SY0-501 Exam
CompTIA SY0-501 Study Guides 2021

It is more faster and easier to pass the by using . Immediate access to the and find the same core area with professionally verified answers, then PASS your exam with a high score now.
Online CompTIA SY0-501 free dumps demo Below:
NEW QUESTION 1
Due to regulatory requirements, server in a global organization must use time synchronization. Which of the following represents the MOST secure method of time synchronization?
- A. The server should connect to external Stratum 0 NTP servers for synchronization
- B. The server should connect to internal Stratum 0 NTP servers for synchronization
- C. The server should connect to external Stratum 1 NTP servers for synchronization
- D. The server should connect to external Stratum 1 NTP servers for synchronization
Answer: B
NEW QUESTION 2
A company is deploying a new VoIP phone system. They require 99.999% uptime for their phone service and are concerned about their existing data network interfering with the VoIP phone system. The core switches in the existing data network are almost fully saturated. Which of the following options will pro-vide the best performance and availability for both the VoIP traffic, as well as the traffic on the existing data network?
- A. Put the VoIP network into a different VLAN than the existing data network.
- B. Upgrade the edge switches from 10/100/1000 to improve network speed
- C. Physically separate the VoIP phones from the data network
- D. Implement flood guards on the data network
Answer: A
NEW QUESTION 3
Joe notices there are several user accounts on the local network generating spam with embedded malicious code. Which of the following technical control should Joe put in place to BEST reduce these incidents?
- A. Account lockout
- B. Group Based Privileges
- C. Least privilege
- D. Password complexity
Answer: A
NEW QUESTION 4
When attempting to secure a mobile workstation, which of the following authentication technologies rely on the user's physical characteristics? (Select TWO)
- A. MAC address table
- B. Retina scan
- C. Fingerprint scan
- D. Two-factor authentication
- E. CAPTCHA
- F. Password string
Answer: BC
NEW QUESTION 5
When performing data acquisition on a workstation, which of the following should be captured based on memory volatility? (Select two.)
- A. USB-attached hard disk
- B. Swap/pagefile
- C. Mounted network storage
- D. ROM
- E. RAM
Answer: BE
NEW QUESTION 6
Which of the following describes the key difference between vishing and phishing attacks?
- A. Phishing is used by attackers to steal a person's identity.
- B. Vishing attacks require some knowledge of the target of attack.
- C. Vishing attacks are accomplished using telephony services.
- D. Phishing is a category of social engineering attack.
Answer: C
NEW QUESTION 7
A security analyst is hardening an authentication server. One of the primary requirements is to ensure there is mutual authentication and delegation. Given these requirements, which of the following technologies should the analyst recommend and configure?
- A. LDAP services
- B. Kerberos services
- C. NTLM services
- D. CHAP services
Answer: B
Explanation: Only Kerberos that can do Mutual Auth and Delegation.
NEW QUESTION 8
A security team wants to establish an Incident Response plan. The team has never experienced an incident. Which of the following would BEST help them establish plans and procedures?
- A. Table top exercises
- B. Lessons learned
- C. Escalation procedures
- D. Recovery procedures
Answer: A
NEW QUESTION 9
A network technician is trying to determine the source of an ongoing network based attack. Which of the following should the technician use to view IPv4 packet data on a particular internal network segment?
- A. Proxy
- B. Protocol analyzer
- C. Switch
- D. Firewall
Answer: B
NEW QUESTION 10
A company’s user lockout policy is enabled after five unsuccessful login attempts. The help desk notices a user is repeatedly locked out over the course of a workweek. Upon contacting the user, the help desk discovers the user is on vacation and does not have network access. Which of the following types of attacks are MOST likely occurring? (Select two.)
- A. Replay
- B. Rainbow tables
- C. Brute force
- D. Pass the hash
- E. Dictionary
Answer: CE
NEW QUESTION 11
A datacenter manager has been asked to prioritize critical system recovery priorities. Which of the following is the MOST critical for immediate recovery?
- A. Communications software
- B. Operating system software
- C. Weekly summary reports to management
- D. Financial and production software
Answer: B
NEW QUESTION 12
Adhering to a layered security approach, a controlled access facility employs security guards who verify the authorization of all personnel entering the facility. Which of the following terms BEST describes the security control being employed?
- A. Administrative
- B. Corrective
- C. Deterrent
- D. Compensating
Answer: C
NEW QUESTION 13
An organization has hired a penetration tester to test the security of its ten web servers. The penetration tester is able to gain root/administrative access in several servers by exploiting vulnerabilities associated with the implementation of SMTP, POP, DNS, FTP, Telnet, and IMAP. Which of the following recommendations should the penetration tester provide to the organization to better protect their web servers in the future?
- A. Use a honeypot
- B. Disable unnecessary services
- C. Implement transport layer security
- D. Increase application event logging
Answer: B
NEW QUESTION 14
A company has two wireless networks utilizing captive portals. Some employees report getting a trust error in their browsers when connecting to one of the networks. Both captive portals are using the same server certificate for authentication, but the analyst notices the following differences between the two certificate details:
Certificate 1
Certificate Path: Geotrust Global CA
*company.com Certificate 2 Certificate Path:
*company.com
Which of the following would resolve the problem?
- A. Use a wildcard certificate.
- B. Use certificate chaining.
- C. Use a trust model.
- D. Use an extended validation certificate.
Answer: B
NEW QUESTION 15
The SSID broadcast for a wireless router has been disabled but a network administrator notices that unauthorized users are accessing the wireless network. The administer has determined that attackers are still able to detect the presence of the wireless network despite the fact the SSID has been disabled. Which of the following would further obscure the presence of the wireless network?
- A. Upgrade the encryption to WPA or WPA2
- B. Create a non-zero length SSID for the wireless router
- C. Reroute wireless users to a honeypot
- D. Disable responses to a broadcast probe request
Answer: D
NEW QUESTION 16
The chief Security Officer (CSO) has reported a rise in data loss but no break ins have occurred. By doing which of the following is the CSO most likely to reduce the number of incidents?
- A. Implement protected distribution
- B. Empty additional firewalls
- C. Conduct security awareness training
- D. Install perimeter barricades
Answer: C
NEW QUESTION 17
A systems administrator is deploying a new mission essential server into a virtual environment. Which of the following is BEST mitigated by the environment's rapid elasticity characteristic?
- A. Data confidentiality breaches
- B. VM escape attacks
- C. Lack of redundancy
- D. Denial of service
Answer: D
NEW QUESTION 18
A cybersecurity analyst is looking into the payload of a random packet capture file that was selected for analysis. The analyst notices that an internal host had a socket established with another internal host over a non-standard port.
Upon investigation, the origin host that initiated the socket shows this output: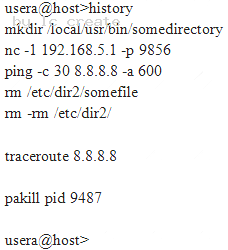
Given the above output, which of the following commands would have established the questionable socket?
- A. traceroute 8.8.8.8
- B. ping -1 30 8.8.8.8 -a 600
- C. nc -1 192.168.5.1 -p 9856
- D. pskill pid 9487
Answer: C
P.S. 2passeasy now are offering 100% pass ensure SY0-501 dumps! All SY0-501 exam questions have been updated with correct answers: https://www.2passeasy.com/dumps/SY0-501/ (540 New Questions)
