SY0-501 Exam
CompTIA SY0-501 Exam Questions 2021

We provide which are the best for clearing SY0-501 test, and to get certified by CompTIA CompTIA Security+ Certification Exam. The covers all the knowledge points of the real SY0-501 exam. Crack your CompTIA SY0-501 Exam with latest dumps, guaranteed!
CompTIA SY0-501 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
When identifying a company’s most valuable assets as part of a BIA, which of the following should be the FIRST priority?
- A. Life
- B. Intellectual property
- C. Sensitive data
- D. Public reputation
Answer: A
NEW QUESTION 2
Which of the following occurs when the security of a web application relies on JavaScript for input validation?
- A. The integrity of the data is at risk.
- B. The security of the application relies on antivirus.
- C. A host-based firewall is required.
- D. The application is vulnerable to race conditions.
Answer: A
NEW QUESTION 3
A security administrator is trying to eradicate a worm, which is spreading throughout the organization, using an old remote vulnerability in the SMB protocol. The worm uses Nmap to identify target hosts within the company. The administrator wants to implement a solution that will eradicate the current worm and any future attacks that may be using zero-day vulnerabilities. Which of the following would BEST meet the requirements when implemented?
- A. Host-based firewall
- B. Enterprise patch management system
- C. Network-based intrusion prevention system
- D. Application blacklisting
- E. File integrity checking
Answer: C
NEW QUESTION 4
A company wants to ensure that the validity of publicly trusted certificates used by its web server can be determined even during an extended internet outage. Which of the following should be implemented?
- A. Recovery agent
- B. Ocsp
- C. Crl
- D. Key escrow
Answer: B
NEW QUESTION 5
Which of the following would verify that a threat does exist and security controls can easily be bypassed without actively testing an application?
- A. Protocol analyzer
- B. Vulnerability scan
- C. Penetration test
- D. Port scanner
Answer: B
Explanation: A vulnerability scan is the automated process of proactively identifying security vulnerabilities of computing systems in a network in order to determine if and where a system can be exploited and/or threatened. While
public servers are important for communication and data transfer over the Internet, they open the door to potential security breaches by threat agents, such as malicious hackers.
Vulnerability scanning employs software that seeks out security flaws based on a database of known flaws, testing systems for the occurrence of these flaws and generating a report of the findings that an individual or an enterprise can use to tighten the network's security.
Vulnerability scanning typically refers to the scanning of systems that are connected to the Internet but can also refer to system audits on internal networks that are not connected to the Internet in order to assess the threat of rogue software or malicious employees in an enterprise.
NEW QUESTION 6
Which of the following would enhance the security of accessing data stored in the cloud? (Select TWO)
- A. Block level encryption
- B. SAML authentication
- C. Transport encryption
- D. Multifactor authentication
- E. Predefined challenge QUESTION NO:s
- F. Hashing
Answer: BD
NEW QUESTION 7
A new Chief Information Officer (CIO) has been reviewing the badging and decides to write a policy that all employees must have their badges rekeyed at least annually. Which of the following controls BEST describes this policy?
- A. Physical
- B. Corrective
- C. Technical
- D. Administrative
Answer: D
NEW QUESTION 8
Malicious traffic from an internal network has been detected on an unauthorized port on an application server. Which of the following network-based security controls should the engineer consider implementing?
- A. ACLs
- B. HIPS
- C. NAT
- D. MAC filtering
Answer: A
NEW QUESTION 9
A company would like to prevent the use of a known set of applications from being used on company computers. Which of the following should the security administrator implement?
- A. Whitelisting
- B. Anti-malware
- C. Application hardening
- D. Blacklisting
- E. Disable removable media
Answer: D
NEW QUESTION 10
AChief Security Officer (CSO) has been unsuccessful in attempts to access the website for a potential partner (www.example.net). Which of the following rules is preventing the CSO from accessing the site?
Blocked sites: *.nonews.com, *.rumorhasit.net, *.mars?
- A. Rule 1: deny from inside to outside source any destination any service smtp
- B. Rule 2: deny from inside to outside source any destination any service ping
- C. Rule 3: deny from inside to outside source any destination {blocked sites} service http-https
- D. Rule 4: deny from any to any source any destination any service any
Answer: C
NEW QUESTION 11
An organization is comparing and contrasting migration from its standard desktop configuration to the newest version of the platform. Before this can happen, the Chief Information Security Officer (CISO) voices the need to evaluate the functionality of the newer desktop platform to ensure interoperability with existing software in use by the organization. In which of the following principles of architecture and design is the CISO engaging?
- A. Dynamic analysis
- B. Change management
- C. Baselining
- D. Waterfalling
Answer: B
NEW QUESTION 12
Technicians working with servers hosted at the company's datacenter are increasingly complaining of electric shocks when touching metal items which have been linked to hard drive failures.
Which of the following should be implemented to correct this issue?
- A. Decrease the room temperature
- B. Increase humidity in the room
- C. Utilize better hot/cold aisle configurations
- D. Implement EMI shielding
Answer: B
NEW QUESTION 13
A user of the wireless network is unable to gain access to the network. The symptoms are:
1.) Unable to connect to both internal and Internet resources
2.) The wireless icon shows connectivity but has no network access
The wireless network is WPA2 Enterprise and users must be a member of the wireless security group to authenticate.
Which of the following is the MOST likely cause of the connectivity issues?
- A. The wireless signal is not strong enough
- B. A remote DDoS attack against the RADIUS server is taking place
- C. The user's laptop only supports WPA and WEP
- D. The DHCP scope is full
- E. The dynamic encryption key did not update while the user was offline
Answer: A
NEW QUESTION 14
A security analyst is reviewing the following output from an IPS: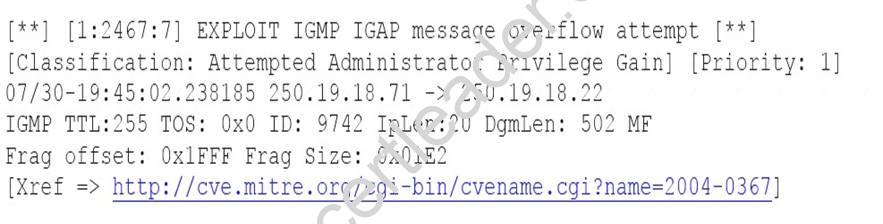
Given this output, which of the following can be concluded? (Select two.)
- A. The source IP of the attack is coming from 250.19.18.22.
- B. The source IP of the attack is coming from 250.19.18.71.
- C. The attacker sent a malformed IGAP packet, triggering the alert.
- D. The attacker sent a malformed TCP packet, triggering the alert.
- E. The TTL value is outside of the expected range, triggering the alert.
Answer: BC
NEW QUESTION 15
An attacker wearing a building maintenance uniform approached a company's receptionist asking for access to a secure areA. The receptionist asks for identification, a building access badge and checks the company's list approved maintenance personnel prior to granting physical access to the secure are. The controls used by the receptionist are in place to prevent which of the following types of attacks?
- A. Tailgating
- B. Shoulder surfing
- C. Impersonation
- D. Hoax
Answer: C
NEW QUESTION 16
Which of the following is an asymmetric function that generates a new and separate key every time it runs?
- A. RSA
- B. DSA
- C. DHE
- D. HMAC
- E. PBKDF2
Answer: C
NEW QUESTION 17
A user downloads and installs an MP3 converter, and runs the application. Upon running the application, the antivirus detects a new port in a listening state. Which of the following has the user MOST likely executed?
- A. RAT
- B. Worm
- C. Ransomware
- D. Bot
Answer: A
NEW QUESTION 18
Joe is exchanging encrypted email with another party. Joe encrypts the initial email with a key. When Joe receives a response, he is unable to decrypt the response with the same key he used initially. Which of the following would explain the situation?
- A. An ephemeral key was used for one of the messages
- B. A stream cipher was used for the initial email; a block cipher was used for the reply
- C. Out-of-band key exchange has taken place
- D. Asymmetric encryption is being used
Answer: D
Explanation: Asymmetric algorithms use two keys to encrypt and decrypt datA. These asymmetric keys are referred to as the public key and the private key. The sender uses the public key to encrypt a message, and the receiver uses the private key to decrypt the message; what one key does, the other one undoes.
Recommend!! Get the Full SY0-501 dumps in VCE and PDF From Certleader, Welcome to Download: https://www.certleader.com/SY0-501-dumps.html (New 540 Q&As Version)
