SY0-501 Exam
CompTIA SY0-501 Exam Questions and Answers 2021

Our pass rate is high to 98.9% and the similarity percentage between our and real exam is 90% based on our seven-year educating experience. Do you want achievements in the CompTIA SY0-501 exam in just one try? I am currently studying for the . Latest , Try CompTIA SY0-501 Brain Dumps First.
Free SY0-501 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
A security administrator learns that PII, which was gathered by the organization, has been found in an open
forum. As a result, several C-level executives found their identities were compromised, and they were victims of a recent whaling attack.
Which of the following would prevent these problems in the future? (Select TWO).
- A. Implement a reverse proxy.
- B. Implement an email DLP.
- C. Implement a spam filter.
- D. Implement a host-based firewall.
- E. Implement a HIDS.
Answer: BC
NEW QUESTION 2
A company is planning to encrypt the files in several sensitive directories of a file server with a symmetric key. Which of the following could be used?
- A. RSA
- B. TwoFish
- C. Diffie-Helman
- D. NTLMv2
- E. RIPEMD
Answer: B
NEW QUESTION 3
A systems administrator has isolated an infected system from the network and terminated the malicious process from executing. Which of the following should the administrator do NEXT according to the incident response process?
- A. Restore lost data from a backup.
- B. Wipe the system.
- C. Document the lessons learned.
- D. Determine the scope of impact.
Answer: A
NEW QUESTION 4
Which of the following would a security specialist be able to determine upon examination of a server’s certificate?
- A. CA public key
- B. Server private key
- C. CSR
- D. OID
Answer: D
NEW QUESTION 5
An organization uses SSO authentication for employee access to network resources. When an employee resigns, as per the organization’s security policy, the employee’s access to all network resources is terminated immediately. Two weeks later, the former employee sends an email to the help desk for a password reset to access payroll information from the human resources server. Which of the following represents the BEST course of action?
- A. Approve the former employee’s request, as a password reset would give the former employee access to only the human resources server.
- B. Deny the former employee’s request, since the password reset request came from an external email address.
- C. Deny the former employee’s request, as a password reset would give the employee access to all network resources.
- D. Approve the former employee’s request, as there would not be a security issue with the former employee gaining access to network resources.
Answer: C
NEW QUESTION 6
An attacker uses a network sniffer to capture the packets of a transaction that adds $20 to a gift card. The attacker then user a function of the sniffer to push those packets back onto the network again, adding another $20 to the gift card. This can be done many times. Which of the following describes this type of attack?
- A. Integer overflow attack
- B. Smurf attack
- C. Replay attack
- D. Buffer overflow attack
- E. Cross-site scripting attack
Answer: C
NEW QUESTION 7
After a user reports stow computer performance, a systems administrator detects a suspicious file, which was installed as part of a freeware software package.
The systems administrator reviews the output below:
Based on the above information, which of the following types of malware was installed on the user's computer?
- A. RAT
- B. Keylogger
- C. Spyware
- D. Worm
- E. Bot
Answer: D
NEW QUESTION 8
As part of the SDLC, a third party is hired to perform a penetration test. The third party will have access to the source code, integration tests, and network diagrams. Which of the following BEST describes the assessment being performed?
- A. Black box
- B. Regression
- C. White box
- D. Fuzzing
Answer: C
NEW QUESTION 9
Which of the following could help detect trespassers in a secure facility? (Select TWO)
- A. Faraday cages
- B. Motion-detection sensors
- C. Tall, chain-link fencing
- D. Security guards
- E. Smart cards
Answer: BD
NEW QUESTION 10
Which of the following is the BEST reason for salting a password hash before it is stored in a database?
- A. To prevent duplicate values from being stored
- B. To make the password retrieval process very slow
- C. To protect passwords from being saved in readable format
- D. To prevent users from using simple passwords for their access credentials
Answer: A
NEW QUESTION 11
A security analyst is reviewing the following packet capture of an attack directed at a company's server located in the DMZ: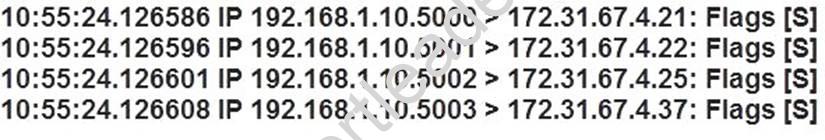
Which of the following ACLs provides the BEST protection against the above attack and any further attacks from the same IP, while minimizing service interruption?
- A. DENY TCO From ANY to 172.31.64.4
- B. Deny UDP from 192.168.1.0/24 to 172.31.67.0/24
- C. Deny IP from 192.168.1.10/32 to 0.0.0.0/0
- D. Deny TCP from 192.168.1.10 to 172.31.67.4
Answer: D
NEW QUESTION 12
Which of the following network vulnerability scan indicators BEST validates a successful, active scan?
- A. The scan job is scheduled to run during off-peak hours.
- B. The scan output lists SQL injection attack vectors.
- C. The scan data identifies the use of privileged-user credentials.
- D. The scan results identify the hostname and IP address.
Answer: D
NEW QUESTION 13
A wireless network uses a RADIUS server that is connected to an authenticator, which in turn connects to a supplicant. Which of the following represents the authentication architecture in use?
- A. Open systems authentication
- B. Captive portal
- C. RADIUS federation
- D. 802.1x
Answer: D
NEW QUESTION 14
During a routine vulnerability assessment, the following command was successful:
echo "vrfy 'perl -e 'print "hi" x 500 ' ' " | nc www.company.com 25 Which of the following vulnerabilities is being exploited?
- A. Buffer overflow directed at a specific host MTA
- B. SQL injection directed at a web server
- C. Cross-site scripting directed at www.company.com
- D. Race condition in a UNIX shell script
Answer: A
NEW QUESTION 15
A security analyst is updating a BIA document. The security analyst notices the support vendor's time to replace a server hard drive went from eight hours to two hours. Given these new metrics, which of the following can be concluded? (Select TWO)
- A. The MTTR is faster.
- B. The MTTR is slower.
- C. The RTO has increased.
- D. The RTO has decreased.
- E. The MTTF has increased.
- F. The MTTF has decreased.
Answer: AD
NEW QUESTION 16
Which of the following controls allows a security guard to perform a post-incident review?
- A. Detective
- B. Preventive
- C. Corrective
- D. Deterrent
Answer: C
NEW QUESTION 17
A vulnerability scan is being conducted against a desktop system. The scan is looking for files, versions, and registry values known to be associated with system vulnerabilities. Which of the following BEST describes the type of scan being performed?
- A. Non-intrusive
- B. Authenticated
- C. Credentialed
- D. Active
Answer: C
NEW QUESTION 18
A development team has adopted a new approach to projects in which feedback is iterative and multiple iterations of deployments are provided within an application’s full life cycle. Which of the following software development methodologies is the development team using?
- A. Waterfall
- B. Agile
- C. Rapid
- D. Extreme
Answer: B
100% Valid and Newest Version SY0-501 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/SY0-501-dumps.html (New 540 Q&As)
