile device management configuration would allow the company data to be removed from the device without touching the new hire's data?
- A. Asset control
- B. Device access control
- C. Storage lock out
- D. Storage segmentation
Answer: B
NEW QUESTION 15
A systems administrator is reviewing the following information from a compromised server:
Given the above information, which of the following processes was MOST likely exploited via a remote buffer overflow attack?
- A. Apache
- B. LSASS
- C. MySQL
- D. TFTP
Answer: A
NEW QUESTION 16
The administrator installs database software to encrypt each field as it is written to disk. Which of the following describes the encrypted data?
- A. In-transit
- B. In-use
- C. Embedded
- D. At-rest
Answer: B
NEW QUESTION 17
A security administrator has written a script that will automatically upload binary and text-based configuration files onto a remote server using a scheduled task. The configuration files contain sensitive information. Which of the following should the administrator use? (Select TWO)
- A. TOPT
- B. SCP
- C. FTP over a non-standard pot
- D. SRTP
- E. Certificate-based authentication
- F. SNMPv3
Answer: CE
NEW QUESTION 18
Which of the following delineates why it is important to perform egress filtering and monitoring on Internet connected security zones of interfaces on a firewall?
- A. Egress traffic is more important than ingress traffic for malware prevention
- B. To rebalance the amount of outbound traffic and inbound traffic
- C. Outbound traffic could be communicating to known botnet sources
- D. To prevent DDoS attacks originating from external network
Answer: B
Thanks for reading the newest SY0-501 exam dumps! We recommend you to try the PREMIUM Surepassexam SY0-501 dumps in VCE and PDF here: https://www.surepassexam.com/SY0-501-exam-dumps.html (540 Q&As Dumps)
